Scaling VLSI Design Debugging with Interpolation Brian Keng

Scaling VLSI Design Debugging with Interpolation Brian Keng, Andreas Veneris FMCAD 2009 Presenter: Meng-Yen Li 1

Introduction n The aim of functional verification is determine whether the implementation of a design conforms to its specification. An error trace is returned if the design if found to be buggy. Design debugging is the task of identifying potential error suspects in the design. 2

Introduction n In modern designs, error trace can be thousands of clock cycles long. Design debugging can consume as much as 30% of the total time to design a VLSI chip. Automated debugging methodologies remain of great interest to both the research and industrial communities. 3

Introduction n This work proposed a novel scalable SATbased design debugging algorithm. The algorithm leverages interpolants to over-approximate sets of constraints that model the erroneous behavior. This approach significantly reduce the memory-intensive circuit replication at any given time. 4
Introduction n The algorithm divides the error trace into several parts(windows). Analyze each window of time-frames separately. Interpolants are use to over-approximate set of constraints to properly constrain the erroneous behavior. 5
Introduction n n The described method finds all error locations. Error location is the place of module where error occurs. The function of the error location can be modified to correct the erroneous behavior for a give error trace and number of errors. A techniques to generate multiple interpolants is introduced to reduce the number of error locations returned. 6
Introduction n n Experiments show the benefits of this work compared to tradition SAT-based debugging: for a conservatitve partitoning of the error trace n n n 34% memory reduction 24% run-time reduction Only increased the number of returned error locations 1% of the total number of suspects. 7
Introduction n for a more aggressive partitioning scheme, average in: n n n 57% memory reduction 23% run-time reduction Above reduction achieved at the cost of increasing the number of returned error locations 2% of the total number of suspects. 8

Introduction n This favorable trade-off between resolution and performance allows for scaling of existing SAT-based debugging methodologies to handle modern VLSI designs. 9
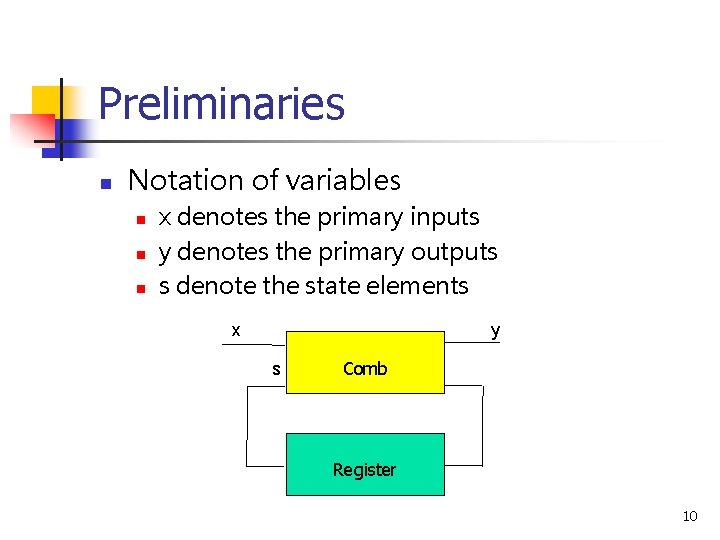
Preliminaries n Notation of variables n n n x denotes the primary inputs y denotes the primary outputs s denote the state elements x y s Comb Register 10
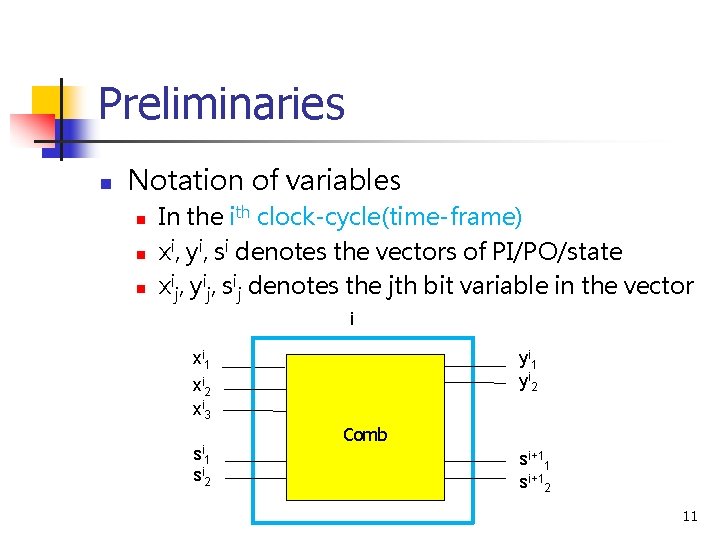
Preliminaries n Notation of variables n n n In the ith clock-cycle(time-frame) xi, yi, si denotes the vectors of PI/PO/state xij, yij, sij denotes the jth bit variable in the vector i xi 1 yi 2 xi 3 si 1 si 2 Comb si+11 si+12 11
Preliminaries n An example of multiple time-frame notation 12
Preliminaries n n Xi, Yi, Si denote a predicate for the ith clock cycle. Transition relation denoted as T(si, si+1, xi, yi). Suspects are all the error locations found in design debugging. A design debugging method is complete if and only if it return all suspects for a given error trace and number of errors. 13

