Secret sharing based reversible data hiding in encrypted

Secret sharing based reversible data hiding in encrypted images with multiple data-hiders Authors: Bing Chen, Wei Lu, Jiwu Huang, Jian Weng, Yicong Zhou Source: IEEETransactions on Dependable and Secure Computing , DOI 10. 1109/TDSC. 2020. 3011923 Reporter: Si. Sheng Chen Date: 2020. 9. 3 1

Outline • Introduction • Related works • Proposed scheme • Experimental results • Conclusions and comments 2
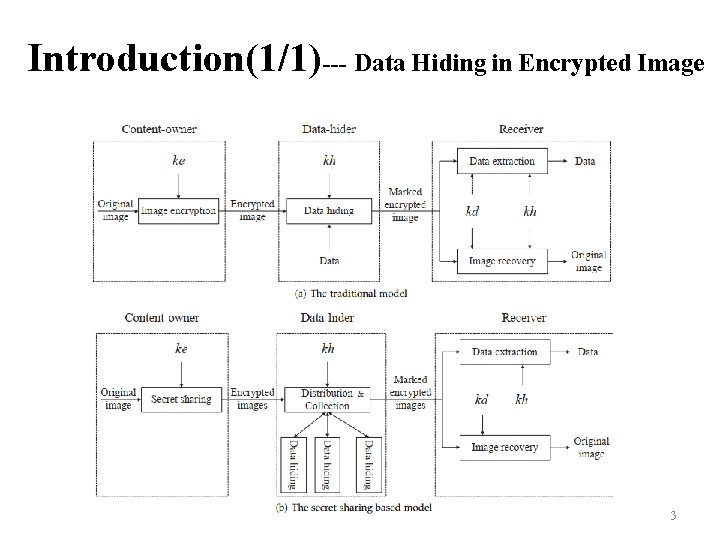
Introduction(1/1)--- Data Hiding in Encrypted Image 3
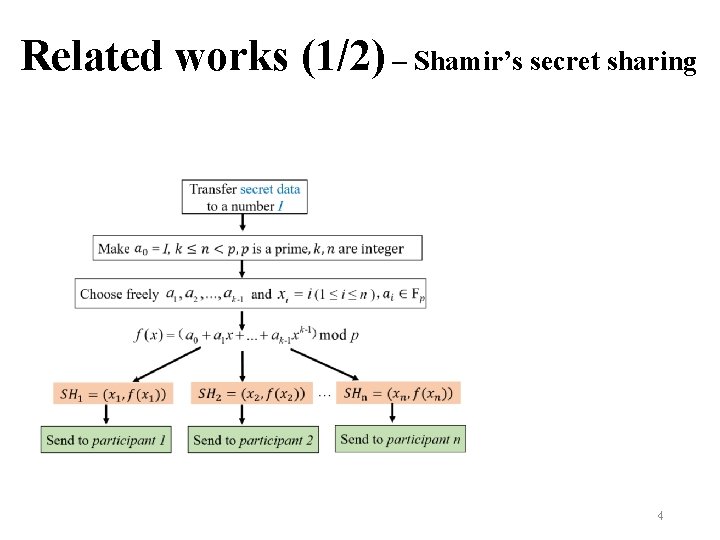
