Secure Electronic Data Communications and Transactions 99 of















- Slides: 33


Secure Electronic Data Communications and Transactions

99% of Paper Documents were created electronically This means: • Electronic documents actually are the original documents! • Paper documents are copies of electronic documents

Why are people still utilizing paper documents? • They believe it’s the only legal option • They believe it’s the only practical option • They believe it’s the only option available to sign documents • They are ignorant regarding any other options available

Is there an alternative? Absolutely – YES! Verifynow dot Info

Is it legal? Yes! Compliant with: • The Electronic Communications and Transactions Act 25, 2002 • The Financial Intelligence Centre Act 32, 2001 • Regulation of Interception of Communications and Provision of Communication-related Information Act 70, 2002

Is it practical and easy to use? Yes! Logical / User friendly Procedures

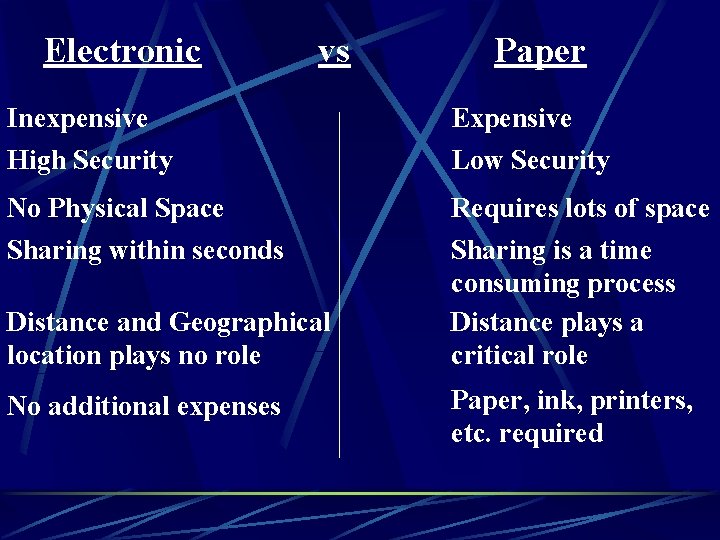
Electronic Inexpensive vs | | | High Security | | No Physical Space | | | Sharing within seconds | | | Distance and Geographical | | | location plays no role | | No additional expenses | | | Paper Expensive Low Security Requires lots of space Sharing is a time consuming process Distance plays a critical role Paper, ink, printers, etc. required

What are the benefits? • Saving Time • Saving Money • Better Access Control • Full Audit Trail • High Security • No additional office space required • Easy to manage and to retrieve • Compliant with business trends • Government motivates us to move into this direction • No additional equipment and software required • Seamlessly integrates with current software • A clean slate and very flexible

Some practical applications of this service • Electronic Invoicing (SARS Compliant) • Tenders and Contracts • Orders and Delivery notes • Electronic Record keeping • Signing and approval of documents • Secure sharing of data

Why Verifynow? • All parties can unconditionally rely on data communicated by means of this service • Absolute protection of the integrity of data • Users have full control over access to - and sharing of data • Legally compliant electronic signatures ensure legally binding agreements, commitments and acceptance of data • Issuing of electronic signatures and verification of identities for this purpose is done according to ECT & FIC Act prescriptions • Full audit trail ensures proper proof of delivery, proof of access and proof of signature. • No deleting, editing or modification of data once communicated or shared • Automatic backup of transaction data for future reference • Impartial third party service legally protecting the interest of all transacting parties

Other product enhancements • Document search facility • Bulk SMS • Document Access Notification • Email Notification • Secure Message facility • Secure Document Sharing facility • In Account Document Access Control • Off Site Data Backup facility • Bio-metric (fingerprint) login option • Third Party Account and Third Party signature facility.

