Rootkits What they are and how to find































- Slides: 63

Rootkits: What they are and how to find them Part 3 Xeno Kovah – 2010 xkovah at gmail

All materials is licensed under a Creative Commons “Share Alike” license. • http: //creativecommons. org/licenses/by-sa/3. 0/ 2

Incident Response && Forensic Analysis • Firewire memory capture if you can, otherwise… • Plug in USB drive with win 32 dd on it • Run win 32 dd from the USB drive, saving the results back to the USB drive • Hard shutdown • Physically remove HD, copy the HD with a hardware write blocker if available • Turn a copy of the disk image into a virtual machine which can be run and examined using the tools described earlier – Being able to interact with and modify the system will be of critical importance if you're going to try and determine the causality behind an unknown change to system integrity • Analyze the memory image with Volatility/Win. Dbg/Memoryze/Responder. Pro etc 3

win 32 dd • http: //www. moonsols. com/windows-memory-toolkit/ – Download the "community edition" • Pretending you had it running from and storing to the Z: drive: – win 32 dd /f Z: machinename. dmp – win 32 dd /d /f Z: machinename. dmp • /d is to put it in windbg crashdump form • We were going to cheat and do it in the VM • win 32 dd apparently doesn't run in vmware though. So we need to take the VM's. vmem file and run – bin 2 dmp. exe <path to. vmem> <name of. dmp> 4

Using Volatility for rootkit detection • See Drew Hunt's class for more about memory analysis and Volatility • The setup of Volatility is the standard 1. 4 install (https: //code. google. com/p/volatility/wiki/Full. Inst allation) with the following extra plugin in your Volatility-1. 4_rc 1volatilityplugins folder – http: //malwarecookbook. googlecode. com/svn/trunk/m alware. py • Good example usage of detecting various stuff here: http: //code. google. com/p/volatility/wiki/Comman d. Reference 5

SSDT hook detection (also tells you when some threads possibly are being pointed to alternate, hooked, copies of the SSDT) • python vol. py ssdt -f bla. dmp • Built in (not from the malware plugin), unfortunately you need to sift it yourself (Ctrl 2 Cap impersonator which hides files) Entry 0 x 0091: 0 xfa 065592 (Nt. Query. Directory. File) owned by Ctr 12 Cap. sys (Daemon Tools + SPTD) Entry 0 x 00 a 0: 0 xf 97 fd 554 (Nt. Query. Key) owned by sptd. sys (Trusteer Rapport normal hook) Entry 0 x 00 e 0: 0 xf 9 b 4 fa 90 (Nt. Set. Information. File) owned by Rapport. Cerberus_23645. sys (Trusteer Rapport shadow SSDT hooks) Entry 0 x 1124: 0 xf 0 f 27324 (Nt. Gdi. Stretch. Blt) owned by Rapport. PG. sys <snip> Entry 0 x 1299: 0 xbf 954 c 65 (Nt. Gdi. UMPDEng. Free. User. Mem) owned by win 32 k. sys Entry 0 x 129 a: 0 xbf 817637 (Nt. Gdi. Draw. Stream) owned by win 32 k. sys SSDT[2] at e 2187818 with 5 entries Entry 0 x 2000: 0 xefead 620 (Unknown) owned by UNKNOWN Entry 0 x 2001: 0 xefead 65 e (Unknown) owned by UNKNOWN Entry 0 x 2002: 0 xefeadc 1 a (Unknown) owned by UNKNOWN He 4 Hook's user->kernel coms Entry 0 x 2003: 0 xefeae 15 a (Unknown) owned by UNKNOWN Entry 0 x 2004: 0 xefead 6 a 2 (Unknown) owned by UNKNOWN 6

SSDT hook detection 2 • python vol. py ssdt_by_threads -f bla. dmp • Only shows things in main SSDT != nt, and shadow SSDT != win 32 k Volatile Systems Volatility Framework 1. 4_rc 1 Pid Tid Name SSDT Entry 0 x 0013: 0 xf 0 f 20 fa 2 (Nt. Assign. Process. To. Job. Object) owned by Rapport. PG. sys Entry 0 x 001 f: 0 xf 0 fd 1534 (Nt. Connect. Port) owned by vsdatant. sys Entry 0 x 0025: 0 xf 0 f 21 a 38 (Nt. Create. File) owned by Rapport. PG. sys <snip> 4 8 System 0 x 80501030 4 12 System 0 x 80501030 4 16 System 0 x 80501030 4 20 System 0 x 80501030 7

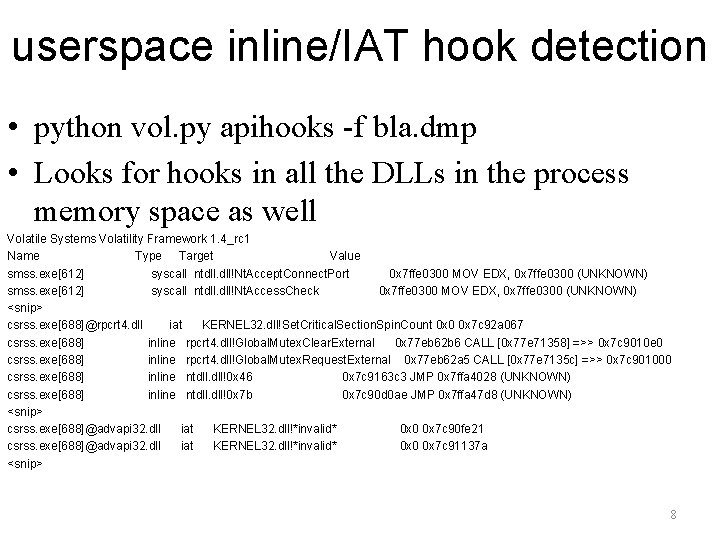
userspace inline/IAT hook detection • python vol. py apihooks -f bla. dmp • Looks for hooks in all the DLLs in the process memory space as well Volatile Systems Volatility Framework 1. 4_rc 1 Name Type Target Value smss. exe[612] syscall ntdll. dll!Nt. Accept. Connect. Port 0 x 7 ffe 0300 MOV EDX, 0 x 7 ffe 0300 (UNKNOWN) smss. exe[612] syscall ntdll. dll!Nt. Access. Check 0 x 7 ffe 0300 MOV EDX, 0 x 7 ffe 0300 (UNKNOWN) <snip> csrss. exe[688]@rpcrt 4. dll iat KERNEL 32. dll!Set. Critical. Section. Spin. Count 0 x 0 0 x 7 c 92 a 067 csrss. exe[688] inline rpcrt 4. dll!Global. Mutex. Clear. External 0 x 77 eb 62 b 6 CALL [0 x 77 e 71358] =>> 0 x 7 c 9010 e 0 csrss. exe[688] inline rpcrt 4. dll!Global. Mutex. Request. External 0 x 77 eb 62 a 5 CALL [0 x 77 e 7135 c] =>> 0 x 7 c 901000 csrss. exe[688] inline ntdll. dll!0 x 46 0 x 7 c 9163 c 3 JMP 0 x 7 ffa 4028 (UNKNOWN) csrss. exe[688] inline ntdll. dll!0 x 7 b 0 x 7 c 90 d 0 ae JMP 0 x 7 ffa 47 d 8 (UNKNOWN) <snip> csrss. exe[688]@advapi 32. dll iat KERNEL 32. dll!*invalid* 0 x 0 0 x 7 c 90 fe 21 csrss. exe[688]@advapi 32. dll iat KERNEL 32. dll!*invalid* 0 x 0 0 x 7 c 91137 a <snip> 8

IRP hook detection • python vol. py driverirp -f bla. dmp • Can use -r to specify a regex if you only want to look at one driver Volatile Systems Volatility Framework 1. 4_rc 1 Driver. Start Name IRP Irp. Addr Irp. Owner Hook. Addr Hook. Owner 0 xefee 5000 'msdirectx' IRP_MJ_CREATE 0 xefee 62 d 0 - (X: not named because hidden? but still the address is clearly close to the module space)0 xefee 5000 'msdirectx' IRP_MJ_CREATE_NAMED_PIPE 0 x 804 f 355 a ntoskrnl. exe 0 xf 9 a 3 c 000 'i 8042 prt' IRP_MJ_DEVICE_CONTROL 0 xf 9 a 42 e 4 b i 8042 prt. sys 0 xf 9 a 3 c 000 'i 8042 prt' IRP_MJ_INTERNAL_DEVICE_CONTROL 0 xf 99 f 06 b 0 Rapport. KELL. sys - (3 rd party module hooking keyboard driver IRP) 0 xf 9 a 3 c 000 'i 8042 prt' IRP_MJ_SHUTDOWN 0 x 804 f 355 a ntoskrnl. exe 0 xf 9601000 'Ntfs' IRP_MJ_CREATE 0 xefeb 3 bdc 0 xf 9601000 'Ntfs' IRP_MJ_CREATE_NAMED_PIPE 0 xefeb 3 bdc 0 xf 9601000 'Ntfs' IRP_MJ_CLOSE 0 xefeb 3 bdc 0 xf 9601000 'Ntfs' IRP_MJ_READ 0 xefeb 3 bdc. . . 0 xf 9 b 8 c 000 'Cdfs' IRP_MJ_CREATE 0 xefeb 3 bdc 0 xf 9 d 7 c 000 'Msfs' IRP_MJ_CREATE 0 xefeb 3 bdc 0 xf 9 d 8 c 000 'Npfs' IRP_MJ_CREATE 0 xefeb 3 bdc. . . (something hooking everything in ntfs, cdfs, msfs, npfs, and others) - - 9

