SCIF Design Best Practices Lessons Learned Presentation to

SCIF Design Best Practices / Lessons Learned Presentation to: September 19, 2016

Purpose of the Presentation • Overview of what a SCIF is & what comprises a SCIF • Governing criteria for a SCIF • Review of SCIF Stakeholders • Best Practices / Lessons Learned in executing a SCIF project

What is a SCIF? • Sensitive Compartmented Information Facility • Facility which handles Confidential, Secret, Top Secret information • Facility must be accredited in order to handle, process, discuss or store Sensitive Compartmented Information (SCI) • Provides for operational capabilities that are critical to the supported command’s mission

What is a SCIF? • Even though SCIF ultimately is a building (or area within a building) in which sensitive information is handled, the development of a SCIF is a process which requires collaboration between many stakeholders • At the conclusion of construction, an accreditation process occurs which classifies the facility as one in which sensitive information can be handled • The execution goal is for there to be “No surprises” when the accreditation process takes place.

Pop Quiz! Question: Why is it important that there not be surprises at the end construction?

Pop Quiz! Question: Why is it important that there not be surprises at the end construction? Answer: Because if the accreditation isn’t obtained, then the facility may not be able to be operated as a SCIF, thereby not fulfilling mission requirements.

Relevant Criteria for SCIF • UFC’s • UFC 4 -010 -01 & 02: Do. D Minimum Antiterrorism Standards/Standoff Distances for Buildings • UFC 4 -010 -05: Sensitive Compartmented Information Facilities Planning, Design and Construction • Other Governing Criteria • ICD/ICS 705: Technical Specifications for Construction and Management of SCIF • JAFAN Manual 6/9: Joint Air Force Army Navy Manual for Physical Security Standards for Special Access Program Facilities (SAPF) • DCID 6/9: Director of Central Intelligence Directive 6/9 was superseded by ICD/ICS 705 Other Do. D Criteria Exists

SCIF Classifications • Secure Working Area (SWA) An area where SCI is handled, discussed and/or processed, but not stored • Temporary Secure Working Area (TSWA) Secure working area which is used less than 40 hours/month and the accreditation is limited to 12 months or less • Temporary SCIF established for a limited time to meet tactical, emergency or immediate operational requirements

SCIF Classifications (cont’d) • Closed Storage SCIF where SCI material is stored in GSA approved storage containers when not in use. This includes documents, computer hard drives and storage media • Open Storage SCIF in which SCI may be openly stored or processed • Continuous Operation SCIF which is staffed and operated 24/7

SCIF Stakeholders • Accrediting Official (AO) Person designated by the Cognizant Security Authority (CSA) who is responsible for all aspects of SCIF management and operations to include security policy implementation and oversight. • Site Security Manager (SSM) Person designated by the AO who is responsible for all aspects of SCIF management and operations to include security policy implementation and oversight. • Certified TEMPEST Technical Authority (CTTA) US Government appointed employee who has met established certification requirements in regard to TEMPEST

