School of Communication Engineering ENGINEERING STUDIES IN TELECOMMUNICATIONS





- Slides: 12

School of Communication Engineering ENGINEERING STUDIES IN TELECOMMUNICATIONS SECURITY

es s u Vir e vi c er f. S lo nia De Natura l Disa sters h c Stolen Laptop a e d es e t h s c a Theft of sensitive Information a Socia w e r l En e b r g a neeri i y Hac t s i r n ker r g a u l Intr l ec usio o ure l i a s d n F tem f s y o S s o et t r o s p p n u u s o d i p l u r l k i c a a b ye B t s Lo Indust rial Es Insiders abuse piona ge Malicious and Self-propagating Codes

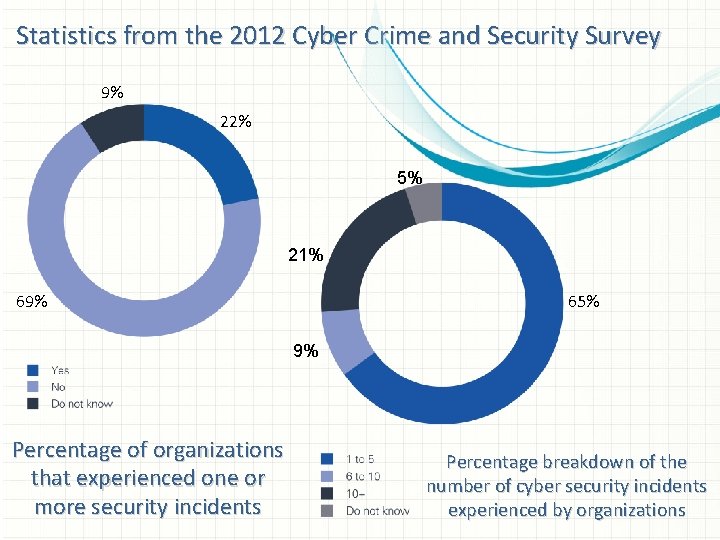
Statistics from the 2012 Cyber Crime and Security Survey 9% 22% 5% 21% 69% 65% 9% Percentage of organizations that experienced one or more security incidents Percentage breakdown of the number of cyber security incidents experienced by organizations

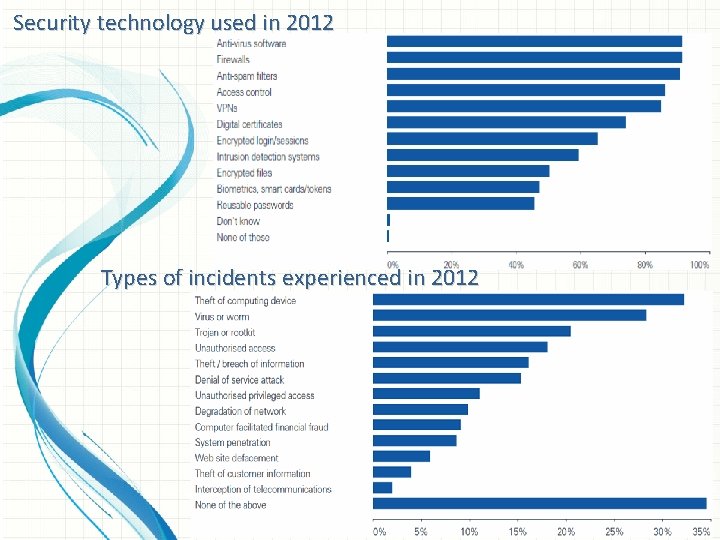
Security technology used in 2012 Types of incidents experienced in 2012

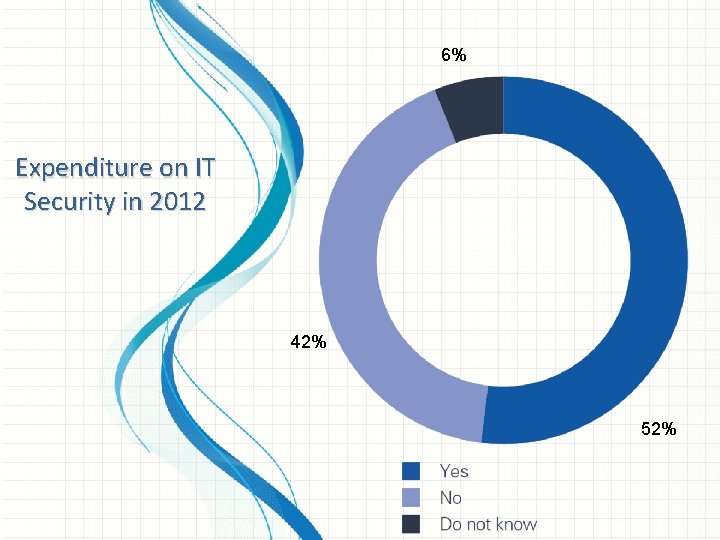
6% Expenditure on IT Security in 2012 42% 52%

Engineering studies in Telecommunications Security Instruct the next-generation of security engineers. Learn techniques, methodologies, policies, strategies, and procedures related to communication and information security. Prepare for a challenging career in the global Telecommunications security field.

