Secure Control Systems A Quantitative Risk Management Approach

![05. Approach for Dynamic Control Systems v Dynamic system model (deception attack [13]) n 05. Approach for Dynamic Control Systems v Dynamic system model (deception attack [13]) n](https://slidetodoc.com/presentation_image_h2/61b86ed58c98cf9aa17a90e5693e9aa4/image-13.jpg)
![05. Approach for Dynamic Control Systems v Wireless Quadruple-Tank Process - Plant model [66] 05. Approach for Dynamic Control Systems v Wireless Quadruple-Tank Process - Plant model [66]](https://slidetodoc.com/presentation_image_h2/61b86ed58c98cf9aa17a90e5693e9aa4/image-14.jpg)

- Slides: 19

Secure Control Systems - A Quantitative Risk Management Approach Teixeira Andre, Kin Cheong Sou, Sandberg, H. , Johansson, K. H. IEEE Control Systems Magazine, Feb. 2015 Presented by Kyoungbok Kim 2015. 03. 23

INDEX Introduction Networked Control System Adversary Model Risk Management Framework For Static & Dynamic System cases Conclusion 2

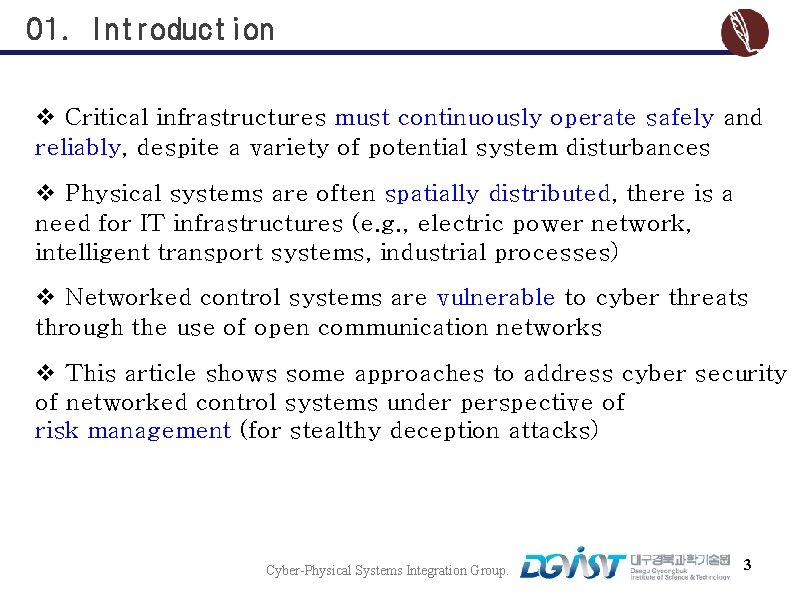
01. Introduction v Critical infrastructures must continuously operate safely and reliably, despite a variety of potential system disturbances v Physical systems are often spatially distributed, there is a need for IT infrastructures (e. g. , electric power network, intelligent transport systems, industrial processes) v Networked control systems are vulnerable to cyber threats through the use of open communication networks v This article shows some approaches to address cyber security of networked control systems under perspective of risk management (for stealthy deception attacks) Cyber-Physical Systems Integration Group. 3

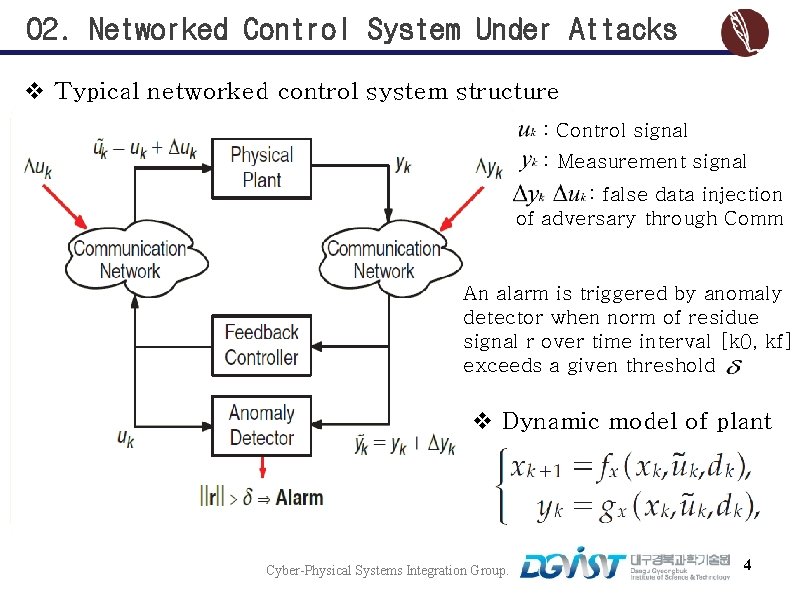
02. Networked Control System Under Attacks v Typical networked control system structure : Control signal : Measurement signal : false data injection of adversary through Comm An alarm is triggered by anomaly detector when norm of residue signal r over time interval [k 0, kf] exceeds a given threshold v Dynamic model of plant Cyber-Physical Systems Integration Group. 4

