Safe Enterprise High Speed Encryptor Overview M Simms









- Slides: 40

Safe. Enterprise High Speed Encryptor Overview M. Simms – Senior Pre-Sales Engineer

Safe. Net HSE vs Router/Firewall VPN Cost and Performance § Requires extra memory/blades in switch/router/firewall due to loss of performance. § Loss of throughput § Layer 3 IPSec reduces throughput by as much as 40% for small packets (64 Bytes). Increased fragmentation on large packets. § Lower layer technologies – reduced latency and improved performance § Higher ongoing costs associated with IPSec management whilst HSE “configure and forget”… Security § Router not designed as security device – designed to switch/route traffic or inspect packets. § Designed to be accessed over a network – telnet etc - not appropriate for security device. Safe. Net use bespoke management system (SMC) providing secure comms and management. § Designed to be physically modified to e. g. add blades – not appropriate for security device, Safe. Net encryptors are physically tamper proof.

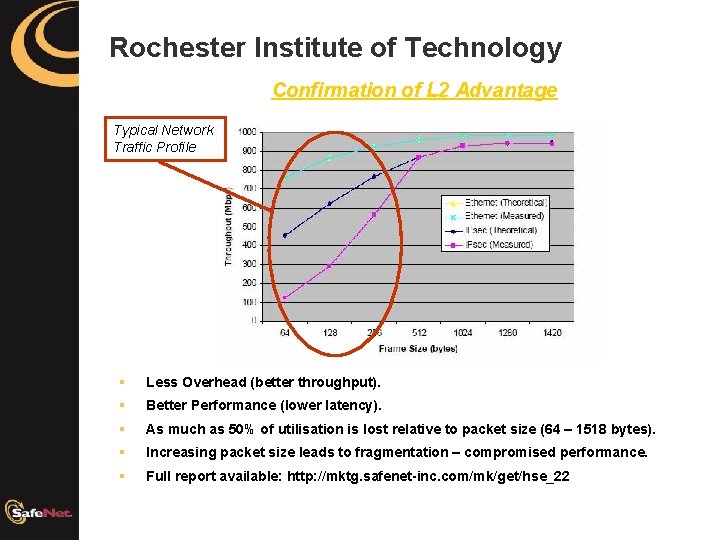
Rochester Institute of Technology Confirmation of L 2 Advantage Typical Network Traffic Profile Security § Less Overhead (better throughput). § Better Performance (lower latency). § As much as 50% of utilisation is lost relative to packet size (64 – 1518 bytes). § Increasing packet size leads to fragmentation – compromised performance. § Full report available: http: //mktg. safenet-inc. com/mk/get/hse_22

Safe. Enterprise High Speed Encryptor External Features § Rack-Mountable § Remote (Carrier) and Local (Private) interfaces (Rear) – SFP/XFP § Management port (10/100 RJ 45) for SMC (Front) § 9 -pin serial port for CLI (Front) § Warning and Status Lights § LCD and Push Button panel § Firmware upgradeable

Safe. Enterprise High Speed Encryptor Transceivers § Plug in modules supporting local and network ports § Copper RJ 45 – 10 Meg, Fast Ethernet, Gb. E § Single/multi mode – 10 Gb. E § OC 3/OC 12 single/multi mode - 155 and 622 Mbps § OC 48 single mode – 2. 488 Gbps § OC 192 single mode – 9. 952 Gbps § Fiber Transceivers plug into interface module § Short Range (2 km), Intermediate Range (15 km), and Long Range (40 km) options § LC Optical Connectors (smaller than SC) XFP SFP

Safe. Enterprise Ethernet Encryptor Overview

Safe. Enterprise Ethernet Encryptor Features § Establishes access control and data privacy for communications over vulnerable Metro Ethernet networks § Certificate based authentication RSA 2048 keys / HMAC-SHA-256 / SNMPv 3 AES § Provides full-duplex line rate encryption at speeds of 10 Mbps, 100 Mbps (Fast. Ethernet), 1 Gbps (Gb. E) and 10 Gbps § AES-256 encryption with automated key management § Selective bypass modes support VLANs and MPLS § Bump-in-the-wire design is transparent to the network – easy installation in existing environments § Common Criteria EAL 4 and FIPS 140 -2 level 3 accreditation

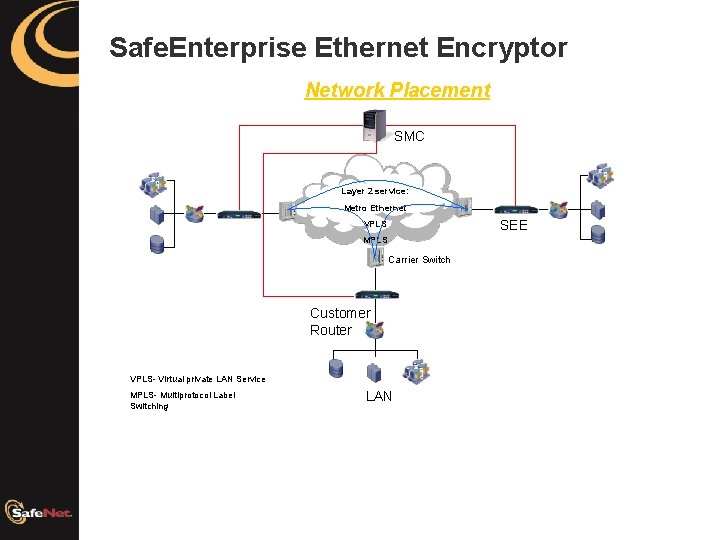
Safe. Enterprise Ethernet Encryptor Network Placement SMC Layer 2 service: Metro Ethernet SEE VPLS MPLS Carrier Switch Customer Router VPLS- Virtual private LAN Service MPLS- Multiprotocol Label Switching LAN