Preliminaries n n The resolution of a debugging method refers to the total number of suspects returned. Fewer suspects correspond to better resolution. 14
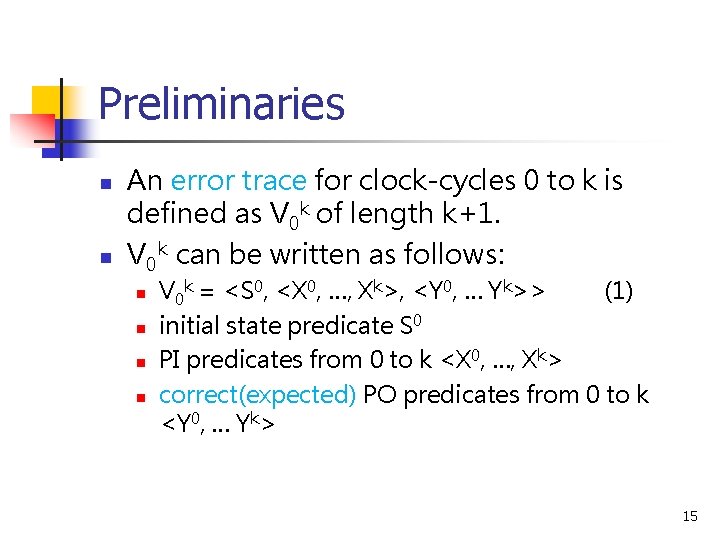
Preliminaries n n An error trace for clock-cycles 0 to k is defined as V 0 k of length k+1. V 0 k can be written as follows: n n V 0 k = <S 0, <X 0, …, Xk>, <Y 0, … Yk>> (1) initial state predicate S 0 PI predicates from 0 to k <X 0, …, Xk> correct(expected) PO predicates from 0 to k <Y 0, … Yk> 15
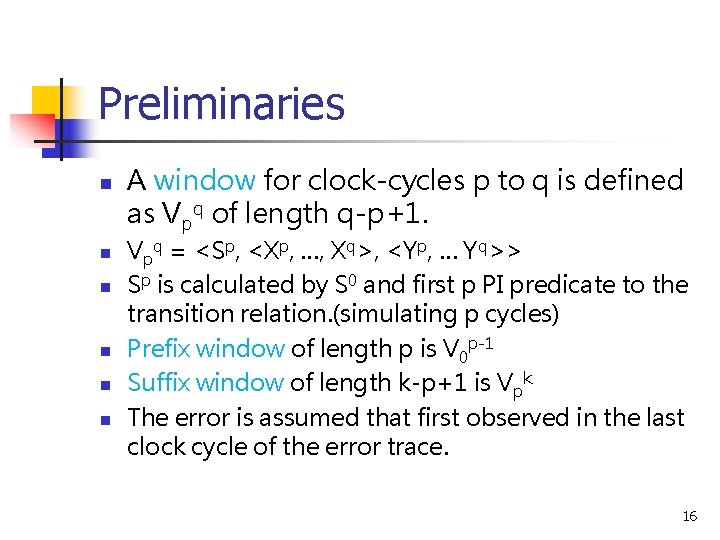
Preliminaries n n n A window for clock-cycles p to q is defined as Vpq of length q-p+1. Vpq = <Sp, <Xp, …, Xq>, <Yp, … Yq>> Sp is calculated by S 0 and first p PI predicate to the transition relation. (simulating p cycles) Prefix window of length p is V 0 p-1 Suffix window of length k-p+1 is Vpk The error is assumed that first observed in the last clock cycle of the error trace. 16
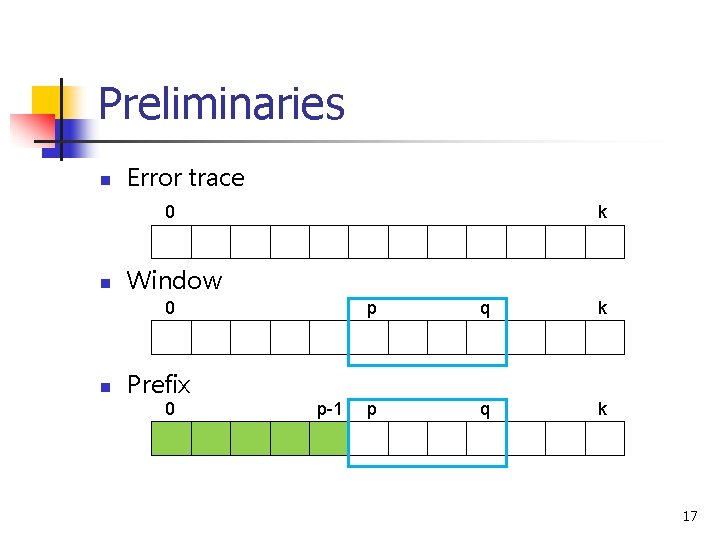