SCIF Stakeholders (cont’d) • Mission Users Persons who will work, operate, handle SCI in the facility once the facility becomes operational • Architect – Engineer • Design of SCIF shall be performed by US Companies utilizing US Citizens or US Persons • A-E’s with past experience in SCIF planning and design provides a big benefit to the Government • Construction Contractor • Construction of SCIF shall be performed by US Companies utilizing US Citizens or US Persons • Construction teams with past experience in SCIF construction techniques also provides a benefit to the Government
Purpose of a SCIF • To mitigate against a forced entry, covert entry, visual surveillance, acoustic eavesdropping and electronic emanations which could compromise the operation held within the SCIF. • Therefore, security requirements to protect against these actions need to be identified and implemented in order to have an accredited SCIF. • Security can be a combination of building features or operational procedures.
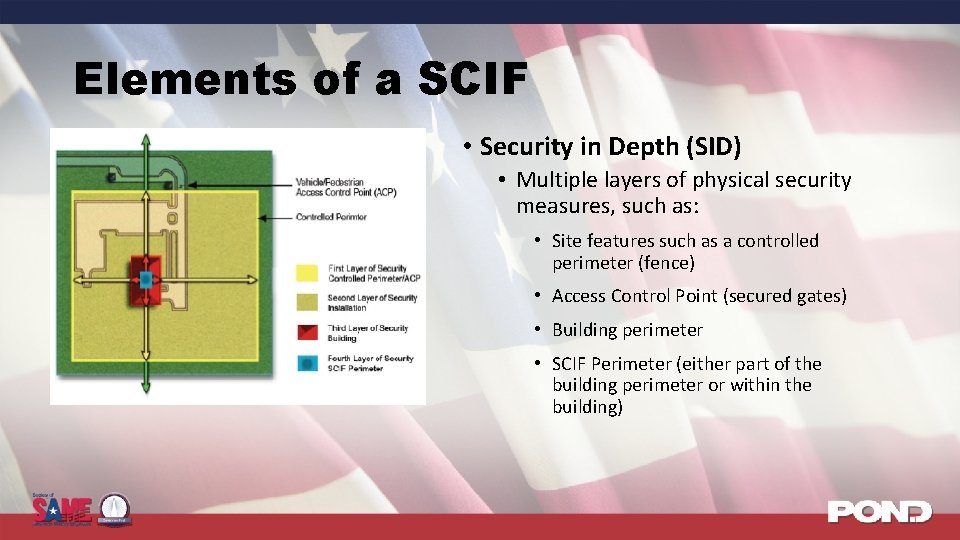
Elements of a SCIF • Security in Depth (SID) • Multiple layers of physical security measures, such as: • Site features such as a controlled perimeter (fence) • Access Control Point (secured gates) • Building perimeter • SCIF Perimeter (either part of the building perimeter or within the building)
Elements of a SCIF • Risk Assessment & Management • AO, SSM, Supported Command (Mission), CTTA, Communications, Security Forces, amongst others must determine the minimum or enhanced security requirements based upon the SCIF classification

Elements of a SCIF(cont’d) • Physical SCIF Perimeter • Wall, floor, ceiling/roof construction • Sound transmission coefficient (STC) Rating of 45 or 50 • RF Shielding • Door and door hardware • Vault – concrete or steel construction • Penetrations of the SCIF Perimeter • Limited number of locations for perimeter penetrations • Utilities such as mechanical, electrical, communications, etc. require special details • Inspection of perimeter penetrations
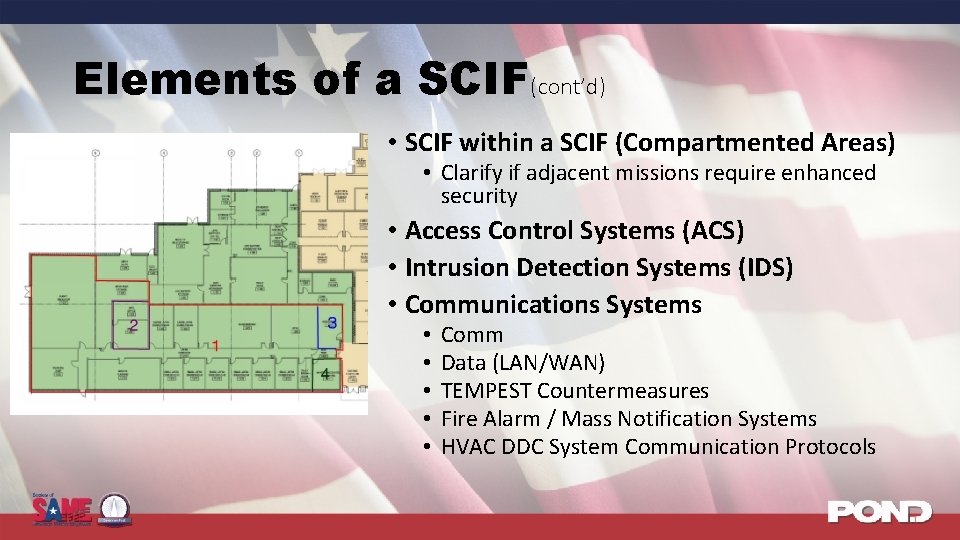
Elements of a SCIF(cont’d) • SCIF within a SCIF (Compartmented Areas) • Clarify if adjacent missions require enhanced security • Access Control Systems (ACS) • Intrusion Detection Systems (IDS) • Communications Systems • • • Comm Data (LAN/WAN) TEMPEST Countermeasures Fire Alarm / Mass Notification Systems HVAC DDC System Communication Protocols