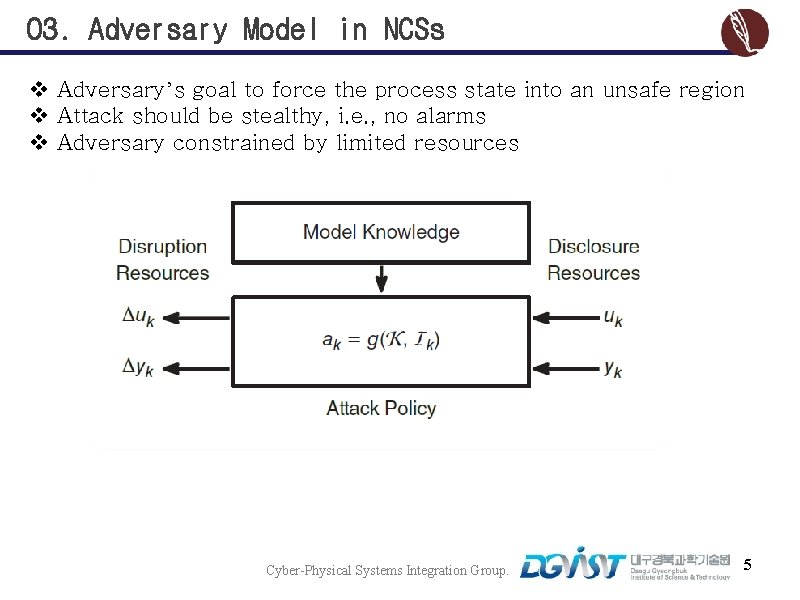
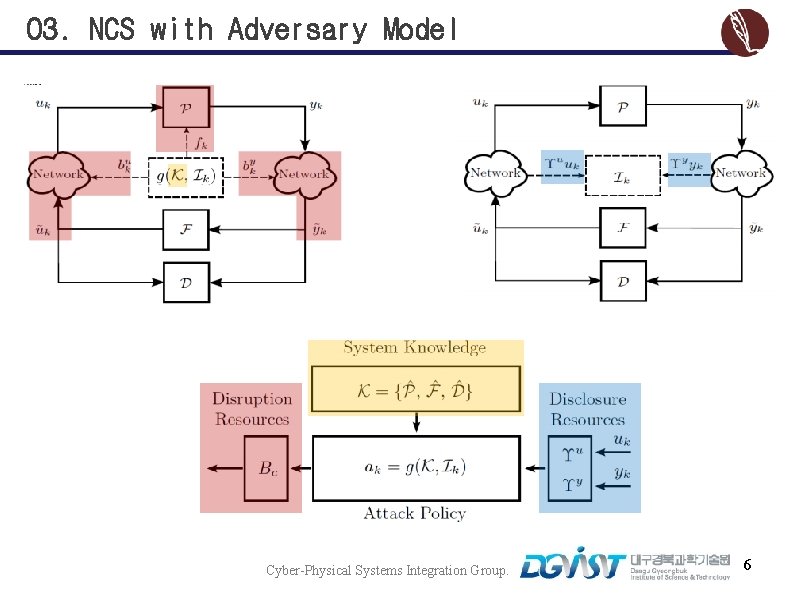
03. Adversary Model in NCSs v Adversary’s goal to force the process state into an unsafe region v Attack should be stealthy, i. e. , no alarms v Adversary constrained by limited resources Cyber-Physical Systems Integration Group. 5