Preliminaries n Error trace 0 n k Window 0 n Prefix 0 p-1 p q k 17
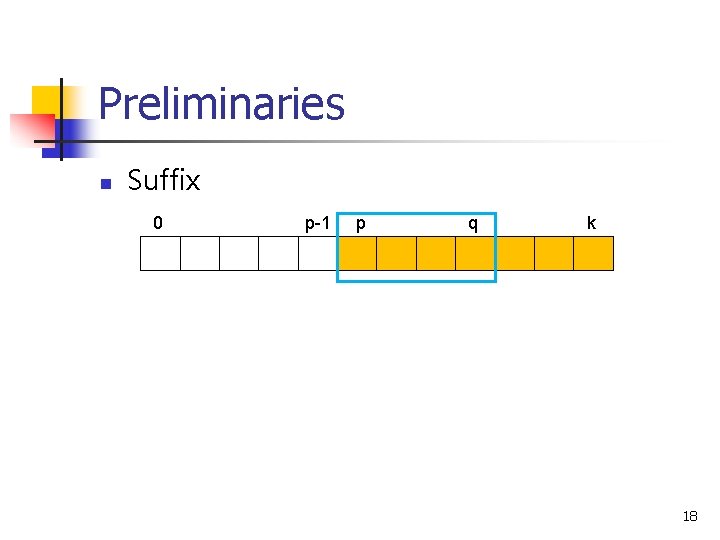
Preliminaries n Suffix 0 p-1 p q k 18
Preliminaries n n n SAT-based Design Debugging A complete method that encodes the problem into a SAT instance for a give error trace and number of errors. The satisfying assignments of the instance correspond to suspects which can be replaced with non-deterministic functions to correct the erroneous behavior in the error trace. 19
Preliminaries n n n The instance is created in several steps First, the transition relation is enhanced by introducing a set of suspect variables, E = {e 0, … en}, denoted Ten(si, si+1, xi, yi, E). Each ei correspond to ith potential error location(gate, module) n n This i is not related the ith clock cycle’s i. If ei = 1 then the location is disconnected from its fan-in and become free variable. n Can be achieved by using multiplexor. 20

