SAFE Implementation Toolkit How to use it Implementation













- Slides: 64

SAFE Implementation Toolkit How to use it

Implementation toolkit • • • Overview Log-in Contents Search Toolkit Use Log-out

Contents Subject Slide Overview 4 Log-in 5 Toolkit Webpage Log-in 6 SAFE Website Log-in 10 General topics 17 Document Access 18 Search 24 Discussion Board 25 Toolkit Use 29 Implementation Process 30 Discover 33 Diagnose 36 Document 41 Decide 46 Deliver 53 Application Enablement 54 Issuer Selection 57 Credentialing 59 Log-out 62 Conclusion 64

Implementation toolkit • This presentation provides the user: – An overview of the SAFE toolkit and instructions to use the presentation most effectively

Implementation Toolkit Log -in • This section provides the user insight into two methods to log-in to the toolkit – Via the Toolkit Webpage off the SAFE Website – From within Live. Link

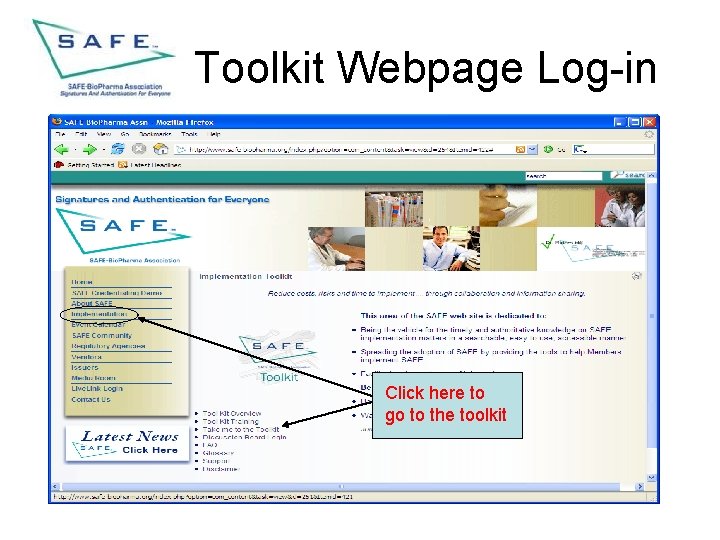
Toolkit Webpage Log-in • Log-in from the Toolkit Webpage • This section explains how to log in to the toolkit from the Toolkit Webpage

Toolkit Webpage Log-in Click here to go to the toolkit

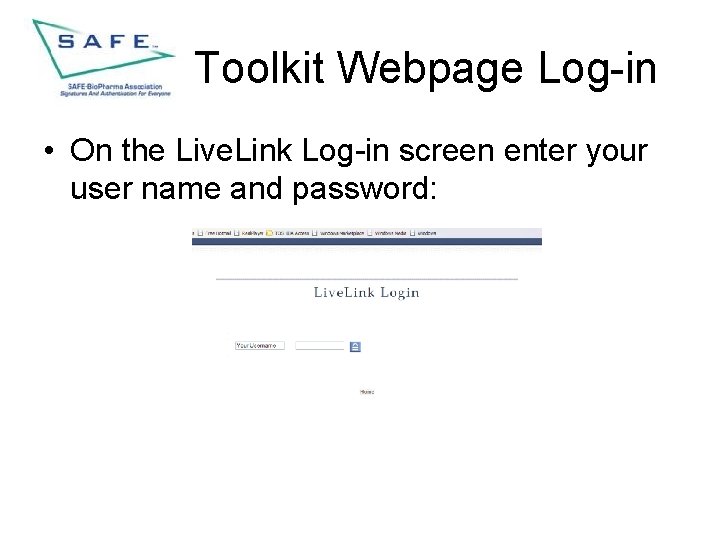
Toolkit Webpage Log-in • On the Live. Link Log-in screen enter your user name and password:

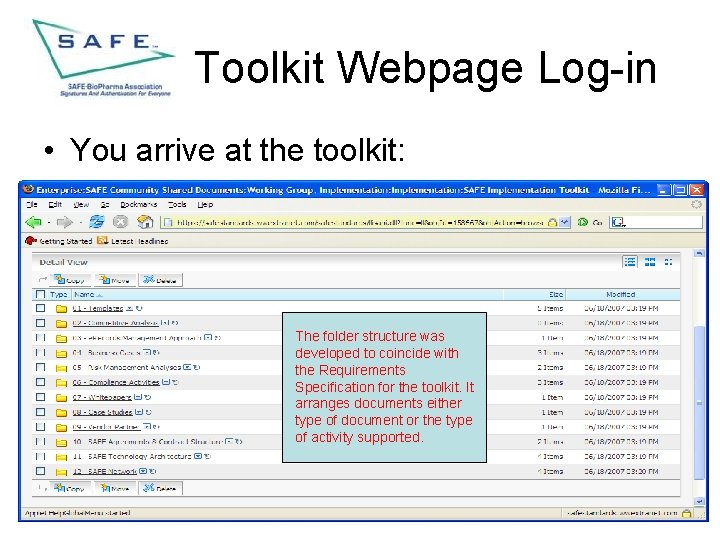
Toolkit Webpage Log-in • You arrive at the toolkit: The folder structure was developed to coincide with the Requirements Specification for the toolkit. It arranges documents either type of document or the type of activity supported.

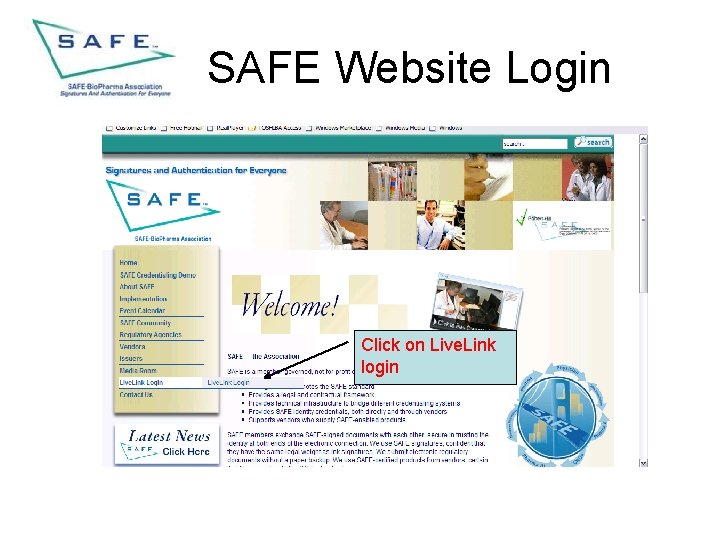
SAFE Website Login • This section provides directions to log-in to the toolkit from the SAFE-Bio. Pharma webpage

SAFE Website Login Click on Live. Link login

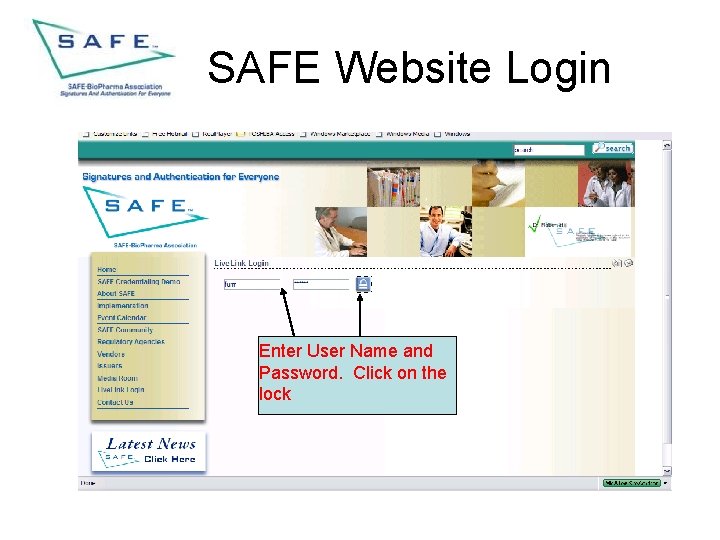
SAFE Website Login Enter User Name and Password. Click on the lock

