SEC 318 Guerilla Security Securing Exchange 2000 and


























- Slides: 41

SEC 318 Guerilla Security – Securing Exchange 2000 and 2003 Infrastructures Fred Baumhardt and Rab Thynne Senior and Partner Strategy Consultant Microsoft UK

Why do we call this Guerilla • Guerilla as a type of warfare is exactly • • what we face in Internet Security Expect attacks from anywhere, with any device, at any time, from the inside Defences must be built exactly the same way, good monitoring, competent security forces, and ruthless execution of security policy on attackers

Session Overview • Core Security Concepts applied to Exchange • The Exchange Server Security Model • Implementing End to End Exchange Security • • Implications of Client Selection Securing Client/Server to Server Communications Network Layer Security Exchange Host Server Security • Questions.

The Big Picture • Exchange is an Infrastructure product – • ergo: it is only as secure as the infrastructure So design of Supporting Infra is critical : • • • DMZ design DCs and their configuration DNS infrastructure Server Build Management and Operations

Internet Security Roots and Mail • Lets be honest – from a security perspective: IPv 4 Sucks – not • • • . designed for Security • Internet used to require Sec clearance to use – physical access was restricted – no need for protocol security • Resistance to Nuclear attack was more important than protecting traffic as people on the network were trusted TCP/IP was thus designed without security in mind – added as a bolt-on- SMTP has almost none SMTP takes anonymous un-authenticated messages from the dirty world and puts them into heart of your network No one thought mail storage would be mission critical

Core Security Concepts applied to Exchange • The OS is only one component of security AND • • • . Firewalls are not a Panacea Getting into the bank branch doesn’t mean you get into the vault In the real world security relies on multiple things. It should also do this in the IT world • People and Process • Internal and Edge Technologies • Management and Operations Securing your Exchange system is securing your core systems – there is no silver bullet wizard

Your Attack Sources for Comms • Answer: Everyone – inside and out • The majority of attacks originate internally • Corporate espionage • People with Inside knowledge • Your Users playing with stuff they don’t understand • Externally…could be anyone • “Script kiddies” armed with widely accessible • tools More serious attackers– fun or profit

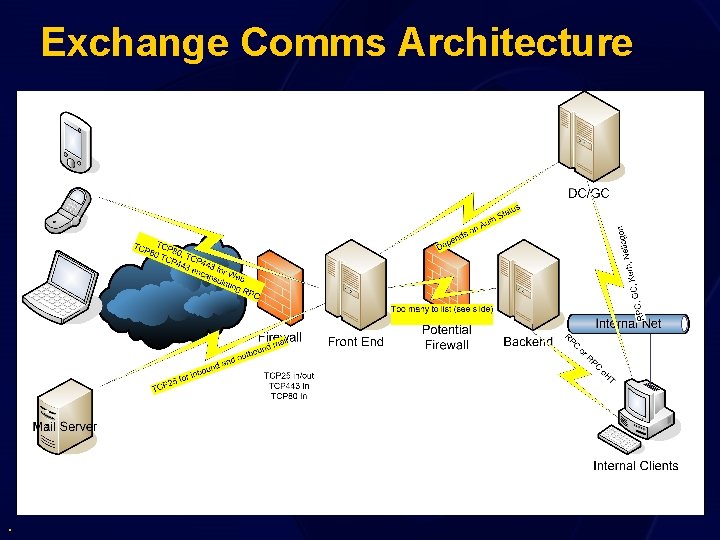
Exchange Comms Architecture .

Internal DMZ Firewall Ports • • • TCP 80 for HTTP 143 for IMAP 110 for POP 25 for SMTP 691 for Link State Algorithm routing protocol TCP/UDP port 389 for LDAP to Directory Service TCP port 3268 for LDAP to Global Catalog Server TCP/UDP port 88 for Kerberos authentication TCP/UDP port 53 - DNS TCP port 135 - RPC endpoint mapper TCP ports 1024+ - RPC service ports (unless DC and Exchange Restricted) If you use IPSec between the front-end and back-end, open the appropriate ports. If the policy you configure only uses AH, you do not need to allow ESP, and vice versa. UDP port 500 – RPC over HTTP can reduce this 600 -2 and 593