Preliminaries n n Ten is unrolled as time-frame expaned model. Suspect variables are not replicated in the model since they represent the same location regardless of the time frame. 21

Preliminaries n n The number of simultaneous active suspect variables denoted as the error cardinality. Constrained to a given constant number N using N(E). 22
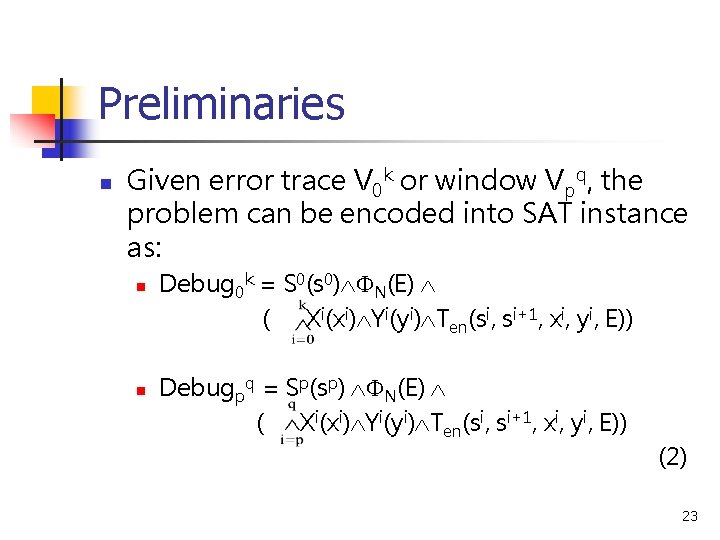
Preliminaries n Given error trace V 0 k or window Vpq, the problem can be encoded into SAT instance as: n n Debug 0 k = S 0(s 0) N(E) ( Xi(xi) Yi(yi) Ten(si, si+1, xi, yi, E)) Debugpq = Sp(sp) N(E) ( Xi(xi) Yi(yi) Ten(si, si+1, xi, yi, E)) (2) 23

Preliminaries n n n Note that for N = 0, Debug 0 k is UNSAT. To find all suspects, for each satisfying assignment, a blocking clause is added to the debugging instance to block the active suspect variables from appearing again as a satisfying assignment. When the solver eventually returns UNSAT, all possible suspects have been found. 24
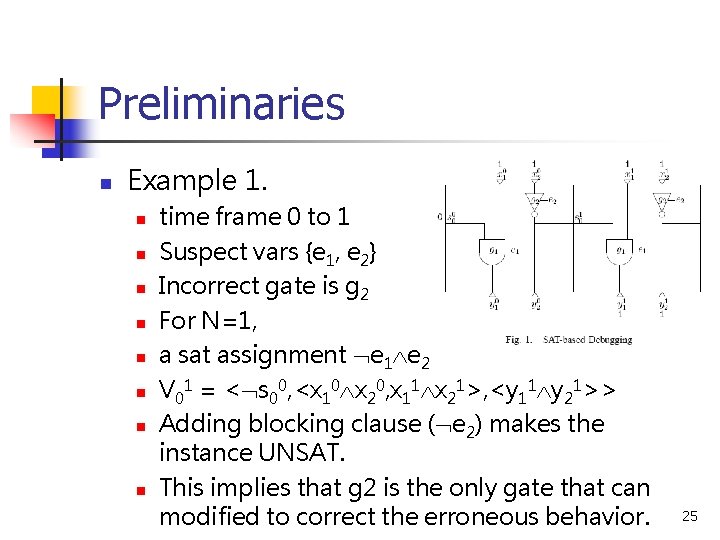
Preliminaries n Example 1. n n n n time frame 0 to 1 Suspect vars {e 1, e 2} Incorrect gate is g 2 For N=1, a sat assignment e 1 e 2 V 01 = < s 00, <x 10 x 20, x 11 x 21>, <y 11 y 21>> Adding blocking clause ( e 2) makes the instance UNSAT. This implies that g 2 is the only gate that can modified to correct the erroneous behavior. 25
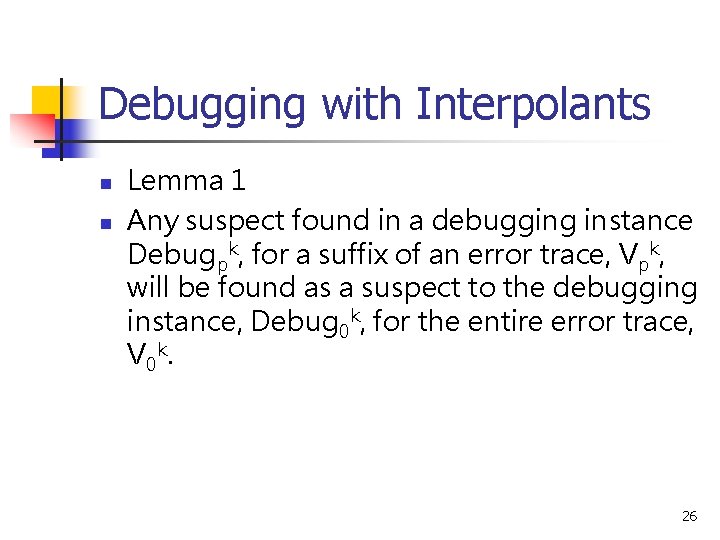
Debugging with Interpolants n n Lemma 1 Any suspect found in a debugging instance Debugpk, for a suffix of an error trace, Vpk, will be found as a suspect to the debugging instance, Debug 0 k, for the entire error trace, V 0 k. 26