Ethernet Basics Overview § Carriers/Service Providers now providing long distance Ethernet “trunks” to connect sites (even intercontinental) § Referred to as Metro or Carrier Ethernet § Can be used instead of traditional WAN protocols – advantages: § No encapsulation (protocol translation) required on router – simpler, cheaper equipment § Easier IP addressing – single “flat” LAN (breaks traditional LAN/WAN division) § Familiarity with simple LAN protocol § WAN services at LAN bandwidths/speeds

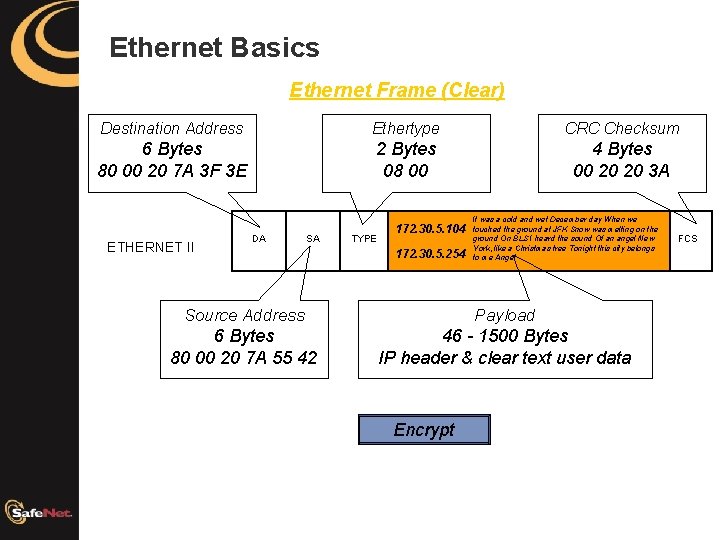
Ethernet Basics Ethernet Frame (Clear) Destination Address Ethertype CRC Checksum 6 Bytes 80 00 20 7 A 3 F 3 E 2 Bytes 08 00 4 Bytes 00 20 20 3 A ETHERNET II DA SA TYPE 172. 30. 5. 104 172. 30. 5. 254 It was a cold and wet December day When we touched the ground at JFK Snow was melting on the ground On BLS I heard the sound Of an angel New York, like a Christmas tree Tonight this city belongs to me Angel Source Address Payload 6 Bytes 80 00 20 7 A 55 42 46 - 1500 Bytes IP header & clear text user data Encrypt FCS

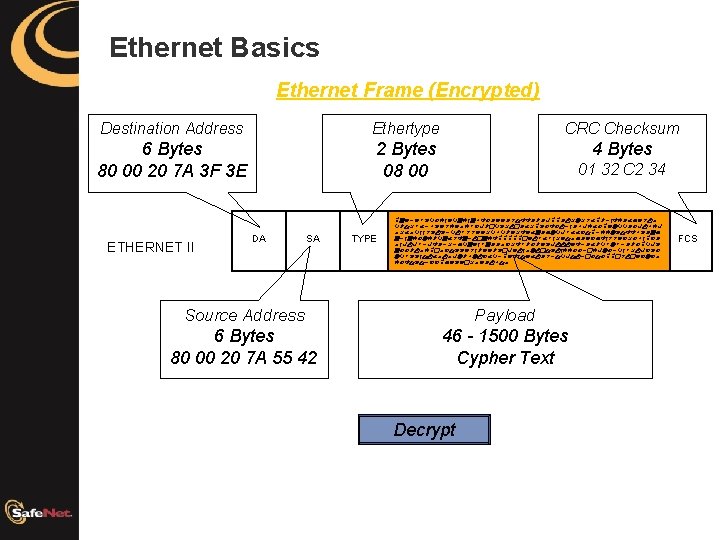
Ethernet Basics Ethernet Frame (Encrypted) Destination Address Ethertype CRC Checksum 6 Bytes 80 00 20 7 A 3 F 3 E 2 Bytes 08 00 4 Bytes ETHERNET II DA SA TYPE 01 32 C 2 34 pgyjzwvqxemyqgemgafxdyydstffdldkppdurnrsbpljmfedbhysuo qltrwbjavysezoewiklcqvrucdbrpvxfxujmdakebxpznqqdxkuaek orboqmmsvuvjquwssyyrqaqlyrfzbgdhnqkwbbitpjeenvtffavdgh gjmgexnelqgbsfgjucgefpppppczuwbwmrztohdyihfmssyirxampid omkukwjkfdjrjhqgymwgddoirfwlxlzvkuuuyfjdblqwnwjdlxpqkv gxxluoepcoitvvysmlzzlvckzumonuctvumeexxjceknxjqmwrukivx nqwvvmtubouoknlanuibqjpzfmtybudsjtqktujcxtxppcsucyinio exftvtjiiphzvzcrozduato Source Address Payload 6 Bytes 80 00 20 7 A 55 42 46 - 1500 Bytes Cypher Text Decrypt FCS

