Rushing Attacks and Defense in Wireless Ad Hoc





![Rushing Attack D S Slide courtesy: [2] 10 Rushing Attack D S Slide courtesy: [2] 10](https://slidetodoc.com/presentation_image_h2/5b99c40025540f34065da29c7ecfce5f/image-10.jpg)













![References l [1] Yih-Chun Hu, Adrian Perrig, David B. Johnson , “Rushing attacks and References l [1] Yih-Chun Hu, Adrian Perrig, David B. Johnson , “Rushing attacks and](https://slidetodoc.com/presentation_image_h2/5b99c40025540f34065da29c7ecfce5f/image-41.jpg)
- Slides: 41

Rushing Attacks and Defense in Wireless Ad Hoc Network Routing Protocols Yih-Chun Hu, Adrian Perrig, and David B. Johnson Presenter: Sandeep Mapakshi CS 6910 -ACIS – Project 6 Instructor: Prof. Leszek T. Lilien, Fall 2006 Department of Computer Science Western Michigan University 1

Outline l l l On-Demand Routing Protocols Rushing Attack Prevention Evaluation Conclusion 2

Introduction l Wireless Ad hoc network l l l a collection of mobile computers (or nodes) cooperate to forward packets dynamic topology self-organization 3

Introduction (cont. ) l Routing protocol l l Transport Subsystem Neighbor State Maintenance Database Maintenance Ad hoc network routing protocols l l Run in untrusted environments Provide resilience against misconfigured nodes 4

Routing Protocols l Proactive routing protocol l l Table-Driven routing protocol Reactive routing protocol l l Source-Initiated On-Demand routing protocol Forward ROUTE REQUEST packets when needed 5

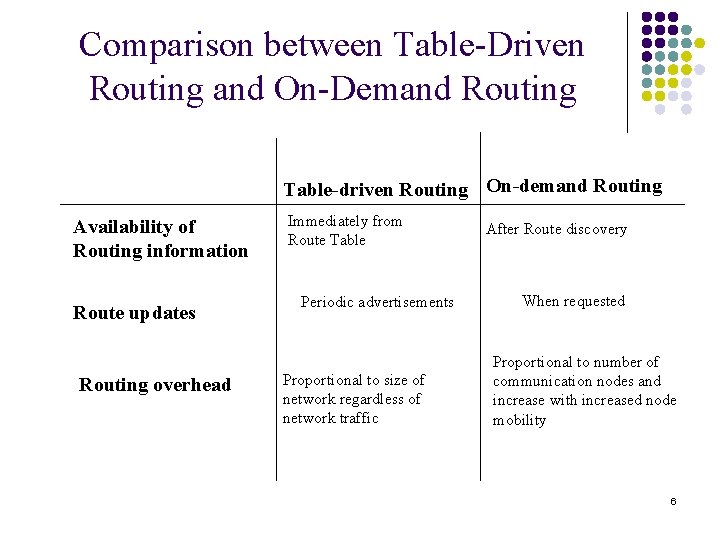
Comparison between Table-Driven Routing and On-Demand Routing Table-driven Routing On-demand Routing Availability of Routing information Route updates Routing overhead Immediately from Route Table Periodic advertisements Proportional to size of network regardless of network traffic After Route discovery When requested Proportional to number of communication nodes and increase with increased node mobility 6

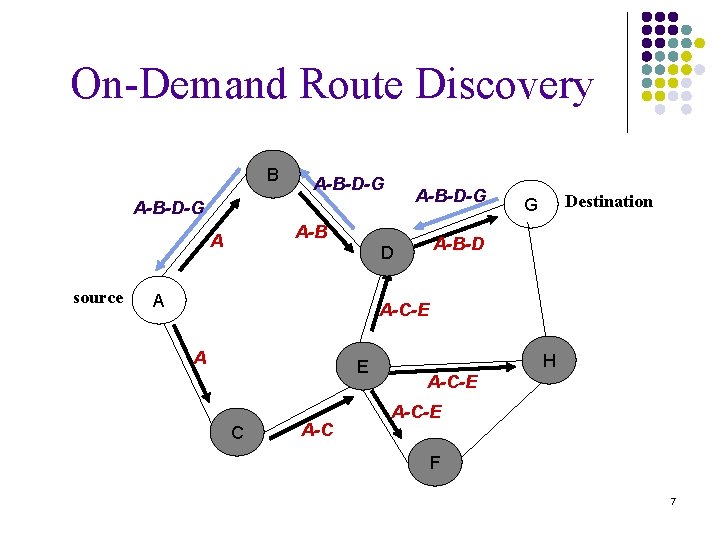
On-Demand Route Discovery B A-B-D-G A-B A source A-B-D D A Destination G A-C-E A E C A-C H A-C-E F 7