Debugging with Interpolants n n n Lemma 1 Proof: Let M(E) be an assignment to the suspect variables in E such that Debugpk M is SAT. The lemma can be written as From eq 2, Debug 0 p-1 Debugpk have same clauses with Debug 0 k Sp(sp) Debug 0 p-1 is SAT because error hasn’t been observed yet 27
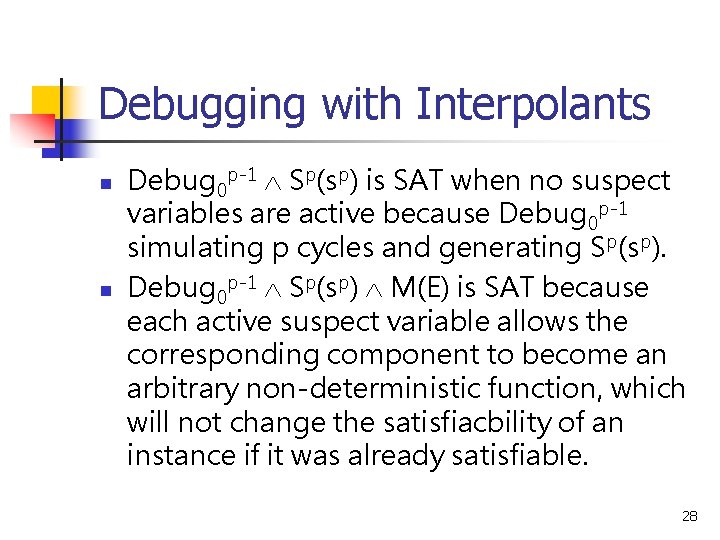
Debugging with Interpolants n n Debug 0 p-1 Sp(sp) is SAT when no suspect variables are active because Debug 0 p-1 simulating p cycles and generating Sp(sp). Debug 0 p-1 Sp(sp) M(E) is SAT because each active suspect variable allows the corresponding component to become an arbitrary non-deterministic function, which will not change the satisfiacbility of an instance if it was already satisfiable. 28

Debugging with Interpolants n n n Therefore, if Debugpk M(E) is SAT then Debug 0 p-1 Debugpk M(E) is SAT, since the only common variables are sp and E which are fully assigned. As a result, Debug 0 k Sp(sp) M(E) is SAT, implying that Debug 0 k M(E) is SAT. Proved. 29

Debugging with Interpolants n n Lemma 1 guarantees that suspects found in the suffix will also be found in the entire trace. However, if the error is excited before the current suffix, then there is no guarantee that the error will be found in Debugpk. 30

Debugging with Interpolants n n Theorem 1 Let U be an UNSAT core generated after blocking all satisfying assignments to suspects for Debugpk. If U Sp(sp) = then the suspects found in Debugpk will be exactly the suspects found in the entire debugging instance, Debug 0 k. 31