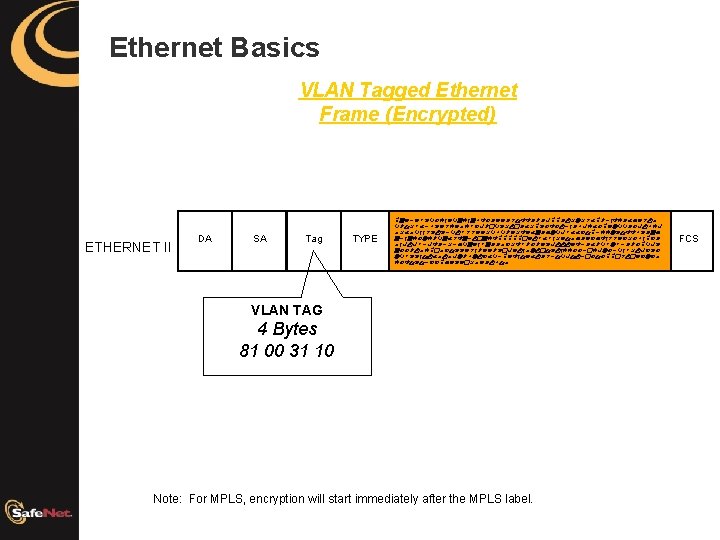
Ethernet Basics VLAN Tagged Ethernet Frame (Encrypted) ETHERNET II DA SA Tag TYPE pgyjzwvqxemyqgemgafxdyydstffdldkppdurnrsbpljmfedbhysuo qltrwbjavysezoewiklcqvrucdbrpvxfxujmdakebxpznqqdxkuaek orboqmmsvuvjquwssyyrqaqlyrfzbgdhnqkwbbitpjeenvtffavdgh gjmgexnelqgbsfgjucgefpppppczuwbwmrztohdyihfmssyirxampid omkukwjkfdjrjhqgymwgddoirfwlxlzvkuuuyfjdblqwnwjdlxpqkv gxxluoepcoitvvysmlzzlvckzumonuctvumeexxjceknxjqmwrukivx nqwvvmtubouoknlanuibqjpzfmtybudsjtqktujcxtxppcsucyinio exftvtjiiphzvzcrozduato VLAN TAG 4 Bytes 81 00 31 10 Note: For MPLS, encryption will start immediately after the MPLS label. FCS

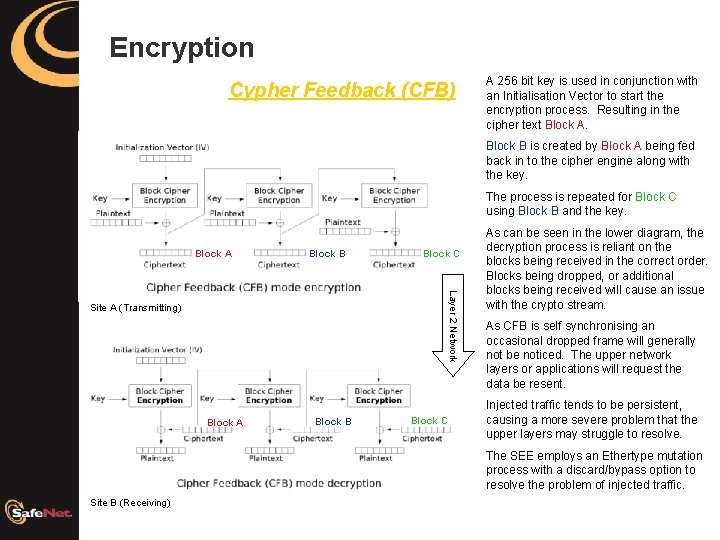
Encryption Cypher Feedback (CFB) A 256 bit key is used in conjunction with an Initialisation Vector to start the encryption process. Resulting in the cipher text Block A. Block B is created by Block A being fed back in to the cipher engine along with the key. The process is repeated for Block C using Block B and the key. Block A Block B Block C Layer 2 Network Site A (Transmitting) Block A Block B Block C As can be seen in the lower diagram, the decryption process is reliant on the blocks being received in the correct order. Blocks being dropped, or additional blocks being received will cause an issue with the crypto stream. As CFB is self synchronising an occasional dropped frame will generally not be noticed. The upper network layers or applications will request the data be resent. Injected traffic tends to be persistent, causing a more severe problem that the upper layers may struggle to resolve. The SEE employs an Ethertype mutation process with a discard/bypass option to resolve the problem of injected traffic. Site B (Receiving)

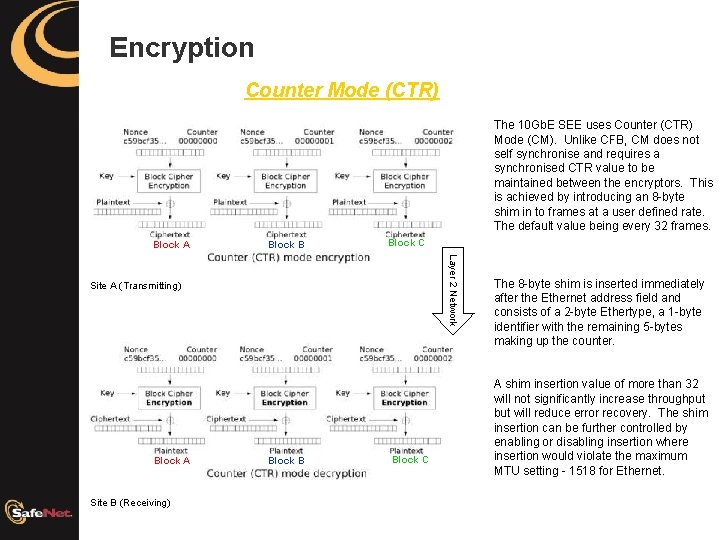
Encryption Counter Mode (CTR) The 10 Gb. E SEE uses Counter (CTR) Mode (CM). Unlike CFB, CM does not self synchronise and requires a synchronised CTR value to be maintained between the encryptors. This is achieved by introducing an 8 -byte shim in to frames at a user defined rate. The default value being every 32 frames. Block A Block B Block C Layer 2 Network Site A (Transmitting) Block A Site B (Receiving) Block B Block C The 8 -byte shim is inserted immediately after the Ethernet address field and consists of a 2 -byte Ethertype, a 1 -byte identifier with the remaining 5 -bytes making up the counter. A shim insertion value of more than 32 will not significantly increase throughput but will reduce error recovery. The shim insertion can be further controlled by enabling or disabling insertion where insertion would violate the maximum MTU setting - 1518 for Ethernet.