03. NCS with Adversary Model Cyber-Physical Systems Integration Group. 6

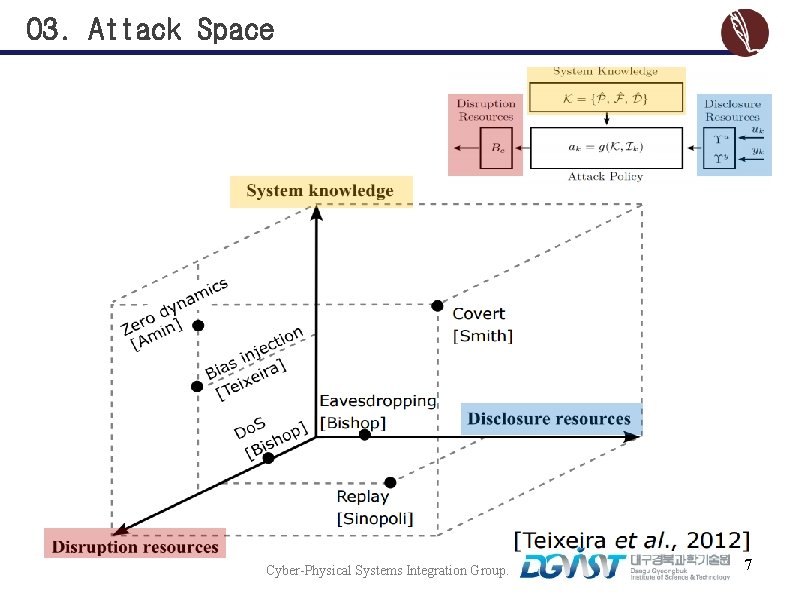
03. Attack Space Cyber-Physical Systems Integration Group. 7

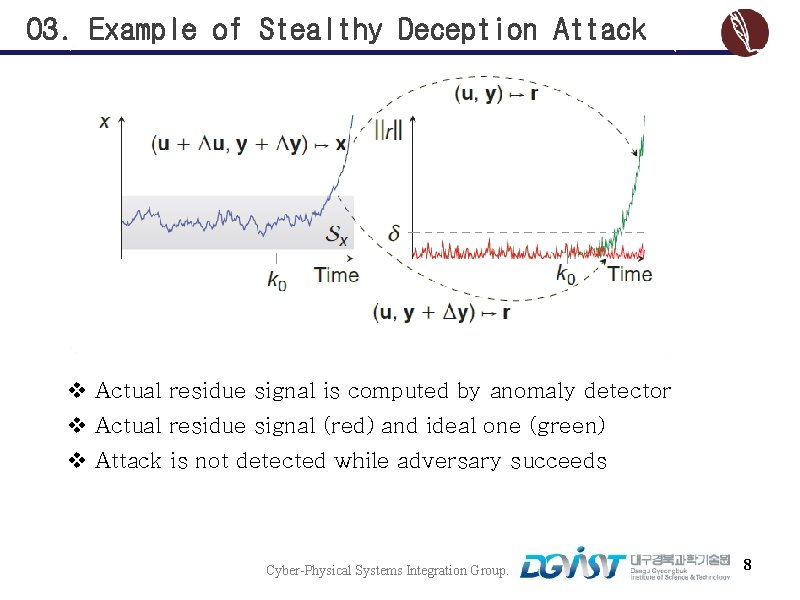
03. Example of Stealthy Deception Attack v Actual residue signal is computed by anomaly detector v Actual residue signal (red) and ideal one (green) v Attack is not detected while adversary succeeds Cyber-Physical Systems Integration Group. 8

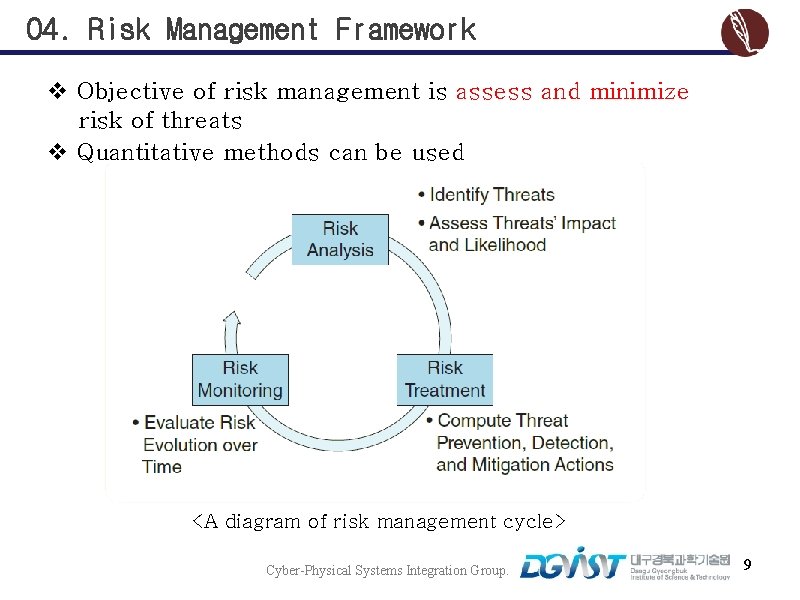
04. Risk Management Framework v Objective of risk management is assess and minimize risk of threats v Quantitative methods can be used <A diagram of risk management cycle> Cyber-Physical Systems Integration Group. 9