Debugging with Interpolants n n n Theorem 1 Prove: By Lemma 1, any suspect found in Debugpk is a suspect found in Debug 0 k. Proving theorem 1 by contradiction. Assume M(E) is an assignment that n n Debug 0 k M(E) is SAT Debugpk M(E) is UNSAT 32

Debugging with Interpolants n n U is the UNSAT core derived after blocking all satisfying assignments to suspects for Debugpk, which contain no clauses in Sp(sp). Since Debugpk M(E) is UNSAT, M(E) is not blocked by the blocking_clausepk. This means Debug 0 k blocking_clausepk is SAT. But in terms of clauses, U (Debugpk blocking_clausepk - Sp(sp)) Debug 0 k blocking_clausepk because U not contains clauses in Sp(sp). 33

Debugging with Interpolants n n n So U M(E) is SAT because Debug 0 k blocking_clausepk M(E) is SAT. But U is an UNSAT core, which is a contradiction. So it must be the case that Debugpk M(E) is SAT. 34
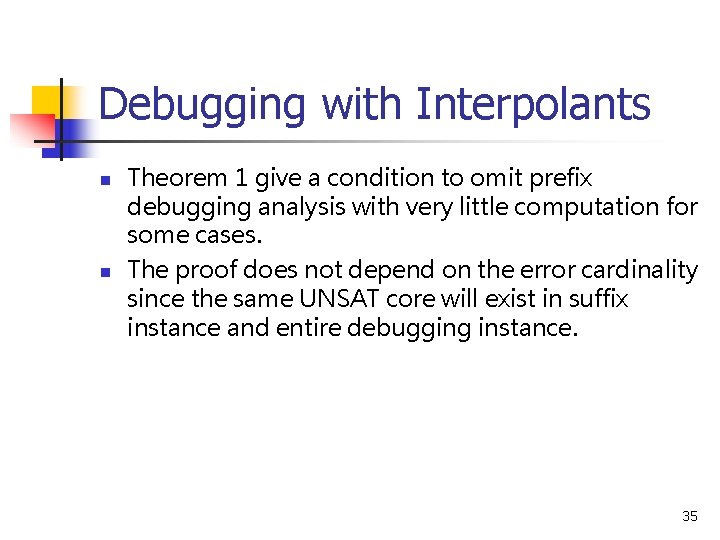
Debugging with Interpolants n n Theorem 1 give a condition to omit prefix debugging analysis with very little computation for some cases. The proof does not depend on the error cardinality since the same UNSAT core will exist in suffix instance and entire debugging instance. 35
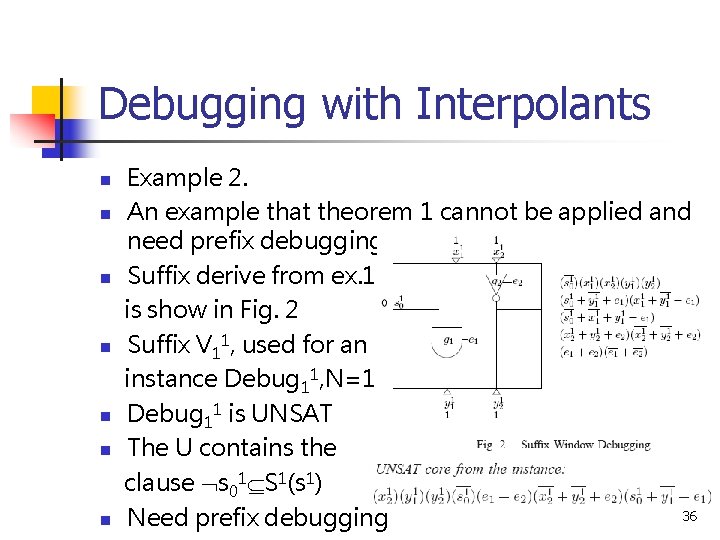
Debugging with Interpolants n n n n Example 2. An example that theorem 1 cannot be applied and need prefix debugging. Suffix derive from ex. 1 is show in Fig. 2 Suffix V 11, used for an instance Debug 11, N=1 Debug 11 is UNSAT The U contains the clause s 01 S 1(s 1) 36 Need prefix debugging
Debugging with Interpolants n Prefix Debugging can be formulated in two parts. n n First part use eq 2. for conventional SAT-based formulation. Second part use interpoant approximating time -frames for the corresponding suffix of the error trace. 37
Debugging with Interpolants n n Recall that erroneous behavior is only observed in last time-frame If only prefix is modelled then the instance will not be properly constrained. To avoid this situation, the interpolant is used as an over-approximation for the constraints that model the corresponding suffix. This ensures that the prefix is properly constrained. 38
Debugging with Interpolants n n The interpolant can be generated by UNSAT core of the solved suffix. Debugpk blocking_clauses is partitioned into A and B. n A= Xi(xi) Yi(yi) Ten(si, si+1, xi, yi, E) n B = Sp(sp) N(E) blocking_clauses The common variables of A and b are the state variables sp and suspect variables E. Interpolant Ppk for the suffix is generated. 39
Debugging with Interpolants n n n Ppk can be interpreted as an overapproximation of the suffix. The benefit of Ppk is it retains only the useful information that causes the erroneous behavior instead of modelling all the time-frames for the suffix of the error trace. Experimental results show that in most cases, the interpolant is much smaller than the instance it was generated from. 40