IDT hook detection • python vol. py idt -f bla. dmp • Shows hooks to the IDT itself, as well as any inline hooks immediately at the target of the IDT entry • Can have semi-misleading results in that most all of the Ki. Unexpected. Interrupt# entries naturally have a jmp to a common function as their first instruction. Also doesn't know about KINTERRUPTs, therefore induces unnecessary suspicion on those entries, and doesn't find KINTERRUPT inline or Service. Routine hooks (but it will get improved with feedback) • • • D 8 Ki. Trap 0 D 0 x 8053 fd 90 ntoskrnl. exe. text E 8 Ki. Trap 0 E 0 xf 9 f 5 c 816 mmpc. sys. text (shadowwalker) F 8 Ki. Trap 0 F 0 x 805407 c 8 ntoskrnl. exe. text 61 8 Ki. Unexpected. Interrupt 49 0 x 8053 cd 5 a ntoskrnl. exe. text => JMP 0 x 8053 d 357 62 8 Ki. Unexpected. Interrupt 50 0 x 81784044 63 8 Ki. Unexpected. Interrupt 51 0 x 8053 cd 6 e ntoskrnl. exe. text => JMP 0 x 8053 d 357 82 8 Ki. Unexpected. Interrupt 82 0 x 8186 fdd 4 83 8 Ki. Unexpected. Interrupt 83 0 x 81 acaa 14 (62, 83 and others turn out to be KINTERRUPTs) 10

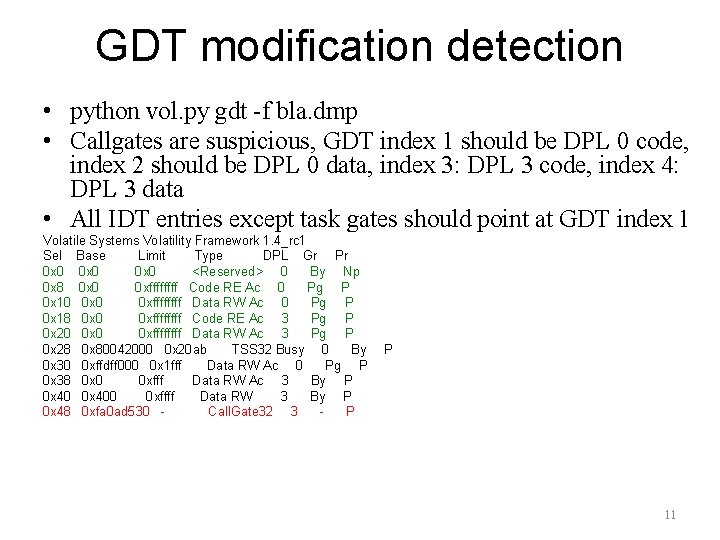
GDT modification detection • python vol. py gdt -f bla. dmp • Callgates are suspicious, GDT index 1 should be DPL 0 code, index 2 should be DPL 0 data, index 3: DPL 3 code, index 4: DPL 3 data • All IDT entries except task gates should point at GDT index 1 Volatile Systems Volatility Framework 1. 4_rc 1 Sel Base Limit Type DPL Gr Pr 0 x 0 <Reserved> 0 By Np 0 x 8 0 x 0 0 xffff Code RE Ac 0 Pg P 0 x 10 0 xffff Data RW Ac 0 Pg P 0 x 18 0 x 0 0 xffff Code RE Ac 3 Pg P 0 x 20 0 xffff Data RW Ac 3 Pg P 0 x 28 0 x 80042000 0 x 20 ab TSS 32 Busy 0 By 0 x 30 0 xffdff 000 0 x 1 fff Data RW Ac 0 Pg P 0 x 38 0 x 0 0 xfff Data RW Ac 3 By P 0 x 400 0 xffff Data RW 3 By P 0 x 48 0 xfa 0 ad 530 Call. Gate 32 3 P P 11

Listing callbacks • python vol. py callbacks -f bla. dmp • Prints kernel callbacks of the following types: – – – – – Ps. Set. Create. Process. Notify. Routine (process creation). Ps. Set. Create. Thread. Notify. Routine (thread creation). Ps. Set. Image. Load. Notify. Routine (DLL/image load). Io. Register. Fs. Registration. Change (file system registration). Ke. Register. Bug. Check and Ke. Register. Bug. Check. Reason. Callback. Cm. Register. Callback (registry callbacks on XP). Cm. Register. Callback. Ex (registry callbacks on Vista and 7). Io. Register. Shutdown. Notification (shutdown callbacks). Dbg. Set. Debug. Print. Callback (debug print callbacks on Vista and 7). – Dbgk. Lkmd. Register. Callback (debug callbacks on 7). • Currently seems to take forever 12

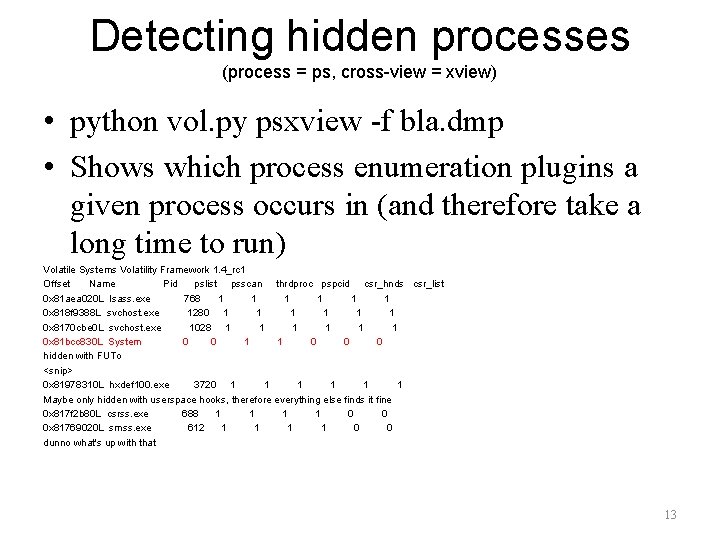
Detecting hidden processes (process = ps, cross-view = xview) • python vol. py psxview -f bla. dmp • Shows which process enumeration plugins a given process occurs in (and therefore take a long time to run) Volatile Systems Volatility Framework 1. 4_rc 1 Offset Name Pid pslist psscan thrdproc pspcid csr_hnds csr_list 0 x 81 aea 020 L lsass. exe 768 1 1 1 0 x 818 f 9388 L svchost. exe 1280 1 1 1 0 x 8170 cbe 0 L svchost. exe 1028 1 1 1 0 x 81 bcc 830 L System 0 0 1 1 0 0 0 hidden with FUTo <snip> 0 x 81978310 L hxdef 100. exe 3720 1 1 1 Maybe only hidden with userspace hooks, therefore everything else finds it fine 0 x 817 f 2 b 80 L csrss. exe 688 1 1 0 0 0 x 81769020 L smss. exe 612 1 1 0 0 dunno what's up with that 13

Listing Windows services • python vol. py svcscan -f bla. dmp • Lots of good stuff there at the end • Still lots to sort through though, doesn't exclude default - this is where you need histograms! 0 x 38 b 268 0 x 108 1192 WZCSVC Wireless Zero Configuration SERVICE_WIN 32_SHARE_PROCESS SERVICE_RUNNING C: WINDOWSSystem 32svchost. exe -k netsvcs 0 x 38 b 2 f 8 0 x 109 ---- xmlprov Network Provisioning Service SERVICE_WIN 32_SHARE_PROCESS SERVICE_STOPPED -------0 x 38 b 388 0 x 10 a ---- msdirectx SERVICE_KERNEL_DRIVER SERVICE_RUNNING Drivermsdirectx 0 x 38 b 418 0 x 10 b ---- mmpc SERVICE_KERNEL_DRIVER SERVICE_RUNNING Drivermmpc 0 x 38 b 4 a 0 0 x 10 c ---- vanquish Vanquish Autoloader v 0. 2. 1 SERVICE_WIN 32_OWN_PROCESS|SERVICE_INTERACTIVE_PROCE SS SERVICE_STOPPED -------0 x 38 b 530 0 x 10 d 3720 Hacker. Defender 100 HXD Service 100 SERVICE_WIN 32_OWN_PROCESS SERVICE_RUNNING C: hxdef 100 rhxdef 100. exe 0 x 38 b 5 d 0 0 x 10 e ---- Ctr 12 Cap SERVICE_KERNEL_DRIVER SERVICE_RUNNING DriverCtr 12 Cap 0 x 38 b 660 0 x 10 f ---- 000627 CE SERVICE_KERNEL_DRIVER SERVICE_STOPPED -------0 x 38 b 6 f 0 0 x 110 ---- basic SERVICE_KERNEL_DRIVER SERVICE_RUNNING Driverbasic 0 x 38 b 778 0 x 111 ---- syse SERVICE_KERNEL_DRIVER SERVICE_RUNNING Driversyse 14

Time-Permitting 15

KOH country for old men • http: //www. rootkit. com/newsread. php? newsid=501 (use wayback machine) • Kernel Object Hooking (KOH) is technically a subset of DKOM • Only thing about kernel objects that it's manipulating is function pointers • Just like in IDT/SSDT/IAT cases, you are just replacing function pointers • The thing is, as opposed to those big name tables, the locations to target for KOH require deeper knowledge of the data structures. • But the idea is that the objects targeted for KOH are going to be potentially popping in and out of existence, or will just generally be in kernel heap memory, and therefore not at well-known locations that the defender can check. • Further, in some case (such as Deferred Procedure Calls) it may be a generic mechanism which can have many different possible function pointers, making it harder to baseline expectations. 16

_KINTERRUPT KOH • http: //www. phrack. org/issues. html? issue=65&id= 4 – Is actually trying to avoid using KOH ("This article present a way of subverting the Windows kernel by modifying only data. No function pointers, no static hooking or others classical technique. ") – But they're using inline hooking in the KINTERRUPT so…what is that? Kernel Object Inline-hooking! KOI! (nah I just made that up) – Just giving it as a reference since it talks about the structure of the KINTERRUPT a bit 17

