Secure Computation of the kth Ranked Element Gagan




![Secure Function Evaluation [Yao, GMW, BGW, CCD] • F(x, y) – A public function. Secure Function Evaluation [Yao, GMW, BGW, CCD] • F(x, y) – A public function.](https://slidetodoc.com/presentation_image_h/7fd2695cca6dae5718dbc7823703d2e8/image-8.jpg)








- Slides: 29

Secure Computation of the k’th Ranked Element Gagan Aggarwal Stanford University Joint work with Nina Mishra and Benny Pinkas, HP Labs 1

A story … I bet the dumbest student in Gryffindor has a higher IQ than the median IQ of all students in the school. Let us compute it. . . We can do “Secure function evaluation” … But you don’t even know what the median IQ is … But, what about privacy of the students. This is all “theory”. It can’t be efficient. 2

Rising Need for Privacy Many opportunities of interaction between institutions and agencies holding sensitive data. Privacy cannot be sacrificed. I. e. different agencies might hold data which they are not allowed to share. A need for protocols to evaluate functions while preserving privacy of data. 3

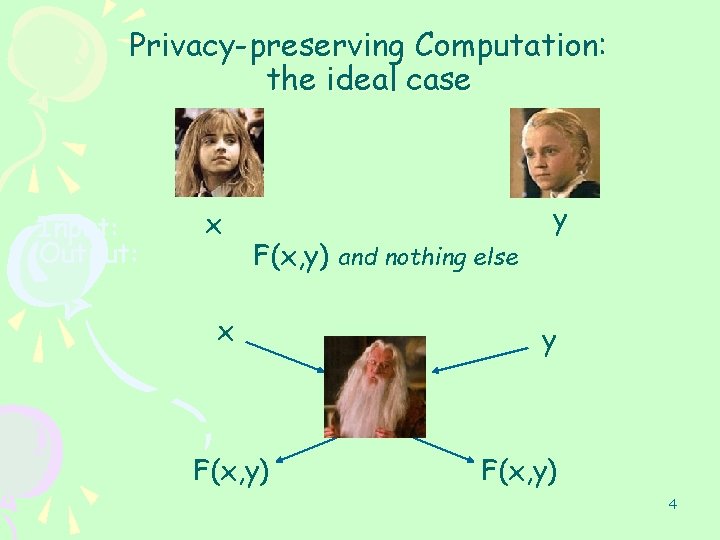
Privacy-preserving Computation: the ideal case Input: Output: x F(x, y) and nothing else x F(x, y) y y F(x, y) 4

Trusted third parties are rare x F(x, y) y F(x, y) • Run a protocol to evaluate F(x, y) without a trusted party. • Two kinds of adversaries: • Semi-honest – Follows the protocol, but is curious to learn more than F(x, y). • Malicious - Might do anything. 5

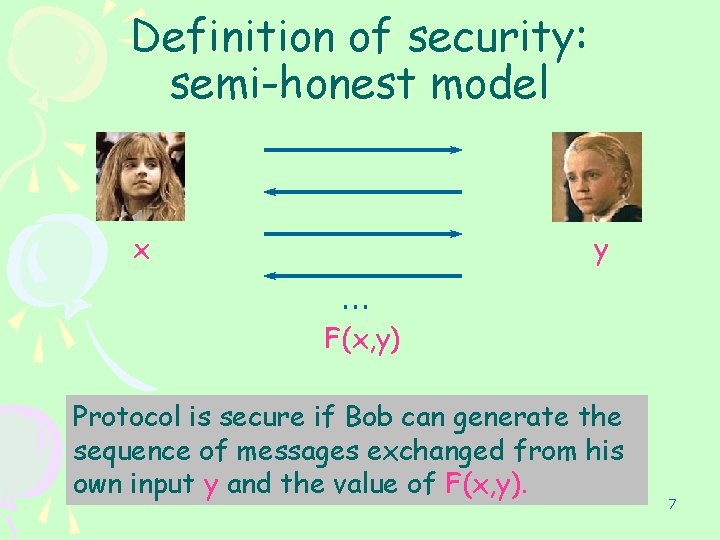
Definition of security: semi-honest model x y … F(x, y) Protocol is secure if Bob can generate the sequence of messages exchanged from his own input y and the value of F(x, y). 7