Application Overview

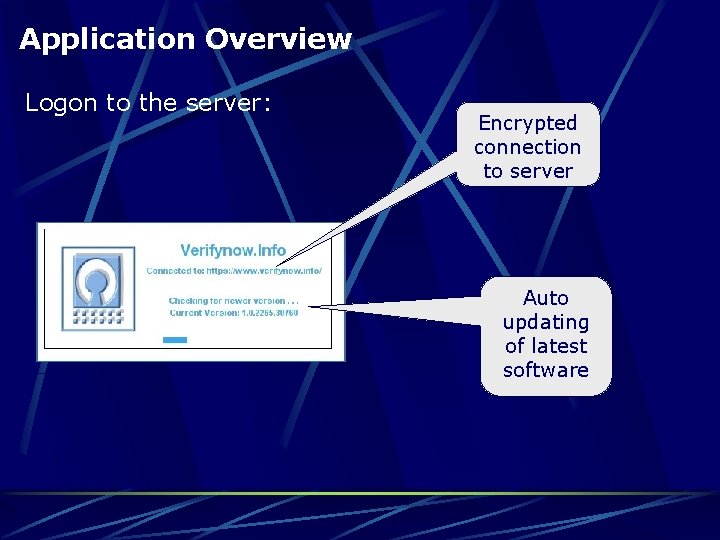
Application Overview Logon to the server: Encrypted connection to server Auto updating of latest software

Application Overview First Login screen:

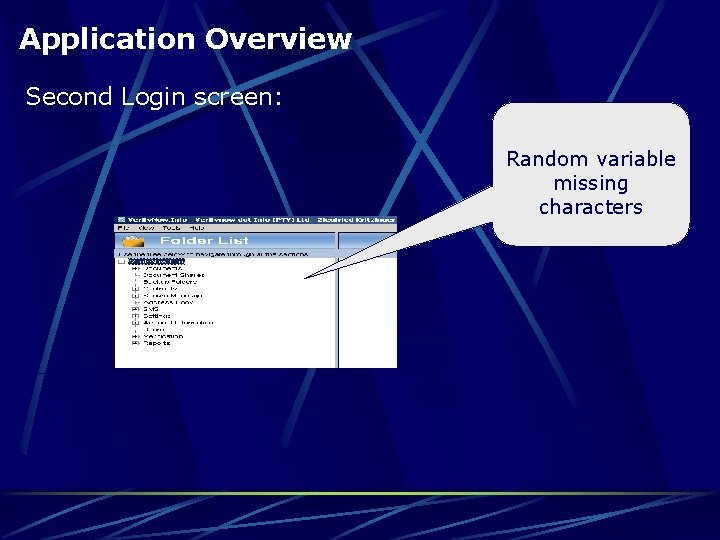
Application Overview Second Login screen: Random variable missing characters

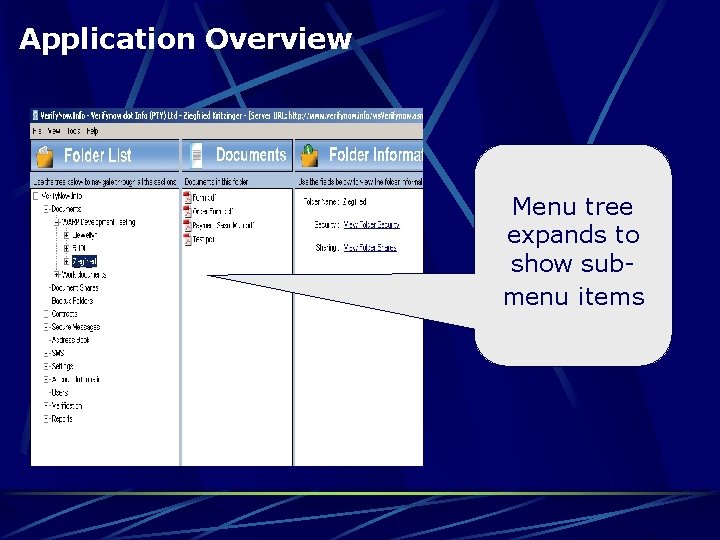
Application Overview Menu tree expands to show submenu items

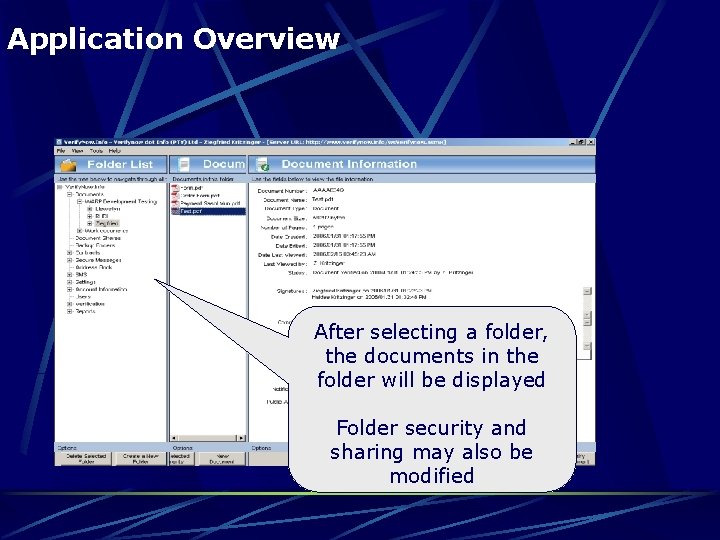
Application Overview After selecting a folder, the documents in the folder will be displayed Folder security and sharing may also be modified