The Rushing Attack l On-demand routing protocols use duplicate suppression at each node: first ROUTE REQUEST that reaches a node is considered legitimate, next are discarded (all have the same identifier, higher identifiers denote new requests) l Attacker scatters RREQ quickly throughout the network suppressing any later legitimate RREQ l Initiator will be unable to discover any usable routes containing at least two hops l An effective denial-of-service attack 8

Why is the Attack Possible? l An attacker can send faster, by avoiding the delays that are part of the design of both routing and MAC (802. 11 b) protocols. l Why Delay in ROUTE REQUEST forwarding ? l In a MAC protocols using time division l On-demand protocols generally specify a delay l Remove these delays at both the MAC and routing layers? - more collisions l Attacker can send at a higher wireless transmission level l An attacker can take advantage of a wormhole, to create flood rushing attacks, use the wormhole to rush the packets ahead of the normal flow 9
![Rushing Attack D S Slide courtesy 2 10 Rushing Attack D S Slide courtesy: [2] 10](https://slidetodoc.com/presentation_image_h2/5b99c40025540f34065da29c7ecfce5f/image-10.jpg)
Rushing Attack D S Slide courtesy: [2] 10

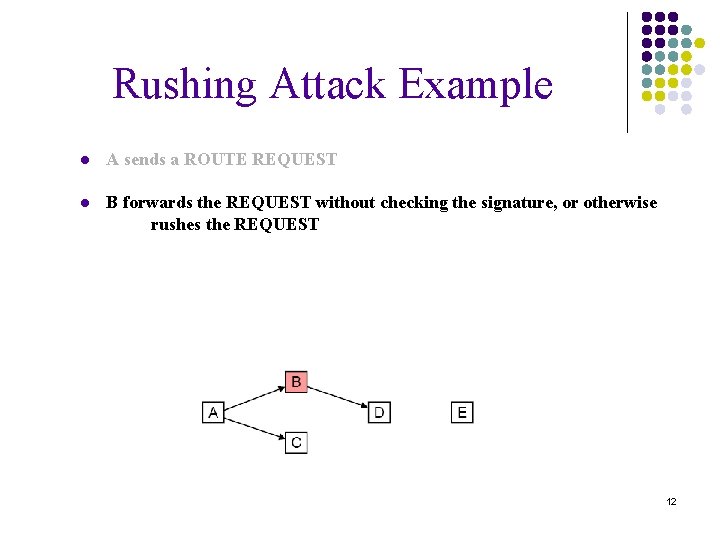
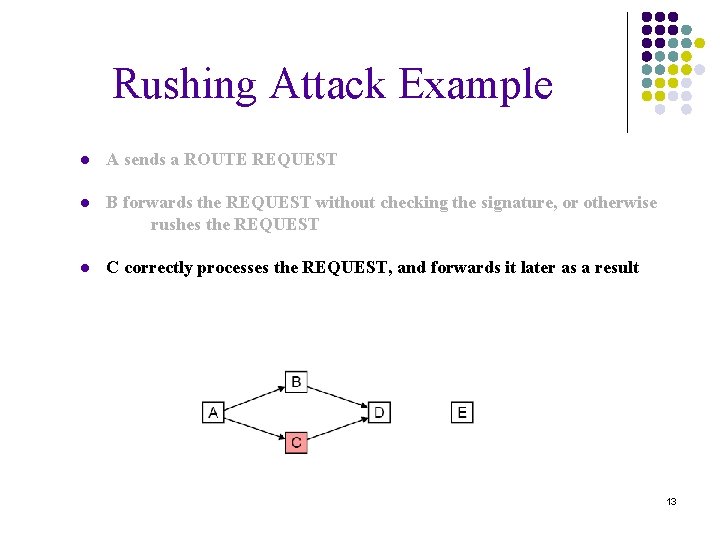
Rushing Attack Example ● A sends a ROUTE REQUEST 11

