RSA PublicKey Encryption Description Problem Solution Rafael Roque

RSA Public-Key Encryption Description Problem Solution Rafael Roque

RSA R. Rivest, A. Shamir, and L. Adleman The most widely used public-key cryptosystem Provide both secrecy and digital signatures Its security is based on the intractability of the integer factorization

RSA - Função Totiente In number theory, the totient φ(n) of a positive integer n is defined to be the number of positive integers less than or equal to n that are coprime to n.
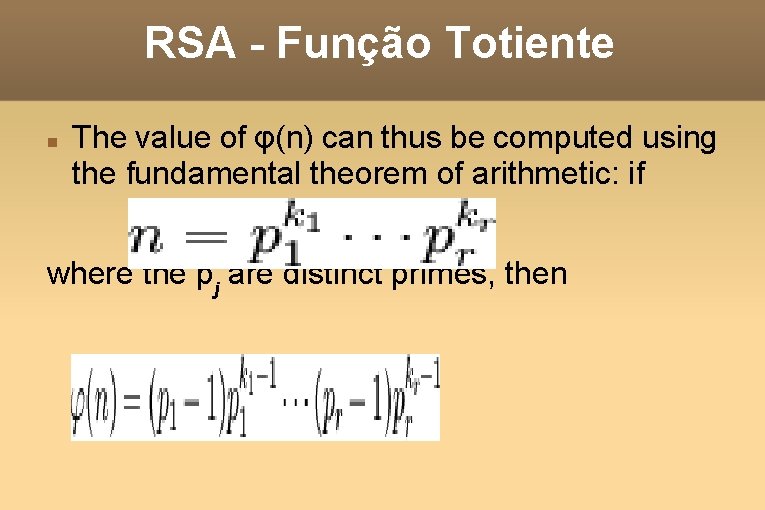
RSA - Função Totiente The value of φ(n) can thus be computed using the fundamental theorem of arithmetic: if where the pj are distinct primes, then
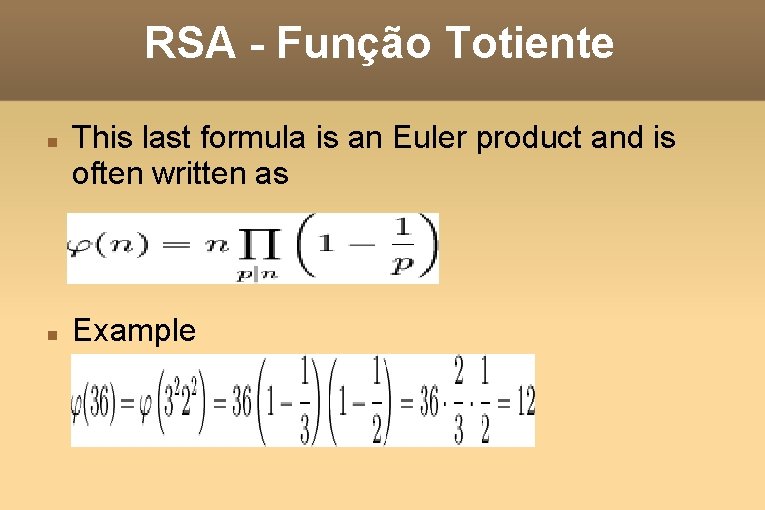
RSA - Função Totiente This last formula is an Euler product and is often written as Example

Key generation for RSA public-key encryption 1. 'A' generate two large random (and distinct) primes p and q, each roughly the same size. 2. Compute n = pq and φ = (p − 1)(q − 1). * 3. Select a random integer e, 1 < e < φ(n), such that gcd(e, φ) = 1. 4. Use the extended Euclidean algorithm to compute the unique integer d, 1 < d < φ, such that ed ≡ 1 (mod φ).

Key generation for RSA public-key encryption The integers e and d in RSA key generation are called the encryption exponent and the decryption exponent, respectively, while n is called the modulus.

RSA public-key encryption Algorithm Encryption. B should do the following: Obtain A’s authentic public key (n, e). Represent the message as an integer m in the interval [0, n − 1]. Compute c = me mod n. Send the ciphertext c to A. Decryption. To recover plaintext m from c, A should do the following: Use the private key d to recover m = cd mod n.

Problem Let’s explore why in the RSA public key system each person has to be assigned a different modulus N = pq. Suppose we try to use the same modulus N = pq for everyone. Each person is assigned a public exponent ei and a private exponent di such that ei · di = 1 mod φ(N ). At first this appears to work fine: to encrypt a message to Bob, Alice computes C = M ebob and sends C to Bob. An eavesdropper Eve, not knowing dbob appears to be unable to decrypt C. Let’s show that using eeve and deve Eve can very easily decrypt C.

Problem (a) Show that given eeve and deve Eve can obtain a multiple of φ(N ). (b) Show that given an integer K which is a multiple of φ(N ) Eve can factor the modulus N. Deduce that Eve can decrypt any RSA ciphertext encrypted using the modulus N intended for Alice or Bob.

Solution - A Remember that we found d as an unique integer, 1 < d < φ, such that ed ≡ 1 (mod φ). eeve · deve = 1 mod φ(N). eeve · deve - 1 = k φ(N) for some k. We found 'eeve · deve - 1' as a multiple of φ(N).

Solution - B Find a g such that g , . . . , g k k/2 k/n does not consist of entirely of 1 s, and furthermore, the first member of the sequence not equal to 1 is also not equal to − 1. Let x be the leftmost element not equal to ± 1. Note x = 1. 2 Suppose x 2 − 1 = 0 mod N. Rewrite this as (x + 1)(x − 1) = 0 mod pq

RSA Public-Key Encryption In other words, (x + 1)(x − 1) is a multiple of pq. Thus p divides x + 1 or p divides x − 1 since p is a prime. Similarly q divides x + 1 or x − 1. If both p and q divide x+1, then x+1 = 0 mod N , but this cannot be since x = − 1 mod N. Similarly, both p and q cannot divide x − 1. Thus gcd(N, x − 1) is either p or q. (Similarly so is gcd(N, x + 1)

Reference Fermat’s Little Theorem Euler’s Theorem Let p be a prime. Any integer a satisfies ap = a mod p, and any integer a not divisible by p satisfies ap-1 = 1 mod p It is the generalization if Fermat’s Little Theorem. It states that for two integers a and n such that gcd(a, n)=1, then ap(phi(n)) = 1 mod n. Miller-Rabin Test for Primality if b 2 = 1 mod n, then b= (+ or-) 1.
- Slides: 14