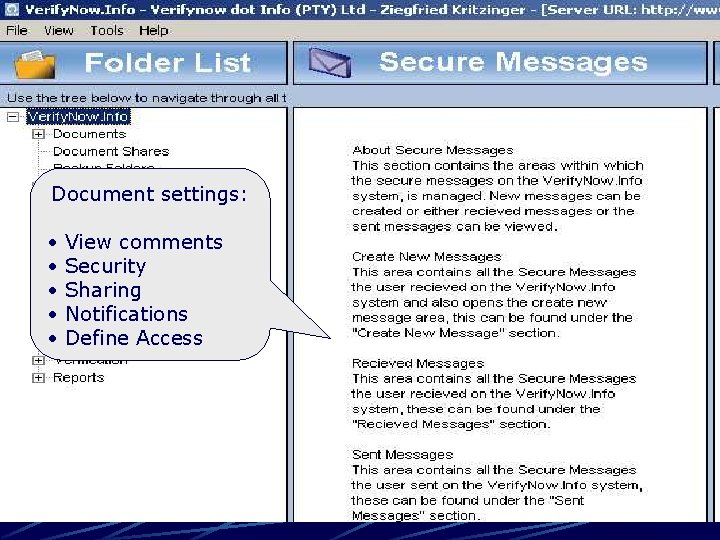
Document settings: • • • View comments Security Sharing Notifications Define Access

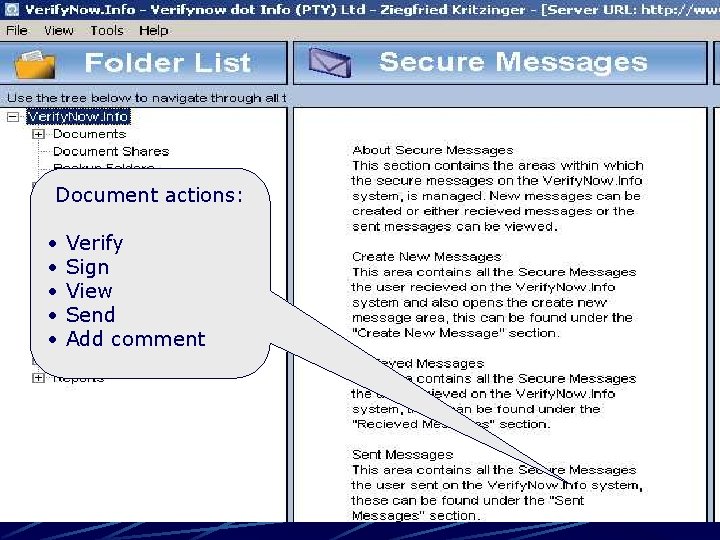
Document actions: • • • Verify Sign View Send Add comment

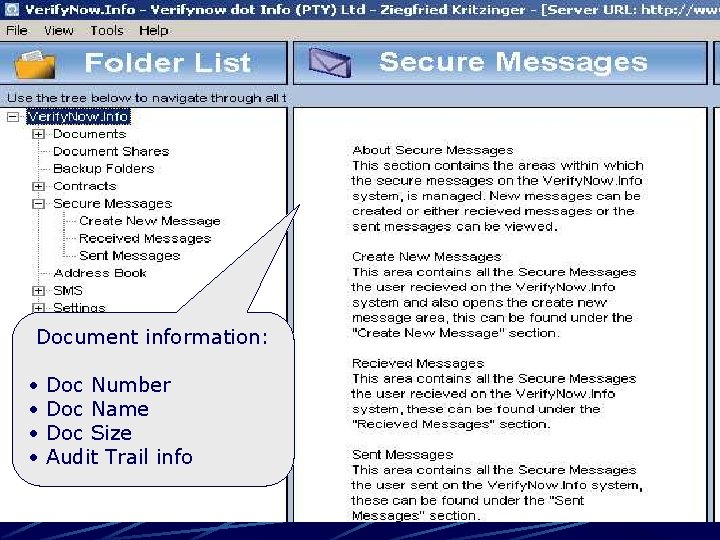
Document information: • • Doc Number Doc Name Doc Size Audit Trail info