Rushing Attack Example ● A sends a ROUTE REQUEST ● B forwards the REQUEST without checking the signature, or otherwise rushes the REQUEST 12

Rushing Attack Example ● A sends a ROUTE REQUEST ● B forwards the REQUEST without checking the signature, or otherwise rushes the REQUEST ● C correctly processes the REQUEST, and forwards it later as a result 13

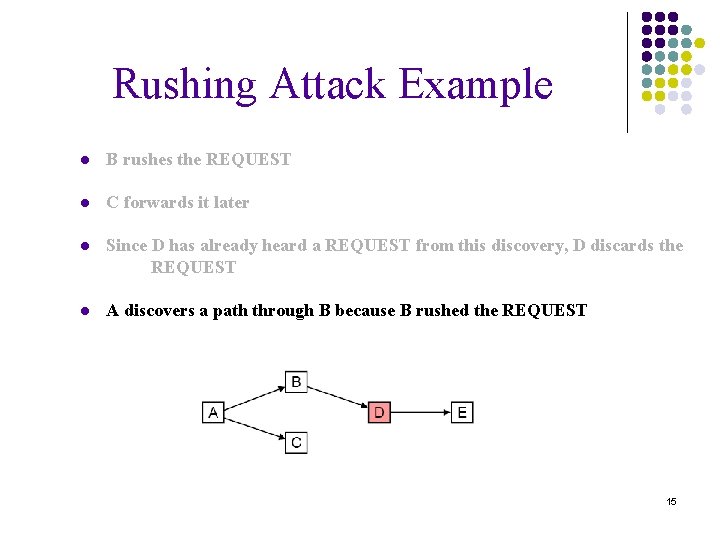
Rushing Attack Example ● A sends a ROUTE REQUEST ● B forwards the REQUEST without checking the signature, or otherwise rushes the REQUEST ● C correctly processes the REQUEST, and forwards it later as a result ● Since D has already heard a REQUEST from this discovery, D discards the REQUEST 14

Rushing Attack Example ● B rushes the REQUEST ● C forwards it later ● Since D has already heard a REQUEST from this discovery, D discards the REQUEST ● A discovers a path through B because B rushed the REQUEST 15

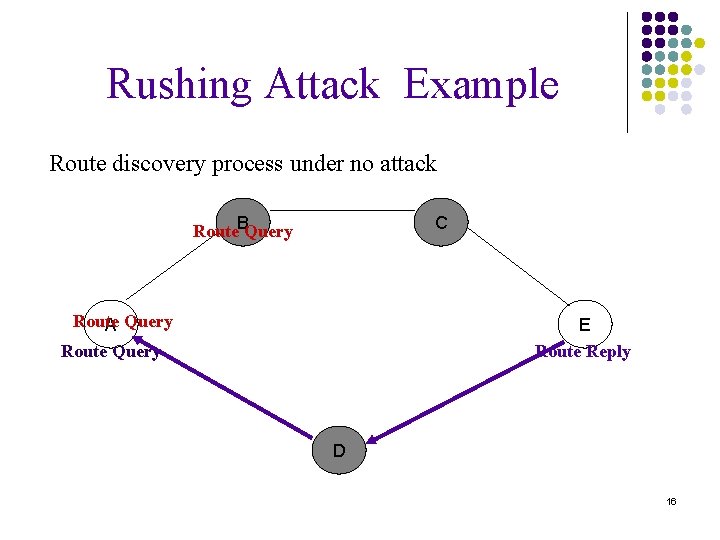
Rushing Attack Example Route discovery process under no attack Route. BQuery C Route A Query Route Query E Route Reply D 16