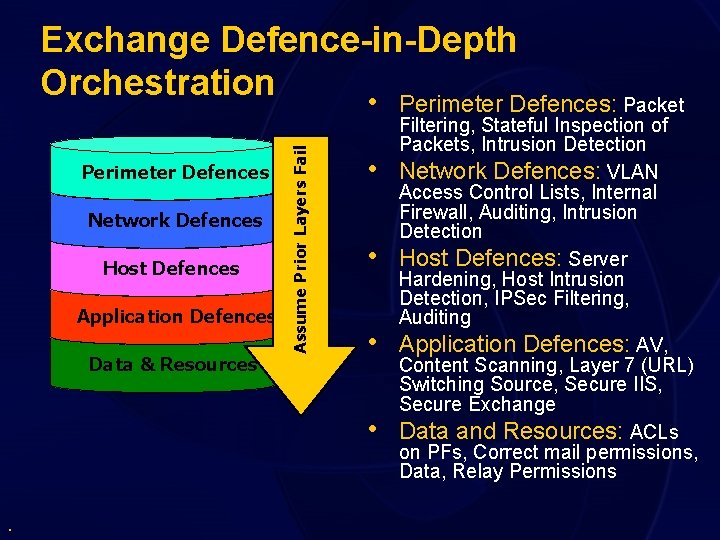
Perimeter Defences Network Defences Host Defences Application Defences Data & Resources Assume Prior Layers Fail Exchange Defence-in-Depth Orchestration • Perimeter Defences: Packet • • . Filtering, Stateful Inspection of Packets, Intrusion Detection Network Defences: VLAN Access Control Lists, Internal Firewall, Auditing, Intrusion Detection Host Defences: Server Hardening, Host Intrusion Detection, IPSec Filtering, Auditing Application Defences: AV, Content Scanning, Layer 7 (URL) Switching Source, Secure IIS, Secure Exchange Data and Resources: ACLs on PFs, Correct mail permissions, Data, Relay Permissions

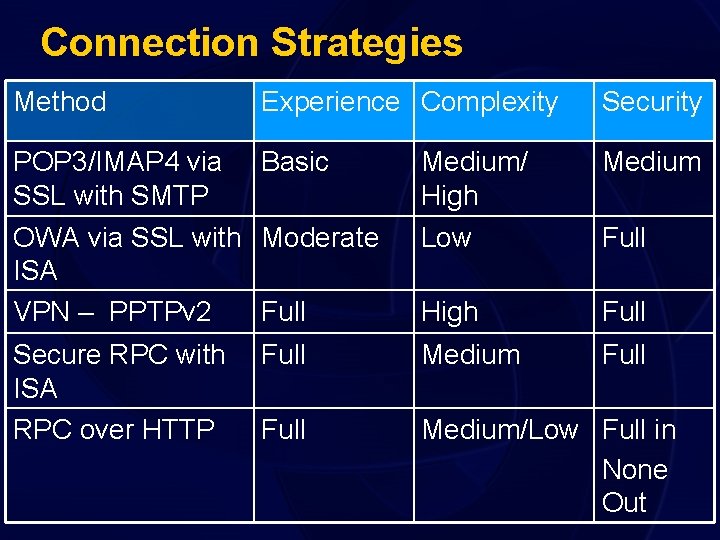
Connection Strategies Method Experience Complexity Security POP 3/IMAP 4 via Basic SSL with SMTP OWA via SSL with Moderate ISA VPN – PPTPv 2 Full Medium/ High Low Medium High Full Secure RPC with ISA RPC over HTTP Full Medium/Low Full in None Out Full

POP 3/IMAP 4 with SMTP • Uses SSL to secure POP or IMAP connection • Does not authenticate at front end • Requires SMTP at front-end to send mail OR • • • . separate SMTP relay (watch for relay spam) Removes much of the rich functionality Public Folder access can be tricky Don’t enable unless you absolutely have to

OWA via SSL with ISA • OWA is lightweight and available anywhere • Not totally functional but close • No Offline facility – but great usability • SSL is an easy and proven security tool • Can be terminated at ISA with Feature Pack • Only used to Front-end server – not FE-BE in 2000 – • . 2003 can use Kerberos for delegation Pre-authentication with ISA is very strong