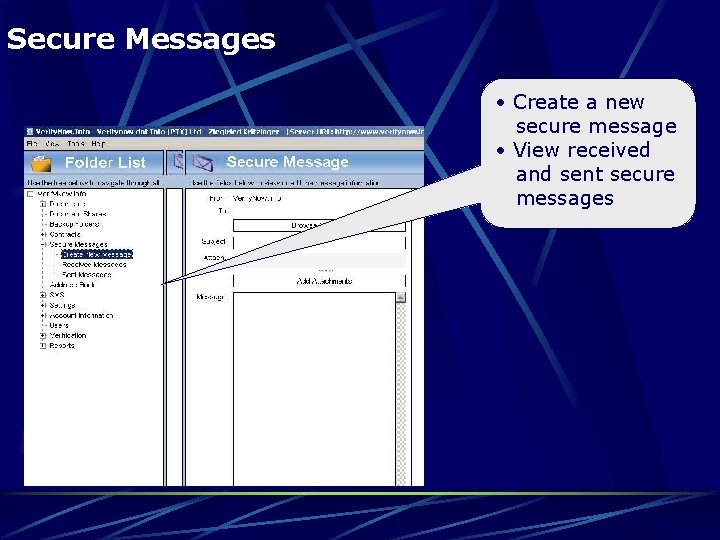
Secure Messages • Create a new secure message • View received and sent secure messages

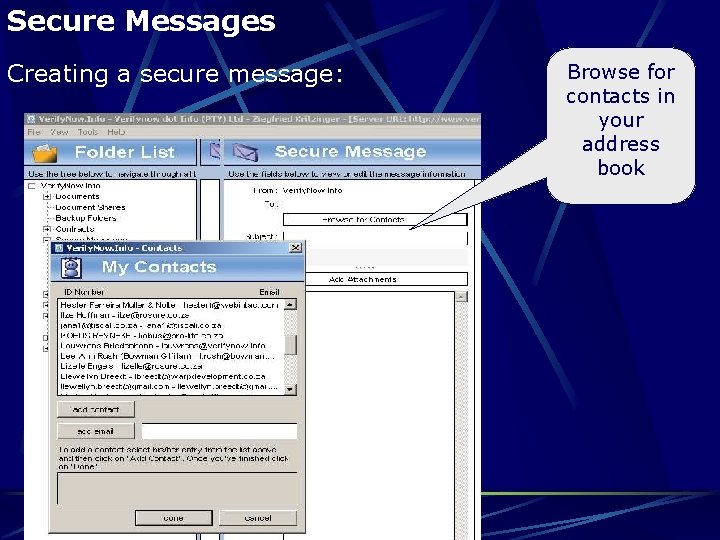
Secure Messages Creating a secure message: Browse for contacts in your address book

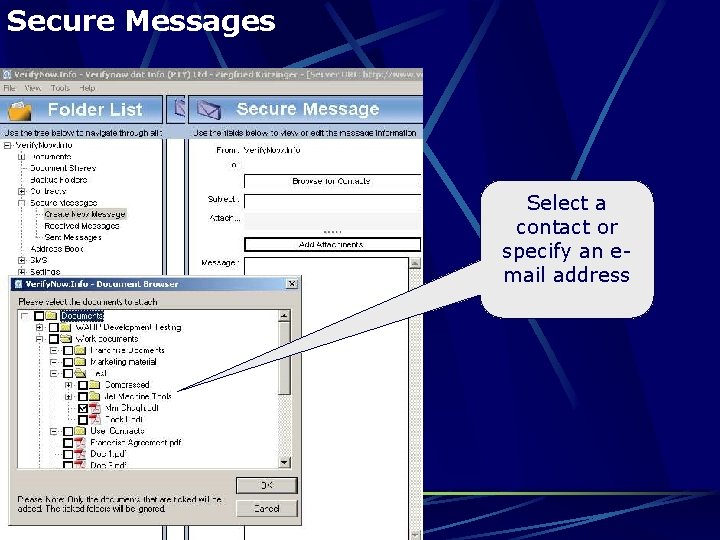
Secure Messages Select a contact or specify an email address