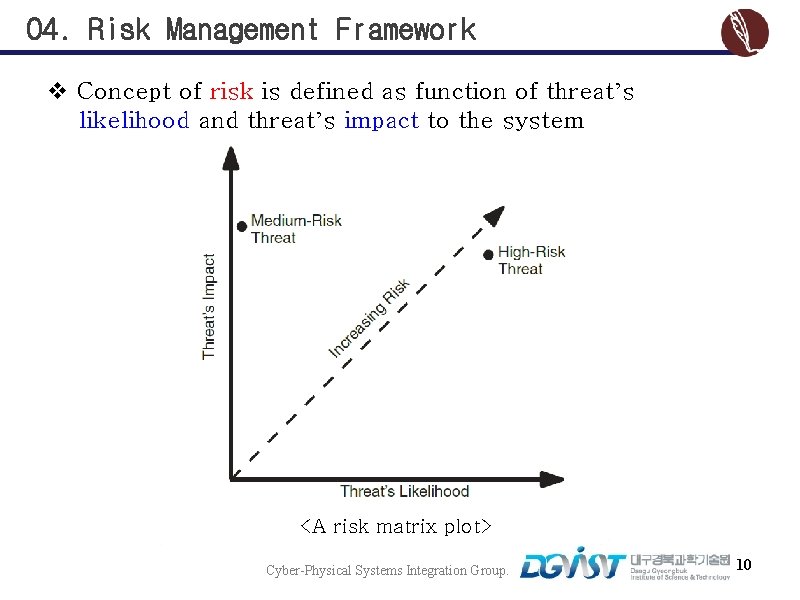
04. Risk Management Framework v Concept of risk is defined as function of threat’s likelihood and threat’s impact to the system <A risk matrix plot> Cyber-Physical Systems Integration Group. 10

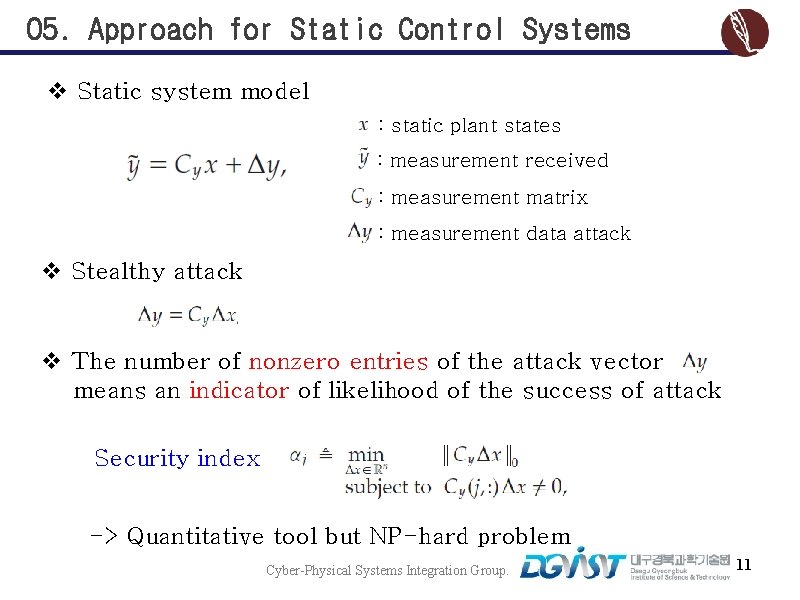
05. Approach for Static Control Systems v Static system model : static plant states : measurement received : measurement matrix : measurement data attack v Stealthy attack v The number of nonzero entries of the attack vector means an indicator of likelihood of the success of attack Security index -> Quantitative tool but NP-hard problem Cyber-Physical Systems Integration Group. 11

