RSAbased password authenticated key exchange protocol Presenter Jungwen

RSA-based password authenticated key exchange protocol Presenter: Jung-wen Lo(駱榮問)

Outline l Introduction l C. C. Yang, R. C. Wang, "Cryptanalysis of improvement of password authenticated key exchange based on RSA for imbalanced wireless networks, " IEICE Transactions on Communications, Vol. E 88 -B, No. 11, pp. 4370 -4372, 2005. Chien-Lung Hsu, Wen-Te Lin, and Yen-Chun Chou, “New Efficient Password Authenticated Key Exchange Protocol for Imbalanced Wireless Networks”, Journal of Computers, Vol. 18, No. 2, pp. 25 -32, 2007 l l Conclusion & Comment 2
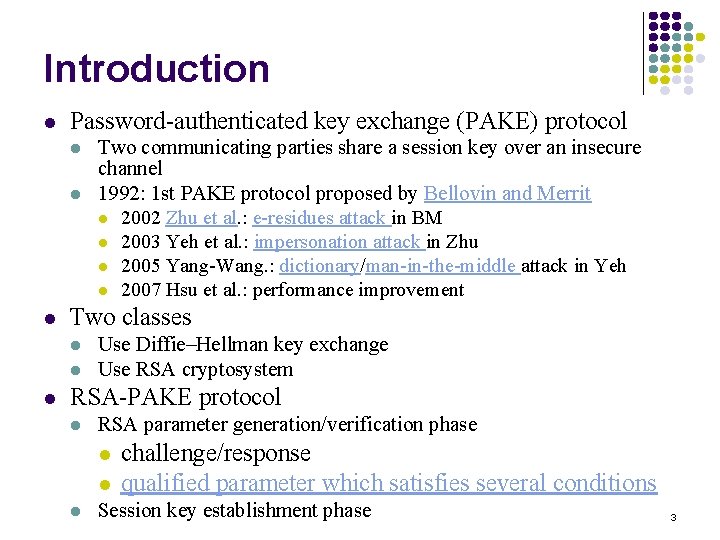
Introduction l Password-authenticated key exchange (PAKE) protocol l Two classes l l l Two communicating parties share a session key over an insecure channel 1992: 1 st PAKE protocol proposed by Bellovin and Merrit l 2002 Zhu et al. : e-residues attack in BM l 2003 Yeh et al. : impersonation attack in Zhu l 2005 Yang-Wang. : dictionary/man-in-the-middle attack in Yeh l 2007 Hsu et al. : performance improvement Use