Secure and Serverless RFID Authentication and Search Protocols














- Slides: 17

Secure and Serverless RFID Authentication and Search Protocols Authors: Chiu C. Tan, Bo Sheng, and Qun Li Sources: IEEE Transaction on Wireless Communication, vol. 7, no. 4, pp. 1400 -1407, 2008 Speaker: C. H. Wei Date: 2009. 10. 1 1

Outline • • • The problem Authentication protocol Secure search protocol Conclusion Comments 2

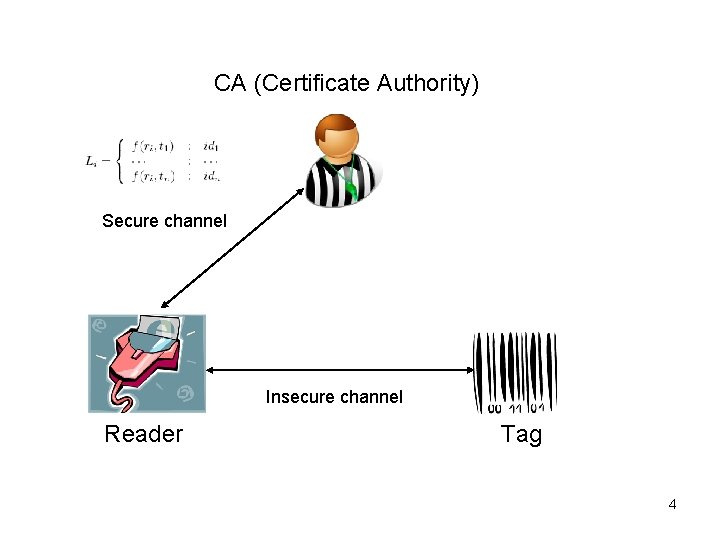
The Problem • Traditional RFID System is based on Central database. – It is not useful in other scenario – The truck driver is unable to connect with the central database to authenticate the goods • Serverless(無主機) RFID 3

CA (Certificate Authority) Secure channel Insecure channel Reader Tag 4

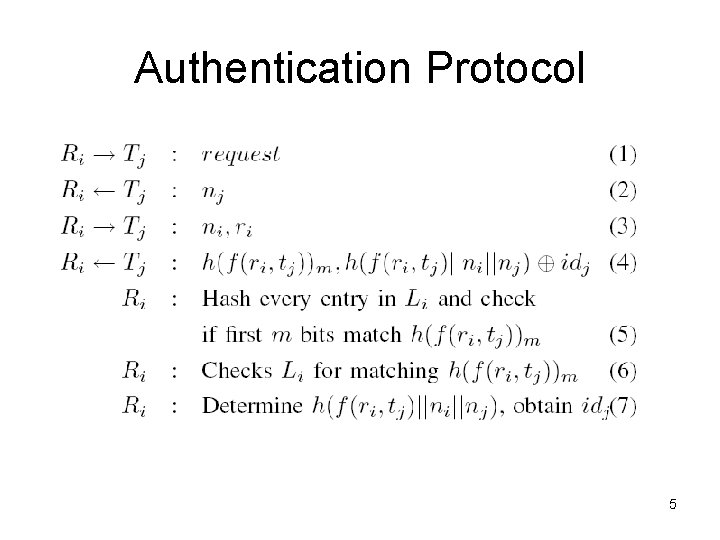
Authentication Protocol 5

Security Analysis • Basic Privacy – Assume that adversary has a list of targeted RFID tags – Tag generates a new response at each time – Adversary cannot identify which RFID tag is on his list • Tracking – Adversary cannot predict the random nj generated each time 6

Security Analysis (cont. ) • Cloning – Adversary want to replace a fake RFID tag – Adversary cannot predict ni • Eavesdropping – Adversary learns ri, nj, – Adversary does not know ; therefore, it cannot derive the correct hash result 7

Security Analysis (cont. ) • Physical attack – Adversary compromises the reader • Attacker know the contents of Li • The goal is to prevent attacker counterfeit tag that can fool another reader – Adversary compromises the Tag • Attacker know any information that reader passes to tag • The goal is to prevent attacker creating another tag that can fool reader 8

Security Analysis (cont. ) • Denial of Service (Do. S) – Adversary sends a large number of requests to the backend server to overwhelm the server. • Reader only needs to contact the server once to obtain an access list. 9

Secure search protocol • A pharmacist wanting to find a particular drug can broadcast his query and receive an answer 10

Search protocol improvement Ⅰ • To force the reader use a different random number nr for each new query 11

Search protocol improvement Ⅱ • To avoid the condition where replying to a query can be used to identify a tag • Multiple tags share the same m bits, attacker cannot infer any unique information from the reply 12

Search protocol improvement Ⅲ • The solution is to use noise to mask the reply 13


Comments • Advantage – Serverless RFID 的概念,在現實環境中確實是有需 要 – 本篇的解法把原本存在Server端資料,透過可靠的 certificate authority (CA) copy一份在reader • Disadvantage – 本篇所建議的secure authentication protocol是假設 reader和tag之間是insecure,和之前學者研究的傳統 RFID的authentication protocol並無差別 – 無法抵抗Tracking因為每次傳送的 都一樣 15

Comments • Mobile RFID – 無法連結上網 (將資料庫存在mobile reader) • 假設 insecure channel between the reader and the tag • 任何人拿到mobile reader都可以去讀取資料,因此 確認user的身份變的重要 • 除了預先將資料庫儲存在mobile reader,要使用 mobile reader要先輸入password再進行讀取tag的 動作 16

Comments • Mobile RFID – 無線網路連結上網 • 假設 insecure channel between the server and the reader 和insecure channel between the reader and the tag • Mobile RFID reader, tag和Sensor node, 基地台有 點相似,都是需要lightweight computation和無線傳 輸,可以改良wireless sensor network相關安全機 制 • 是否也可以考慮smart card + mobile reader – Registration phase – Login phase – Verification phase 17