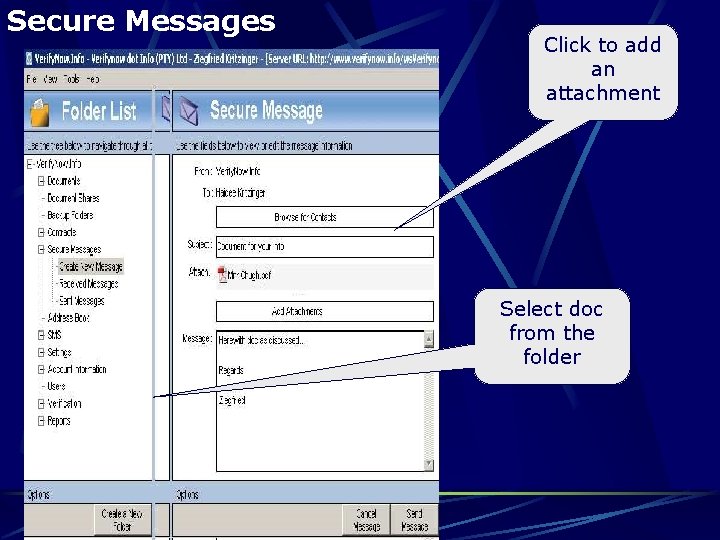
Secure Messages Click to add an attachment Select doc from the folder

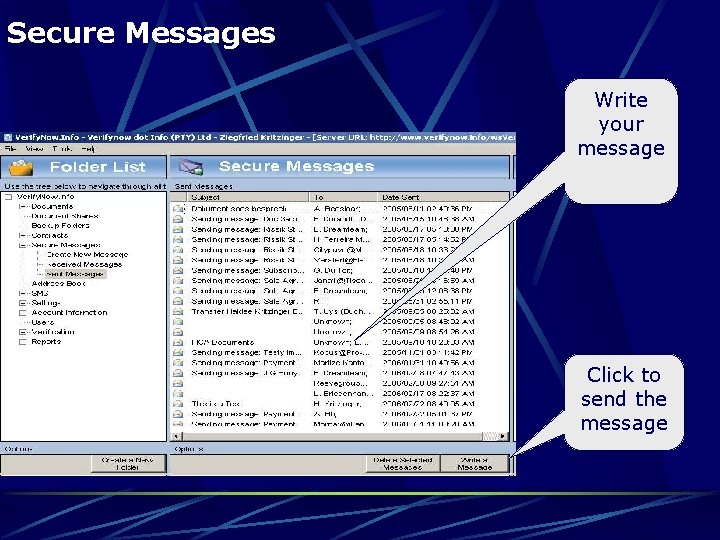
Secure Messages Write your message Click to send the message

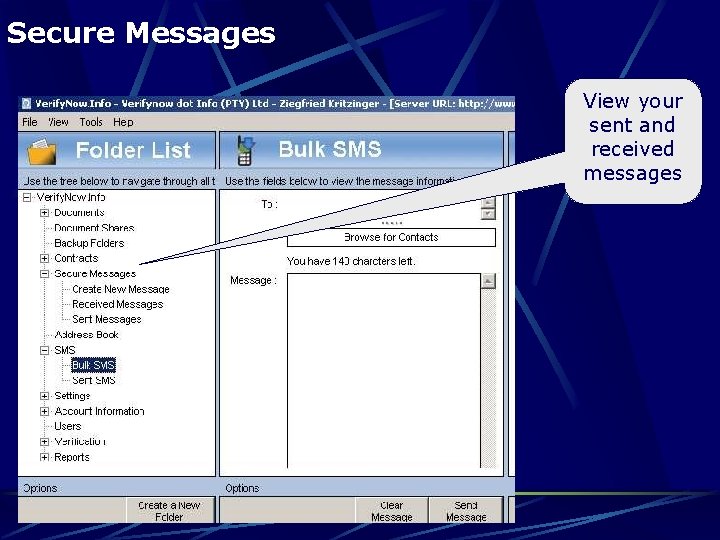
Secure Messages View your sent and received messages