Related works (1/2) – Shamir’s secret sharing 4
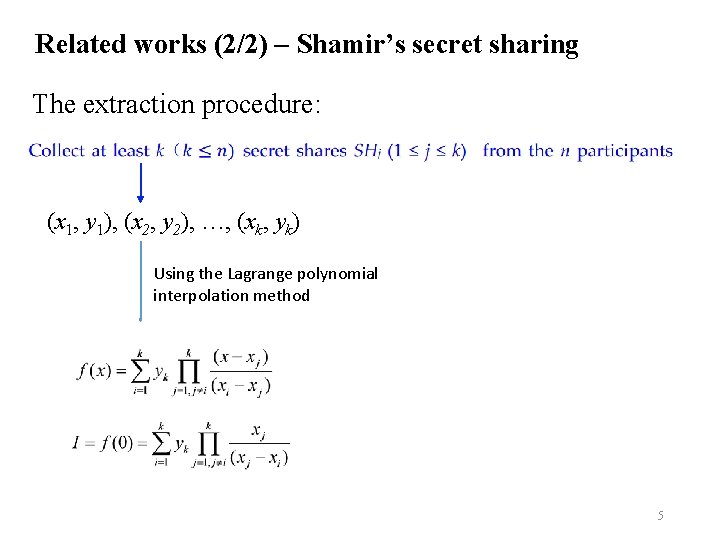
Related works (2/2) – Shamir’s secret sharing The extraction procedure: (x 1, y 1), (x 2, y 2), …, (xk, yk) Using the Lagrange polynomial interpolation method 5
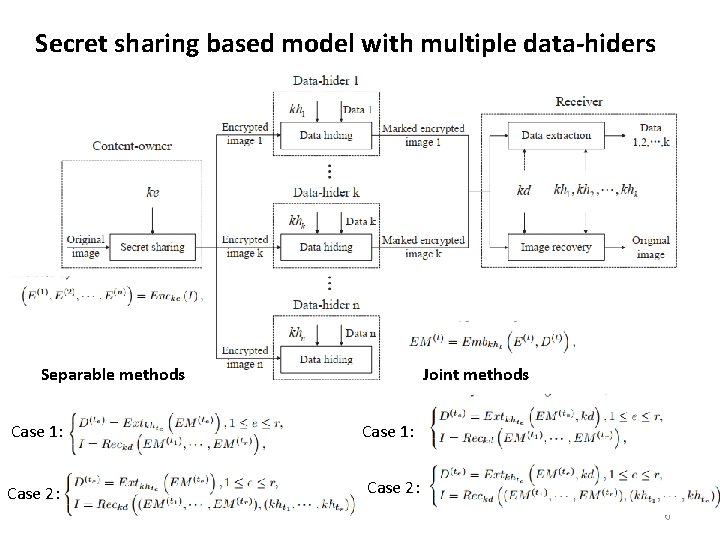
Secret sharing based model with multiple data-hiders Separable methods Case 1: Case 2: Joint methods Case 1: Case 2: 6
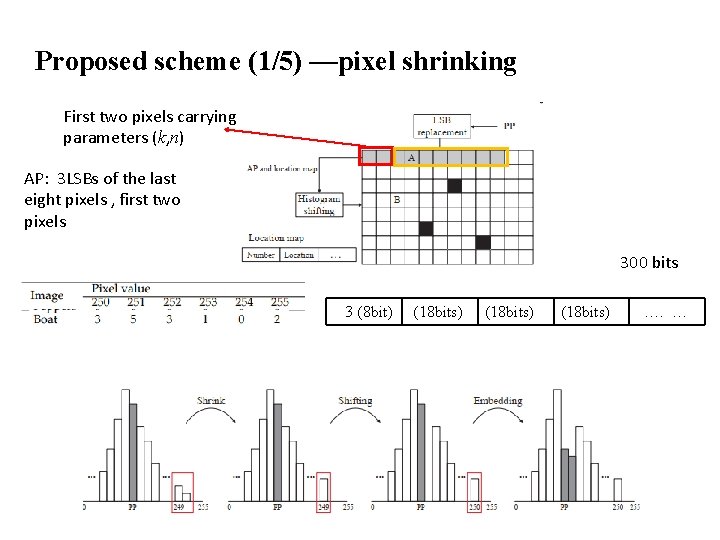
Proposed scheme (1/5) —pixel shrinking First two pixels carrying parameters (k, n) AP: 3 LSBs of the last eight pixels , first two pixels 300 bits 3 (8 bit) (18 bits) …. …