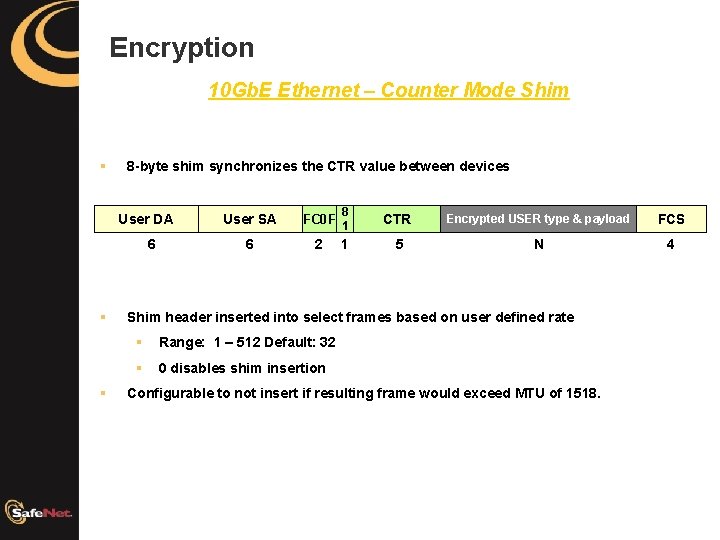
Encryption 10 Gb. E Ethernet – Counter Mode Shim § 8 -byte shim synchronizes the CTR value between devices User DA 6 § § User SA FC 0 F 8 1 CTR Encrypted USER type & payload FCS 6 2 1 5 N 4 Shim header inserted into select frames based on user defined rate § Range: 1 – 512 Default: 32 § 0 disables shim insertion Configurable to not insert if resulting frame would exceed MTU of 1518.

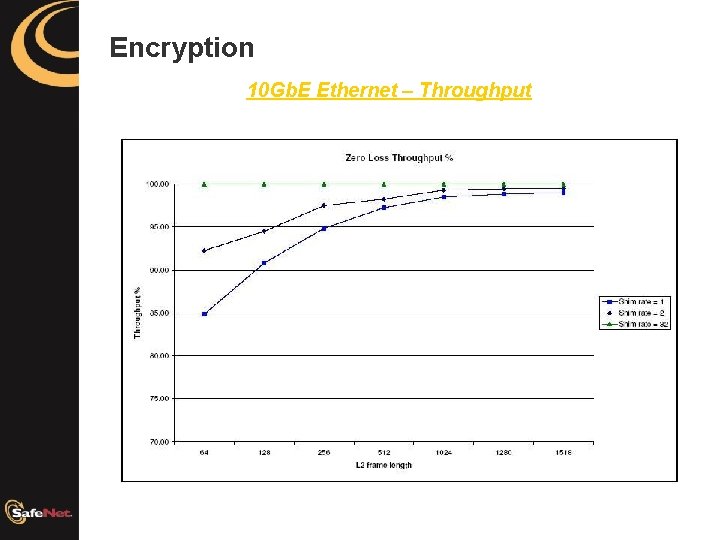
Encryption 10 Gb. E Ethernet – Throughput

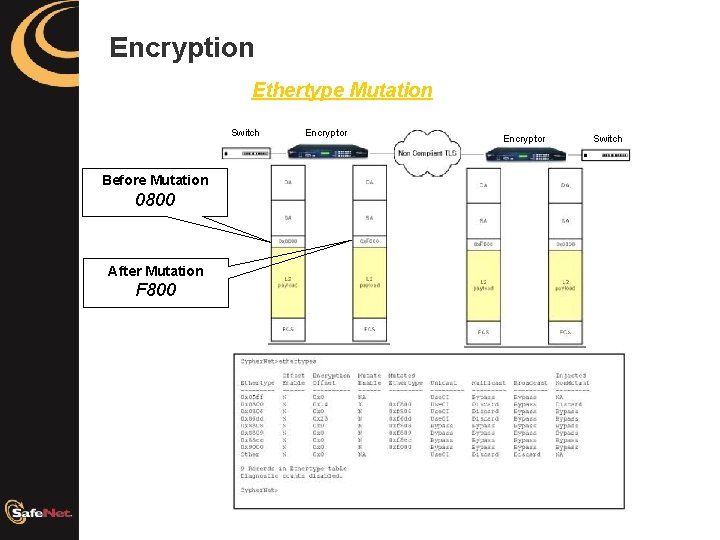
Encryption Ethertype Mutation Switch Before Mutation 0800 After Mutation F 800 Encryptor Switch

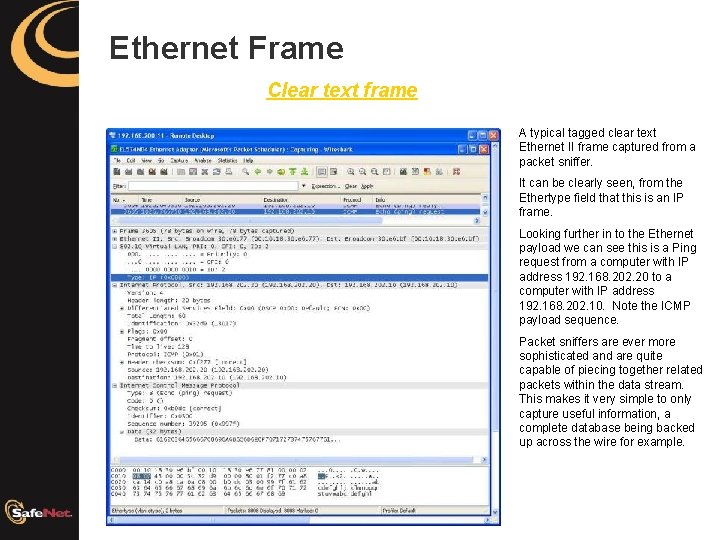
Ethernet Frame Clear text frame A typical tagged clear text Ethernet II frame captured from a packet sniffer. It can be clearly seen, from the Ethertype field that this is an IP frame. Looking further in to the Ethernet payload we can see this is a Ping request from a computer with IP address 192. 168. 202. 20 to a computer with IP address 192. 168. 202. 10. Note the ICMP payload sequence. Packet sniffers are ever more sophisticated and are quite capable of piecing together related packets within the data stream. This makes it very simple to only capture useful information, a complete database being backed up across the wire for example.