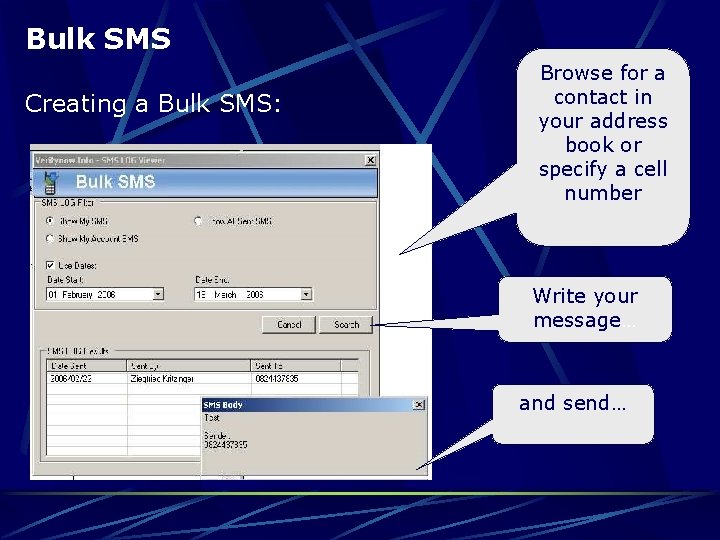
Bulk SMS Creating a Bulk SMS: Browse for a contact in your address book or specify a cell number Write your message… and send…

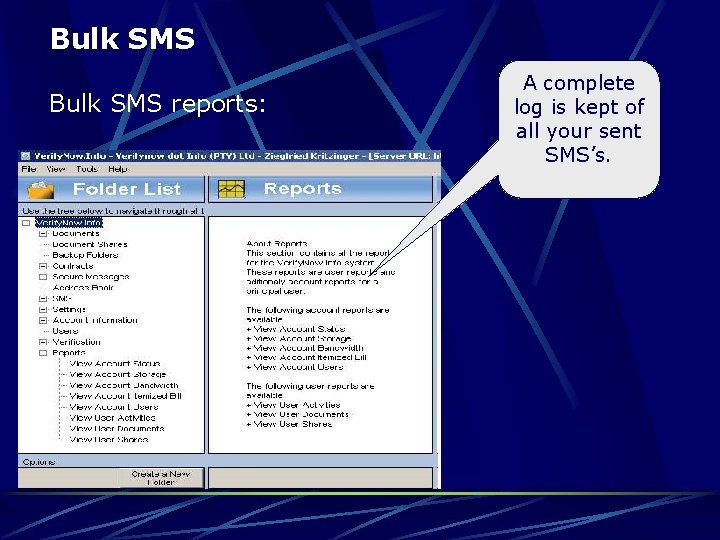
Bulk SMS reports: A complete log is kept of all your sent SMS’s.

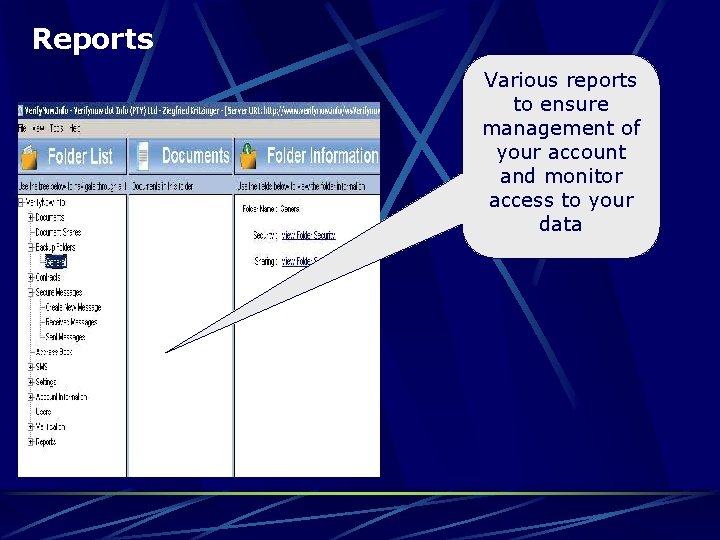
Reports Various reports to ensure management of your account and monitor access to your data

File Backup A special Backup facility to save your files off-site. All security and access control measures are also applicable here.

Why Verifynow? • A South African system, designed for compliance with South African legislation. • Strict control measures to ensure that data communicated or shared with other parties may not be modified, edited or deleted, once uploaded onto the server • User in control of access to his documents and may define security settings for all his data on the server.

Thank You Contact details: Ziegfried Kritzinger 082 443 7835 ziegfried@verifynow. info Lauwrens Briedenhann 083 418 1298 lauwrens@verifynow. info Willie Coetzee 082 455 3350 willie@verifynow. info