Rough Set Received qmail 3071 invoked by uid








基于Rough Set的数据挖掘技术在网络安全中的应用研究 邮件头示例 由邮件服务器添加 的信封信息 Received: (qmail 3071 invoked by uid 10000); 3 Jan 2002 07: 09: 33 +0800 Received: from unknown (HELO hctelecom. com) (61. 134. 9. 11) by 61. 135. 132. 233 with SMTP; 3 Jan 2002 07: 09: 33 +0800 Received: from localhost [12. 235. 111. 30] by hctelecom. com with ESMTP (SMTPD 32 -7. 04) id AFBB 105014 E; Wed, 02 Jan 2002 04: 43 +0800 Received: from apple ([128. 8. 99. 7]) by cpimssmtpu 08. email. msn. com with Microsoft SMTPSVC(5. 0. 2195. 4617); Tue, Jan 1 13: 22: 30 2002 -0800 Message-ID: <836 TFI 19@qibo. com. cn> Return-Path: <neakvkl@qibo. com. cn> Delivered-To: pjims@mail. chinaren. com Date: Tue, Jan 1 16: 14: 52 2002 +0800 (CST) From: neakvkl <neakvkl@qibo. com. cn> 由用户自己写入的 To: gwncvkr@hebust. edu. cn 信息 Subject: (Junk mail)…… 2004 -5 -22 重庆邮电学院信息安全技术重点实验室 8
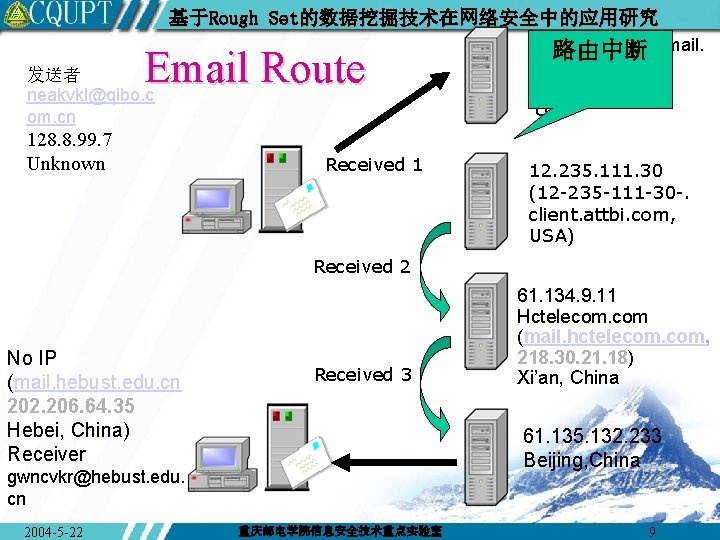
基于Rough Set的数据挖掘技术在网络安全中的应用研究 Email Route 发送者 neakvkl@qibo. c om. cn 128. 8. 99. 7 Unknown Received 1 cpimssmtpu 08. email. 路由中断 msn. com 207. 46. 181. 83 USA 12. 235. 111. 30 (12 -235 -111 -30 -. client. attbi. com, USA) Received 2 No IP (mail. hebust. edu. cn 202. 206. 64. 35 Hebei, China) Receiver Received 3 61. 135. 132. 233 Beijing, China gwncvkr@hebust. edu. cn 2004 -5 -22 61. 134. 9. 11 Hctelecom. com (mail. hctelecom. com, 218. 30. 21. 18) Xi’an, China 重庆邮电学院信息安全技术重点实验室 9
















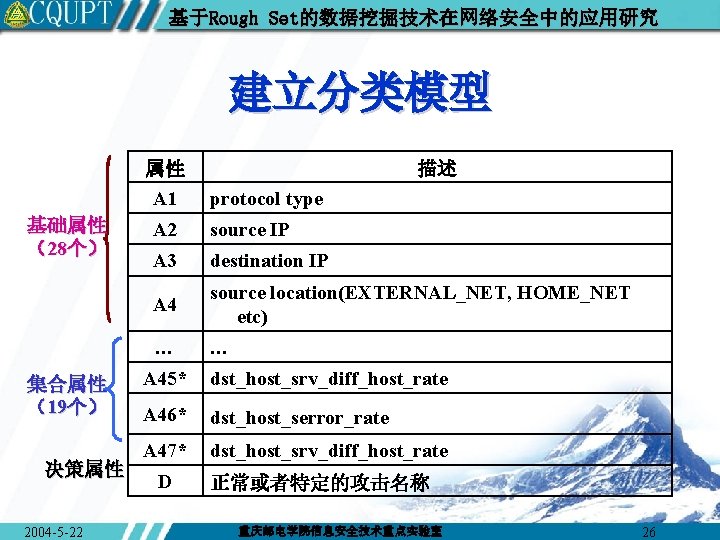
基于Rough Set的数据挖掘技术在网络安全中的应用研究 建立分类模型 属性 A 1 基础属性 (28个) 集合属性 (19个) 决策属性 2004 -5 -22 描述 protocol type A 2 source IP A 3 destination IP A 4 source location(EXTERNAL_NET, HOME_NET etc) … … A 45* dst_host_srv_diff_host_rate A 46* dst_host_serror_rate A 47* dst_host_srv_diff_host_rate D 正常或者特定的攻击名称 重庆邮电学院信息安全技术重点实验室 26




基于Rough Set的数据挖掘技术在网络安全中的应用研究 部分规则示例 �� A 10 A 120 D 3 A 16 A 41 A 88 D 12 A 11 A 89 A 187 A 375 D 19 2004 -5 -22 ���� IF the protocol type is IP AND the source IP is the same as the destination IP THEN it is a “land” attack IF the protocol type is TCP AND the TCP flag is FIN AND the number of connections to the same destination is in [180. 5. 5, 254. 5) Then it is a “TCP FIN scan” attack. IF the protocol is icmp, AND the service is icmp echo, AND the number of connections to the same destination is at least 254. 5 AND the number of connections with the same service is at least 113. THEN it is a “smurf” attack. 重庆邮电学院信息安全技术重点实验室 30









- Slides: 39