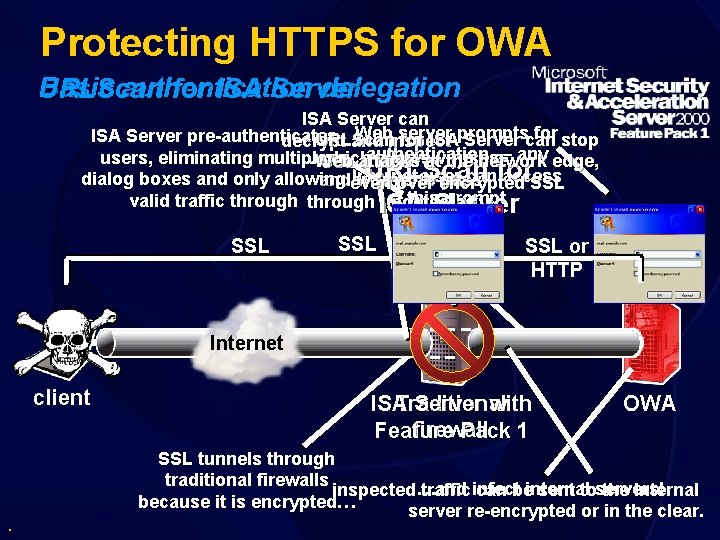
Protecting HTTPS for OWA Basic authentication delegation URLScan for ISA Server can Webinspect server for stop ISA Server pre-authenticates URLScan for ISAprompts Server can decrypt and authentication — any edge, users, eliminating multiple …which allowsatviruses Web the network SSL attacks traffic URLScan Internet user canfor access dialog boxes and only allowing andeven worms to pass over encrypted SSL this prompt valid traffic through ISA undetected… Server SSL SSL or HTTP Internet client . Traditional ISA Server with firewall Feature Pack 1 OWA SSL tunnels through traditional firewalls inspected …and traffic infect can beinternal sent toservers! the internal because it is encrypted… server re-encrypted or in the clear.

VPN Inbound • Dedicated HW/SW VPN infrastructure • Requires opening of ports for VPN and • • authentication Provides Full and Rich Network Access Can be costly for enterprises to implement • RPC over HTTP can reduce need – also secure RPC publishing with ALF .

Using ISA for RPC Publishing • ISA Can Securely Publish RPC • Opens 135 and listens (can block by source) • Only Allows Specific UUID for Outlook • • (configurable) Dynamically Port Filters subsequent connections Can require Encrypted RPC only • Outlook can have full functionality without VPN.

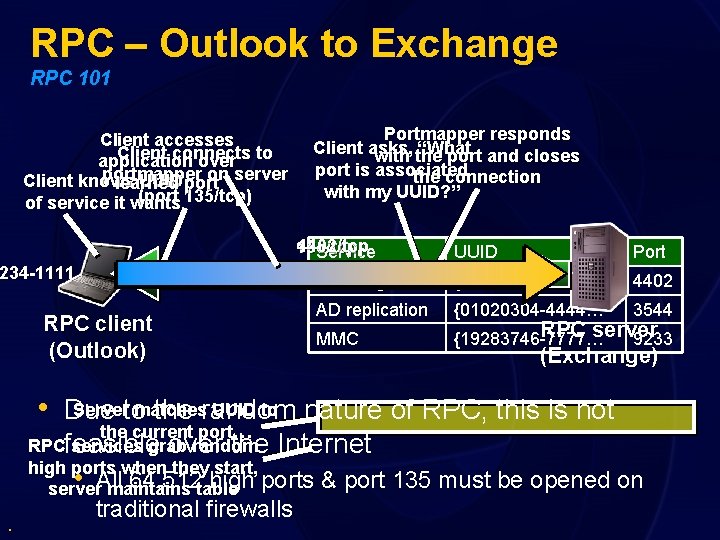
RPC – Outlook to Exchange RPC 101 Client accesses Client connects application over to portmapper on server Client knows UUID port learned (port 135/tcp) of service it wants Portmapper responds Client asks, “What with the port and closes port is associated the connection with my UUID? ” 4402/tcp 135/tcp Service 234 -1111…} RPC client (Outlook) Port Exchange UUID 4402/tcp {1234 -1111… AD replication {01020304 -4444… 3544 MMC 4402 RPC server {19283746 -7777… 9233 (Exchange) Serverto matches UUID to nature of RPC, this is not • Due the random the current port… RPCfeasible services grab random over the Internet high ports when they start, 64, 512 table high ports & port server. All maintains • . traditional firewalls 135 must be opened on