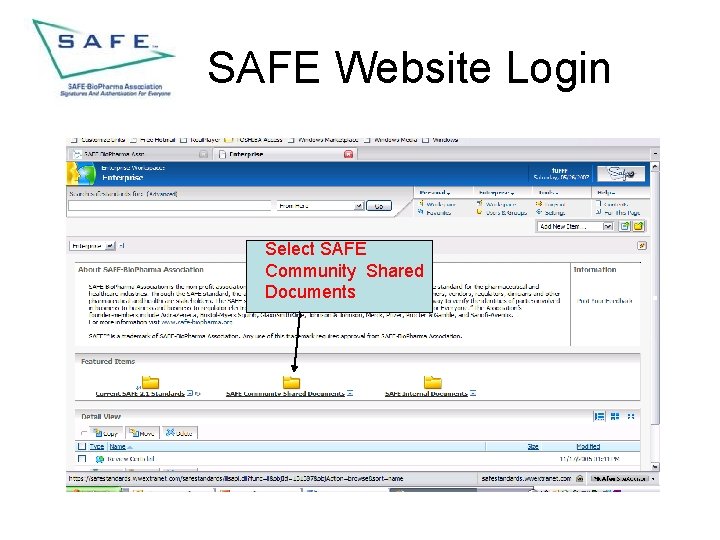
SAFE Website Login Select SAFE Community Shared Documents

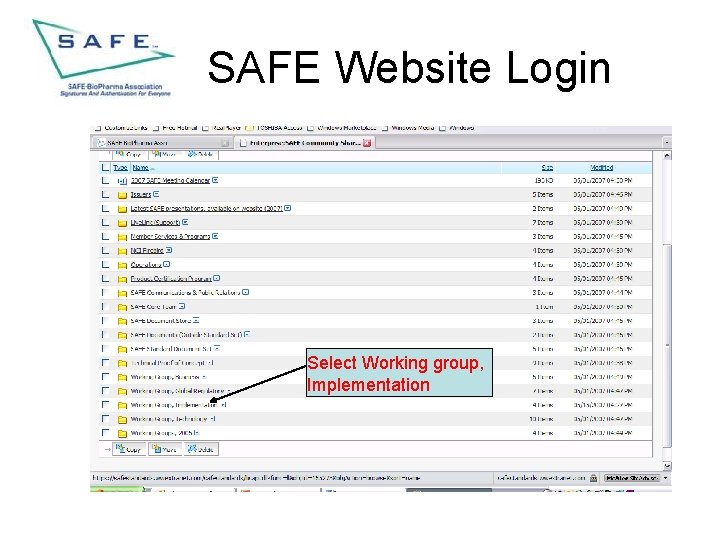
SAFE Website Login Select Working group, Implementation

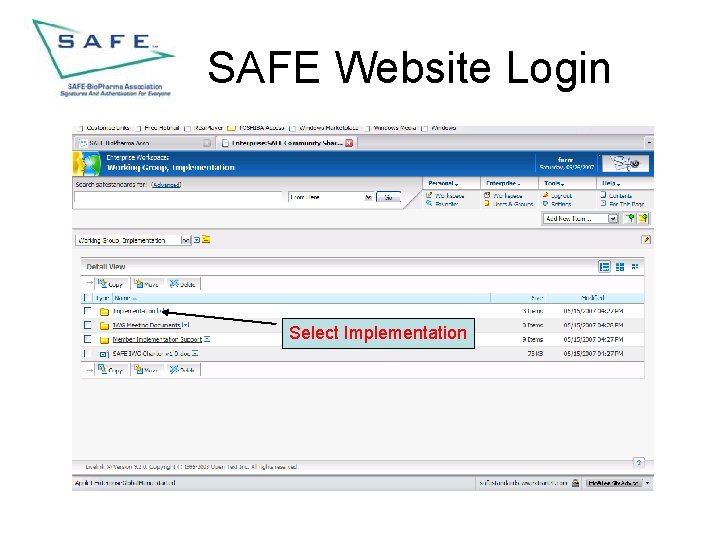
SAFE Website Login Select Implementation

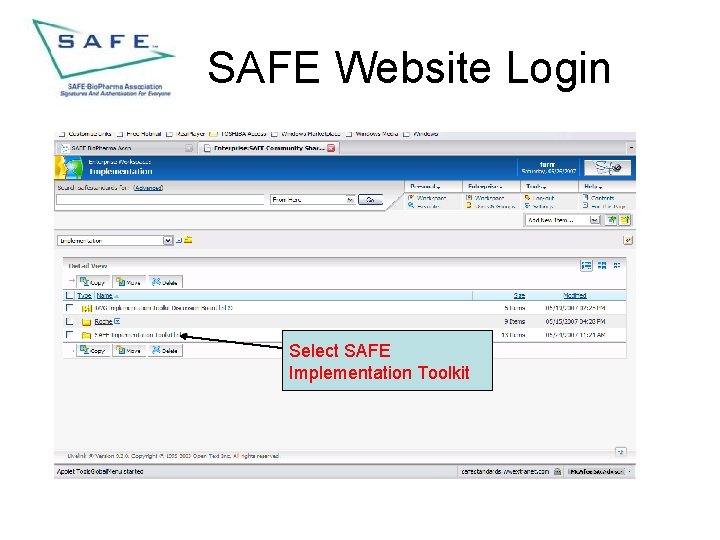
SAFE Website Login Select SAFE Implementation Toolkit

General topics • This section provides guidance for use of the toolkit in some general areas: – Document access – Search capabilities – Discussion board use

Document Access • This section shows how to access documents and how to use the actions pick list

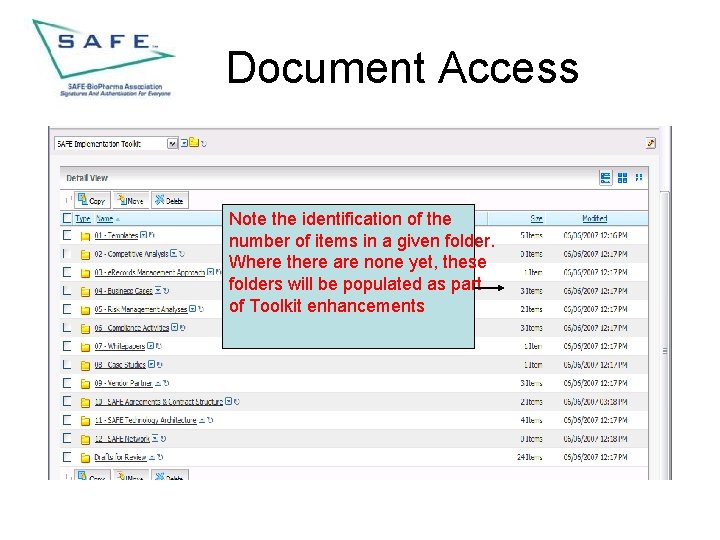
Document Access Note the identification of the number of items in a given folder. Where there are none yet, these folders will be populated as part of Toolkit enhancements

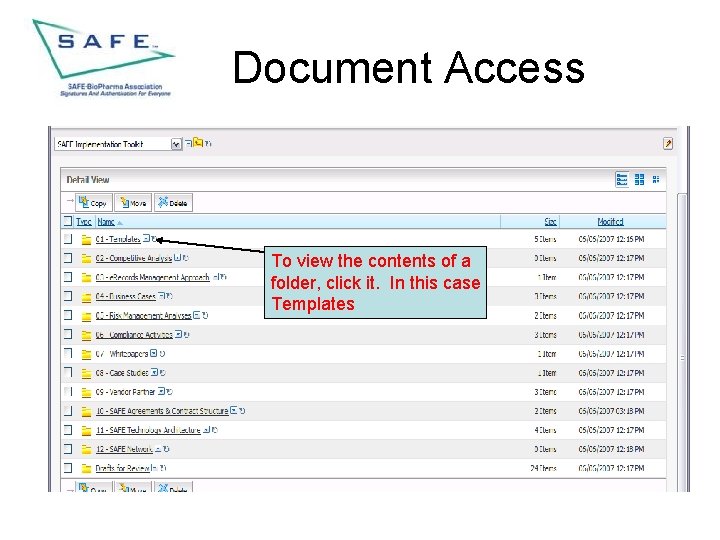
Document Access To view the contents of a folder, click it. In this case Templates

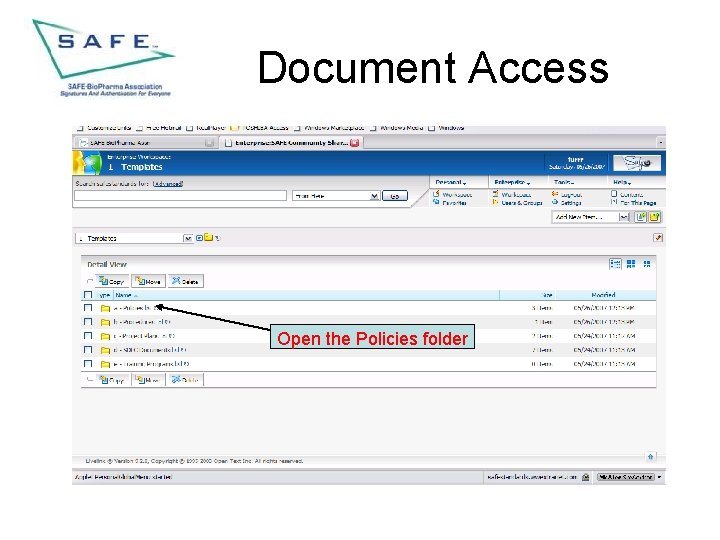
Document Access Open the Policies folder