Debugging with Interpolants n n Using Ppk , Debug 0 p-1 can be constrained with the cause for erroneous behavior. The debugging instance for a prefix of an error trace with an interpolant is denoted as Debug. Itp 0 p-1 = Debug 0 p-1 Ppk Debug. Itp 0 p-1 will be UNSAT when no suspect variables are active because Debug 0 p-1 means simulating for clock cycle 0 to p-1, generate predicate Sp. Sp Ppk is UNSAT. 41
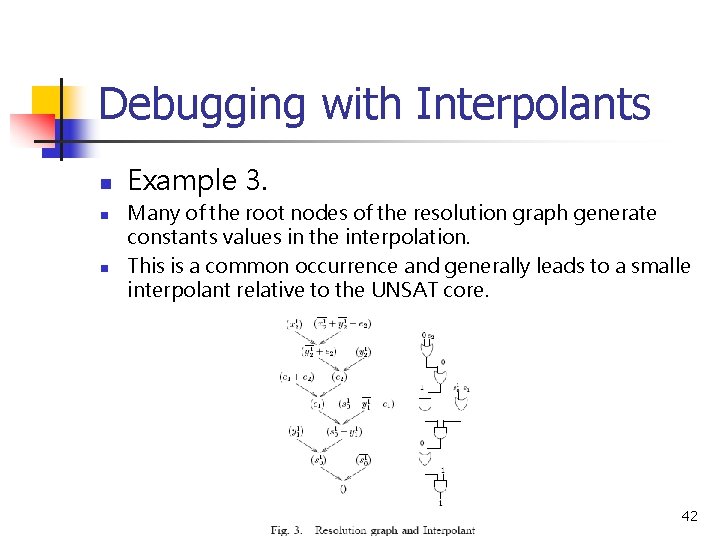
Debugging with Interpolants n n n Example 3. Many of the root nodes of the resolution graph generate constants values in the interpolation. This is a common occurrence and generally leads to a smalle interpolant relative to the UNSAT core. 42

Debugging with Interpolants n n Example 4. Shows how interpolant generated in ex. 3 can be used to debug a prefix of an error trace. Notice that the interpolant is significantly smaller once the constants have been propagated through the gates. In Fig 4, activating suspect variable, e 2, leads to the only satisfying assignment. This is consistent with the solution found in 43
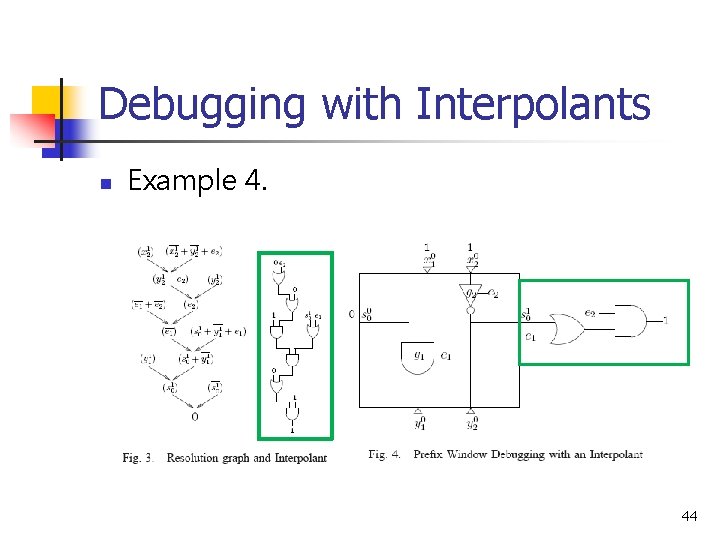
Debugging with Interpolants n Example 4. 44