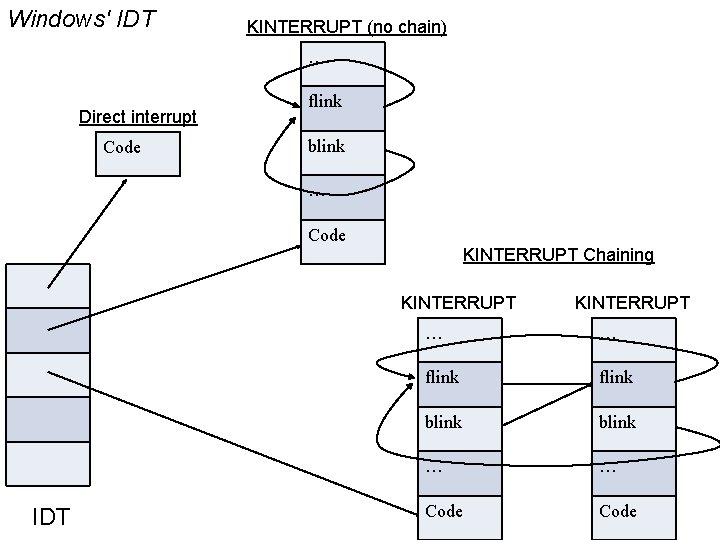
Windows' IDT KINTERRUPT (no chain) … Direct interrupt Code flink blink … Code KINTERRUPT Chaining KINTERRUPT IDT KINTERRUPT … … flink blink … … Code 18

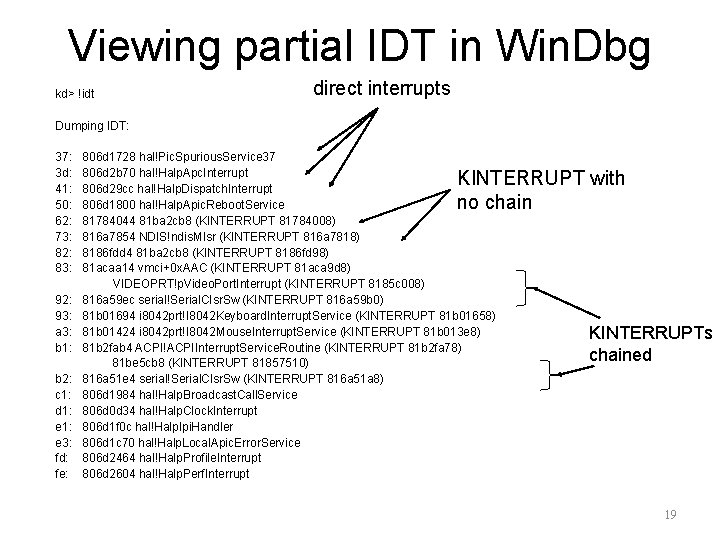
Viewing partial IDT in Win. Dbg kd> !idt direct interrupts Dumping IDT: 37: 3 d: 41: 50: 62: 73: 82: 83: 92: 93: a 3: b 1: b 2: c 1: d 1: e 3: fd: fe: 806 d 1728 hal!Pic. Spurious. Service 37 806 d 2 b 70 hal!Halp. Apc. Interrupt 806 d 29 cc hal!Halp. Dispatch. Interrupt 806 d 1800 hal!Halp. Apic. Reboot. Service 81784044 81 ba 2 cb 8 (KINTERRUPT 81784008) 816 a 7854 NDIS!ndis. MIsr (KINTERRUPT 816 a 7818) 8186 fdd 4 81 ba 2 cb 8 (KINTERRUPT 8186 fd 98) 81 acaa 14 vmci+0 x. AAC (KINTERRUPT 81 aca 9 d 8) VIDEOPRT!p. Video. Port. Interrupt (KINTERRUPT 8185 c 008) 816 a 59 ec serial!Serial. CIsr. Sw (KINTERRUPT 816 a 59 b 0) 81 b 01694 i 8042 prt!I 8042 Keyboard. Interrupt. Service (KINTERRUPT 81 b 01658) 81 b 01424 i 8042 prt!I 8042 Mouse. Interrupt. Service (KINTERRUPT 81 b 013 e 8) 81 b 2 fab 4 ACPI!ACPIInterrupt. Service. Routine (KINTERRUPT 81 b 2 fa 78) 81 be 5 cb 8 (KINTERRUPT 81857510) 816 a 51 e 4 serial!Serial. CIsr. Sw (KINTERRUPT 816 a 51 a 8) 806 d 1984 hal!Halp. Broadcast. Call. Service 806 d 0 d 34 hal!Halp. Clock. Interrupt 806 d 1 f 0 c hal!Halp. Ipi. Handler 806 d 1 c 70 hal!Halp. Local. Apic. Error. Service 806 d 2464 hal!Halp. Profile. Interrupt 806 d 2604 hal!Halp. Perf. Interrupt KINTERRUPT with no chain KINTERRUPTs chained 19

<snip> 73: 816 a 7854 NDIS!ndis. MIsr (KINTERRUPT 816 a 7818) <snip> kd> u 816 a 7854 54 816 a 7855 55 816 a 7856 53 816 a 7857 56 816 a 7858 57 816 a 7859 83 ec 54 <snip> push push sub esp ebx esi edi esp, 54 h kd> dt _KINTERRUPT 816 a 7818 nt!_KINTERRUPT +0 x 000 Type : 22 +0 x 002 Size : 484 +0 x 004 Interrupt. List. Entry : _LIST_ENTRY [ 0 x 816 a 781 c - 0 x 816 a 781 c ] +0 x 00 c Service. Routine : 0 xf 95 ece 10 unsigned char NDIS!ndis. MIsr+0 +0 x 010 Service. Context : 0 x 819652 bc +0 x 014 Spin. Lock : 0 +0 x 018 Tick. Count : 0 xffff +0 x 01 c Actual. Lock : 0 x 816 a 7 a 7 c -> 0 +0 x 020 Dispatch. Address : 0 x 80541550 void nt!Ki. Interrupt. Dispatch+0 +0 x 024 Vector : 0 x 173 +0 x 028 Irql : 0 x 6 '' +0 x 029 Synchronize. Irql : 0 x 6 '' +0 x 02 a Floating. Save : 0 '' +0 x 02 b Connected : 0 x 1 '' +0 x 02 c Number : 0 '' +0 x 02 d Share. Vector : 0 x 1 '' +0 x 030 Mode : 0 ( Level. Sensitive ) +0 x 034 Service. Count : 0 +0 x 038 Dispatch. Count : 0 xffff +0 x 03 c Dispatch. Code : [106] 0 x 56535554 20

_NDIS_PROTOCOL_CHARACTERISTICS KOH • NDIS = Network Driver Interface Specification. MS's network driver abstraction system • Every NDIS driver has to register a bunch of callback functions for how it will handle various activities such as receiving packets, sending packets, • It does this with Ndis. Register. Protocol which takes a pointer to the NDIS_PROTOCOL_CHARACTERISTICS structure which has all those callbacks filled in. – http: //msdn. microsoft. com/en-us/library/ff 554653(v=vs. 85). aspx • The callbacks are a target for KOH • http: //www. f-secure. com/weblog/archives/00001393. html – KOHed by mebroot, rustock, srizbi Book page 614 21

_NDIS_PROTOCOL_CHARACTERISTICS KOH typedef struct _NDIS_PROTOCOL_CHARACTERISTICS { UCHAR Major. Ndis. Version; UCHAR Minor. Ndis. Version; UINT Reserved; OPEN_ADAPTER_COMPLETE_HANDLER Open. Adapter. Complete. Handler; CLOSE_ADAPTER_COMPLETE_HANDLER Close. Adapter. Complete. Handler; SEND_COMPLETE_HANDLER Send. Complete. Handler; TRANSFER_DATA_COMPLETE_HANDLER Transfer. Data. Complete. Handler; RESET_COMPLETE_HANDLER Reset. Complete. Handler; REQUEST_COMPLETE_HANDLER Request. Complete. Handler; RECEIVE_HANDLER Receive. Handler; RECEIVE_COMPLETE_HANDLER Receive. Complete. Handler; STATUS_HANDLER Status. Handler; STATUS_COMPLETE_HANDLER Status. Complete. Handler; NDIS_STRING Name; // // Major. Ndis. Version must be set to 0 x 04 or 0 x 05 // with any of the following members. // RECEIVE_PACKET_HANDLER Receive. Packet. Handler; BIND_HANDLER Bind. Adapter. Handler; UNBIND_HANDLER Unbind. Adapter. Handler; PNP_EVENT_HANDLER Pn. PEvent. Handler; UNLOAD_PROTOCOL_HANDLER Unload. Handler; // // Major. Ndis. Version must be set to 0 x 05 // with any of the following members. // CO_SEND_COMPLETE_HANDLER Co. Send. Complete. Handler; CO_STATUS_HANDLER Co. Status. Handler; CO_RECEIVE_PACKET_HANDLER Co. Receive. Packet. Handler; CO_AF_REGISTER_NOTIFY_HANDLER Co. Af. Register. Notify. Handler; } NDIS_PROTOCOL_CHARACTERISTICS, *PNDIS_PROTOCOL_CHARACTERISTICS; 22

_OBJECT_TYPE_INITIALIZER KOH • Think of it like a structure which holds function pointer for constructors/descructors/accessors for an object • http: //www. prevx. com/blog/120/MBR-rootkitchanges-itself-and-strikes-again. html – The mebroot people are apparently quite familiar with the concept of KOH 23