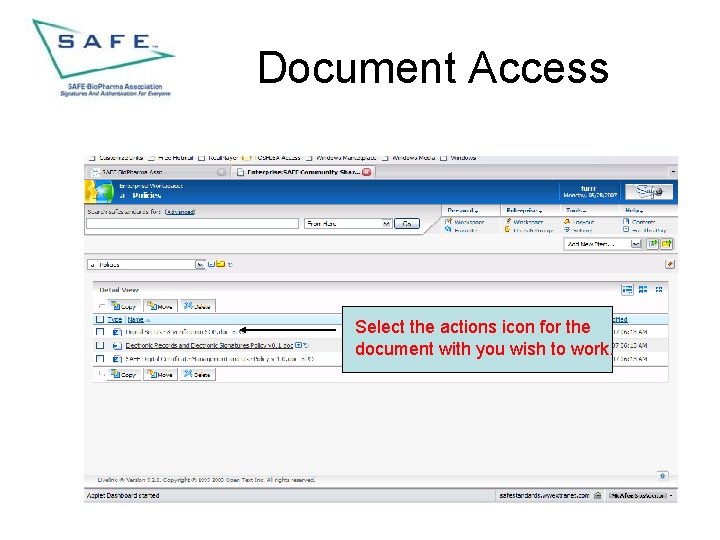
Document Access Select the actions icon for the document with you wish to work.

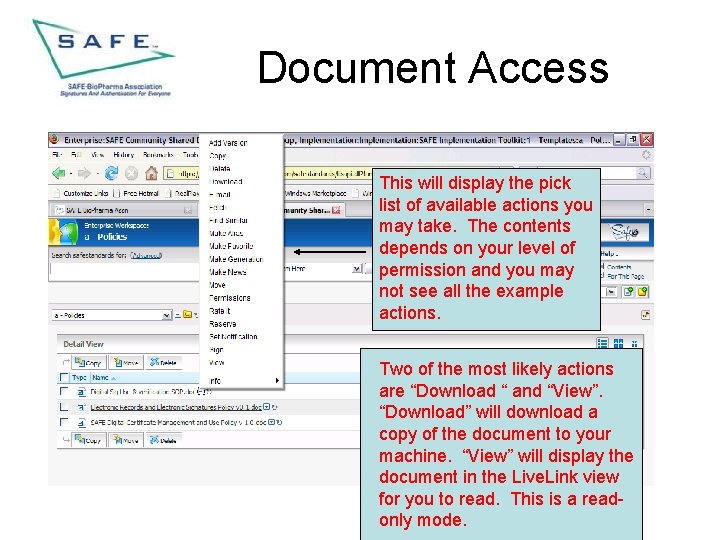
Document Access This will display the pick list of available actions you may take. The contents depends on your level of permission and you may not see all the example actions. Two of the most likely actions are “Download “ and “View”. “Download” will download a copy of the document to your machine. “View” will display the document in the Live. Link view for you to read. This is a readonly mode.

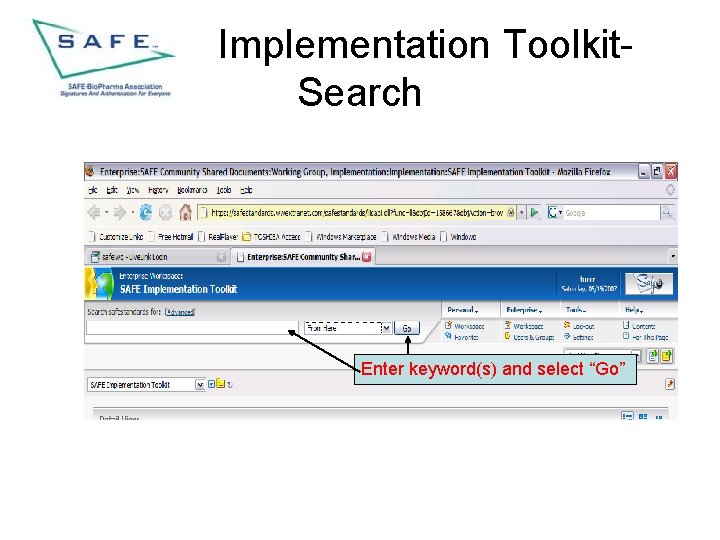
Implementation Toolkit. Search Enter keyword(s) and select “Go”

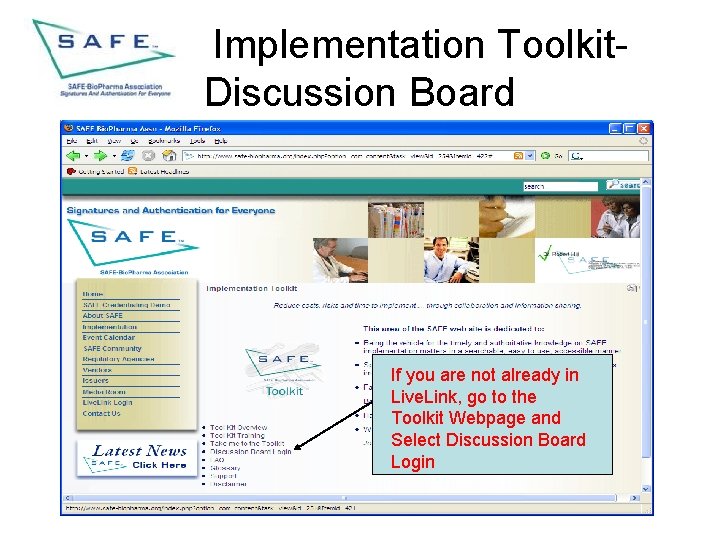
Implementation Toolkit. Discussion Board If you are not already in Live. Link, go to the Toolkit Webpage and Select Discussion Board Login

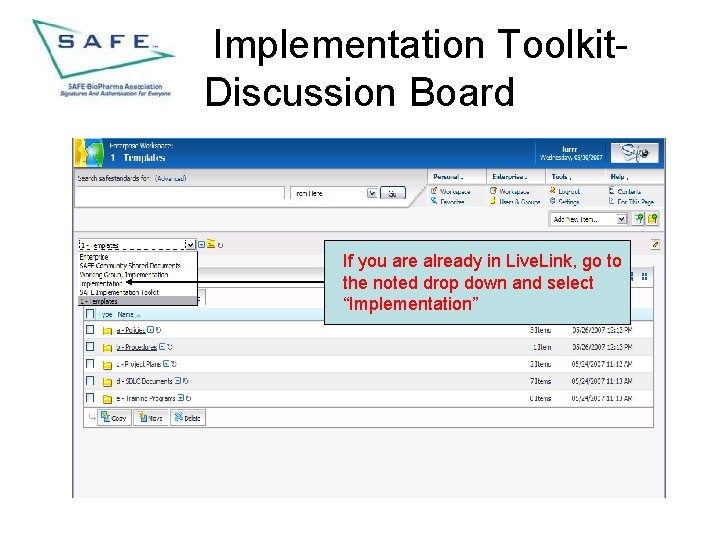
Implementation Toolkit. Discussion Board If you are already in Live. Link, go to the noted drop down and select “Implementation”

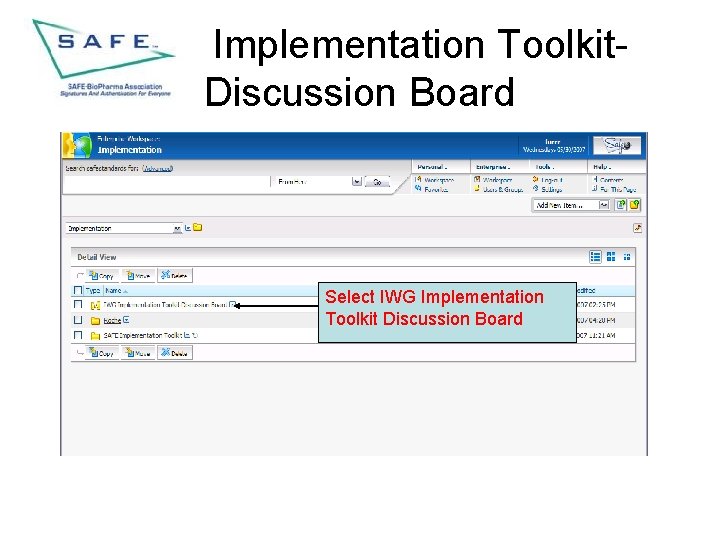
Implementation Toolkit. Discussion Board Select IWG Implementation Toolkit Discussion Board