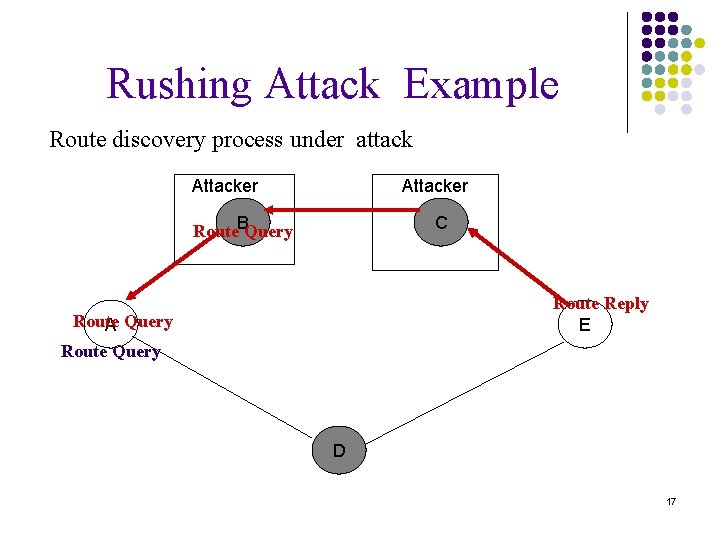
Rushing Attack Example Route discovery process under attack Attacker Route. BQuery C Route Reply E Route A Query Route Query D 17

Wormhole Attack l l Attacker records a packet at one location in the network, tunnels the packet to another location. Packets may be replayed from the far end of the wormhole. Puts attacker in a powerful position. It’s a replay so authentication does not help Applications of the Wormhole Attack l l l Denial-of-Service Routing Disruptions Unauthorized Access 18

Routing Tree Adapted from Chris Karlof and David Wagner's 19 WSNPA slides

Routing Adapted from Chris Karlof and David Wagner's 20 WSNPA slides

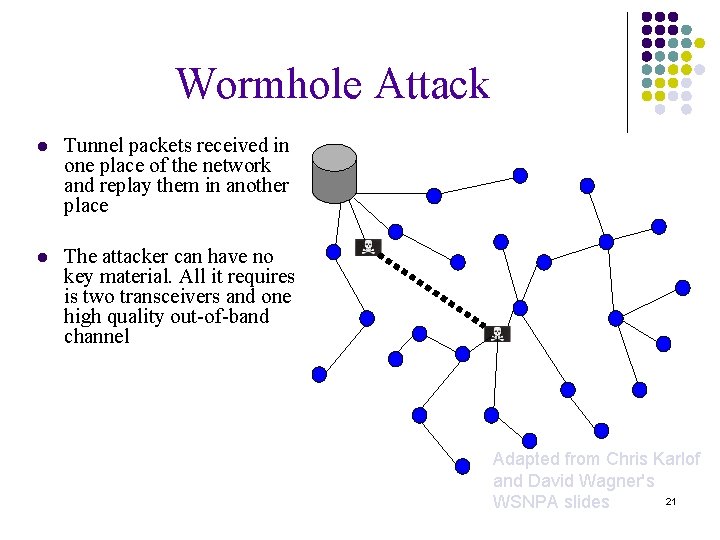
Wormhole Attack l Tunnel packets received in one place of the network and replay them in another place l The attacker can have no key material. All it requires is two transceivers and one high quality out-of-band channel Adapted from Chris Karlof and David Wagner's 21 WSNPA slides

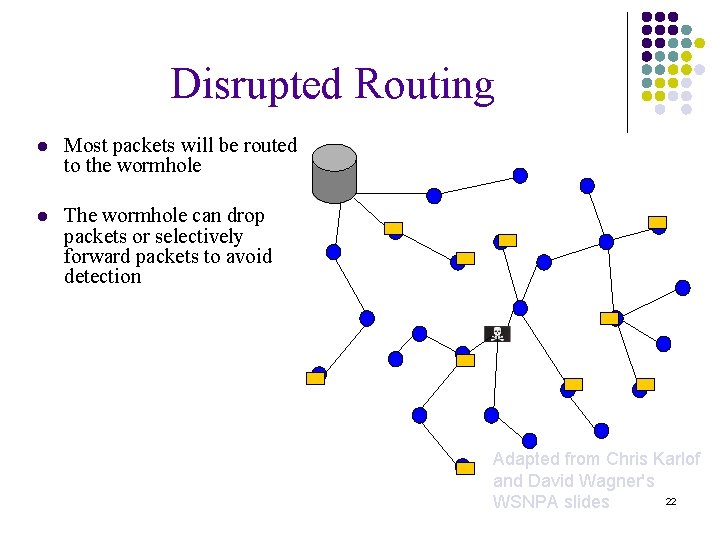
Disrupted Routing l Most packets will be routed to the wormhole l The wormhole can drop packets or selectively forward packets to avoid detection Adapted from Chris Karlof and David Wagner's 22 WSNPA slides