_OBJECT_TYPE_INITIALIZER nt!_OBJECT_TYPE_INITIALIZER +0 x 000 Length : Uint 2 B +0 x 002 Use. Default. Object : UChar +0 x 003 Case. Insensitive : UChar +0 x 004 Invalid. Attributes : Uint 4 B +0 x 008 Generic. Mapping : _GENERIC_MAPPING +0 x 018 Valid. Access. Mask : Uint 4 B +0 x 01 c Security. Required : UChar +0 x 01 d Maintain. Handle. Count : UChar +0 x 01 e Maintain. Type. List : UChar +0 x 020 Pool. Type : _POOL_TYPE +0 x 024 Default. Paged. Pool. Charge : Uint 4 B +0 x 028 Default. Non. Paged. Pool. Charge : Uint 4 B +0 x 02 c Dump. Procedure : Ptr 32 void +0 x 030 Open. Procedure : Ptr 32 long +0 x 034 Close. Procedure : Ptr 32 void +0 x 038 Delete. Procedure : Ptr 32 void +0 x 03 c Parse. Procedure : Ptr 32 long +0 x 040 Security. Procedure : Ptr 32 long +0 x 044 Query. Name. Procedure : Ptr 32 long +0 x 048 Okay. To. Close. Procedure : Ptr 32 unsigned char 24

Some others • A catalog of windows local kernel-mode backdoors • http: //www. uninformed. org/? v=8&a=2&t=sumry • Very good document, highly recommended read • And again, more structures are mentioned offhandedly in that original KOH article 25

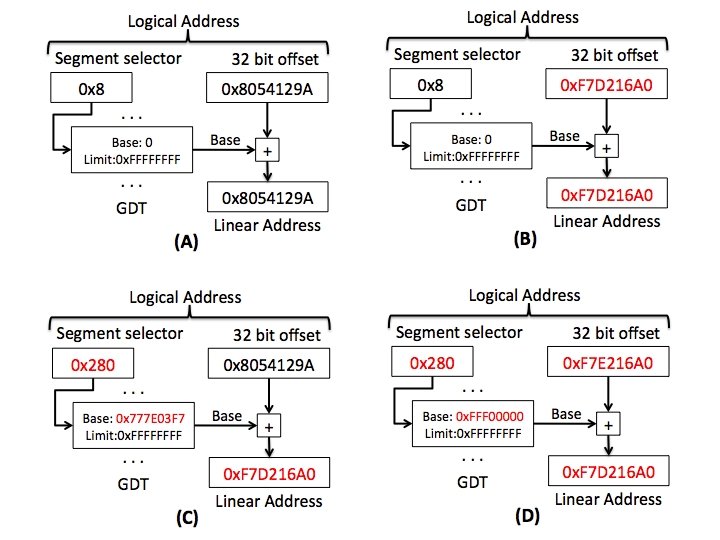
Segment Hooking (Xeno's tiny contribution to the understanding of hooking) • Recall that an interrupt descriptor is actually a far pointer. That means there's a 32 bit offset and a 16 bit segment selector. • A normal hook on a direct interrupt changes the 32 bit offset • Xeno found that we can change the segment selector to select a new segment where the base + existing 32 bit offset = attacker code. • The crazy thing is that we can actually purposely overflow the 32 bit space in order to jump to code which is at a lower address than the existing 32 bit offset. • Existing tools (Win. Dbg, GMER, Memoryze, etc) only look for a change to the 32 bit offset, so this is invisible for the moment (everyone has been informed) 26

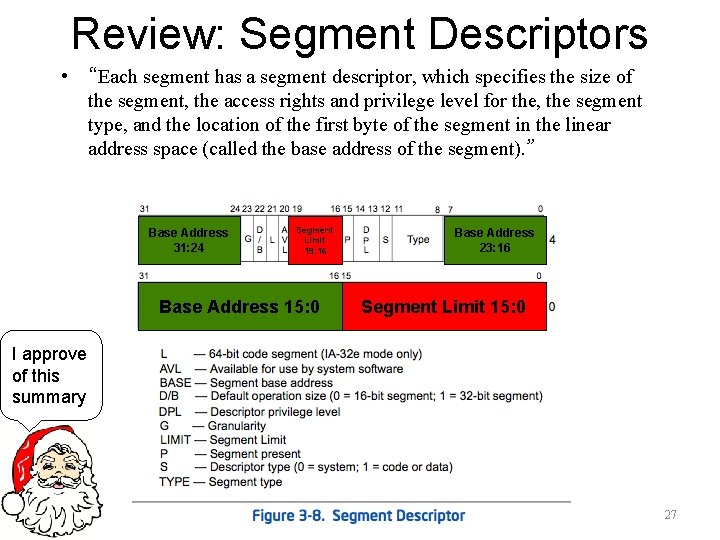
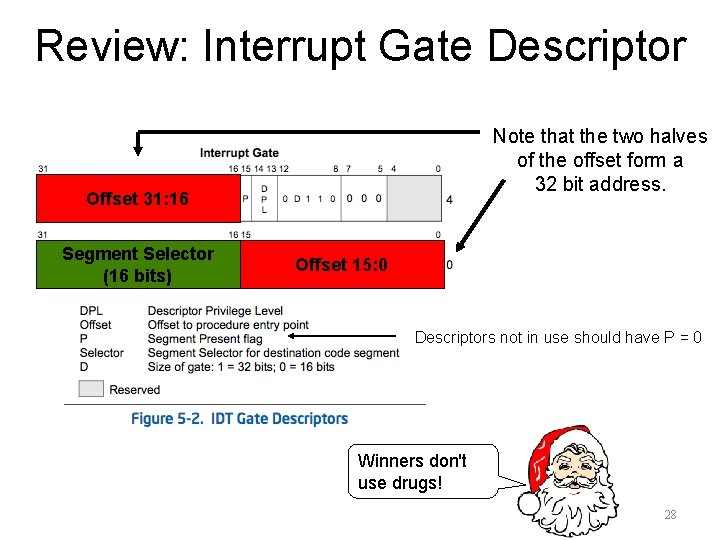
Review: Segment Descriptors • “Each segment has a segment descriptor, which specifies the size of the segment, the access rights and privilege level for the, the segment type, and the location of the first byte of the segment in the linear address space (called the base address of the segment). ” Base Address 31: 24 Segment Limit 19: 16 Base Address 15: 0 Base Address 23: 16 Segment Limit 15: 0 I approve of this summary 27

Review: Interrupt Gate Descriptor Note that the two halves of the offset form a 32 bit address. Offset 31: 16 Segment Selector (16 bits) Offset 15: 0 Descriptors not in use should have P = 0 Winners don't use drugs! 28

29

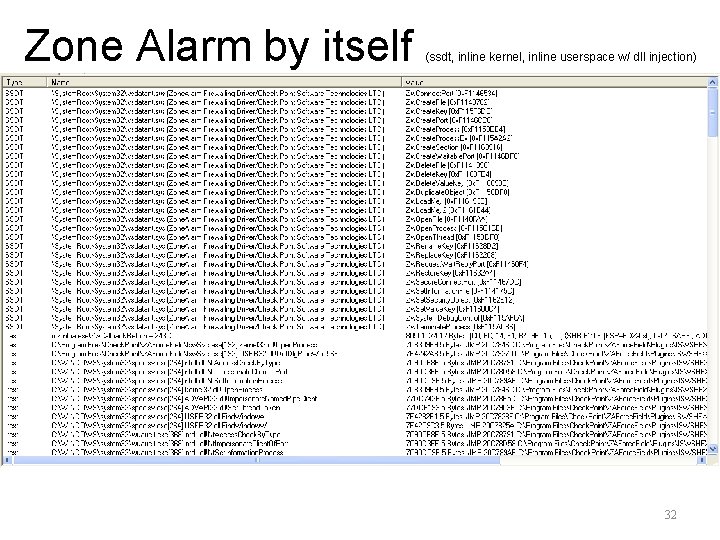
Chaff • As I'm sure you noticed, I threw in some 3 rd party software as chaff - Ctrl 2 Cap, Daemon Tools, Zone Alarm, Trusteer Rapport • I knew this software would make changes to things like the IDT, SSDT, Inline Hooks, IATs, IRP Major Function hooks, IRP device attachment • 3 rd party software's use of hooking techniques makes integrity verification that much harder 30

Ctrl 2 Cap by itself (device attachment) Rapport by itself (SSDT, inline kernel, inline userspace w/dll inject, IRP hook (not shown) 31