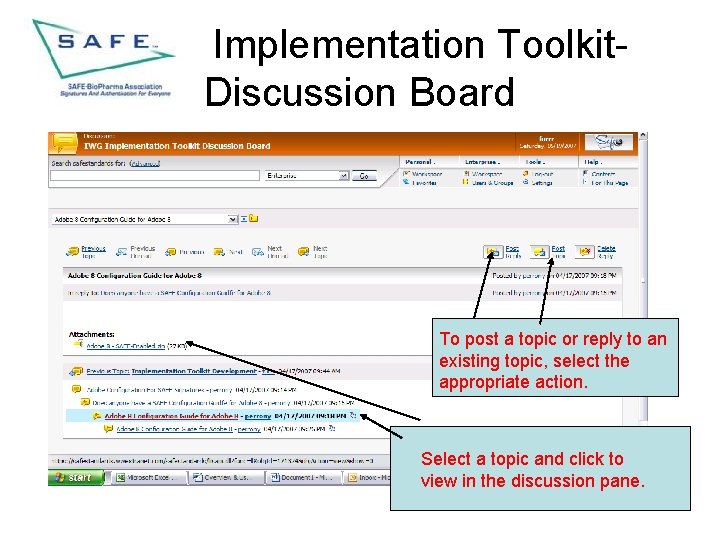
Implementation Toolkit. Discussion Board To post a topic or reply to an existing topic, select the appropriate action. Select a topic and click to view in the discussion pane.

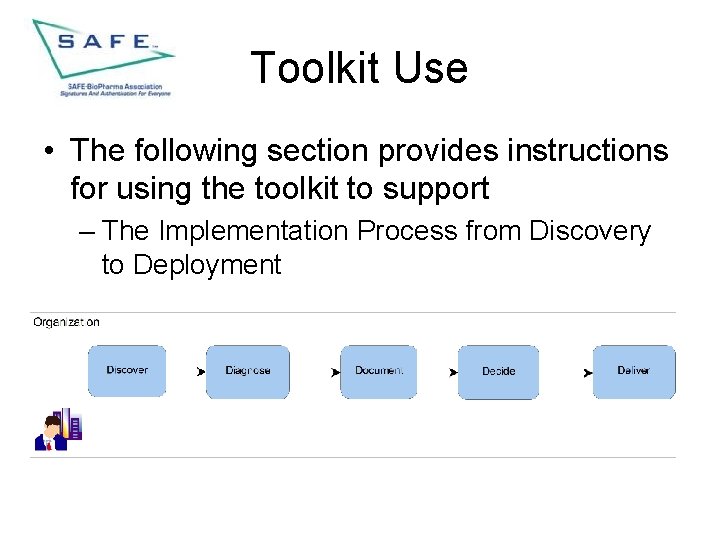
Toolkit Use • The following section provides instructions for using the toolkit to support – The Implementation Process from Discovery to Deployment

Implementation Process • • • Discover - A prospective Member organization becomes aware of the existence of SAFE-Bio. Pharma, Assn and wishes to “discover” more about what it is and what “need” it meets. Diagnose - This phase relates to using the various documents to review the options available to implement a public key infrastructure (PKI) infrastructure. Document - The documents that support this phase provide the background and knowledge required to understand, from a SAFE perspective, subjects such as electronic identity management, how to use and verify digital signatures on documents, the contract structure and rights and responsibilities of the various participants that subscribe to the SAFE Standard. Other documents provide insight into legal and regulatory rationale for a structured approach to the use of electronic records, how SAFE and the FDA interact and a legal analysis of the use of digital signatures. All this information adds to the base of knowledge supporting the implementation of SAFE-enabled applications and can be used by both non-Member and Member companies.

Implementation Process • • Decide - The documents supporting this phase are more specific to supporting the actual decision to implement. These document include templates for SOP’s, template project plans, SAFE functional and technical specifications to assist in identifying the requirements that must be met by any SAFE-enabled implementation and checklists to assist the project planner and team. Deliver - Within this phase of implementation there are three separate, but closely related sub-phases and each is supported by a set of tools in the toolkit.

Deliver Sub-phases • • • Application enablement - The documents supporting this phase provide guidance regarding compliance with the SAFE Standard and also 21 CFR, Pt 11, as well as implementation methodology agnostic templates model documents supporting system lifecycle development. These later documents may be modified to meet the specific internal methodology that any specific implementing organization might use. Issuer Selection - The documents supporting this phase specifically support the decision to either implement an internal PKI or to seek the services of an external third party Issuer (which includes a registration authority (RA) and a certification authority (CA). The documents include those form the SAFE Standard document set that specify the requirements for an RA and CA and end user devices which host the end user digital identity certificates and the specific technical documents that describe the SAFE certificate policies and profiles that a CA must meet in order to work within the SAFE system. The final document in this section describes the process an internal PKI must complete in order to cross certify with the SAFE Bridge Certification Authority and be part of the SAFE system of trust. Credentialing – The documents supporting this final phase include the current documents that support the provisioning of credentials to users using the SAFE Registration and Certificate configuration Authority (RACCA) system. If SAFE adds additional credentialing mechanisms, documents will be added.

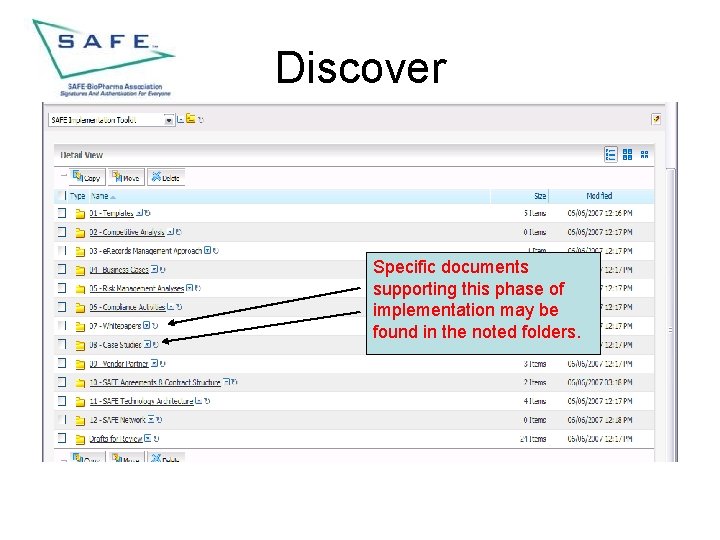
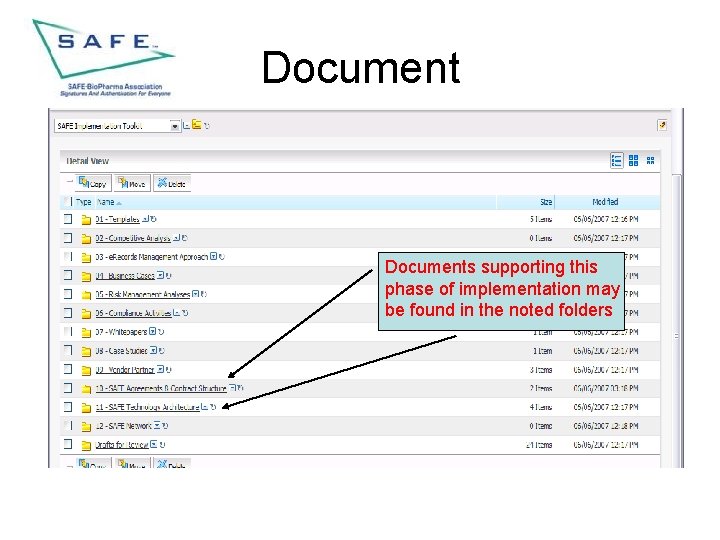
Discover Specific documents supporting this phase of implementation may be found in the noted folders.