What Protocols Are Vulnerable? l l On-demand unsecure (AODV, DSR) and secure (ARAN, Ariadne, etc) protocols Result: when under attack, the routing protocol will not be able to discover paths longer than 2 hops 23

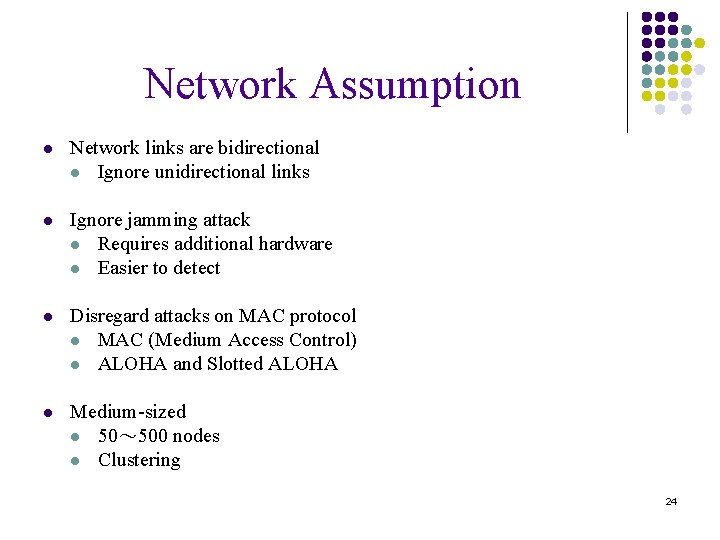
Network Assumption l Network links are bidirectional l Ignore unidirectional links l Ignore jamming attack l Requires additional hardware l Easier to detect l Disregard attacks on MAC protocol l MAC (Medium Access Control) l ALOHA and Slotted ALOHA l Medium-sized l 50~ 500 nodes l Clustering 24

Security Assumptions And Key Setup l Fast authentication protocol l Instantly-verifiable broadcast authentication l Keys setup l Broadcast authentication key are distributed in advance l Powerful attacker l Coordinated attacker 25

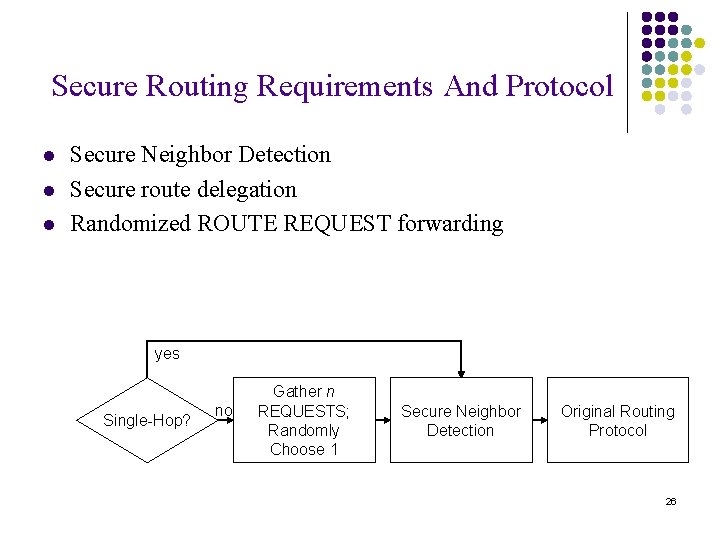
Secure Routing Requirements And Protocol l Secure Neighbor Detection Secure route delegation Randomized ROUTE REQUEST forwarding yes Single-Hop? no Gather n REQUESTS; Randomly Choose 1 Secure Neighbor Detection Original Routing Protocol 26