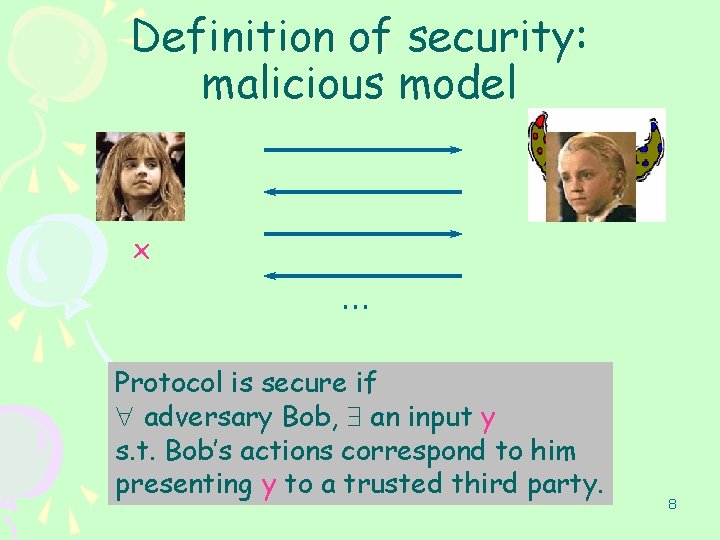
Definition of security: malicious model x … Protocol is secure if " adversary Bob, an input y s. t. Bob’s actions correspond to him presenting y to a trusted third party. 8
![Secure Function Evaluation Yao GMW BGW CCD Fx y A public function Secure Function Evaluation [Yao, GMW, BGW, CCD] • F(x, y) – A public function.](https://slidetodoc.com/presentation_image_h/7fd2695cca6dae5718dbc7823703d2e8/image-8.jpg)
Secure Function Evaluation [Yao, GMW, BGW, CCD] • F(x, y) – A public function. • Represented as a Boolean circuit C(x, y). Input: Output: x C(x, y) and nothing else C(x, y) y and nothing else Implementation: • O(|X|) “oblivious transfers”. • O(|C|) communication. • Pretty efficient for small circuits! e. g. Is x > y? (Millionaire’s problem) 9

Some useful primitives • Useful to have efficient solutions for simple primitives. • Let X and Y be sets of elements: – X Y (first talk) – Statistics over X Y: • Max, Min, Average, Median, kthranked element. 10

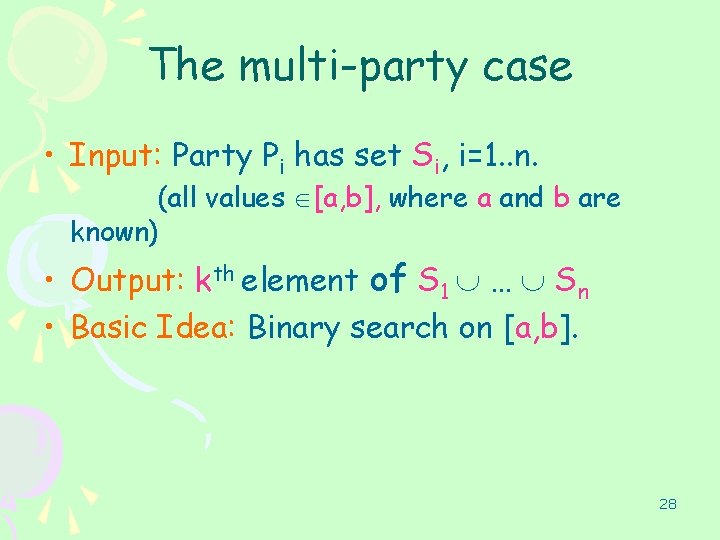
kth-ranked element • Inputs: – Alice: SA Bob: SB – Large sets of unique items (є S). – The rank k • Could depend on the size of input datasets. • Median: k = (|SA| + |SB|) / 2 • Output: – x SA SB s. t. x has k-1 elements smaller than it. 11

Results Finding the kth ranked item (D=|domain|) – Two-party: reduction to log k secure comparisons of log D bit numbers. • log k rounds * O(log D) – Multi-party: reduction to log D simple computations with log D bit numbers. • log D rounds * O(log D) – Also, security against malicious parties. – Can hide the size of the datasets. 14

Related work • Lower bound: Ω(log D) – From communication complexity. • Generic constructions – Using circuits [Yao …]: • Overhead at least linear in k. – Naor-Nissim: • Overhead of Ω(D). 15