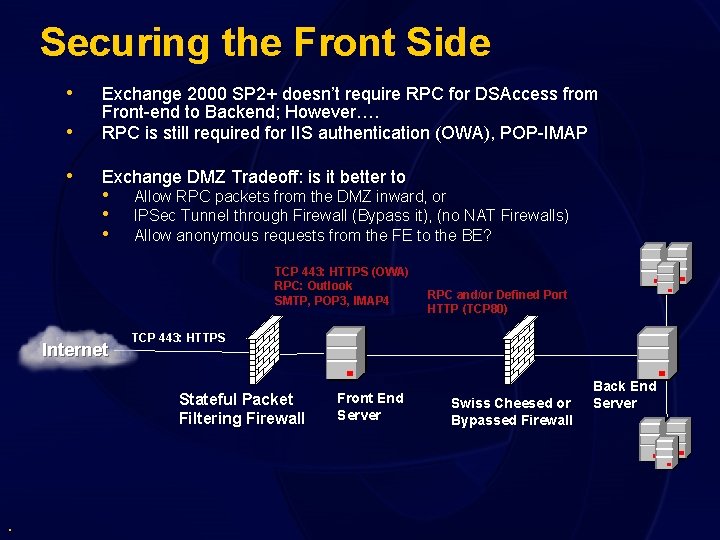
Securing the Front Side • • Exchange 2000 SP 2+ doesn’t require RPC for DSAccess from Front-end to Backend; However…. RPC is still required for IIS authentication (OWA), POP-IMAP • Exchange DMZ Tradeoff: is it better to • • • Allow RPC packets from the DMZ inward, or IPSec Tunnel through Firewall (Bypass it), (no NAT Firewalls) Allow anonymous requests from the FE to the BE? TCP 443: HTTPS (OWA) RPC: Outlook SMTP, POP 3, IMAP 4 Internet TCP 443: HTTPS Stateful Packet Filtering Firewall . RPC and/or Defined Port HTTP (TCP 80) Front End Server Swiss Cheesed or Bypassed Firewall Back End Server

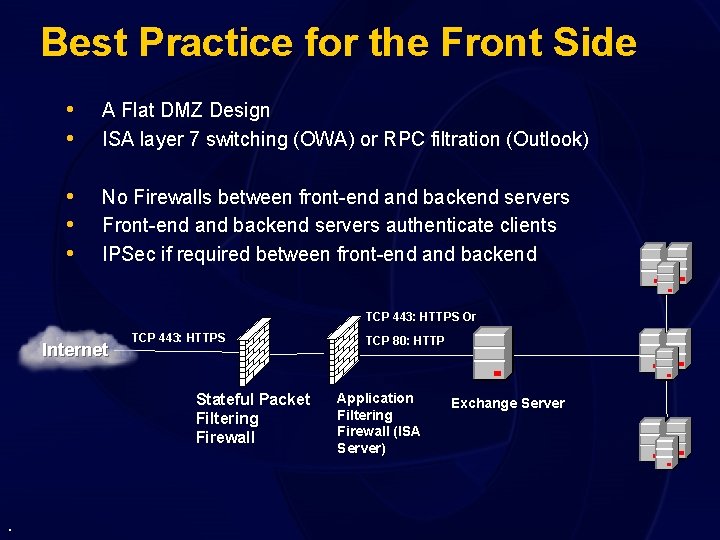
Best Practice for the Front Side • • A Flat DMZ Design ISA layer 7 switching (OWA) or RPC filtration (Outlook) • • • No Firewalls between front-end and backend servers Front-end and backend servers authenticate clients IPSec if required between front-end and backend TCP 443: HTTPS Or Internet TCP 443: HTTPS Stateful Packet Filtering Firewall . TCP 80: HTTP Application Filtering Firewall (ISA Server) Exchange Server

Is This Less Secure ? • Same numbers of firewalls to defeat • RPC or tunnelling can negate firewalls anyway • Attacks come at Data Layer • This is a shift in thinking as Firewalls move up the stack and switches start port filtering .