Secure Neighbor Detection l l l l Two nodes detect a bidirectional link between themselves In Proactive routing protocol In Reactive routing protocol Requirements l l Sender-receiver can check that the other is within the normal communication range Node needs to hear Neighbor Request 27

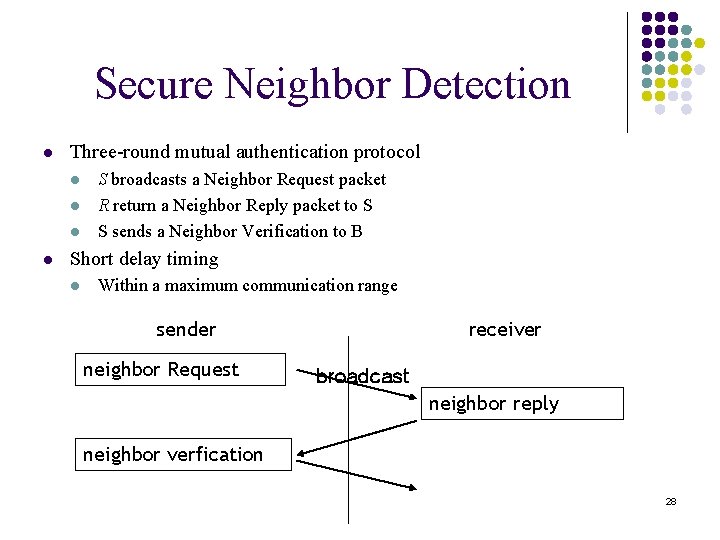
Secure Neighbor Detection l Three-round mutual authentication protocol l l S broadcasts a Neighbor Request packet R return a Neighbor Reply packet to S S sends a Neighbor Verification to B Short delay timing l Within a maximum communication range sender neighbor Request receiver broadcast neighbor reply neighbor verfication 28

Notation 29

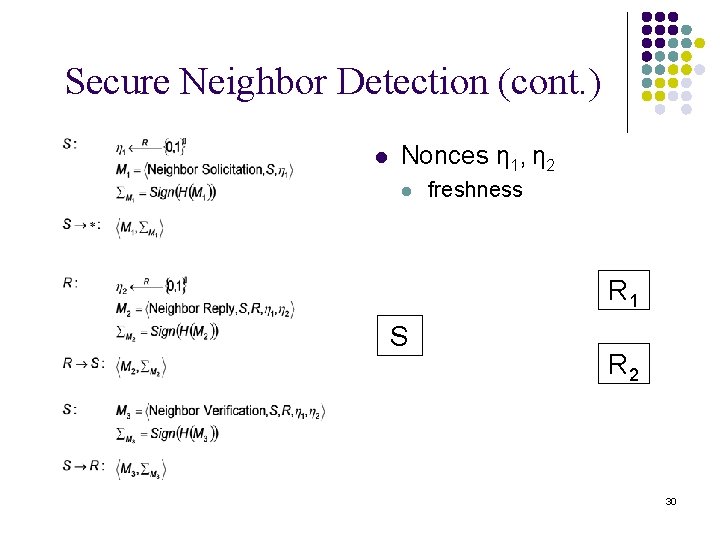
Secure Neighbor Detection (cont. ) l Nonces η 1, η 2 l freshness <M 32, Σ , ΣM > <M > 23 S R 1 <M 1, ΣM > 1 R 2 30

Secure Neighbor Detection (cont. ) l Integration with an On-Demand Protocol l l A *: B A: A B: B *: REQUEST || Neighbor Request. A Neighbor Reply. B A || Neighbor Request. B Neighbor Verification. A B || Neighbor Reply. A B REQUEST || Neighbor Verification. A B || Neighbor Verification. B A 31