Discover In the 7 - Whitepapers folder

Discover In the 8 - Case Studies folder

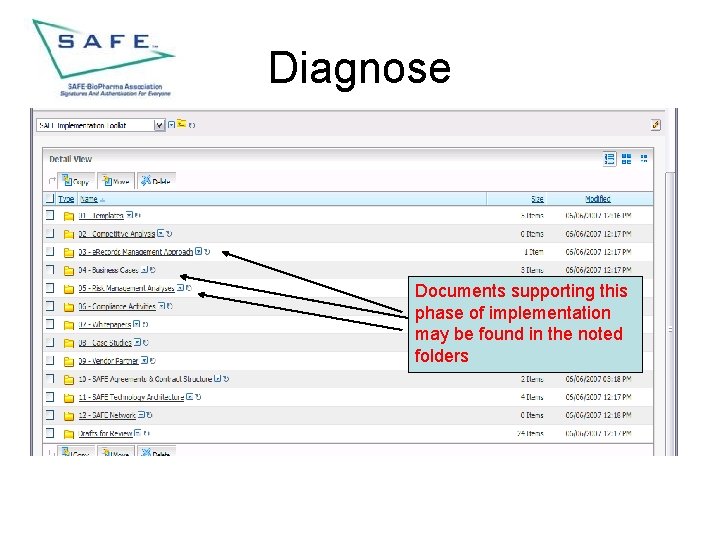
Diagnose Documents supporting this phase of implementation may be found in the noted folders

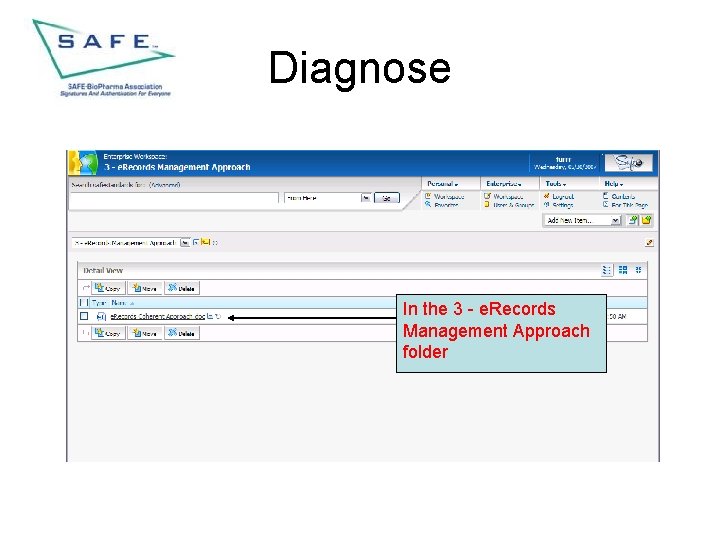
Diagnose In the 3 - e. Records Management Approach folder

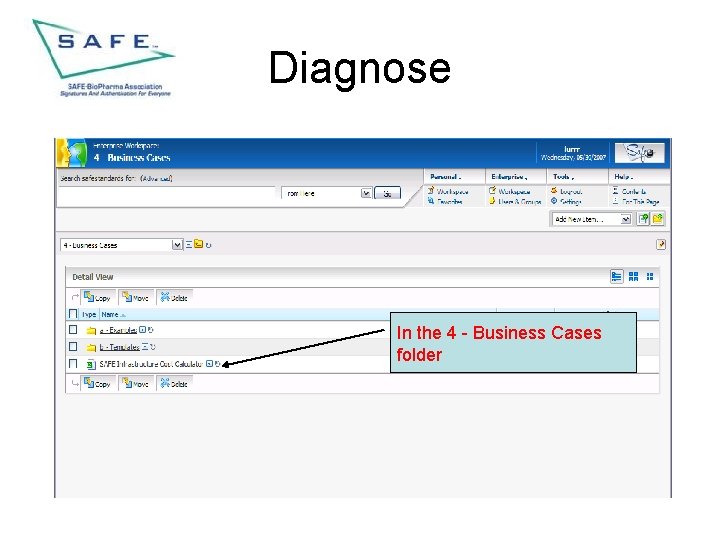
Diagnose In the 4 - Business Cases folder

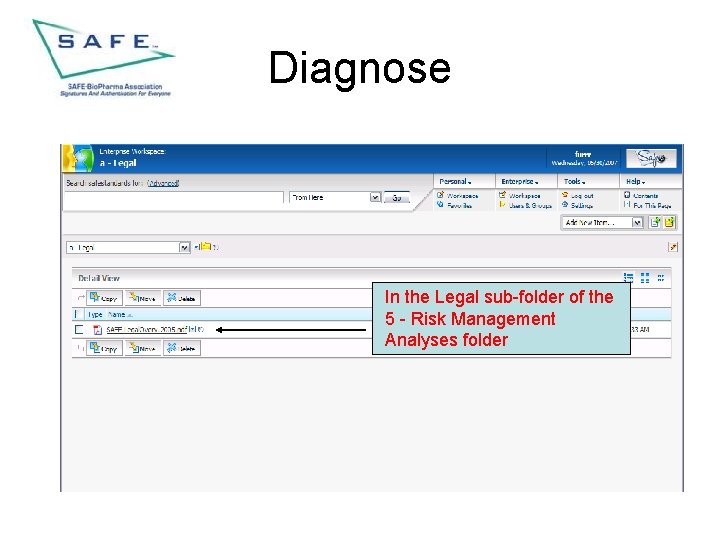
Diagnose In the Legal sub-folder of the 5 - Risk Management Analyses folder

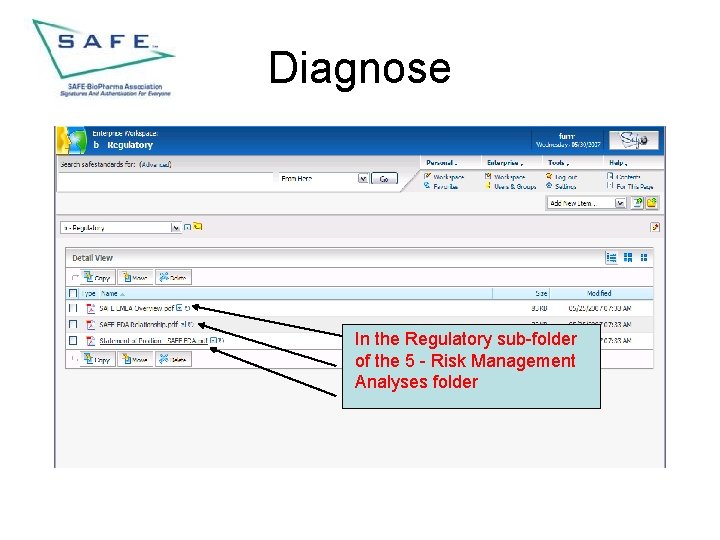
Diagnose In the Regulatory sub-folder of the 5 - Risk Management Analyses folder

Documents supporting this phase of implementation may be found in the noted folders

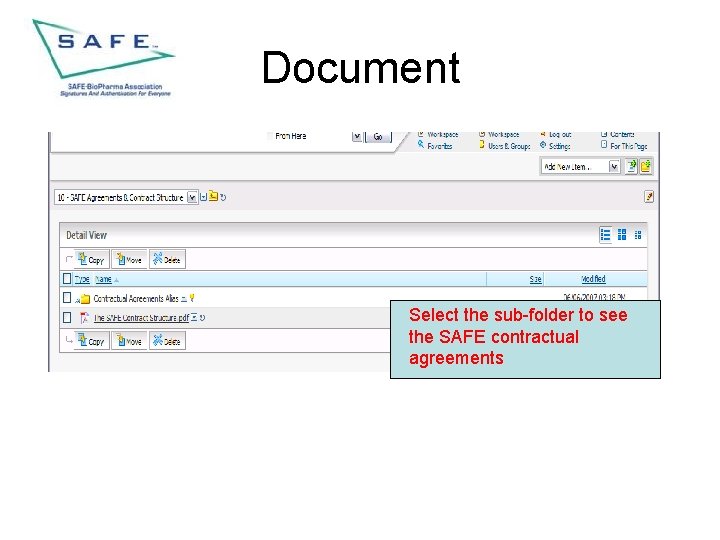
Document Select the sub-folder to see the SAFE contractual agreements