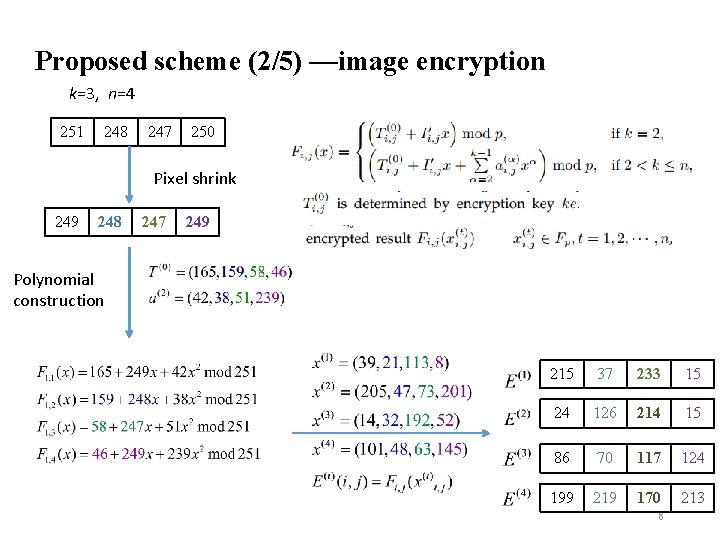
Proposed scheme (2/5) —image encryption k=3, n=4 251 248 247 250 Pixel shrink 249 248 247 249 Polynomial construction 215 37 233 15 24 126 214 15 86 70 117 124 199 219 170 213 8
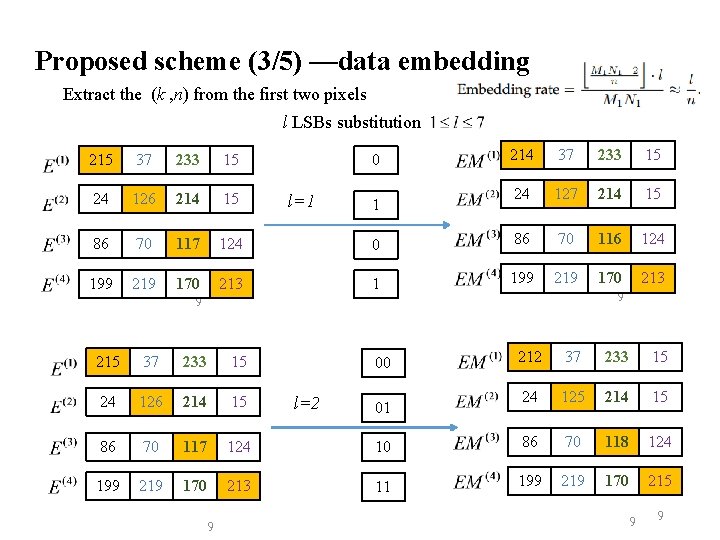
Proposed scheme (3/5) —data embedding Extract the (k , n) from the first two pixels l LSBs substitution 215 37 233 15 24 126 214 15 86 70 117 124 199 219 170 213 214 37 233 15 24 127 214 15 0 86 70 116 124 1 199 219 170 213 0 l=1 1 9 9 215 37 233 15 24 126 214 15 86 70 117 124 199 219 170 213 9 212 37 233 15 24 125 214 15 10 86 70 118 124 11 199 219 170 215 00 l=2 01 9 9