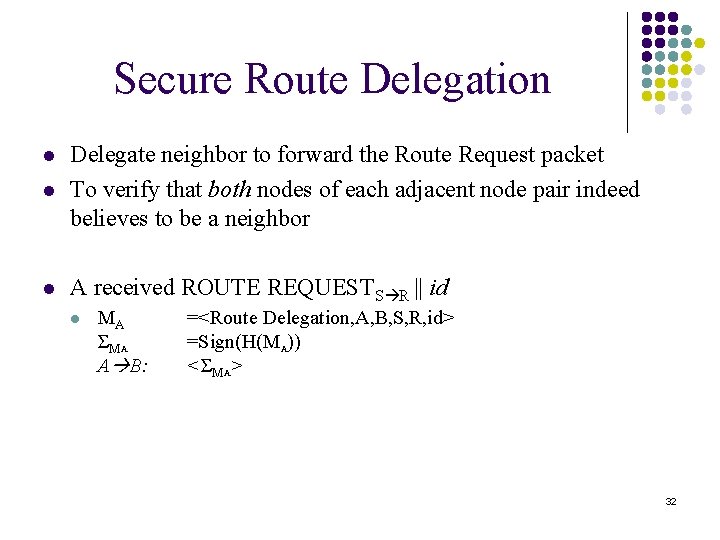
Secure Route Delegation l Delegate neighbor to forward the Route Request packet To verify that both nodes of each adjacent node pair indeed believes to be a neighbor l A received ROUTE REQUESTS R || id l l MA ΣM A A B: =<Route Delegation, A, B, S, R, id> =Sign(H(MA)) <ΣMA> 32

Randomized Message Forwarding l To minimize the chance that a rushing adversary can dominate all returned routes l Randomized message forwarding l Collects a number of REQUESTs l Selects a REQUEST at random to forward l The number of REQUEST packets collected l The more the better? l The algorithm by which timeouts are chosen l Topology closer l Geographically closer l Randomly 33

Secure Route Discovery l l To secure any protocol using an on-demand Route Discovery protocol l Secure Neighbor Detection l Secure route delegation l Randomized ROUTE REQUEST forwarding To limit the number of REQUESTs that traverse an attacker l The nodes that don’t have n distinct path to the source of the REQUEST l Choose a random timeout l Two addition security optimizations l Each REQUEST signed l Use location information 34

Evaluation l Simulation Evaluation l l l l Underlying protocol: Adriane HORS as broadcast signature 100 nodes 1000 m x 1000 m Random waypoint model Pause Time: 0, 30, 60, 120, 300, 600, 900 Workload: 5 flows l l 4 packets per second 64 -byte packets 35

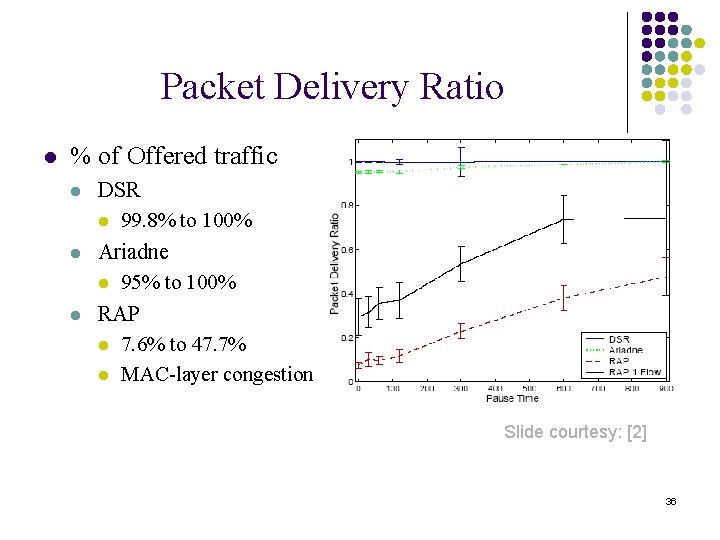
Packet Delivery Ratio l % of Offered traffic l l l DSR l 99. 8% to 100% Ariadne l 95% to 100% RAP l 7. 6% to 47. 7% l MAC-layer congestion Slide courtesy: [2] 36