Document

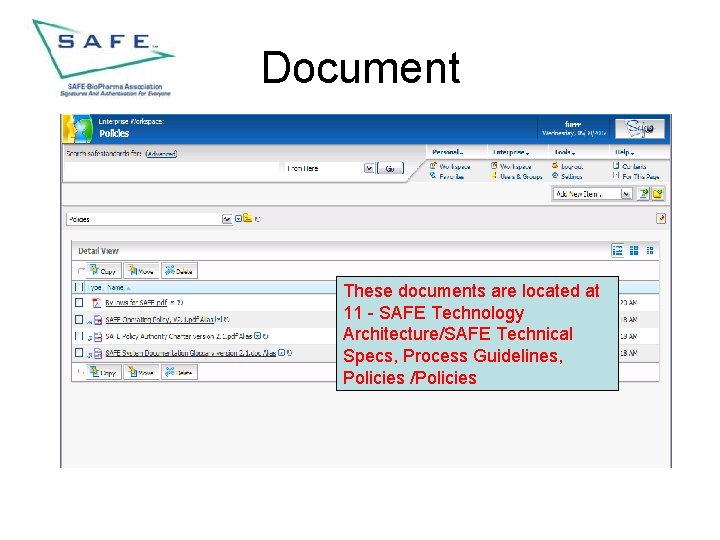
Document These documents are located at 11 - SAFE Technology Architecture/SAFE Technical Specs, Process Guidelines, Policies /Policies

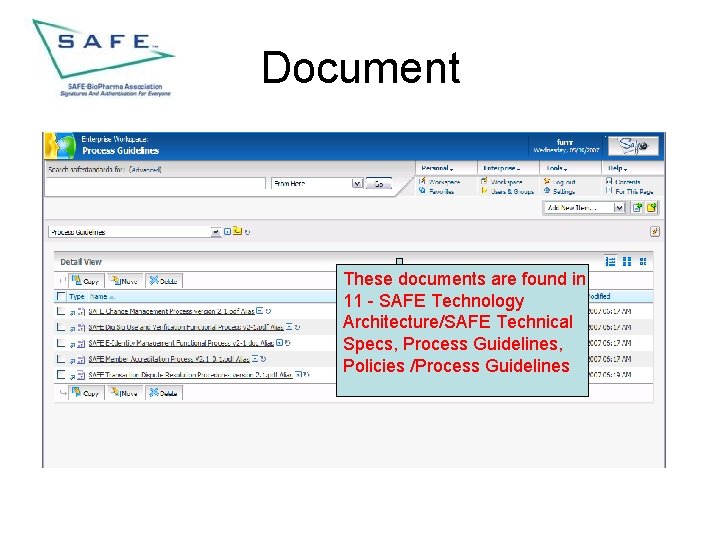
Document These documents are found in 11 - SAFE Technology Architecture/SAFE Technical Specs, Process Guidelines, Policies /Process Guidelines

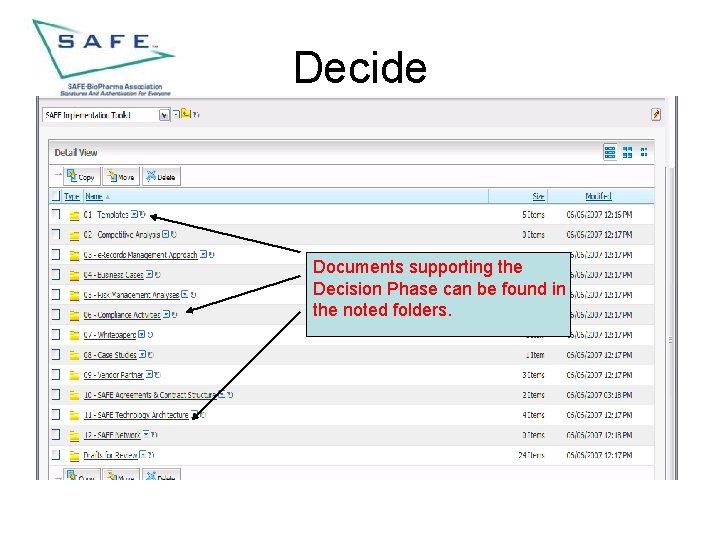
Decide Documents supporting the Decision Phase can be found in the noted folders.

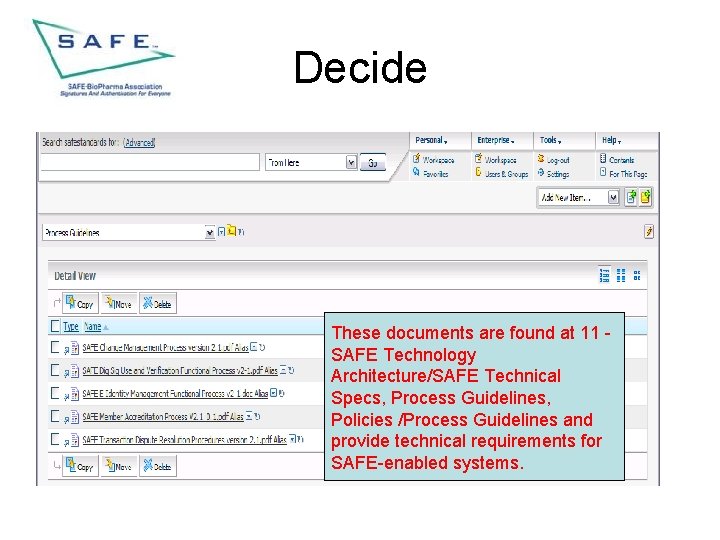
Decide These documents are found at 11 SAFE Technology Architecture/SAFE Technical Specs, Process Guidelines, Policies /Process Guidelines and provide technical requirements for SAFE-enabled systems.

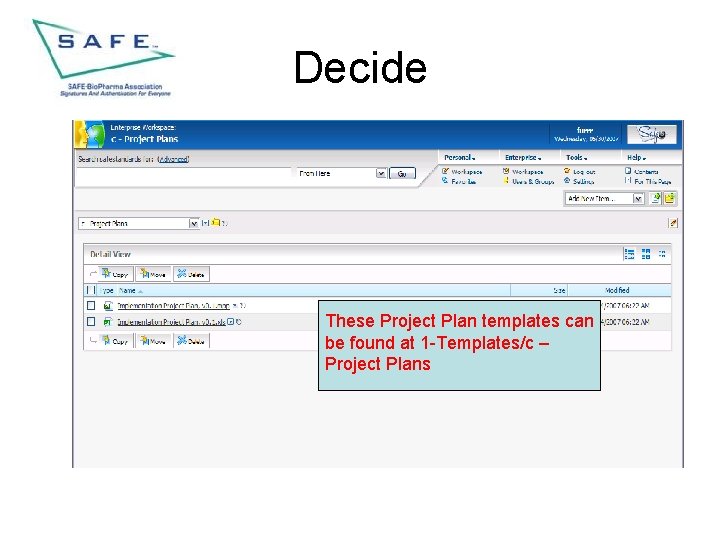
Decide These Project Plan templates can be found at 1 -Templates/c – Project Plans

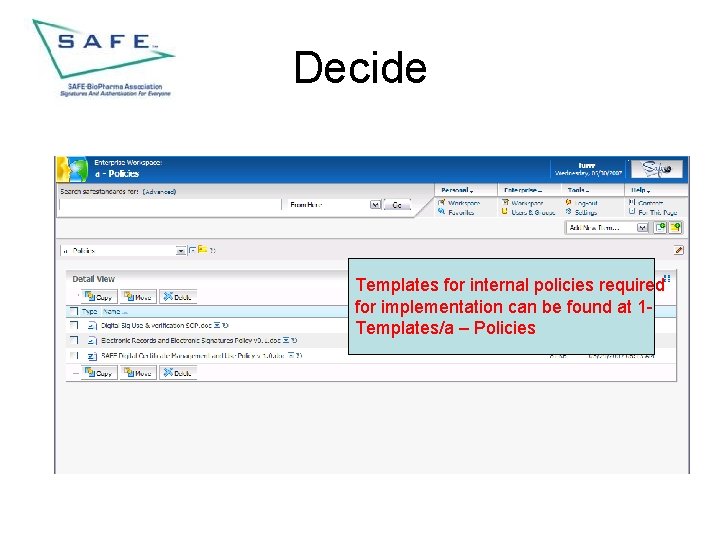
Decide Templates for internal policies required for implementation can be found at 1 Templates/a – Policies