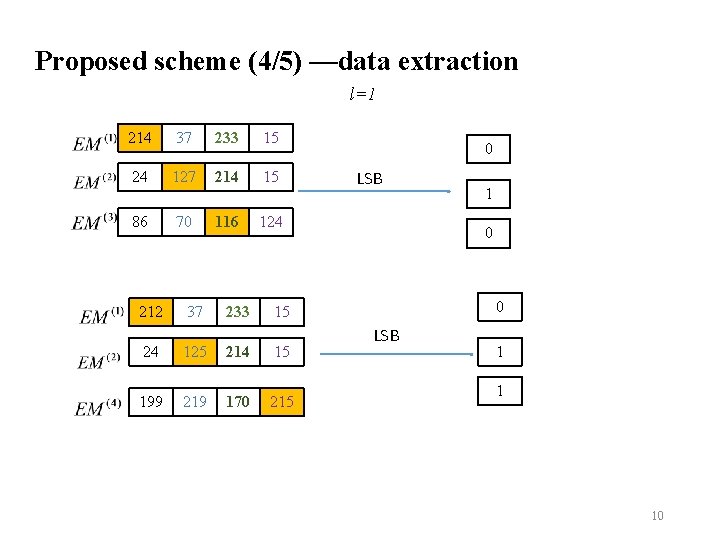
Proposed scheme (4/5) —data extraction l=1 214 37 233 15 24 127 214 15 86 70 116 124 212 37 233 0 LSB 0 0 15 24 125 214 15 199 219 170 215 1 LSB 1 1 10
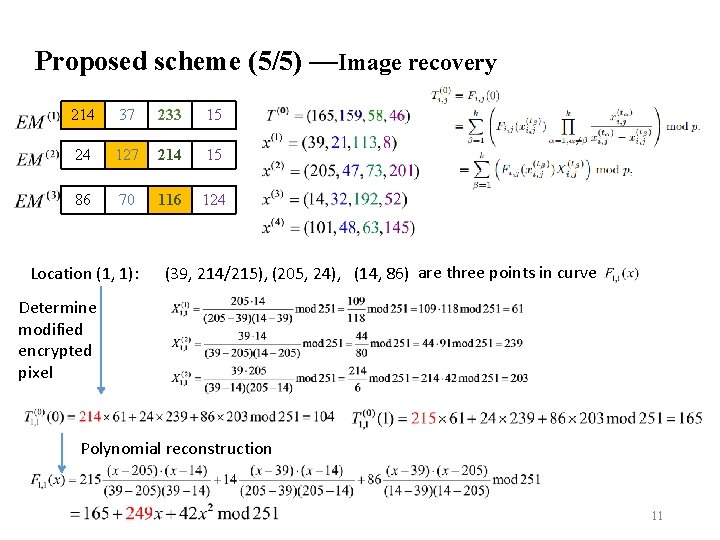
Proposed scheme (5/5) —Image recovery 214 37 233 15 24 127 214 15 86 70 116 124 Location (1, 1): (39, 214/215), (205, 24), (14, 86) are three points in curve Determine modified encrypted pixel Polynomial reconstruction 11
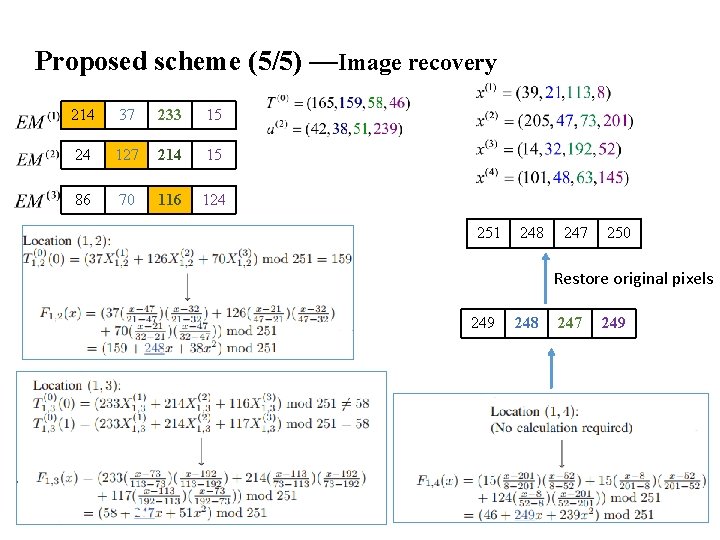
Proposed scheme (5/5) —Image recovery 214 37 233 15 24 127 214 15 86 70 116 124 251 248 247 250 Restore original pixels 249 248 247 249