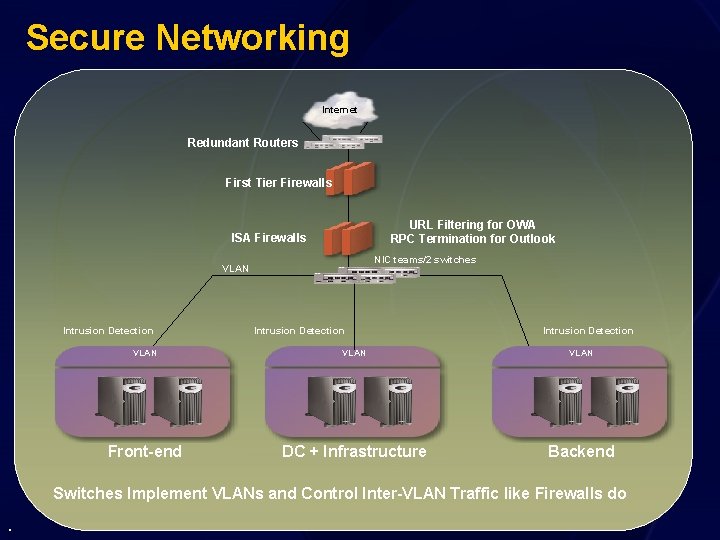
Secure Networking Internet Redundant Routers First Tier Firewalls URL Filtering for OWA RPC Termination for Outlook ISA Firewalls NIC teams/2 switches VLAN Intrusion Detection VLAN Front-end DC + Infrastructure Backend Switches Implement VLANs and Control Inter-VLAN Traffic like Firewalls do .

Client Security from Internet • Every time you connect into a network you • extend the security perimeter RPC Publishing and VPN both require great care at the client • Harden your clients on the Internet or hackers • • will attack clients and ride the VPN Require RPC encryption for Outlook Client Based IDS systems

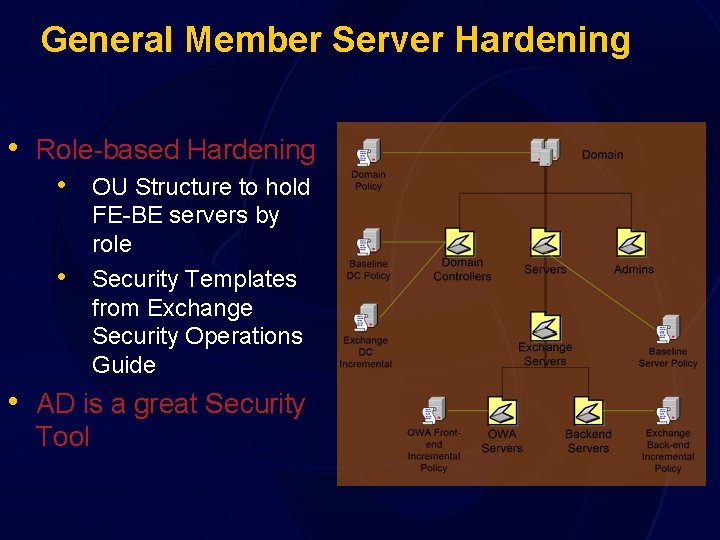
General Member Server Hardening • Role-based Hardening • OU Structure to hold • FE-BE servers by role Security Templates from Exchange Security Operations Guide • AD is a great Security Tool

IIS Lockdown Changes • File ACLs-denies relevant permissions on • • • home directory Also sets ACL on (Exch. Directory)Exch. Web Denies execute access to all system utilities, such as cmd. exe, in the c: winntsystem 32 folder. Changes by IISLockdown can be overwritten by Group Policy