Zone Alarm by itself (ssdt, inline kernel, inline userspace w/ dll injection) 32

Zone Alarm by itself (showing the entire inline hook) 33

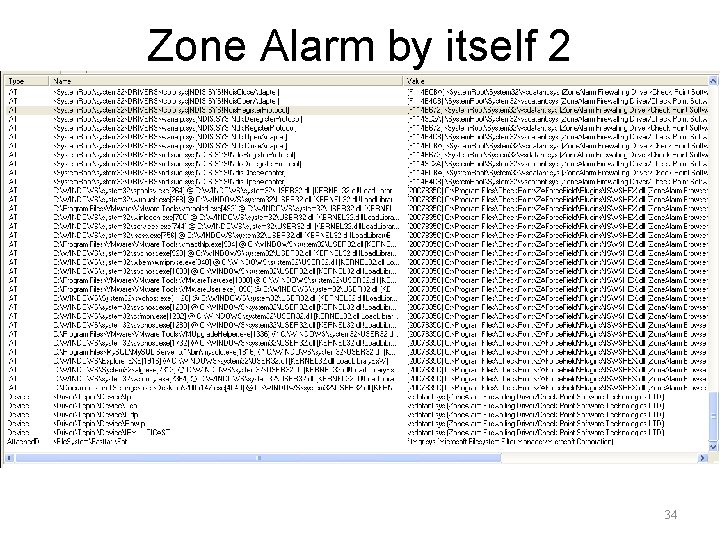
Zone Alarm by itself 2 34

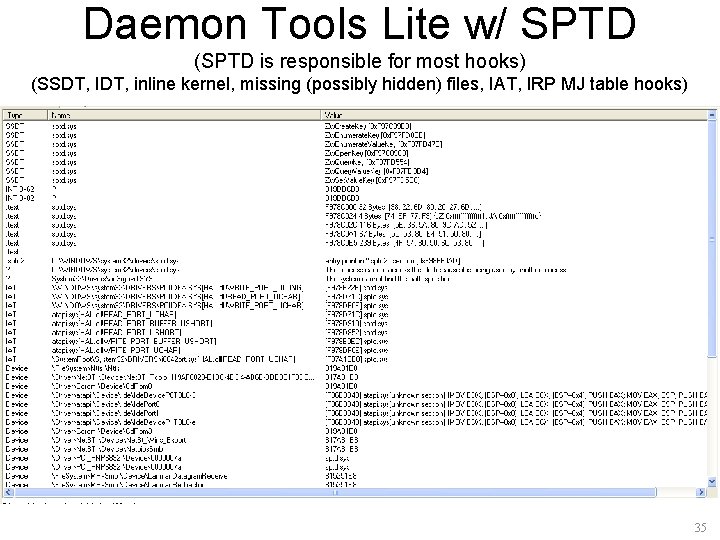
Daemon Tools Lite w/ SPTD (SPTD is responsible for most hooks) (SSDT, IDT, inline kernel, missing (possibly hidden) files, IAT, IRP MJ table hooks) 35

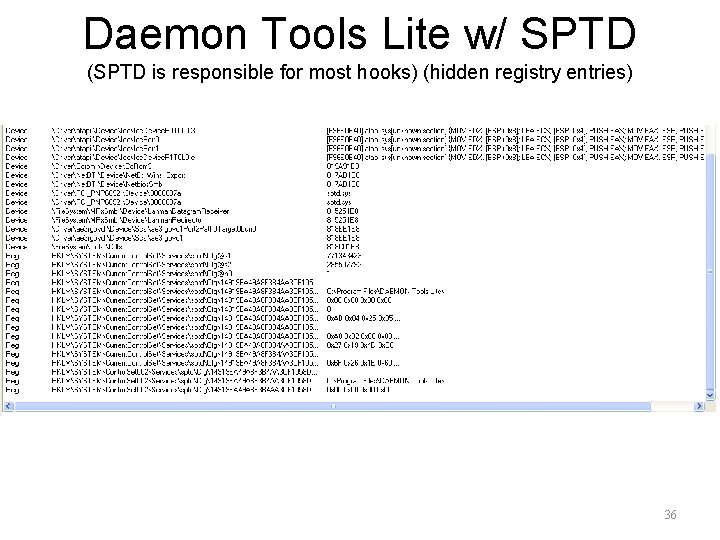
Daemon Tools Lite w/ SPTD (SPTD is responsible for most hooks) (hidden registry entries) 36

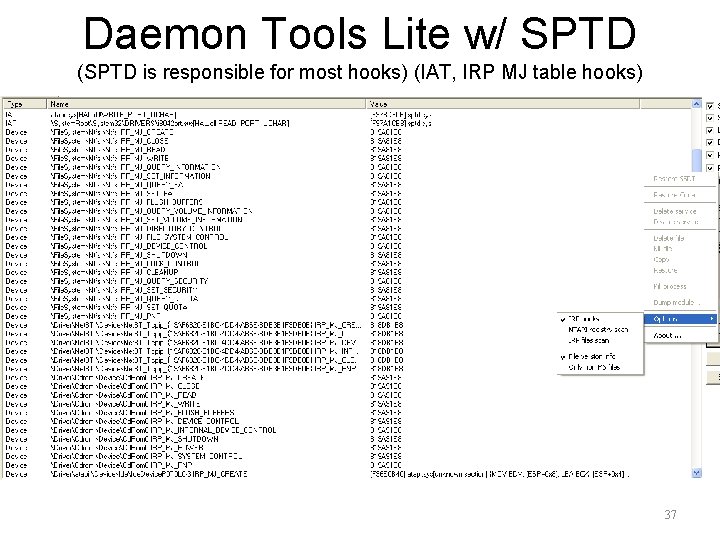
Daemon Tools Lite w/ SPTD (SPTD is responsible for most hooks) (IAT, IRP MJ table hooks) 37

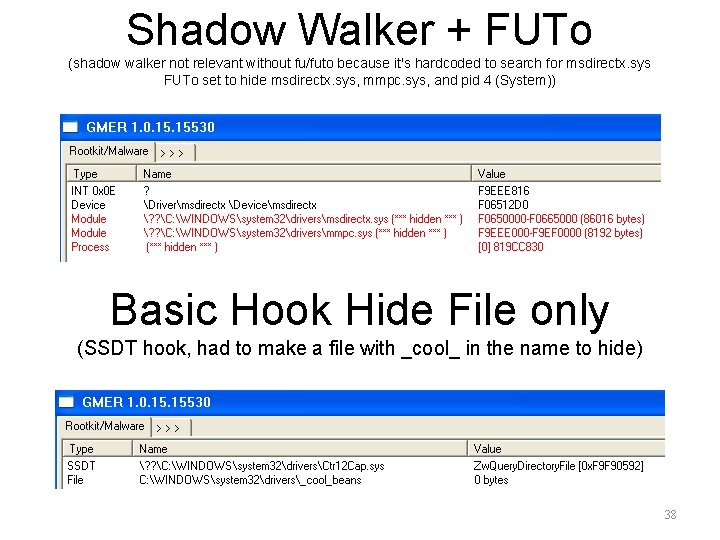
Shadow Walker + FUTo (shadow walker not relevant without fu/futo because it's hardcoded to search for msdirectx. sys FUTo set to hide msdirectx. sys, mmpc. sys, and pid 4 (System)) Basic Hook Hide File only (SSDT hook, had to make a file with _cool_ in the name to hide) 38

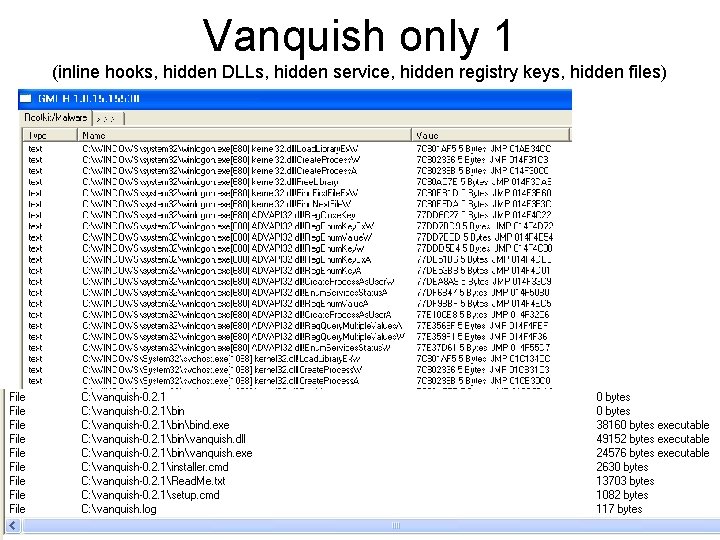
Vanquish only 1 (inline hooks, hidden DLLs, hidden service, hidden registry keys, hidden files) 39

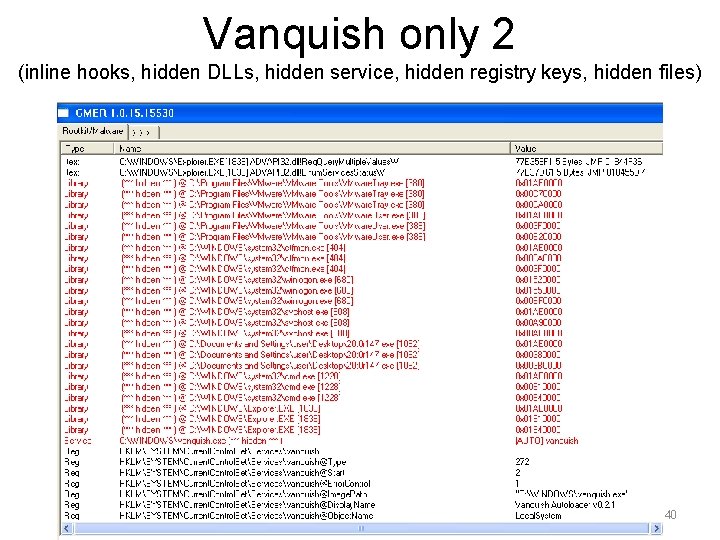
Vanquish only 2 (inline hooks, hidden DLLs, hidden service, hidden registry keys, hidden files) 40