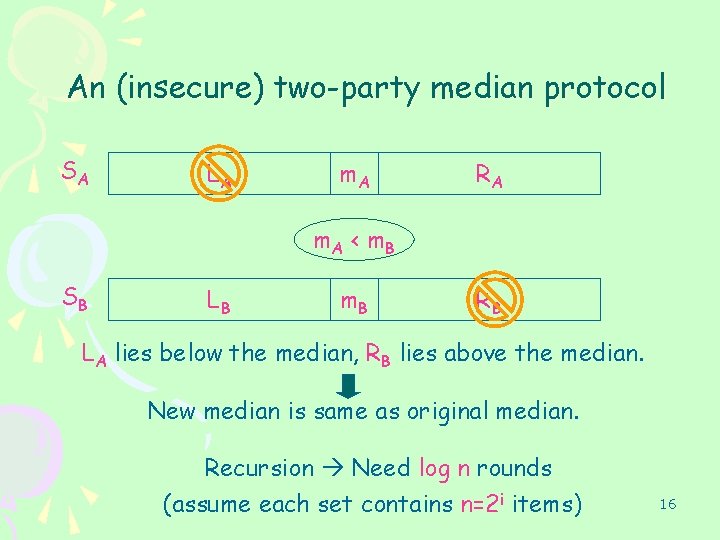
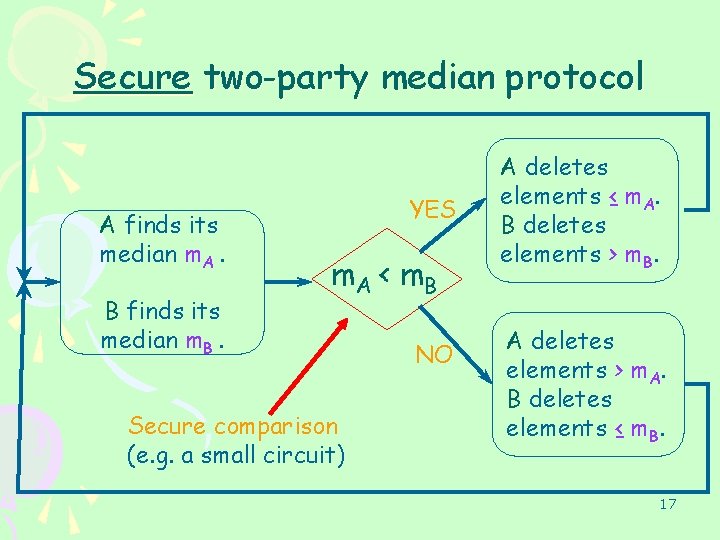
An (insecure) two-party median protocol SA LA m. A RA m. A < m. B SB LB m. B RB LA lies below the median, RB lies above the median. New median is same as original median. Recursion Need log n rounds (assume each set contains n=2 i items) 16

Secure two-party median protocol A finds its median m. A. B finds its median m. B. YES m. A < m. B Secure comparison (e. g. a small circuit) NO A deletes elements ≤ m. A. B deletes elements > m. B. A deletes elements > m. A. B deletes elements ≤ m. B. 17

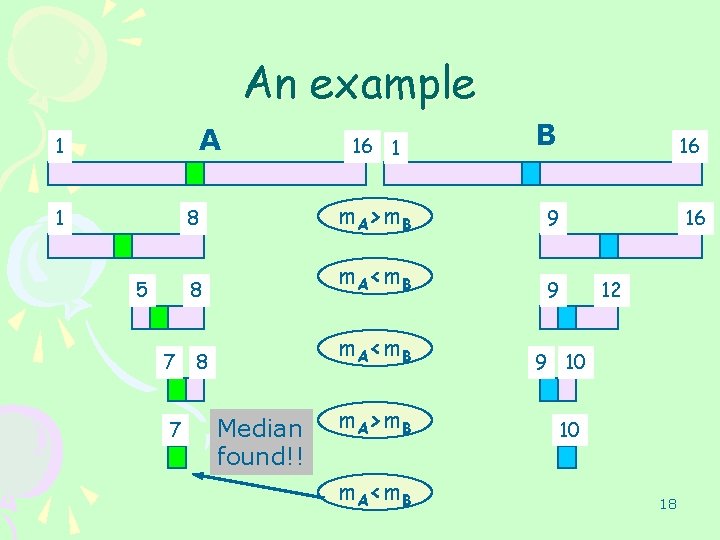
An example A 1 1 5 7 7 16 1 B 16 16 8 m. A>m. B 9 8 m. A<m. B 9 10 m. A>m. B 10 Median found!! m. A<m. B 12 18