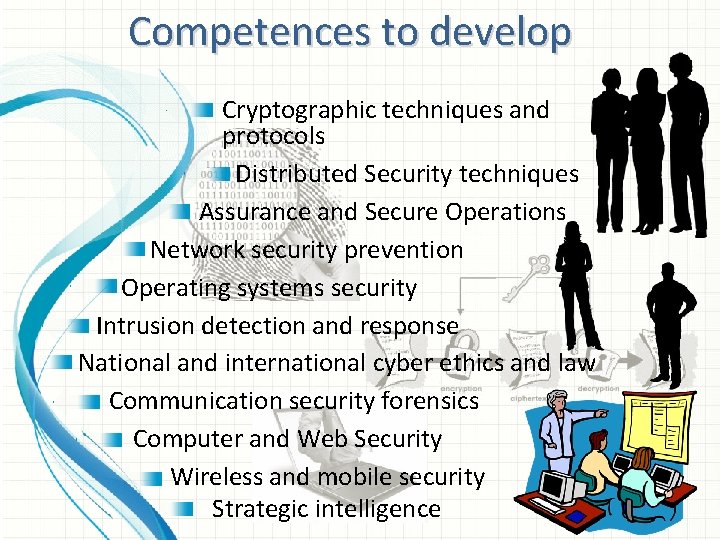
Competences to develop Cryptographic techniques and protocols Distributed Security techniques Assurance and Secure Operations Network security prevention Operating systems security Intrusion detection and response National and international cyber ethics and law Communication security forensics Computer and Web Security Wireless and mobile security Strategic intelligence

Your future job Expert and consultant in communication security Design, development, deployment, and management of security solutions Security and network administration and planning Security audit, verification, and assessment Incident response and risk assessment

An opportunity to take contact with industrial partners A course of seminars will be given by leading security experts from the industry An academic program shaped to the national and international industrial requirements, including certifications Security ethics and policy aspects, are also studied, focusing also on national and international regulations

Competitiveness Conformance to the need to make available well trained engineers at the international level The Program is close to those provided at the master level in several American universities : – – – Purdue University James Madison University John Hopkins university Carnegie Mellon University. … Some courses will be taught in English

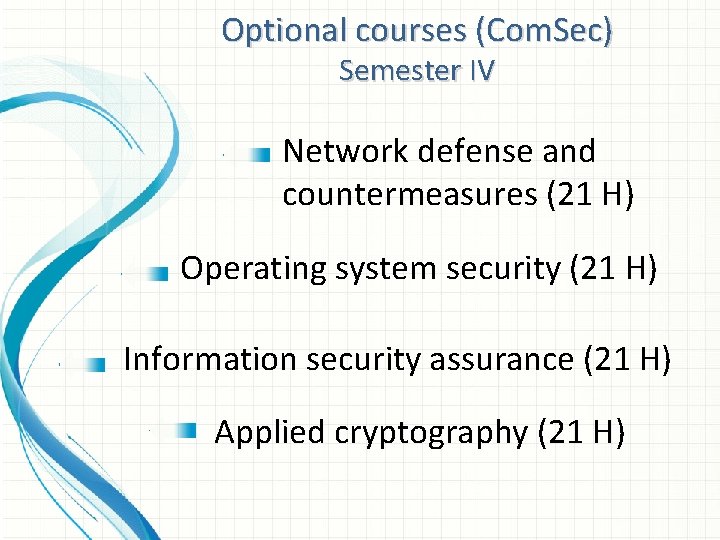
Optional courses (Com. Sec) Semester IV Network defense and countermeasures (21 H) Operating system security (21 H) Information security assurance (21 H) Applied cryptography (21 H)

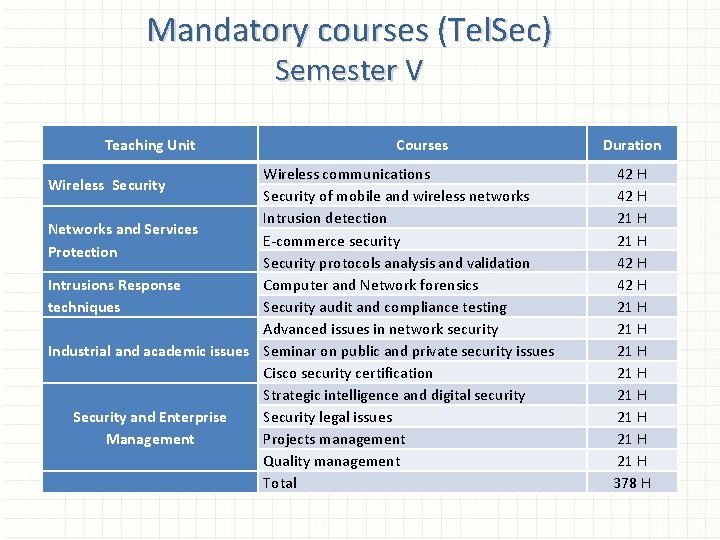
Mandatory courses (Tel. Sec) Semester V Teaching Unit Courses Wireless communications Security of mobile and wireless networks Intrusion detection Networks and Services E-commerce security Protection Security protocols analysis and validation Intrusions Response Computer and Network forensics Security audit and compliance testing techniques Advanced issues in network security Industrial and academic issues Seminar on public and private security issues Cisco security certification Strategic intelligence and digital security Security legal issues Security and Enterprise Management Projects management Quality management Total Wireless Security Duration 42 H 21 H 21 H 21 H 378 H