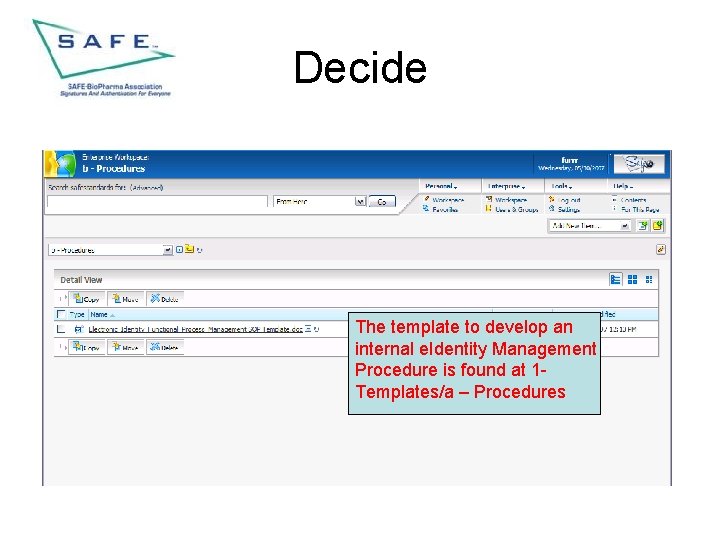
Decide The template to develop an internal e. Identity Management Procedure is found at 1 Templates/a – Procedures

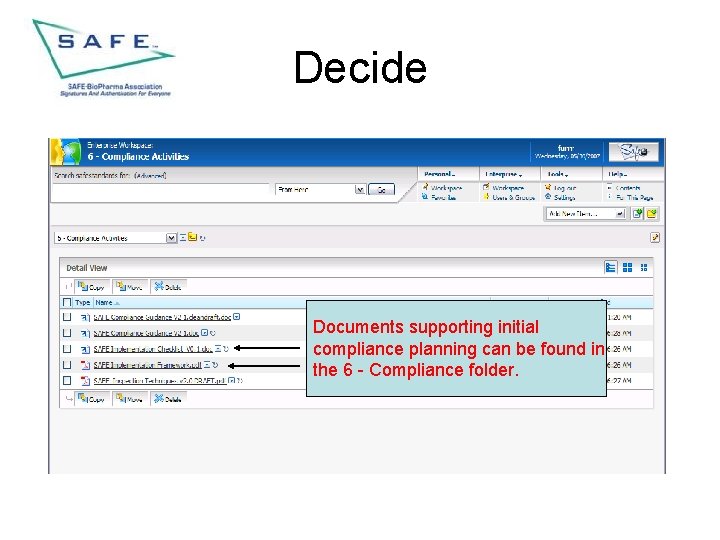
Decide Documents supporting initial compliance planning can be found in the 6 - Compliance folder.

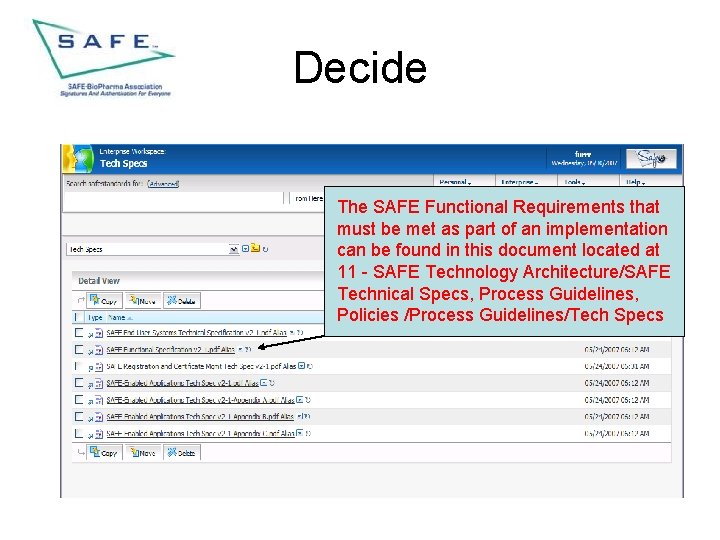
Decide The SAFE Functional Requirements that must be met as part of an implementation can be found in this document located at 11 - SAFE Technology Architecture/SAFE Technical Specs, Process Guidelines, Policies /Process Guidelines/Tech Specs

Deliver • There are three sub-phases in the Deliver Phase – Application Enablement – Issuer Selection – Credentialing

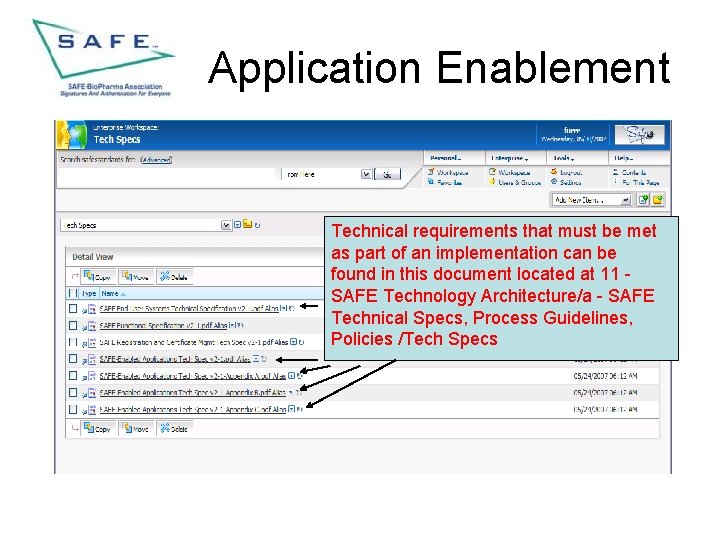
Application Enablement Technical requirements that must be met as part of an implementation can be found in this document located at 11 SAFE Technology Architecture/a - SAFE Technical Specs, Process Guidelines, Policies /Tech Specs

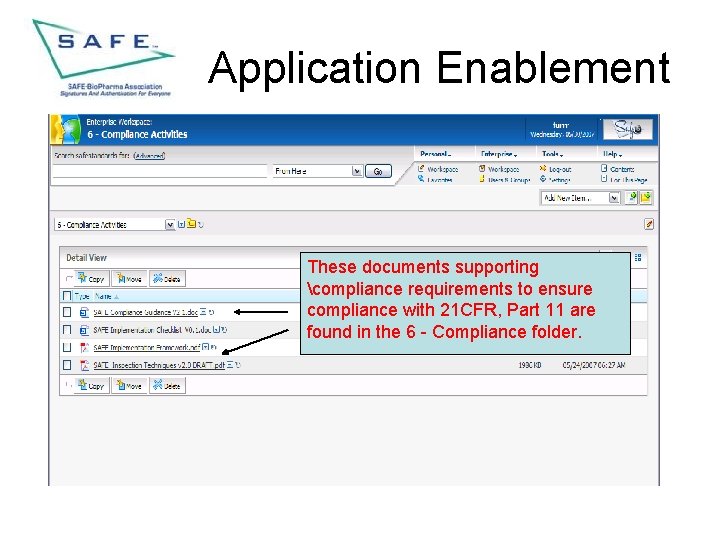
Application Enablement These documents supporting compliance requirements to ensure compliance with 21 CFR, Part 11 are found in the 6 - Compliance folder.

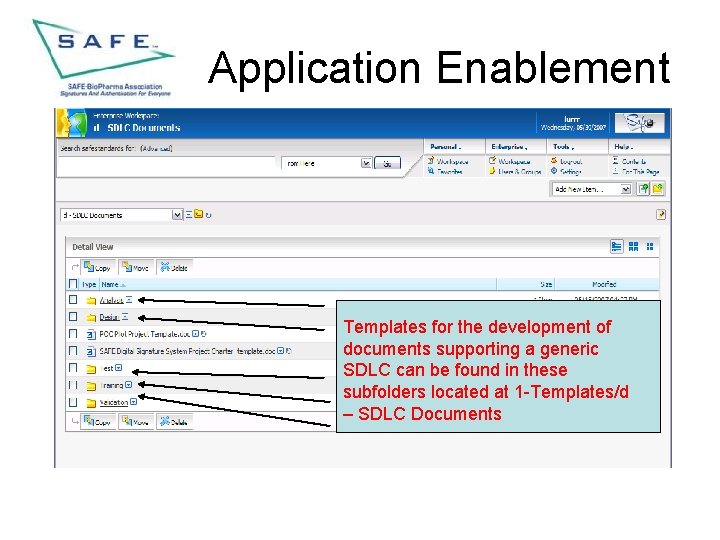
Application Enablement Templates for the development of documents supporting a generic SDLC can be found in these subfolders located at 1 -Templates/d – SDLC Documents