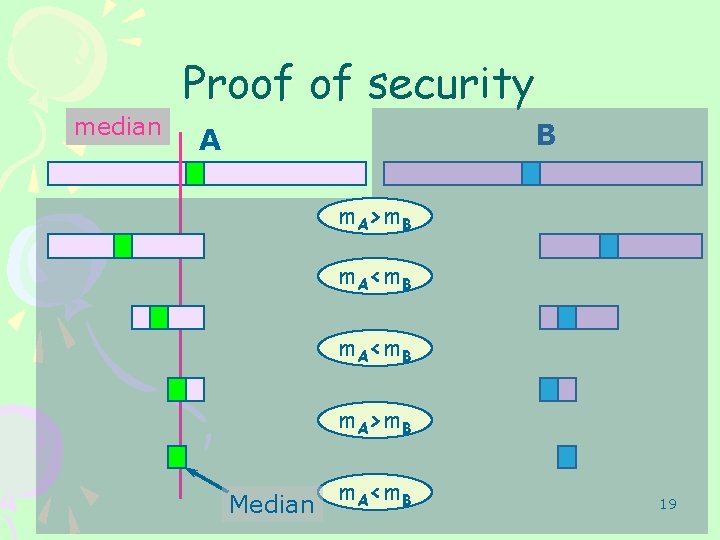
median Proof of security B A m. A>m. B m. A<m. B m. A>m. B Median m. A<m. B 19

Still to come… • Security against malicious parties. • Adapt the median protocol for arbitrary k and arbitrary input set size. • Hide the size of the datasets. • kth element for multi-party scenario. 20

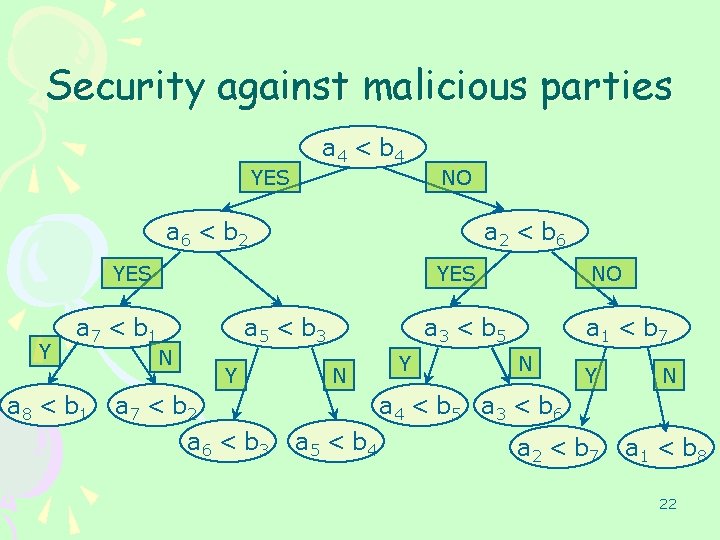
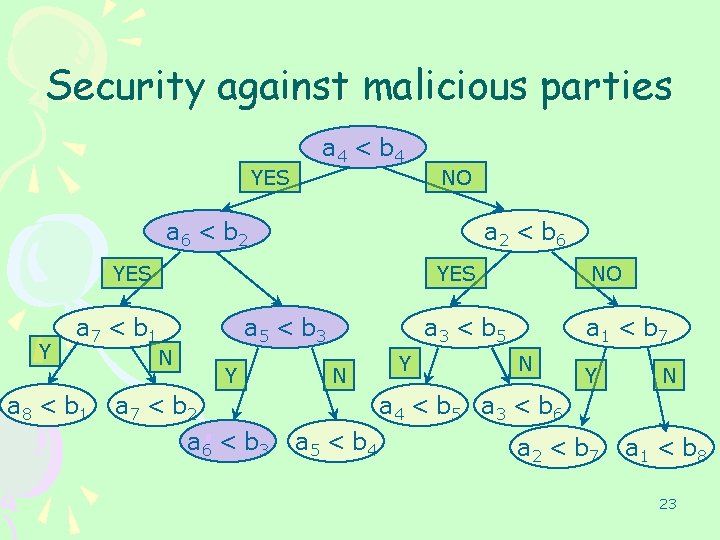
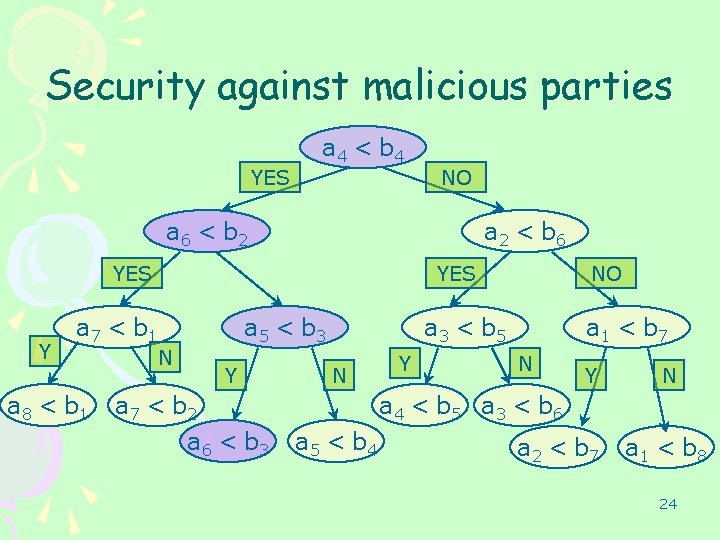
Security against malicious parties • • – – Comparisons secure against malicious parties. Verify that parties’ inputs to comparisons are consistent. I. e. , prevent Round 1: m. A = 1000. Is told to delete all x>1000. Round 2: m. A = 1100… Solution: Each round sends secure “state” to next round (i. e. , boundaries for parties’ inputs). Implement “reactive computation” [C, CLOS]. Can implement in a single circuit. Efficient security against malicious parties. 21