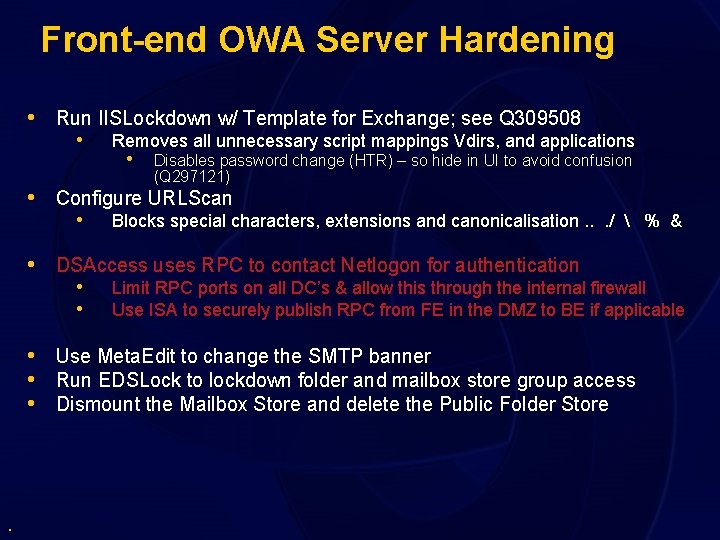
Front-end OWA Server Hardening • Run IISLockdown w/ Template for Exchange; see Q 309508 • Removes all unnecessary script mappings Vdirs, and applications • Disables password change (HTR) – so hide in UI to avoid confusion (Q 297121) • Configure URLScan • Blocks special characters, extensions and canonicalisation. . . / % & • DSAccess uses RPC to contact Netlogon for authentication • • Limit RPC ports on all DC’s & allow this through the internal firewall Use ISA to securely publish RPC from FE in the DMZ to BE if applicable • Use Meta. Edit to change the SMTP banner • Run EDSLock to lockdown folder and mailbox store group access • Dismount the Mailbox Store and delete the Public Folder Store .

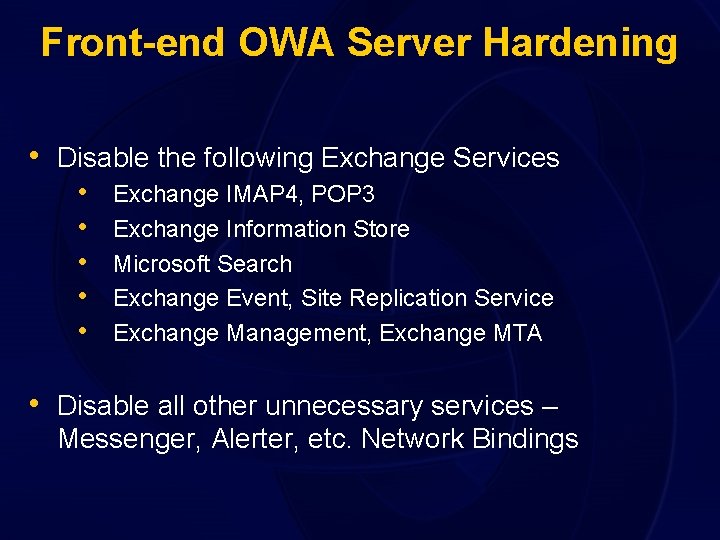
Front-end OWA Server Hardening • Disable the following Exchange Services • • • Exchange IMAP 4, POP 3 Exchange Information Store Microsoft Search Exchange Event, Site Replication Service Exchange Management, Exchange MTA • Disable all other unnecessary services – Messenger, Alerter, etc. Network Bindings

Front End OWA Server Hardening • Ensure the following are enabled • • • Exchange Routing Engine IPSEC Policy Agent RPC Locator IIS Admin Service World Wide Web Publishing Service

Backend Server Hardening • Enabled Exchange Services • Information Store • Exchange Management Instrumentation • Exchange System Attendant • Exchange Routing Engine • Disabled Exchange Services • IMAP 4 • POP • Exchange Event Service (If E 2 K only) • Exchange Site Replication Service (If E 2 K only) • Exchange MTA Stacks (If E 2 K only and no X. 400)