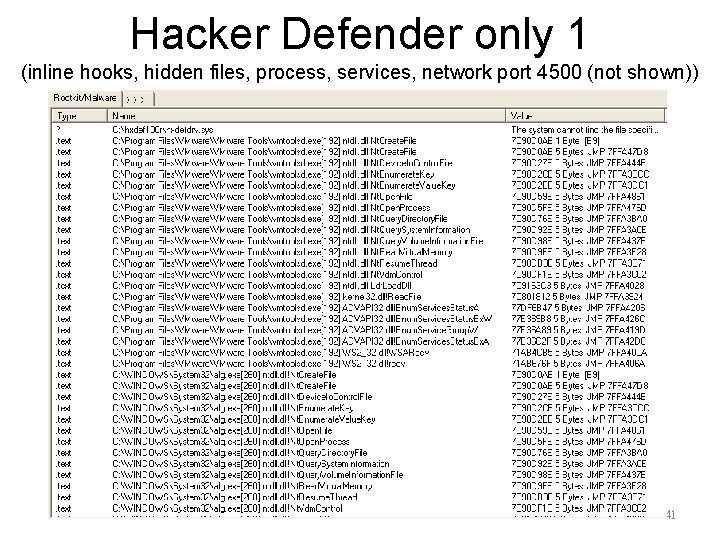
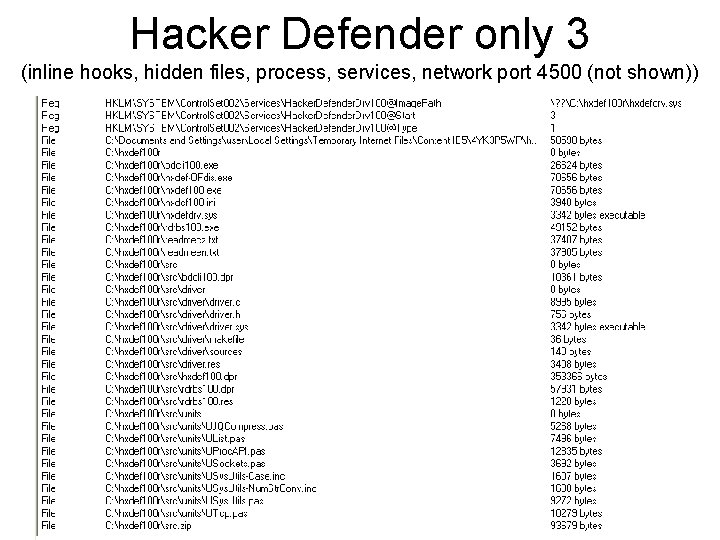
Hacker Defender only 1 (inline hooks, hidden files, process, services, network port 4500 (not shown)) 41

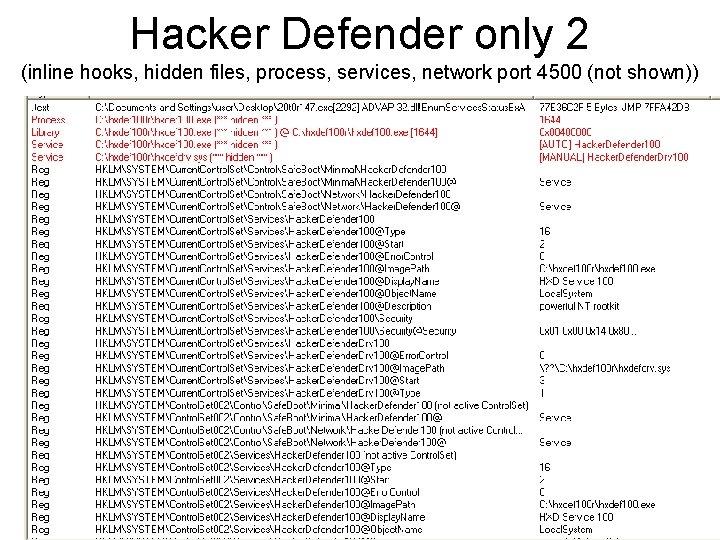
Hacker Defender only 2 (inline hooks, hidden files, process, services, network port 4500 (not shown)) 42

Hacker Defender only 3 (inline hooks, hidden files, process, services, network port 4500 (not shown)) 43

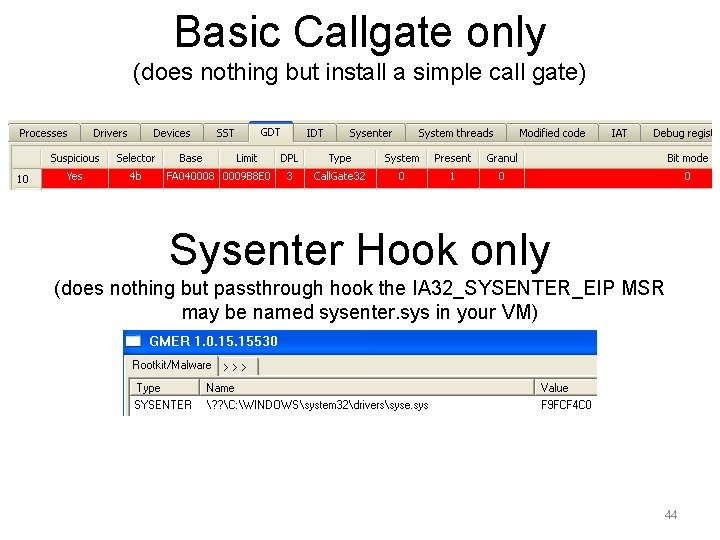
Basic Callgate only (does nothing but install a simple call gate) Sysenter Hook only (does nothing but passthrough hook the IA 32_SYSENTER_EIP MSR may be named sysenter. sys in your VM) 44

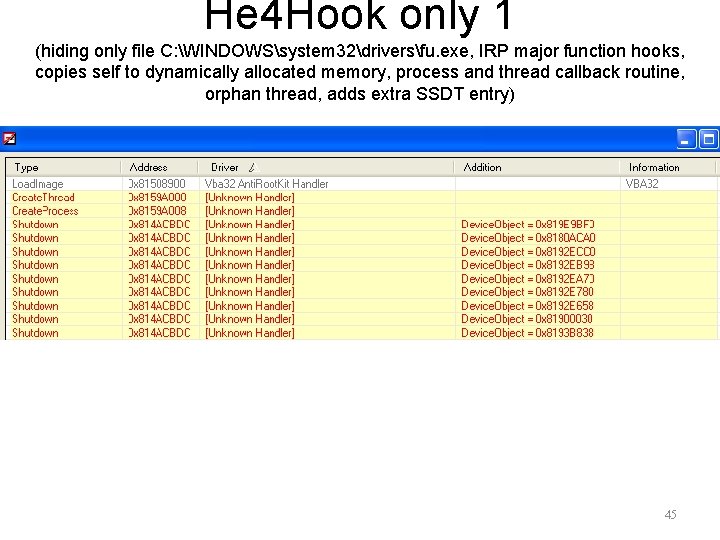
He 4 Hook only 1 (hiding only file C: WINDOWSsystem 32driversfu. exe, IRP major function hooks, copies self to dynamically allocated memory, process and thread callback routine, orphan thread, adds extra SSDT entry) 45

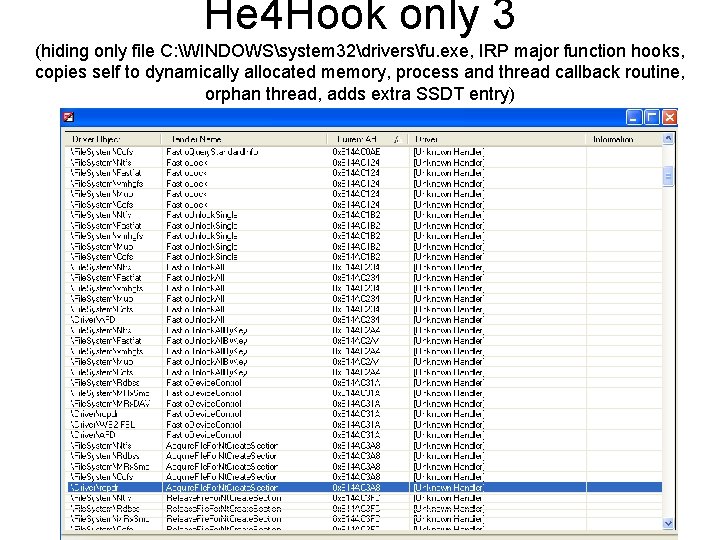
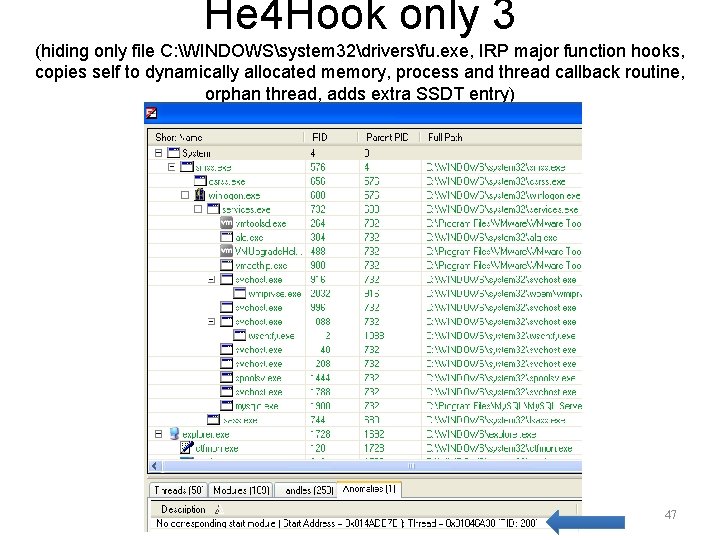
He 4 Hook only 3 (hiding only file C: WINDOWSsystem 32driversfu. exe, IRP major function hooks, copies self to dynamically allocated memory, process and thread callback routine, orphan thread, adds extra SSDT entry) 46

He 4 Hook only 3 (hiding only file C: WINDOWSsystem 32driversfu. exe, IRP major function hooks, copies self to dynamically allocated memory, process and thread callback routine, orphan thread, adds extra SSDT entry) 47