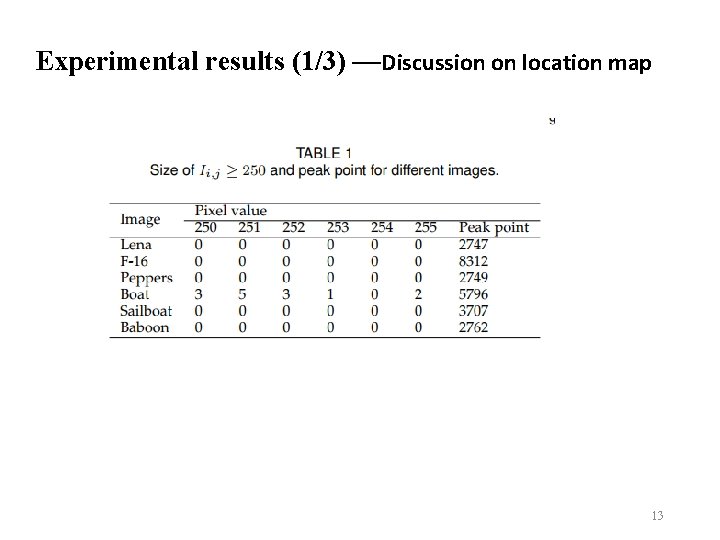
Experimental results (1/3) —Discussion on location map 13
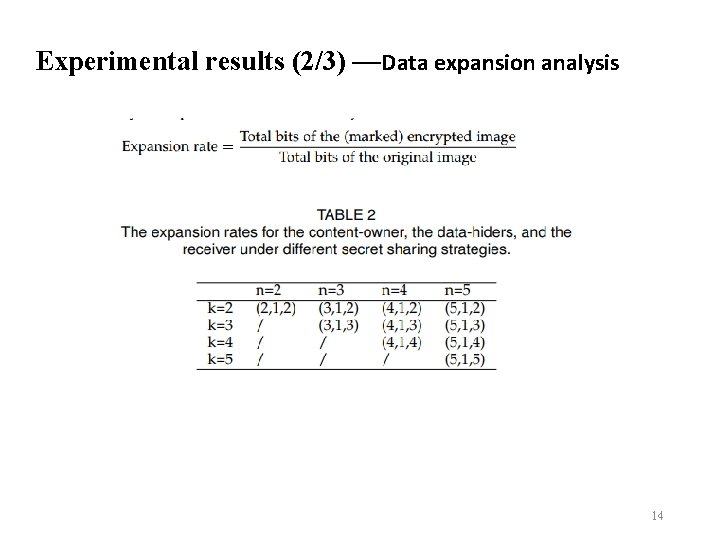
Experimental results (2/3) —Data expansion analysis 14
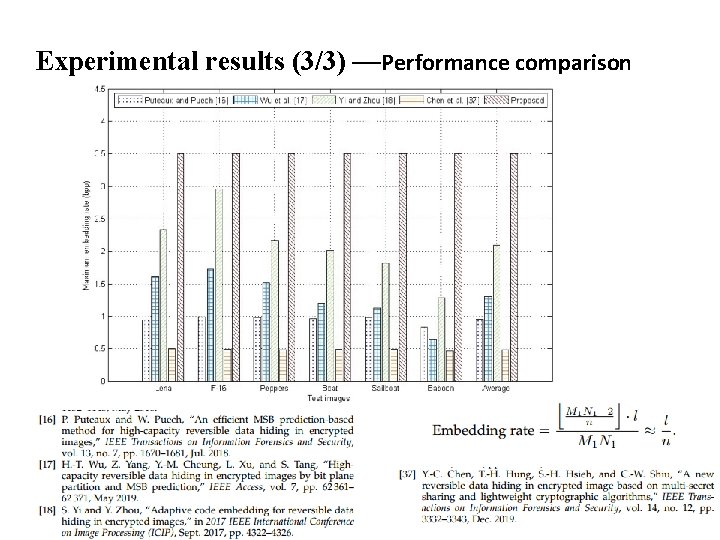
Experimental results (3/3) —Performance comparison 15
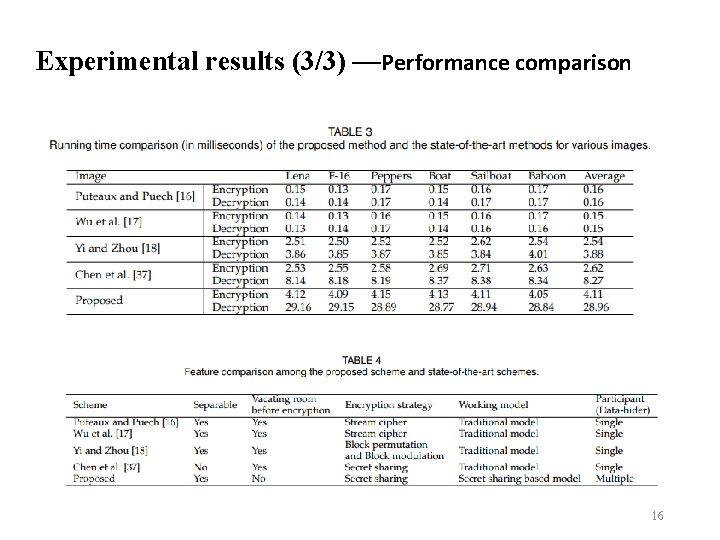
Experimental results (3/3) —Performance comparison 16

Conclusions p. This paper proposes a novel model with multiple data -hides for RDH-EI based on secret sharing. p Based on the proposed model, a separable RDH-EI method with high-capacity is proposed 17
- Slides: 17