Backend Server Hardening • Exchange Required O/S Services • • • WWW Service (OWA comms) IIS Admin Service (Exchange Routing) SMTP RPC Locator (DC comms) IPSEC Policy Agent • System Attendant Depends on • • • Event Log NTLM Security Support Provider RPC Locator Server Workstation

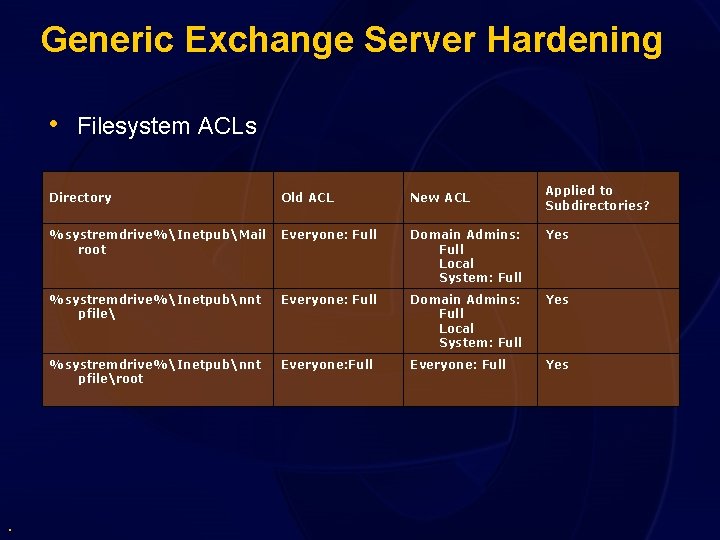
Generic Exchange Server Hardening • Filesystem ACLs . Applied to Subdirectories? Directory Old ACL New ACL %systremdrive%InetpubMail root Everyone: Full Domain Admins: Full Local System: Full Yes %systremdrive%Inetpubnnt pfileroot Everyone: Full Yes

Business Continuity • Security planning also needs to cover • • • breaches Think through disaster recovery strategy Backup and Recovery Strategy critical Critical Incident Management Procedure

Physical Server Access • Physical Infrastructure access must be • • strictly controlled Access to Domain Controllers can cripple networks in seconds We often find mission critical machines under desks

Additional Security Protection • Antivirus applications are critical to • • exchange SMTP Screening software is becoming increasingly important Content Blocking – Appropriate E-mails

Maintaining Security • Microsoft Baseline Security Analyzer • V 1. 2 Scans Exchange and Windows • Software Update Services – simplified patch • • . management and control – free tool Not enterprise focused tools – SMS 2003 is better option Use Group Policy to enforce configuration

Top 10 Ways to Get Secure 1. Implement the Security Operations Guides for Windows and Exchange http: //msdn. microsoft. com/practices 2. 3. 4. 5. . Use MBSA to identify missing patches Implement IISLockdown based on role Secure Infrastructure Assets Use the EDSLock script to restrict groups

Top 10 Ways To Get Secure 6. Get adequate antivirus protection for servers and desktops 7. Use perimeter SMTP scanning 8. Automate Patch Management 9. Use SSL, IPsec, and MAPI encryption where appropriate 10. Plan your response to an intrusion before it happens

Exchange Security Resources • • • . Exchange Security Operations Guide Windows Security Operations Guide NSA Security Guides Microsoft Systems Architecture – EDC-IDC Microsoft Operations Framework

Other Links • • • Exchange 2000 – EDS Lockdown http: //support. microsoft. com/default. aspx? scid=http: //support. microsoft. com: 80/supp ort/kb/articles/Q 313/8/07. asp&No. Web. Content=1 Exchange Library http: //www. microsoft. com/exchange/library Exchange Security http: //www. microsoft. com/downloads/details. aspx? displaylang=en&Family. ID=D 286 E 9 A 7 -FE 36 -4 A 02 -A 0 F 8 -75 D 4 F 9 EB 8 D 2 D

In Closing… • Thanks for coming! • Feel free to send comments or feedback • fredbaum@microsoft. com • athynne@microsoft. com • PLEASE fill out your evaluations! .

evaluations

© 2003 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.