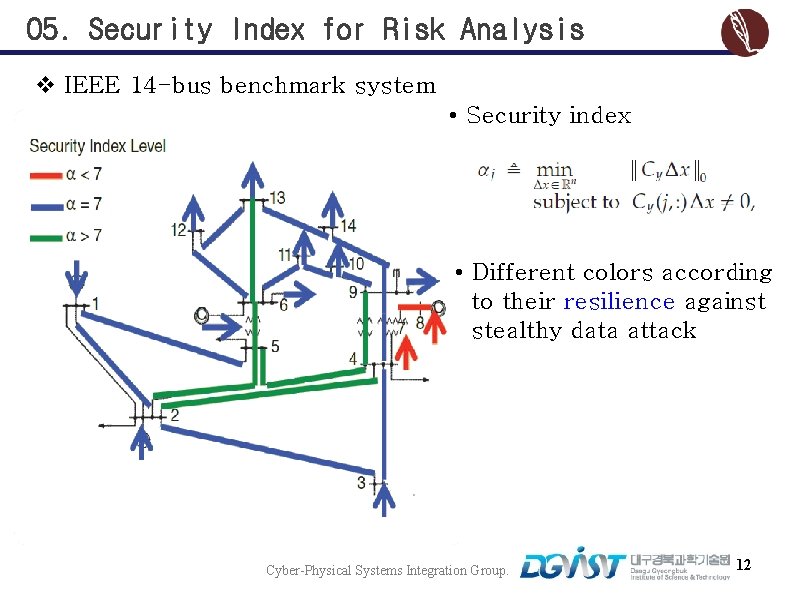
05. Security Index for Risk Analysis v IEEE 14 -bus benchmark system • Security index • Different colors according to their resilience against stealthy data attack Cyber-Physical Systems Integration Group. 12
![05 Approach for Dynamic Control Systems v Dynamic system model deception attack 13 n 05. Approach for Dynamic Control Systems v Dynamic system model (deception attack [13]) n](https://slidetodoc.com/presentation_image_h2/61b86ed58c98cf9aa17a90e5693e9aa4/image-13.jpg)
05. Approach for Dynamic Control Systems v Dynamic system model (deception attack [13]) n : system state x : attack signals r : residue v Maximum Impact, Minimum-Resource Attack : Attack impact : number of resource used in attack : attack signal : used resource if is nonzero Cyber-Physical Systems Integration Group. 13
![05 Approach for Dynamic Control Systems v Wireless QuadrupleTank Process Plant model 66 05. Approach for Dynamic Control Systems v Wireless Quadruple-Tank Process - Plant model [66]](https://slidetodoc.com/presentation_image_h2/61b86ed58c98cf9aa17a90e5693e9aa4/image-14.jpg)
05. Approach for Dynamic Control Systems v Wireless Quadruple-Tank Process - Plant model [66] • 2 actuators and 2 measurements • LQG (Linear-quadratic-Gaussian) Controller • Kalman filter based anomaly detector Cyber-Physical Systems Integration Group. 14

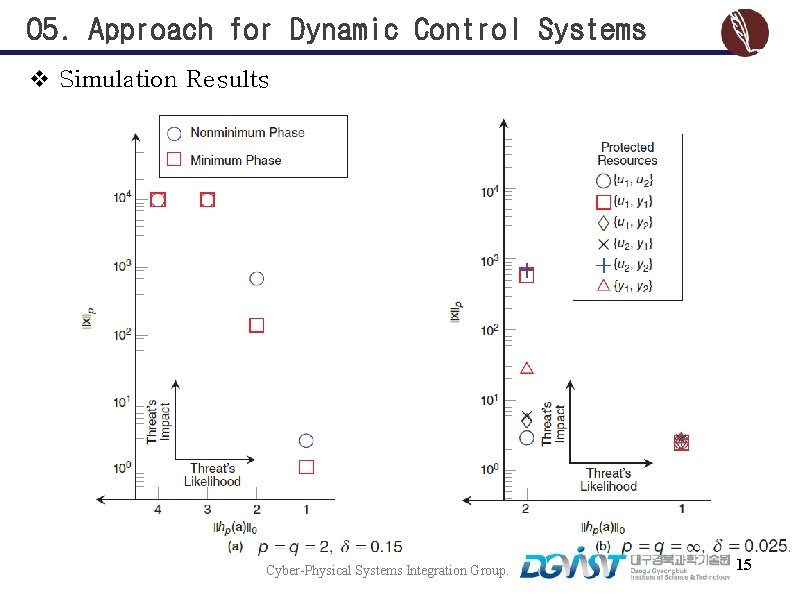
05. Approach for Dynamic Control Systems v Simulation Results Cyber-Physical Systems Integration Group. 15