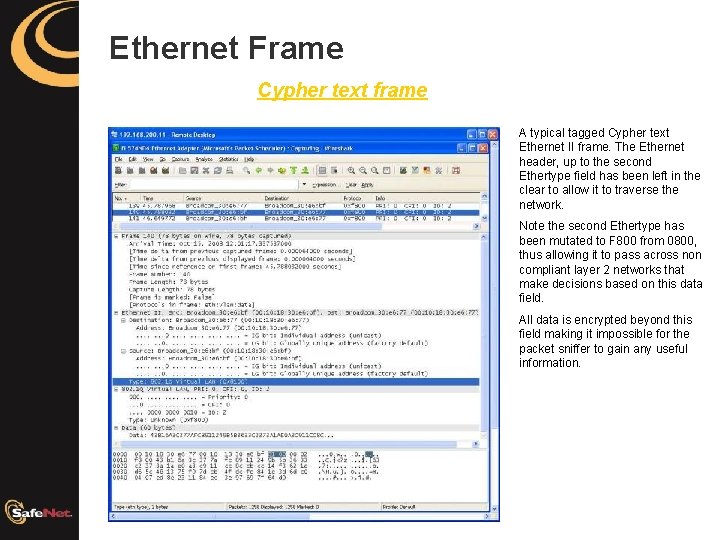
Ethernet Frame Cypher text frame A typical tagged Cypher text Ethernet II frame. The Ethernet header, up to the second Ethertype field has been left in the clear to allow it to traverse the network. Note the second Ethertype has been mutated to F 800 from 0800, thus allowing it to pass across non compliant layer 2 networks that make decisions based on this data field. All data is encrypted beyond this field making it impossible for the packet sniffer to gain any useful information.

Safe. Enterprise SONET Encryptor Overview

Safe. Enterprise SONET Encryptor Features § SONET/SDH Line/Path Encryptor § Bump-In-The-Fiber (BITF) – Transparent to switches & regenerators § Support for OC 3, OC 12, OC 48 and OC 192 links § Supports AES 256 algorithm § Certificate based authentication RSA 2048 keys / HMAC-SHA-256 / SNMPv 3 AES § Secure and simple remote management using SMC § Common Criteria EAL 4 and FIPS 140 -2 level 3 accreditation

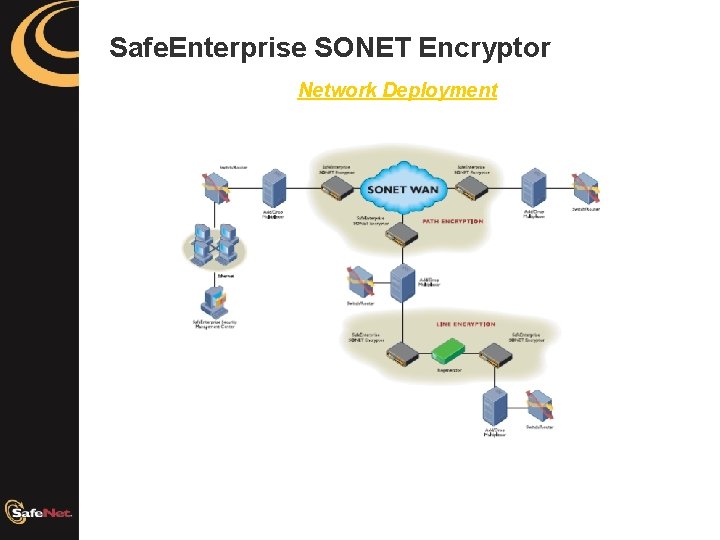
Safe. Enterprise SONET Encryptor Network Deployment

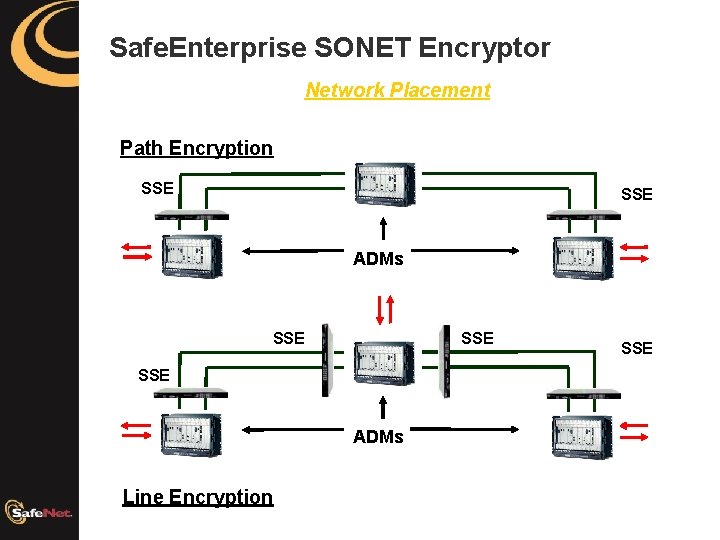
Safe. Enterprise SONET Encryptor Network Placement Path Encryption SSE ADMs SSE SSE ADMs Line Encryption SSE