Security against malicious parties YES a 4 < b 4 NO a 6 < b 2 a 2 < b 6 YES Y YES a 7 < b 1 a 8 < b 1 N a 5 < b 3 Y a 7 < b 2 a 6 < b 3 NO a 3 < b 5 N Y a 1 < b 7 N Y N a 4 < b 5 a 3 < b 6 a 5 < b 4 a 2 < b 7 a 1 < b 8 22

Security against malicious parties YES a 4 < b 4 NO a 6 < b 2 a 2 < b 6 YES Y YES a 7 < b 1 a 8 < b 1 N a 5 < b 3 Y a 7 < b 2 a 6 < b 3 NO a 3 < b 5 N Y a 1 < b 7 N Y N a 4 < b 5 a 3 < b 6 a 5 < b 4 a 2 < b 7 a 1 < b 8 23

Security against malicious parties YES a 4 < b 4 NO a 6 < b 2 a 2 < b 6 YES Y YES a 7 < b 1 a 8 < b 1 N a 5 < b 3 Y a 7 < b 2 a 6 < b 3 NO a 3 < b 5 N Y a 1 < b 7 N Y N a 4 < b 5 a 3 < b 6 a 5 < b 4 a 2 < b 7 a 1 < b 8 24

Security against malicious parties • An adversary is fully defined by the input ai’s it gives for each of the nodes of this tree. • These (consistent) ai’s form an input x which can be used with F(x, y) to generate a transcript. 25

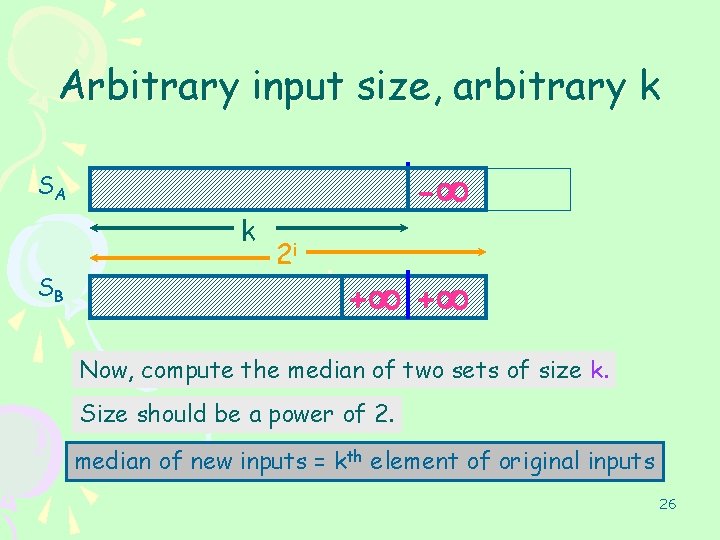
Arbitrary input size, arbitrary k - SA k SB 2 i + + Now, compute the median of two sets of size k. Size should be a power of 2. median of new inputs = kth element of original inputs 26