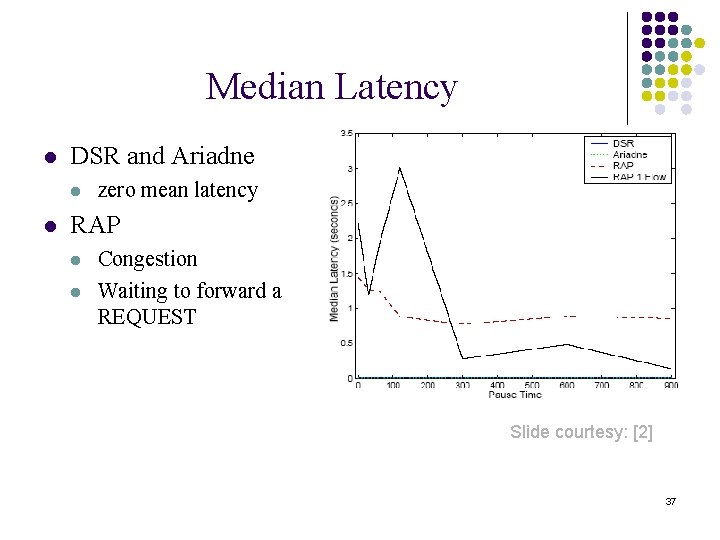
Median Latency l DSR and Ariadne l l zero mean latency RAP l l Congestion Waiting to forward a REQUEST Slide courtesy: [2] 37

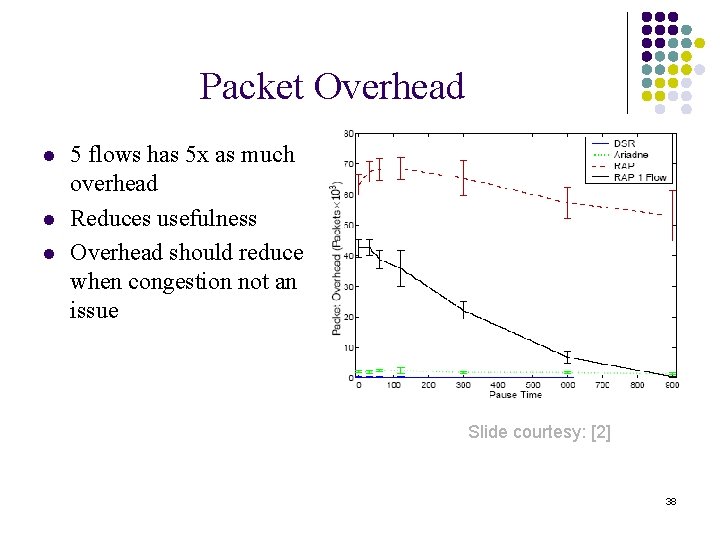
Packet Overhead l l l 5 flows has 5 x as much overhead Reduces usefulness Overhead should reduce when congestion not an issue Slide courtesy: [2] 38

Overall l Evaluation l l RAP adds significant costs Higher costs due to congestion at lower bit rates. RAP is designed to be used only when necessary l Only when underlying protocol is unable to discover a working route Security Analysis l Attacker needs to propagate ROUTE REQUEST from each ROUTE DISCOVERY from many locations. l Wouldn’t do it if they considered due to intrusion detection 39

Conclusion l Described the Rushing attack l Presented RAP (Rushing Attack Prevention) l RAP incurs higher overhead, but it can find usable routes when other protocols cannot work 40
![References l 1 YihChun Hu Adrian Perrig David B Johnson Rushing attacks and References l [1] Yih-Chun Hu, Adrian Perrig, David B. Johnson , “Rushing attacks and](https://slidetodoc.com/presentation_image_h2/5b99c40025540f34065da29c7ecfce5f/image-41.jpg)
References l [1] Yih-Chun Hu, Adrian Perrig, David B. Johnson , “Rushing attacks and defense in wireless ad hoc network routing protocols”, Proceedings of the 2003 ACM workshop on Wireless security, San Diego, CA, USA. Available at: http: //www. ece. cmu. edu/~adrian/projects/securerouting/wise 2003. pdf l [2] Rushing Attacks and Defense in Wireless Ad Hoc Network Routing Protocols Yih-Chun Hu, Adrian Perrig, and David B. Johnson Presenter: Tammy Nguyen. Available at: http: //www. eecs. wsu. edu/~smedidi/teaching/Spring 05/rushing 1. ppt 41