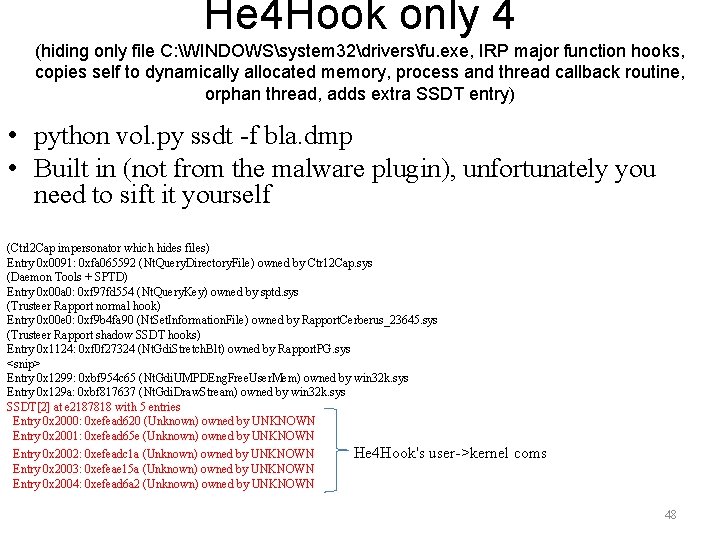
He 4 Hook only 4 (hiding only file C: WINDOWSsystem 32driversfu. exe, IRP major function hooks, copies self to dynamically allocated memory, process and thread callback routine, orphan thread, adds extra SSDT entry) • python vol. py ssdt -f bla. dmp • Built in (not from the malware plugin), unfortunately you need to sift it yourself (Ctrl 2 Cap impersonator which hides files) Entry 0 x 0091: 0 xfa 065592 (Nt. Query. Directory. File) owned by Ctr 12 Cap. sys (Daemon Tools + SPTD) Entry 0 x 00 a 0: 0 xf 97 fd 554 (Nt. Query. Key) owned by sptd. sys (Trusteer Rapport normal hook) Entry 0 x 00 e 0: 0 xf 9 b 4 fa 90 (Nt. Set. Information. File) owned by Rapport. Cerberus_23645. sys (Trusteer Rapport shadow SSDT hooks) Entry 0 x 1124: 0 xf 0 f 27324 (Nt. Gdi. Stretch. Blt) owned by Rapport. PG. sys <snip> Entry 0 x 1299: 0 xbf 954 c 65 (Nt. Gdi. UMPDEng. Free. User. Mem) owned by win 32 k. sys Entry 0 x 129 a: 0 xbf 817637 (Nt. Gdi. Draw. Stream) owned by win 32 k. sys SSDT[2] at e 2187818 with 5 entries Entry 0 x 2000: 0 xefead 620 (Unknown) owned by UNKNOWN Entry 0 x 2001: 0 xefead 65 e (Unknown) owned by UNKNOWN Entry 0 x 2002: 0 xefeadc 1 a (Unknown) owned by UNKNOWN Entry 0 x 2003: 0 xefeae 15 a (Unknown) owned by UNKNOWN Entry 0 x 2004: 0 xefead 6 a 2 (Unknown) owned by UNKNOWN He 4 Hook's user->kernel coms 48

Win. Dbg Rootkit Searching Cheat-Sheet • List all processes – !process 0 0 – will be fooled by DKOM process unlinking! • Change into a process contest –. process <pid> or. process <EPROCESS address> • List all kernel drivers – lmf • "list loaded modules with file information" – will be fooled by DKOM driver unlinking! 49

Win. Dbg Rootkit Searching Cheat-Sheet 2 • Search for inline hooks in a exe/dll/sys file – !chkimg -d <module name> – !for_each_module !chkimg -d @#Module. Name • Examine each thread’s Service. Table to see which System. Service. Descriptor. Table struct it’s pointing at (there should only be two results and they should correspond to the addresses of Ke. Service. Descriptor. Table or Ke. Service. Descriptor. Table. Shadow – !for_each_thread ". echo Thread: @#Thread; dt nt!_kthread Service. Table @#Thread" 50

Win. Dbg Rootkit Searching Cheat-Sheet 3 • Examine the SSDT function pointers – dd Ke. Service. Descriptor. Table L 10 • says to print 0 x 10 dword values starting at Ke. Service. Descriptor. Table 8055 c 700 8055 c 710 8055 c 720 8055 c 730 80504480 0000011 c 805048 f 4 00000000 00000000 00000000 – The 0 x 80504480 is Service. Table. Base (start of the array of function pointers) and 0 x 11 C is the total number of function pointers – dds 0 x 80504480 L 112 • Says to print the symbol names for the 0 x 112 dwords which are going to be printed out 80504480 80504484 80504488 8050448 c 80504490 … 805 a 4630 nt!Nt. Accept. Connect. Port 805 f 140 e nt!Nt. Access. Check 805 f 4 c 44 nt!Nt. Access. Check. And. Audit. Alarm 805 f 1440 nt!Nt. Access. Check. By. Type 805 f 4 c 7 e nt!Nt. Access. Check. By. Type. And. Audit. Alarm 51

Win. Dbg Rootkit Searching Cheat-Sheet 3 • Check the sysenter MSRs – rdmsr 0 x 176 (for IA 32_SYSENTER_EIP) – rdmsr 0 x 174 (for IA 32_SYSENTER_CS) • Examine the IDT and GDT by using the !protmode plugin from Intermediate x 86 class • Examine the IDT – !idt –a (shows all entries) – !idt (shows only some entries which don’t point at nt or hal) • Break on each module load during boot – sxe -c ". lastevent" ld • Just list each module loading – sxn -c ". lastevent" ld • Turn off breaks/notifications – sxi -c "" ld 52

Listing registered callbacks in Win. Dbg • http: //analyze-v. com/? p=746 - process/memory image load (Ps. Set. Create. Process. Notify. Routine[Ex]/Ps. Set. Image. Load. Notify. Routine) • http: //analyze-v. com/? p=756 - registry callbacks(Cm. Register. Callback[Ex]) • Here comes a new challenger! Hadoken! • http: //www. moonsols. com/2011/02/17/global-windows-callbacks-and-windbg/ kd> $$>a<c: pscallbacks. wbs ************************ * This command brought to you by Analyze-v. com * ************************ * Printing image load callbacks. . . * ***************************************** * Printing process notification callbacks. . . * *********************** 814 ec 008 ff 2508605 c 81 jmp dword ptr ds: [815 C 6008 h] 53

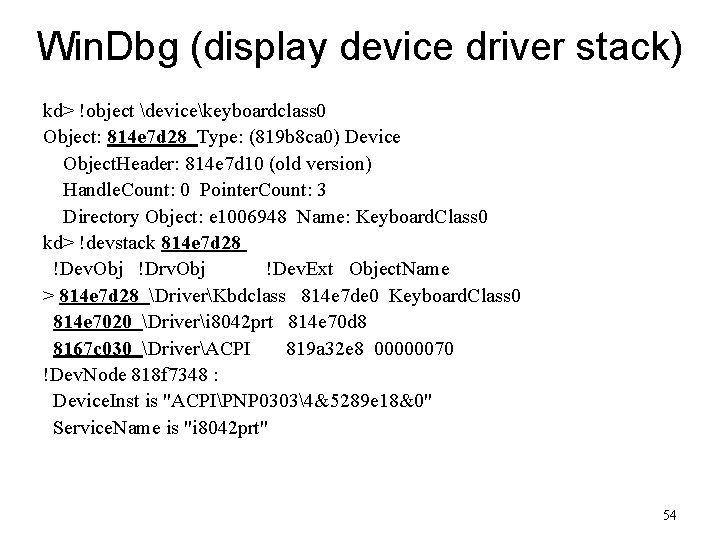
Win. Dbg (display device driver stack) kd> !object devicekeyboardclass 0 Object: 814 e 7 d 28 Type: (819 b 8 ca 0) Device Object. Header: 814 e 7 d 10 (old version) Handle. Count: 0 Pointer. Count: 3 Directory Object: e 1006948 Name: Keyboard. Class 0 kd> !devstack 814 e 7 d 28 !Dev. Obj !Drv. Obj !Dev. Ext Object. Name > 814 e 7 d 28 DriverKbdclass 814 e 7 de 0 Keyboard. Class 0 814 e 7020 Driveri 8042 prt 814 e 70 d 8 8167 c 030 DriverACPI 819 a 32 e 8 00000070 !Dev. Node 818 f 7348 : Device. Inst is "ACPIPNP 03034&5289 e 18&0" Service. Name is "i 8042 prt" 54