Debugging with Interpolants n n n Theorem 2 Any suspect found in Debug 0 k will be found in Debug. Itp 0 p-1. Proof: n n n By definition, Debug 0 k = Debug 0 p-1 A Any satisfying assignment to Debug 0 k will satisfy Debug 0 p-1 and A But A→Ppk, so it also satisfies Ppk satisfying Debug. Itp 0 p-1 45

Debugging with Interpolants n n n Theorem 2 guarantees that solving the prefix will result in a complete method where no suspects will be missed. However Th 2 does not guarantee that spurious suspects will no be found. Ppk is used as an over-approximation for the suffix, this results in Debug. Itp 0 p-1 possibly returning suspects that will not be found when debugging the entire error trace. 46
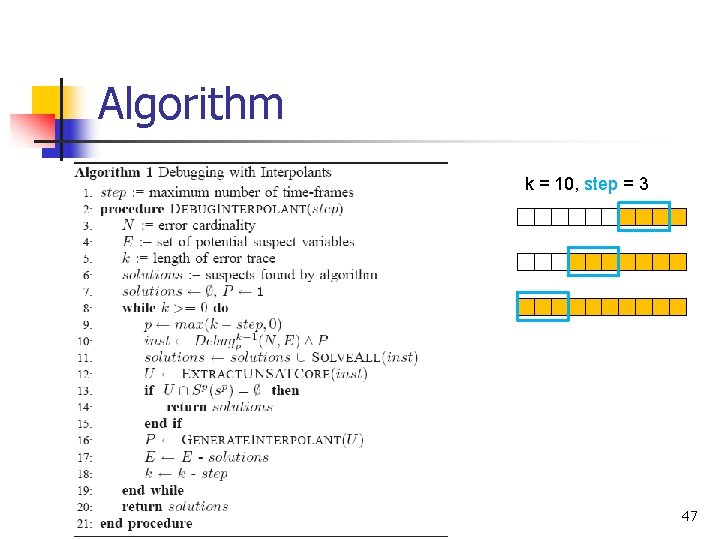
Algorithm k = 10, step = 3 47
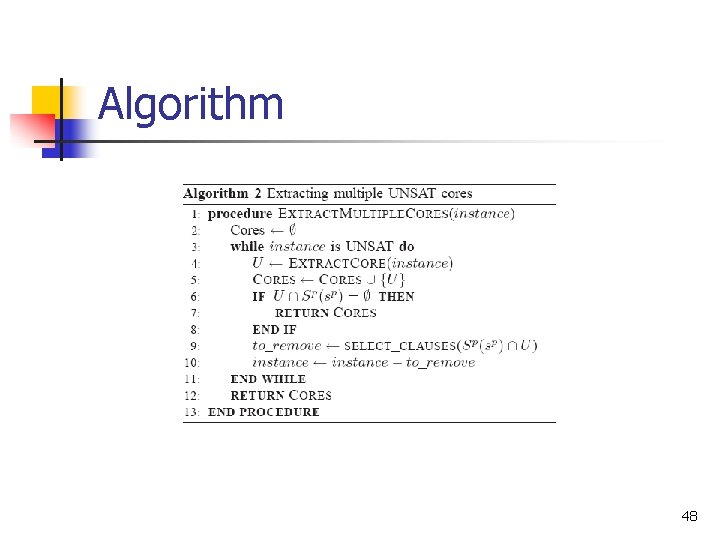
Algorithm 48
- Slides: 48