Diffie–Hellman key exchange Use RSA cryptosystem RSA-PAKE protocol l RSA parameter generation/verification phase l l l challenge/response qualified parameter which satisfies several conditions Session key establishment phase 3

Cryptanalysis of improvement of password authenticated key exchange based on RSA for imbalanced wireless networks Authors: C. C. Yang and R. C. Wang, Src: IEICE Transactions on Communications, Vol. E 88 -B, No. 11, pp. 4370 -4372, 2005. 4
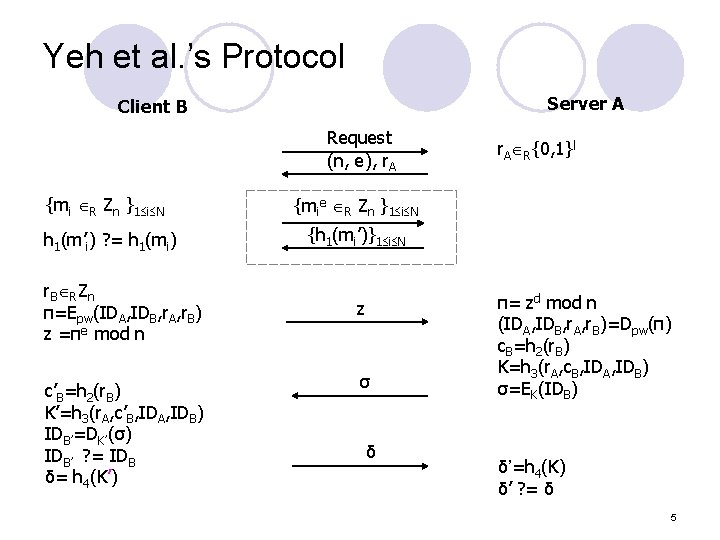
Yeh et al. ’s Protocol Server A Client B Request (n, e), r. A {mi R Zn }1 i N h 1(m’i) ? = h 1(mi) r B R Zn π=Epw(IDA, IDB, r. A, r. B) z =πe mod n c’B=h 2(r. B) K’=h 3(r. A, c’B, IDA, IDB) IDB’=DK’(σ) IDB’ ? = IDB δ= h 4(K’) r. A R{0, 1}l {mie R Zn }1 i N {h 1(mi’)}1 i N z σ δ π= zd mod n (IDA, IDB, r. A, r. B)=Dpw(π) c. B=h 2(r. B) K=h 3(r. A, c. B, IDA, IDB) σ=EK(IDB) δ’=h 4(K) δ’ ? = δ 5
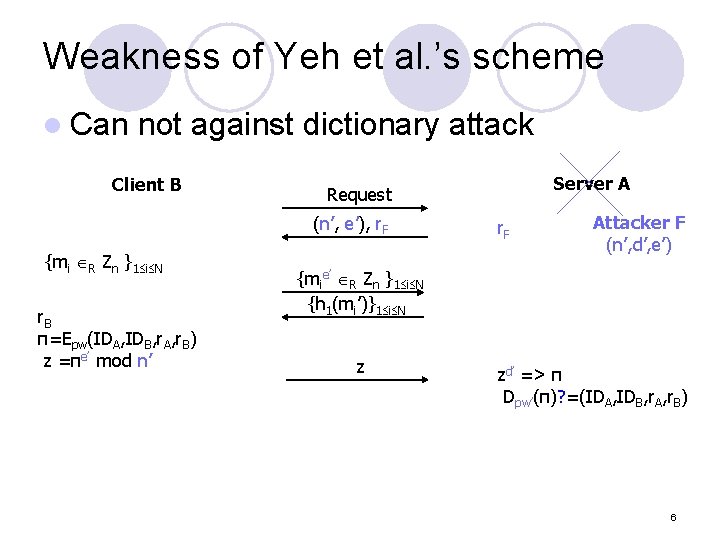
Weakness of Yeh et al. ’s scheme l Can not against dictionary attack Client B (n’, e’), r. F {mi R Zn }1 i N r. B π=Epw(IDA, IDB, r. A, r. B) z =πe’ mod n’ Server A Request r. F Attacker F (n’, d’, e’) {mie’ R Zn }1 i N {h 1(mi’)}1 i N z zd’ => π Dpw’(π)? =(IDA, IDB, r. A, r. B) 6