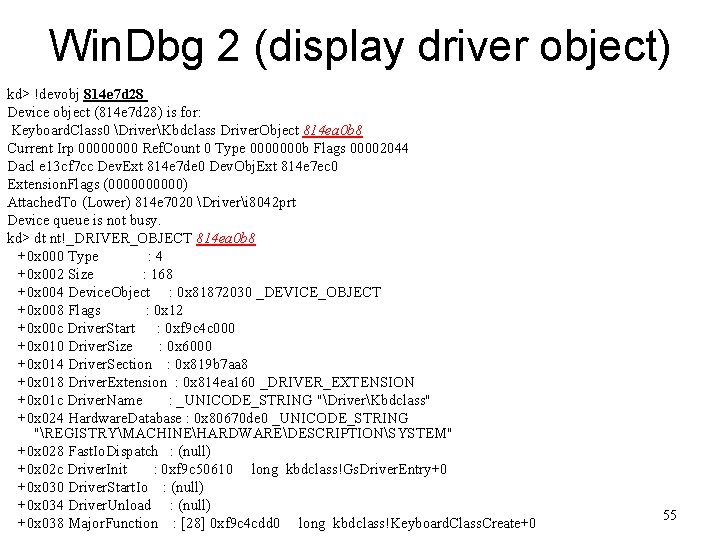
Win. Dbg 2 (display driver object) kd> !devobj 814 e 7 d 28 Device object (814 e 7 d 28) is for: Keyboard. Class 0 DriverKbdclass Driver. Object 814 ea 0 b 8 Current Irp 0000 Ref. Count 0 Type 0000000 b Flags 00002044 Dacl e 13 cf 7 cc Dev. Ext 814 e 7 de 0 Dev. Obj. Ext 814 e 7 ec 0 Extension. Flags (00000) Attached. To (Lower) 814 e 7020 Driveri 8042 prt Device queue is not busy. kd> dt nt!_DRIVER_OBJECT 814 ea 0 b 8 +0 x 000 Type : 4 +0 x 002 Size : 168 +0 x 004 Device. Object : 0 x 81872030 _DEVICE_OBJECT +0 x 008 Flags : 0 x 12 +0 x 00 c Driver. Start : 0 xf 9 c 4 c 000 +0 x 010 Driver. Size : 0 x 6000 +0 x 014 Driver. Section : 0 x 819 b 7 aa 8 +0 x 018 Driver. Extension : 0 x 814 ea 160 _DRIVER_EXTENSION +0 x 01 c Driver. Name : _UNICODE_STRING "DriverKbdclass" +0 x 024 Hardware. Database : 0 x 80670 de 0 _UNICODE_STRING "REGISTRYMACHINEHARDWAREDESCRIPTIONSYSTEM" +0 x 028 Fast. Io. Dispatch : (null) +0 x 02 c Driver. Init : 0 xf 9 c 50610 long kbdclass!Gs. Driver. Entry+0 +0 x 030 Driver. Start. Io : (null) +0 x 034 Driver. Unload : (null) +0 x 038 Major. Function : [28] 0 xf 9 c 4 cdd 0 long kbdclass!Keyboard. Class. Create+0 55

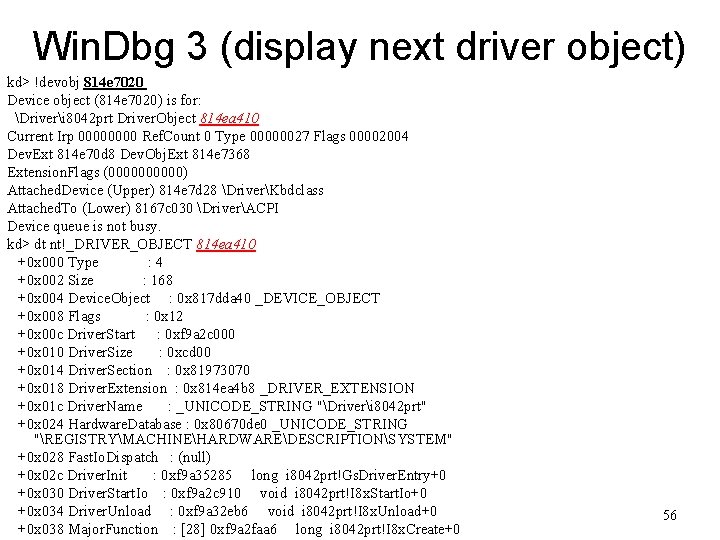
Win. Dbg 3 (display next driver object) kd> !devobj 814 e 7020 Device object (814 e 7020) is for: Driveri 8042 prt Driver. Object 814 ea 410 Current Irp 0000 Ref. Count 0 Type 00000027 Flags 00002004 Dev. Ext 814 e 70 d 8 Dev. Obj. Ext 814 e 7368 Extension. Flags (00000) Attached. Device (Upper) 814 e 7 d 28 DriverKbdclass Attached. To (Lower) 8167 c 030 DriverACPI Device queue is not busy. kd> dt nt!_DRIVER_OBJECT 814 ea 410 +0 x 000 Type : 4 +0 x 002 Size : 168 +0 x 004 Device. Object : 0 x 817 dda 40 _DEVICE_OBJECT +0 x 008 Flags : 0 x 12 +0 x 00 c Driver. Start : 0 xf 9 a 2 c 000 +0 x 010 Driver. Size : 0 xcd 00 +0 x 014 Driver. Section : 0 x 81973070 +0 x 018 Driver. Extension : 0 x 814 ea 4 b 8 _DRIVER_EXTENSION +0 x 01 c Driver. Name : _UNICODE_STRING "Driveri 8042 prt" +0 x 024 Hardware. Database : 0 x 80670 de 0 _UNICODE_STRING "REGISTRYMACHINEHARDWAREDESCRIPTIONSYSTEM" +0 x 028 Fast. Io. Dispatch : (null) +0 x 02 c Driver. Init : 0 xf 9 a 35285 long i 8042 prt!Gs. Driver. Entry+0 +0 x 030 Driver. Start. Io : 0 xf 9 a 2 c 910 void i 8042 prt!I 8 x. Start. Io+0 +0 x 034 Driver. Unload : 0 xf 9 a 32 eb 6 void i 8042 prt!I 8 x. Unload+0 +0 x 038 Major. Function : [28] 0 xf 9 a 2 faa 6 long i 8042 prt!I 8 x. Create+0 56

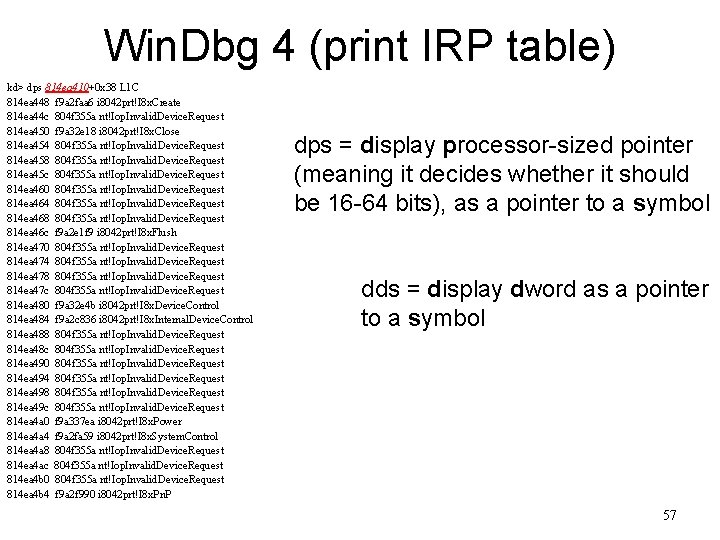
Win. Dbg 4 (print IRP table) kd> dps 814 ea 410+0 x 38 L 1 C 814 ea 448 f 9 a 2 faa 6 i 8042 prt!I 8 x. Create 814 ea 44 c 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 450 f 9 a 32 e 18 i 8042 prt!I 8 x. Close 814 ea 454 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 458 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 45 c 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 460 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 464 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 468 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 46 c f 9 a 2 e 1 f 9 i 8042 prt!I 8 x. Flush 814 ea 470 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 474 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 478 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 47 c 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 480 f 9 a 32 e 4 b i 8042 prt!I 8 x. Device. Control 814 ea 484 f 9 a 2 c 836 i 8042 prt!I 8 x. Internal. Device. Control 814 ea 488 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 48 c 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 490 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 494 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 498 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 49 c 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 4 a 0 f 9 a 337 ea i 8042 prt!I 8 x. Power 814 ea 4 a 4 f 9 a 2 fa 59 i 8042 prt!I 8 x. System. Control 814 ea 4 a 8 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 4 ac 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 4 b 0 804 f 355 a nt!Iop. Invalid. Device. Request 814 ea 4 b 4 f 9 a 2 f 990 i 8042 prt!I 8 x. Pn. P dps = display processor-sized pointer (meaning it decides whether it should be 16 -64 bits), as a pointer to a symbol dds = display dword as a pointer to a symbol 57

Level up! • +120 Win. Dbg EXP • +1 Skill Point, +1 r 0 x 0 r Point • You gained new tool "Laboskopia Win. Dbg scripts"! – http: //www. laboskopia. com/download/Sysec. Labs. Windbg-Script. zip • Now use em! – http: //www. reconstructer. org/papers/Hunting%20 r ootkits%20 with%20 Windbg. pdf 58

Teardown close out • What did we learn? – Using GMER, Tuluka, Virus Blok Ada Anti. Rookit for in-system rootkit detection – Using Win. Dbg for live debugging – Using Volatility for offline memory analysis – IDT, IAT, inline, SSDT, SYSENTER, IRP hooking – GDT call gates, DKOM, KOH, kernel callbacks, bootkits 59

Materials for you • These slides • The anonymized writeups from people who submitted their homework • Spreadsheet showing what tools detect • Tiddly. Wiki with example of running to ground a false positive (due to Symantec), and the true positive (shadowwalker). • Collection of rootkits installed on the VM + the. bat file used to install them. (Don't download to any system with on -access AV scanning, since some of them will be flagged. ) • Go analyze the existing VM again with different tools to get more familiarity with them. I will distribute a VM in the future which will have a couple things installed which will be more difficult to detect, but which will still be within the materials covered in this class. 60

Required Recommended r 0 x 0 r Skill Tree Approved Intended Future Malware Analysis you are here! Advanced x 86 TBD Rootkits (Xeno Kovah) (Matt Briggs - Fall 2011) Reverse Engineering (Matt Briggs - May 2 -3 2011) Intermediate x 86 Life of Binaries (Xeno Kovah) Vulnerabilities & Exploits (Corey Kallenberg June 6 -10) Intro x 86 (Xeno Kovah) 61

Required Recommended r 0 x 0 r Skill Tree Approved Intended Future Malware Analysis (Matt Briggs - Fall 2011) Advanced x 86 TBD Rootkits (Xeno Kovah) Intermediate x 86 Life of Binaries (Xeno Kovah) you should be there! Reverse Engineering Vulnerabilities & Exploits (Matt Briggs - May 2 -3 2011) (Corey Kallenberg) Intro x 86 (Xeno Kovah) 62

Rootkits: 63