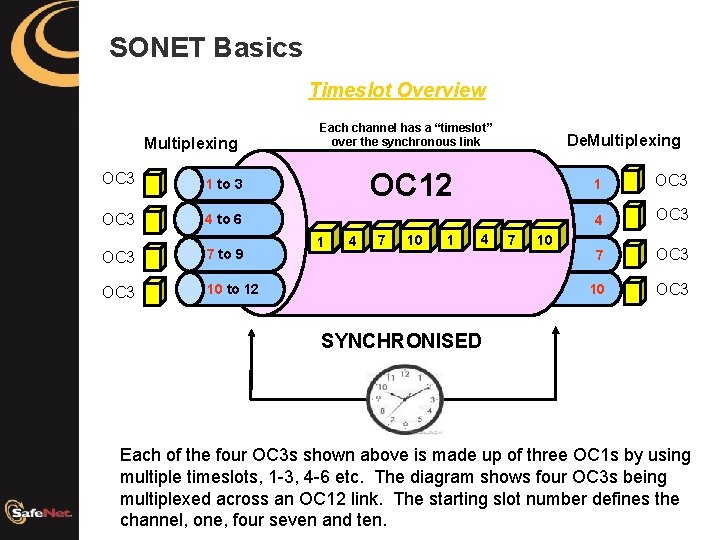
SONET Basics Timeslot Overview Multiplexing OC 3 1 to 3 OC 3 4 to 6 OC 3 7 to 9 OC 3 10 to 12 Each channel has a “timeslot” over the synchronous link De. Multiplexing OC 12 1 4 7 10 1 OC 3 4 OC 3 7 OC 3 10 OC 3 SYNCHRONISED Each of the four OC 3 s shown above is made up of three OC 1 s by using multiple timeslots, 1 -3, 4 -6 etc. The diagram shows four OC 3 s being multiplexed across an OC 12 link. The starting slot number defines the channel, one, four seven and ten.

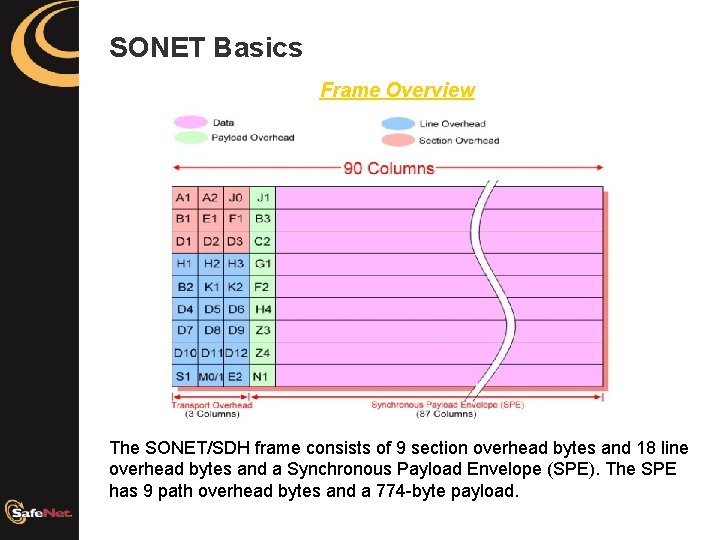
SONET Basics Frame Overview The SONET/SDH frame consists of 9 section overhead bytes and 18 line overhead bytes and a Synchronous Payload Envelope (SPE). The SPE has 9 path overhead bytes and a 774 -byte payload.

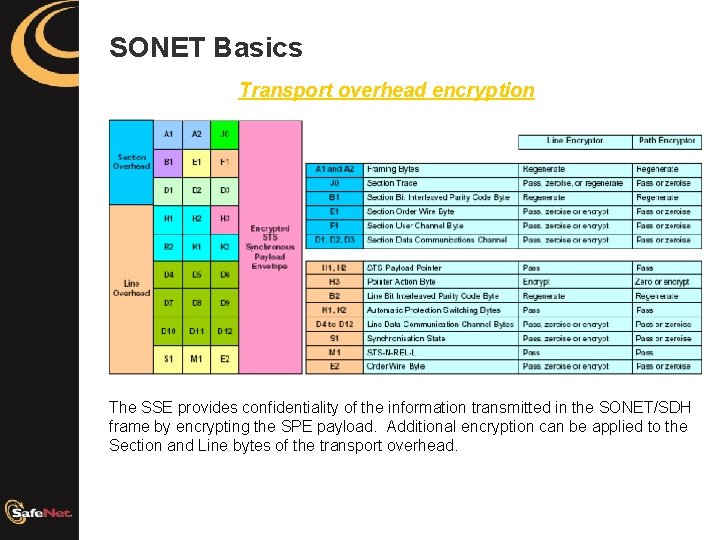
SONET Basics Transport overhead encryption The SSE provides confidentiality of the information transmitted in the SONET/SDH frame by encrypting the SPE payload. Additional encryption can be applied to the Section and Line bytes of the transport overhead.

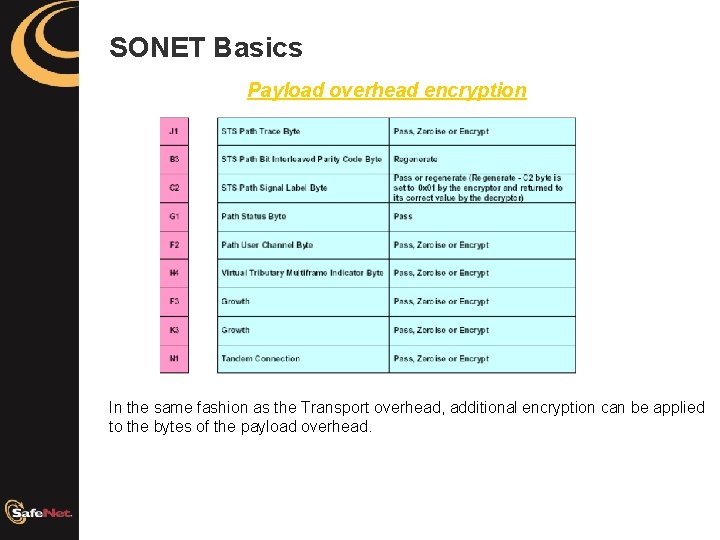
SONET Basics Payload overhead encryption In the same fashion as the Transport overhead, additional encryption can be applied to the bytes of the payload overhead.