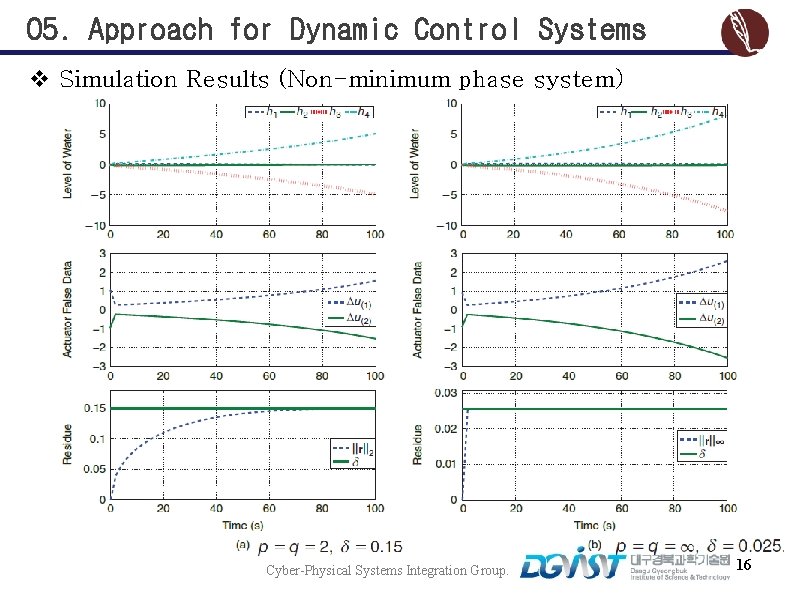
05. Approach for Dynamic Control Systems v Simulation Results (Non-minimum phase system) Cyber-Physical Systems Integration Group. 16

06. Conclusions v Networked control systems have vulnerabilities according to the use of IT infrastructures v Quantitative risk management is needed considering threat’s likelihood and impact v Adversary model v Approach for Static system & Dynamic system v Possible to extend this work under noise and uncertain communication channel Cyber-Physical Systems Integration Group. 17

Thank you!

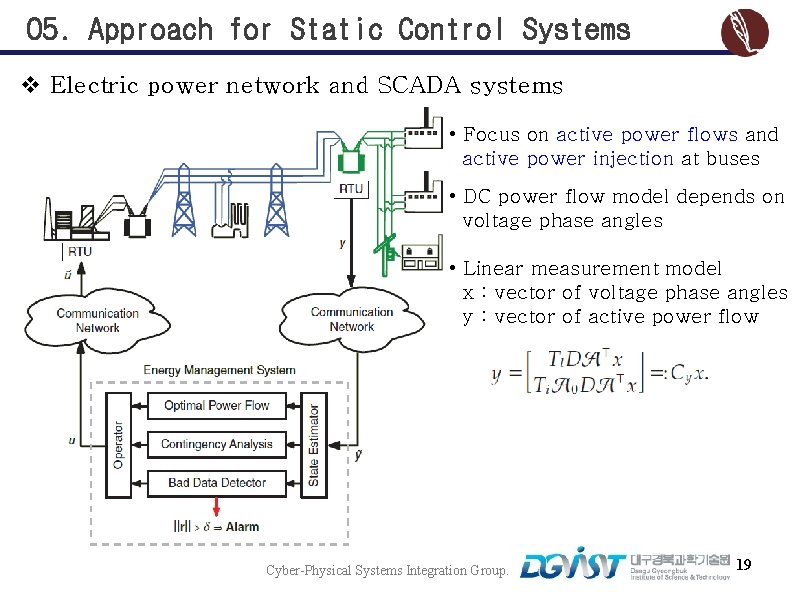
05. Approach for Static Control Systems v Electric power network and SCADA systems • Focus on active power flows and active power injection at buses • DC power flow model depends on voltage phase angles • Linear measurement model x : vector of voltage phase angles y : vector of active power flow Cyber-Physical Systems Integration Group. 19