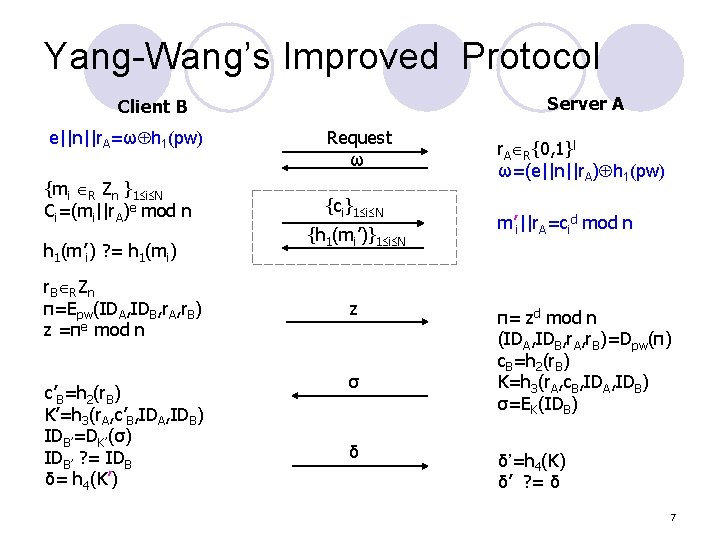
Yang-Wang’s Improved Protocol Server A Client B e||n||r. A=ω h 1(pw) {mi R Zn }1 i N Ci=(mi||r. A)e mod n h 1(m’i) ? = h 1(mi) r B R Zn π=Epw(IDA, IDB, r. A, r. B) z =πe mod n c’B=h 2(r. B) K’=h 3(r. A, c’B, IDA, IDB) IDB’=DK’(σ) IDB’ ? = IDB δ= h 4(K’) Request ω {ci}1 i N {h 1(mi’)}1 i N z σ δ r. A R{0, 1}l ω=(e||n||r. A) h 1(pw) m’i||r. A=cid mod n π= zd mod n (IDA, IDB, r. A, r. B)=Dpw(π) c. B=h 2(r. B) K=h 3(r. A, c. B, IDA, IDB) σ=EK(IDB) δ’=h 4(K) δ’ ? = δ 7

New Efficient Password Authenticated Key Exchange Protocol for Imbalanced Wireless Networks Authors: Chien-Lung Hsu, Wen-Te Lin, and Yen-Chun Chou Src: Journal of Computers, Vol. 18, No. 2, pp. 25 -32, 2007 8
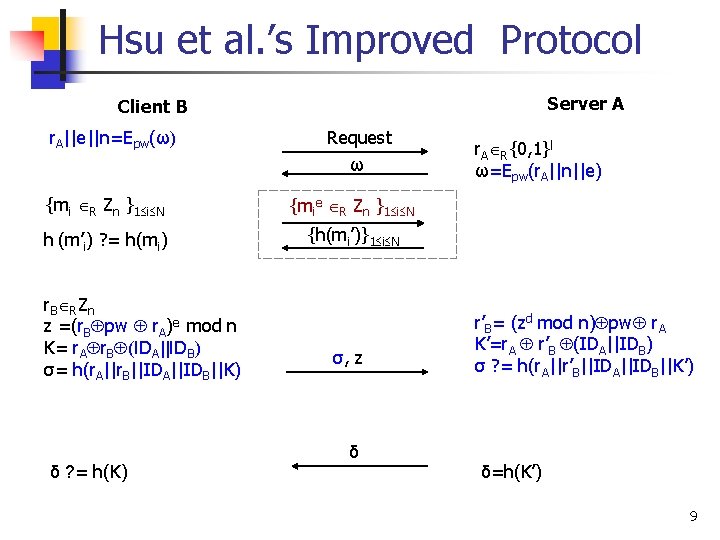
Hsu et al. ’s Improved Protocol Server A Client B r. A||e||n=Epw(ω) Request ω {mi R Zn }1 i N {mie R Zn }1 i N h (m’i) ? = h(mi) {h(mi’)}1 i N r B R Zn z =(r. B pw r. A)e mod n K= r. A r. B (IDA||IDB) σ= h(r. A||r. B||IDA||IDB||K) δ ? = h(K) σ, z δ r. A R{0, 1}l ω=Epw(r. A||n||e) r’B= (zd mod n) pw r. A K’=r. A r’B (IDA||IDB) σ ? = h(r. A||r’B||IDA||IDB||K’) δ=h(K’) 9
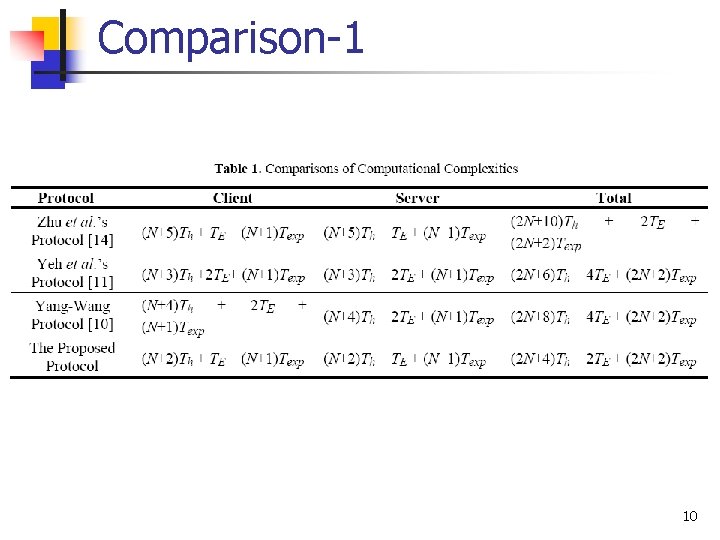
Comparison-1 10
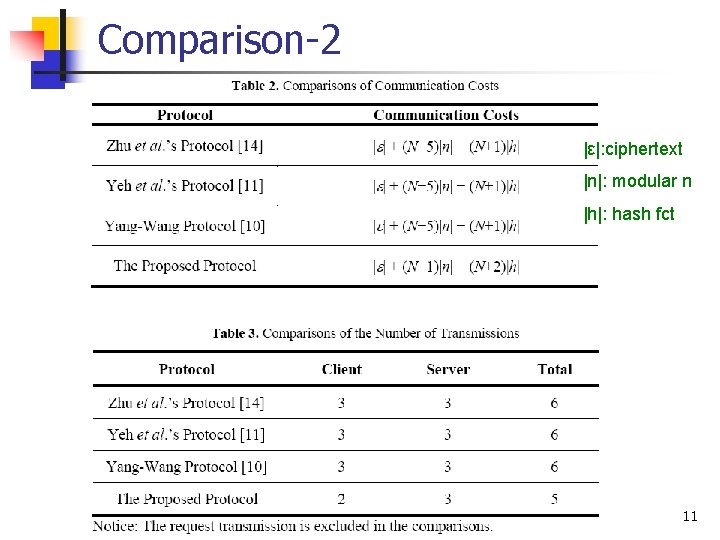
Comparison-2 |ε|: ciphertext |n|: modular n |h|: hash fct 11
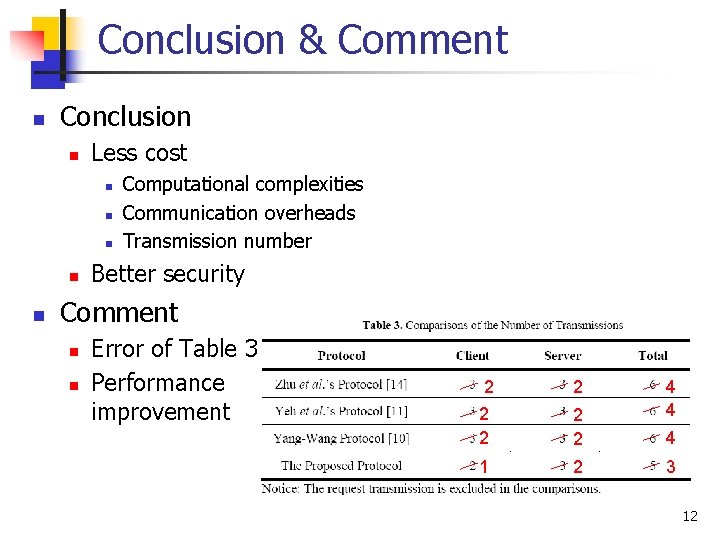
Conclusion & Comment n Conclusion n Less cost n n n Computational complexities Communication overheads Transmission number Better security Comment n n Error of Table 3 Performance improvement 2 2 2 1 2 4 4 4 3 12
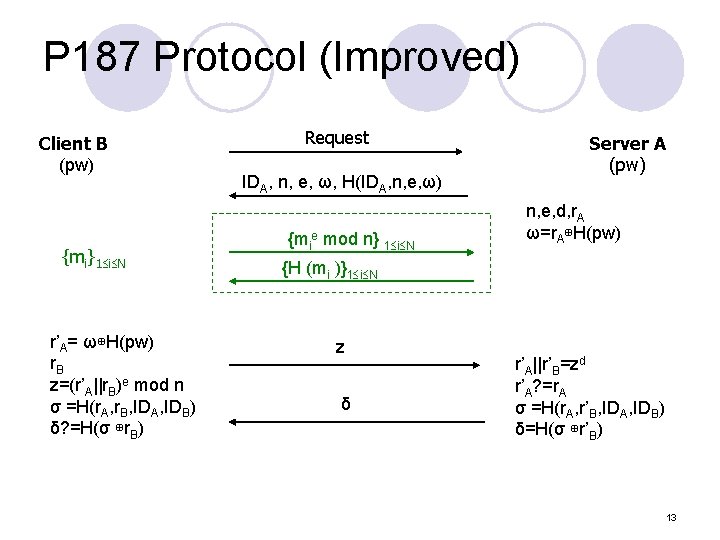
P 187 Protocol (Improved) Client B (pw) {mi}1 i N r’A= ω⊕H(pw) r. B z=(r’A||r. B)e mod n σ =H(r. A, r. B, IDA, IDB) δ? =H(σ ⊕r. B) Request IDA, n, e, ω, H(IDA, n, e, ω) {mie mod n} 1 i N Server A (pw) n, e, d, r. A ω=r. A⊕H(pw) {H (mi )}1 i N z δ r’A||r’B=zd r’A? =r. A σ =H(r. A, r’B, IDA, IDB) δ=H(σ ⊕r’B) 13
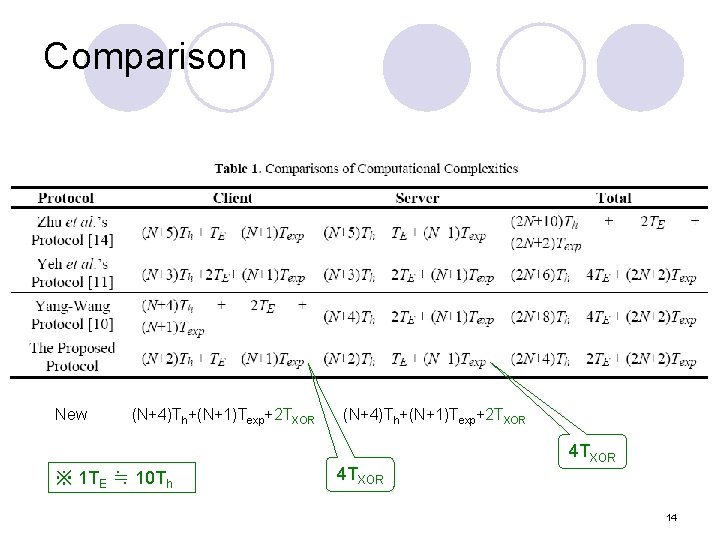
Comparison New (N+4)Th+(N+1)Texp+2 TXOR ※ 1 TE ≒ 10 Th (N+4)Th+(N+1)Texp+2 TXOR 4 TXOR 14
- Slides: 14