Safe. Enterprise Management Centre Overview

Safe. Enterprise Management Centre Overview § Software application that securely manages the installation, configuration and monitoring of Safe. Net HSE encryption devices § Manage and configure all devices from one central location § § § Optional Pairing, Replication or Clustering Built in CA to administer generation and storage of certificates for devices enabling secure authentication LUNA Keystore § § Generation and/or storage of key pairs and certificates used to sign Sx. E device certificates. Root database encryption key § Unique encrypted connection from SMC to each device § RADIUS § VMWare § Provides monitoring and audit capabilities § Can act as an SNMP Proxy to existing NMC

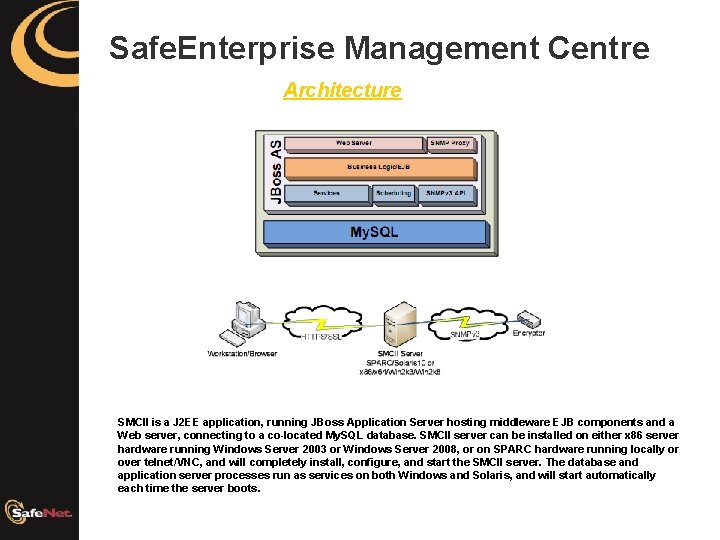
Safe. Enterprise Management Centre Architecture SMCII is a J 2 EE application, running JBoss Application Server hosting middleware EJB components and a Web server, connecting to a co-located My. SQL database. SMCII server can be installed on either x 86 server hardware running Windows Server 2003 or Windows Server 2008, or on SPARC hardware running locally or over telnet/VNC, and will completely install, configure, and start the SMCII server. The database and application server processes run as services on both Windows and Solaris, and will start automatically each time the server boots.

Safe. Enterprise Management Centre Certification process

Safe. Enterprise Management Centre Status Front Panel Display

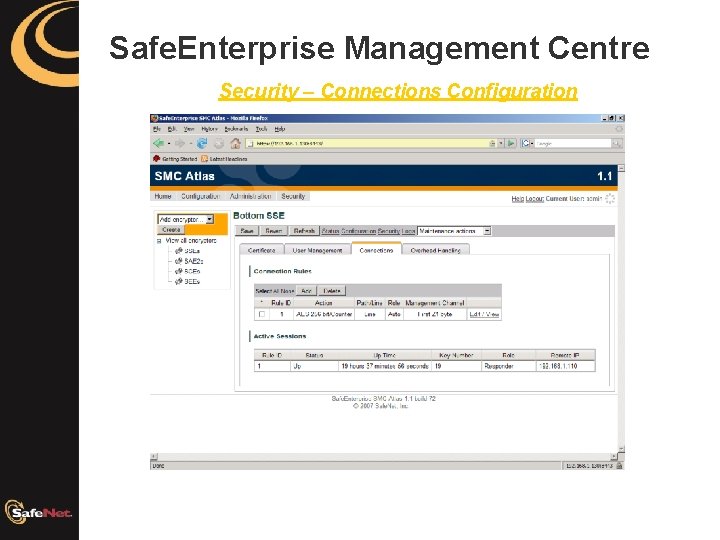
Safe. Enterprise Management Centre Security - Connections

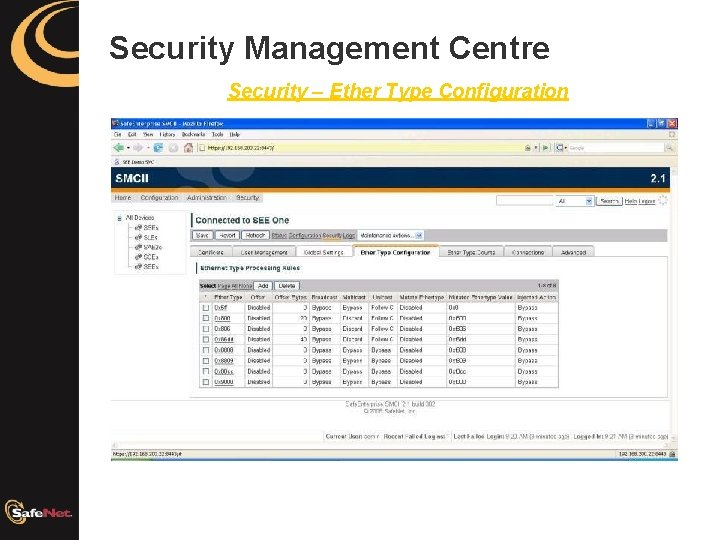
Security Management Centre Security – Ether Type Configuration

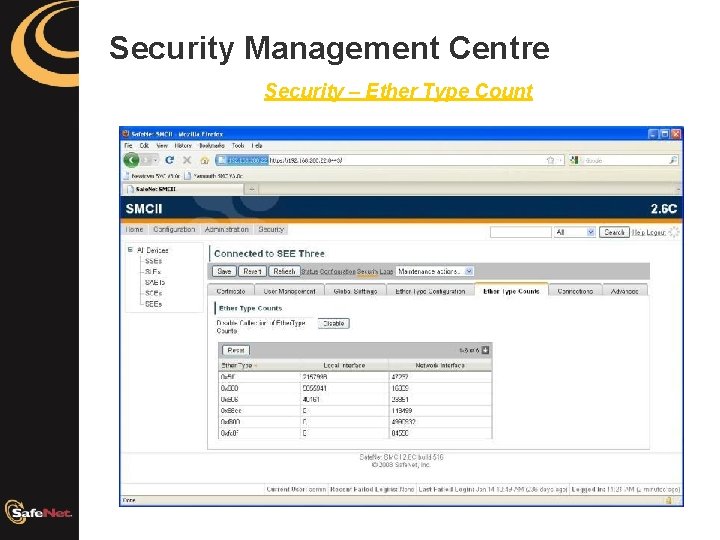
Security Management Centre Security – Ether Type Count