Best Practices / Lessons Learned • Design Charrettes – dedicated discussions between the A-E’s design team and Gov’t security personnel on all aspects of the desired security requirements • AO and SSM need to be identified for the project • AO, SSM and other security stakeholders need to be available to the design team to answer questions throughout the life of the project • Devil is in the Details – review of construction details and specifications by the AO and SSM to ensure security requirements have been satisfied

Best Practices / Lessons Learned Communication and understanding of needs is the biggest “lessons learned” that we’ve experienced
Best Practices / Lessons Learned • Separation requirements for Compartmented Areas • What STC ratings are required? • Do penetrations require unique security measures? • Can utilities cross one CA to serve another CA? • Single Point of Penetration in SCIF Perimeter • Determine interpretation of this ICD/ICS 705 requirement • Alternative means to allow inspection of penetrations • Access Control System (ACS) • Identify zones for Compartmented Areas • Secured vestibule (man trap) • Types of acceptable door hardware, security system, etc. • Is a sole source for a particular vendor necessary to tie into existing systems?

Best Practices / Lessons Learned Ceiling Inspection Panels

Best Practices / Lessons Learned • Intrusion Detection System • Partial design with delegated design responsibility to contractor and manufacturer • Construction Documentation • Include ICD/ICS 705 or JAFAN 6/9 Manual as part of the Division 01 Specs • Highlight specific contractor responsibilities such as: • Construction photographs as documentation • Manner in which to phase/tie-in to existing systems • Inspections prior to concealing construction • Greater importance to phasing needs, tie-ins, existing system operability, SCIF functionality during construction • A detailed Construction Security Plan (CSP) becomes even more critical for a renovation project.

Best Practices / Lessons Learned • Justification & Authorizations (J&A’s) • Avoid change orders for sole source situations • Examples are for ACS, IDS, Door Hardware • Consider Procurement Method • Qualified Design-Build Team • Traditional Design-Bid-Build • Avoid contractors who may not have depth of experience or sophistication to execute a SCIF project • Construction Phase Services • For large SCIF projects, consider oversight required during construction • Full time Resident Engineer/Architect

Best Practices / Lessons Learned • AO, SSM, CTTA and Users (Mission) need to collaborate in order to develop the Construction Security Plan (CSP) • Starts with well developed understanding of security measures required or contemplated • Chapter 2 of UFC 4 -010 -05 has well developed checklist for planning a SCIF project and the required project documentation. For example, • What is the SCIF Classification? • Are there multiple SCIF’s (Compartmented Areas) needed within a particular building? • Has the required security been included in the project budget?

Summary • Successful SCIF project execution requires active involvement by project stakeholders who have a vested interest in the security of the facility • Classification and development of the required security measures identified by the Government • Charrette or other design meetings to collaborate on project security requirements • Active review of design documents to ensure needs are met • Sufficient oversight during construction to ensure details are constructed in accordance with the design • “No Surprises” should be the desired goal when it’s time to obtain the SCIF accreditation

SCIF Facility Design Best Practices / Lessons Learned Thank you for your attention! George Fragulis PE, BEMP, CEM, PMP, LEED AP fragulisg@Pondco. com 404 -748 -4846
- Slides: 25