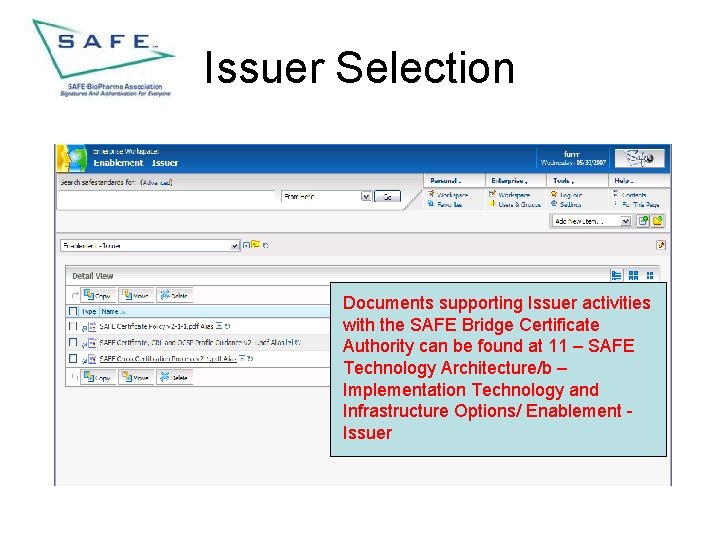
Issuer Selection Documents supporting Issuer activities with the SAFE Bridge Certificate Authority can be found at 11 – SAFE Technology Architecture/b – Implementation Technology and Infrastructure Options/ Enablement Issuer

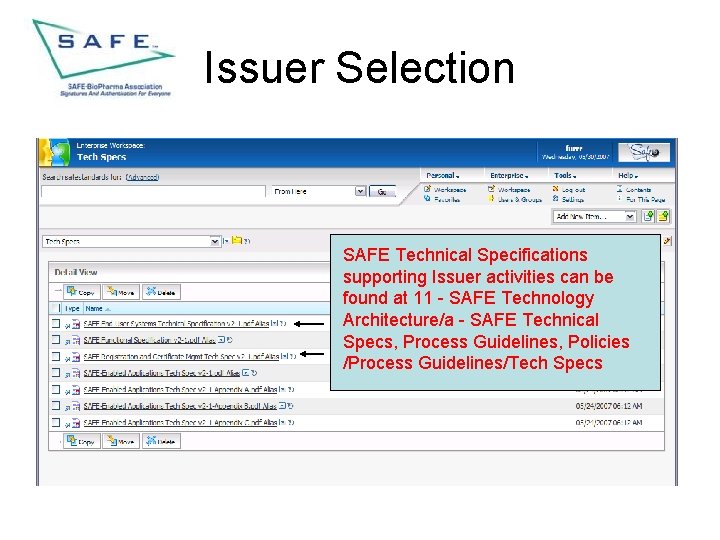
Issuer Selection SAFE Technical Specifications supporting Issuer activities can be found at 11 - SAFE Technology Architecture/a - SAFE Technical Specs, Process Guidelines, Policies /Process Guidelines/Tech Specs

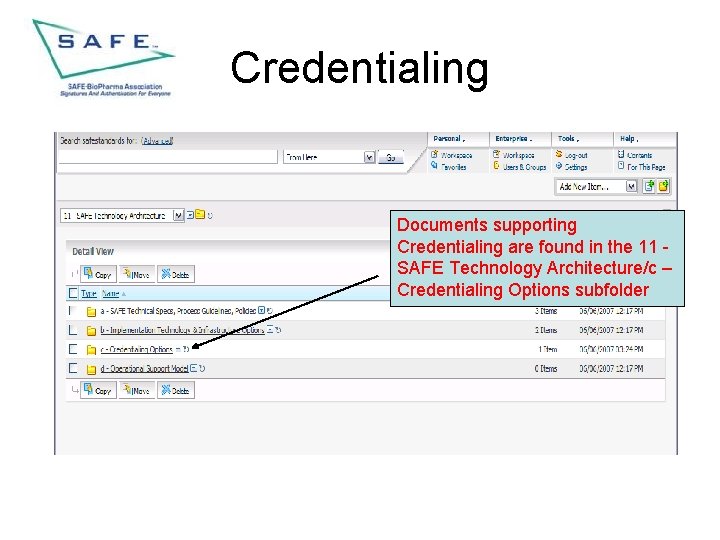
Credentialing Documents supporting Credentialing are found in the 11 SAFE Technology Architecture/c – Credentialing Options subfolder

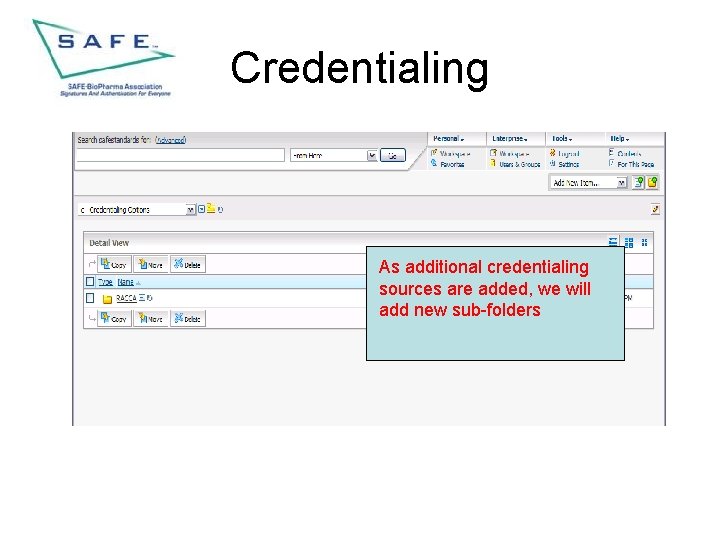
Credentialing As additional credentialing sources are added, we will add new sub-folders

Credentialing

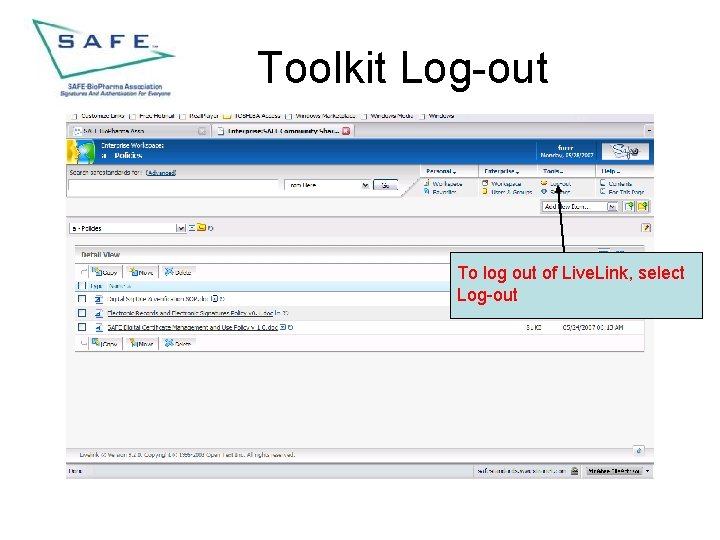
Toolkit Log-out To log out of Live. Link, select Log-out

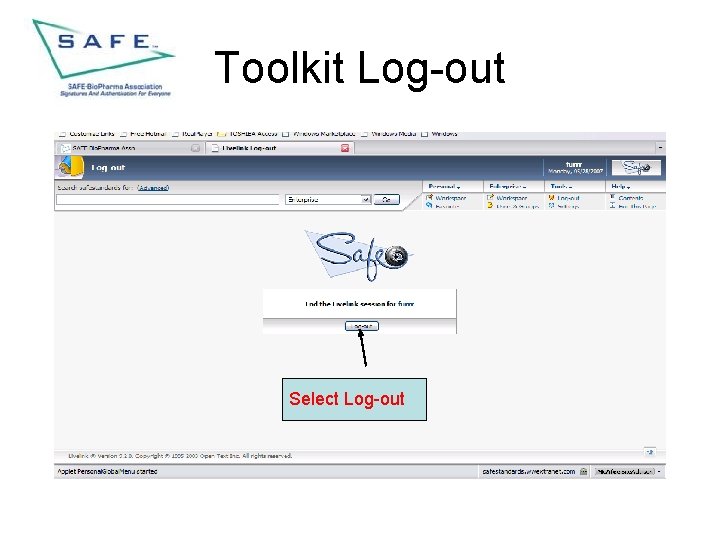
Toolkit Log-out Select Log-out

Conclusion • This completes the overview of the SAFE Implementation toolkit, • If you have questions, concerns or comments please use this link and enter a new topic on the discussion board: http: //safeiwg. googlepages. com/lllogin 2 or, submit a support request at the following link: http: //www. safebiopharma. org/index. php? option=com_content&task=vie w&id=251&Itemid=421