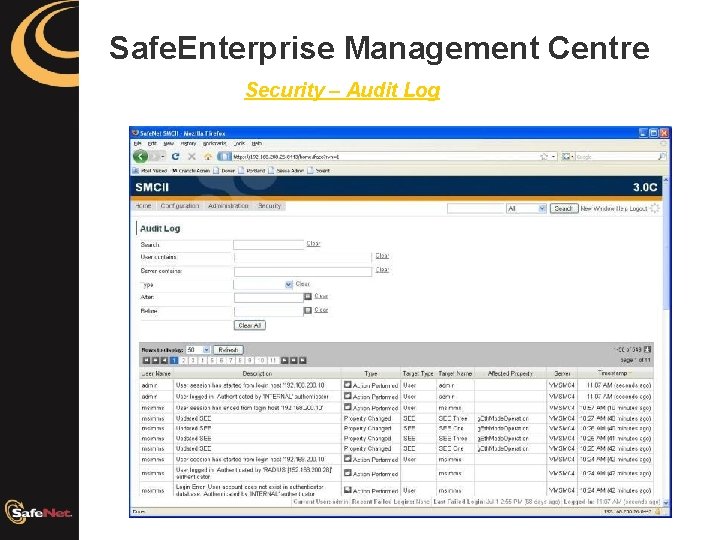
Safe. Enterprise Management Centre Security – Audit Log

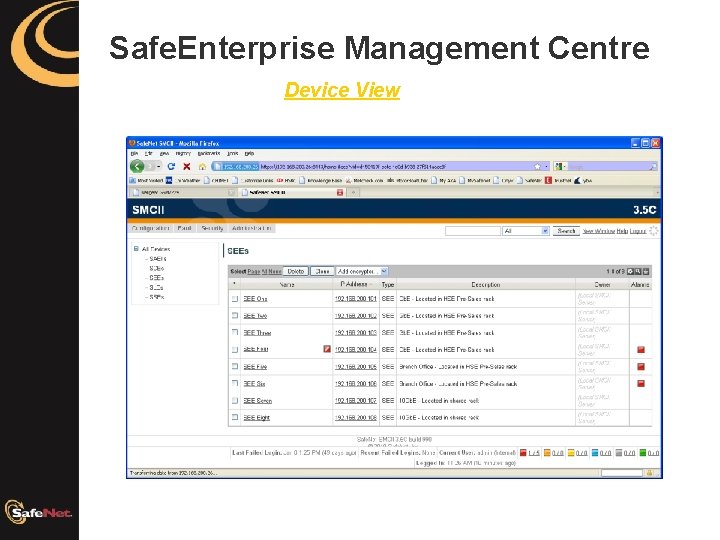
Safe. Enterprise Management Centre Device View

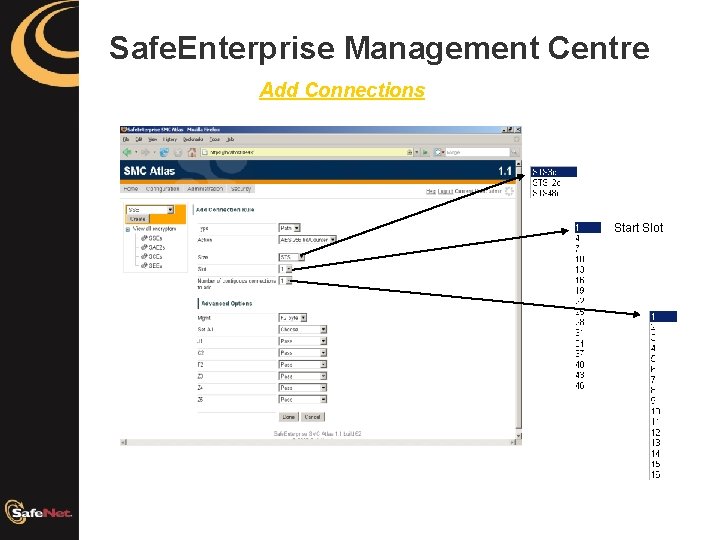
Safe. Enterprise Management Centre Add Connections Start Slot

Safe. Enterprise Management Centre Security – Connections Configuration

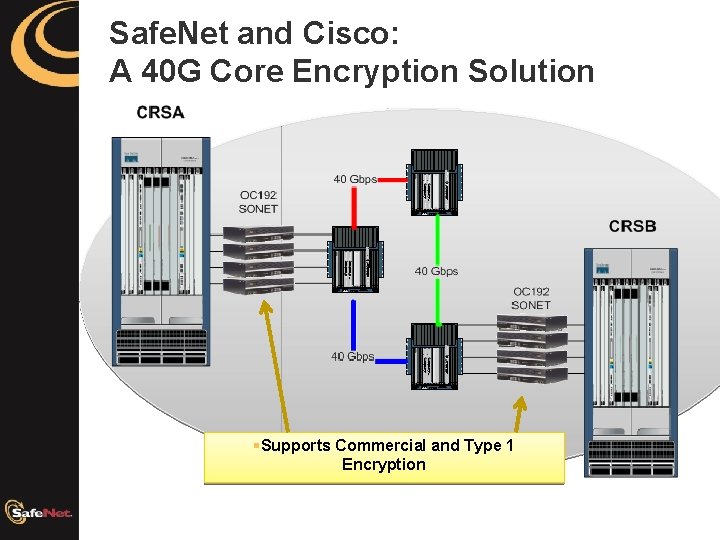
Safe. Net and Cisco: A 40 G Core Encryption Solution §Supports Commercial and Type 1 Encryption