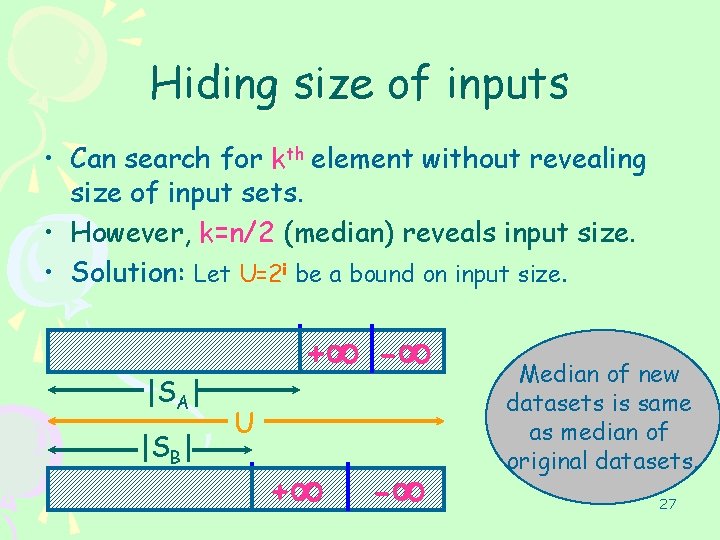
Hiding size of inputs • Can search for kth element without revealing size of input sets. • However, k=n/2 (median) reveals input size. • Solution: Let U=2 i be a bound on input size. |SA| |SB| + - U + - Median of new datasets is same as median of original datasets. 27

The multi-party case • Input: Party Pi has set Si, i=1. . n. (all values [a, b], where a and b are known) • Output: kth element of S 1 … Sn • Basic Idea: Binary search on [a, b]. 28

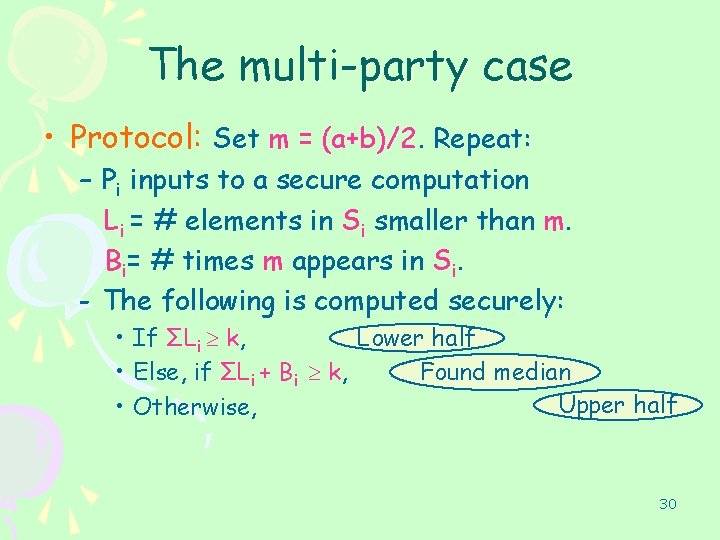
The multi-party case • Protocol: Set m = (a+b)/2. Repeat: – Pi inputs to a secure computation Li = # elements in Si smaller than m. Bi= # times m appears in Si. - The following is computed securely: • If ΣLi k, Lower half Found median • Else, if ΣLi + Bi k, Upper half • Otherwise, 30

The multi-party case • Can be made secure for malicious case. – Using consistency checks. • Works for two-party case. – Can be used for non-distinct elements. 31

Summary • Efficient secure computation of the median. – Two-party: log k rounds * O(log D) – Multi-party: log D rounds * O(log D) – Communication overhead is very close to the communication complexity lower bound of log D bits. • Malicious case is efficient too. – Do not use generic tools. – Instead, we implement simple consistency checks to get security against malicious parties. 32

Thanks for your attention! 33