RoleBased Access Control Overview SSD RH Role Hierarchy
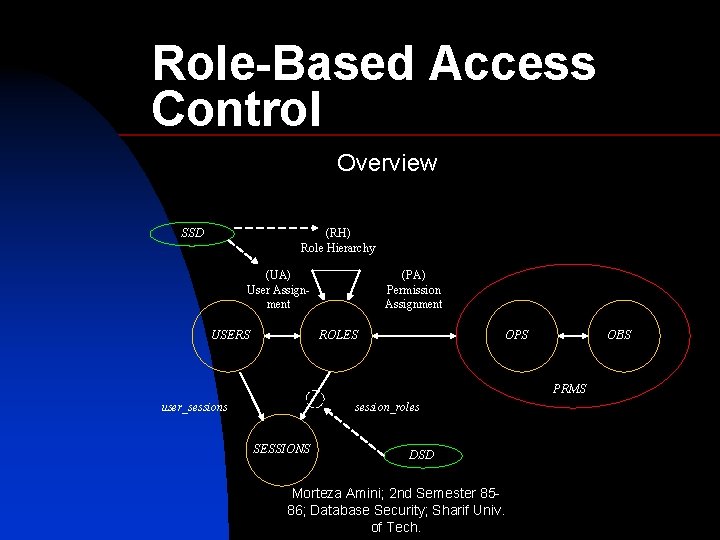
Role-Based Access Control Overview SSD (RH) Role Hierarchy (UA) User Assignment USERS (PA) Permission Assignment ROLES OPS OBS PRMS user_sessions session_roles SESSIONS DSD Morteza Amini; 2 nd Semester 8586; Database Security; Sharif Univ. of Tech.

Objective n n n Compatibility with organizational structures Easy administration Expressiveness: DAC or MAC Principle of least privilege Separation of Duty (So. D) Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.

Access Controls Types n n n Discretionary Access Control Mandatory Access Control Role-Based Access Control Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
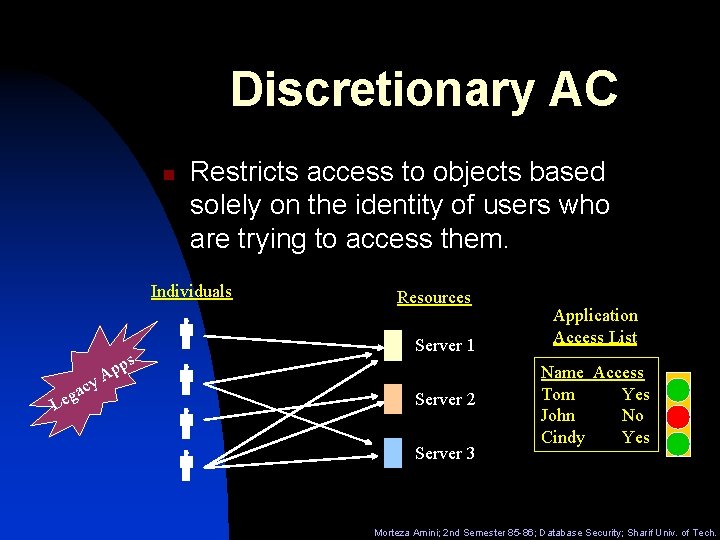
Discretionary AC n Restricts access to objects based solely on the identity of users who are trying to access them. Individuals s Le g acy p Ap Resources Server 1 Server 2 Server 3 Application Access List Name Access Tom Yes John No Cindy Yes Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.

Mandatory AC n MAC mechanisms assign a security level to all information, assign a security clearance to each user, and ensure that all users only have access to that data for which they have a clearance. Principle: Read Down Access equal or less Clearance Write Up Access equal or higher Clearance Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
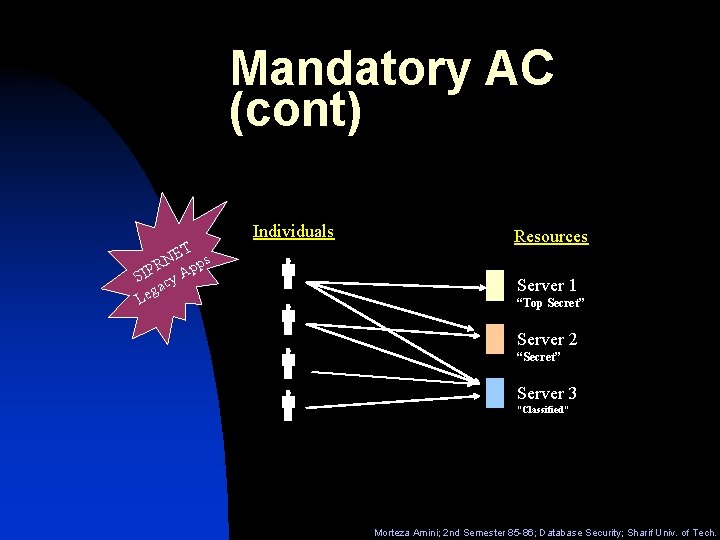
Mandatory AC (cont) ET s N R pp SIP cy A ga Le Individuals Resources Server 1 “Top Secret” Server 2 “Secret” Server 3 “Classified” Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
![Role-Based AC n “Ideally, the [RBAC] system is clearly defined and agile, making the Role-Based AC n “Ideally, the [RBAC] system is clearly defined and agile, making the](http://slidetodoc.com/presentation_image_h/dacecd59a44134c6597cb8c5741f9ce0/image-7.jpg)
Role-Based AC n “Ideally, the [RBAC] system is clearly defined and agile, making the addition of new applications, roles, and employees as efficient as possible” n n A user has access to an object based on the assigned role. Roles are defined based on job functions. Permissions are defined based on job authority and responsibilities within a job function. Operations on an object are invocated based on the permissions. The object is concerned with the user’s role and not the user. Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
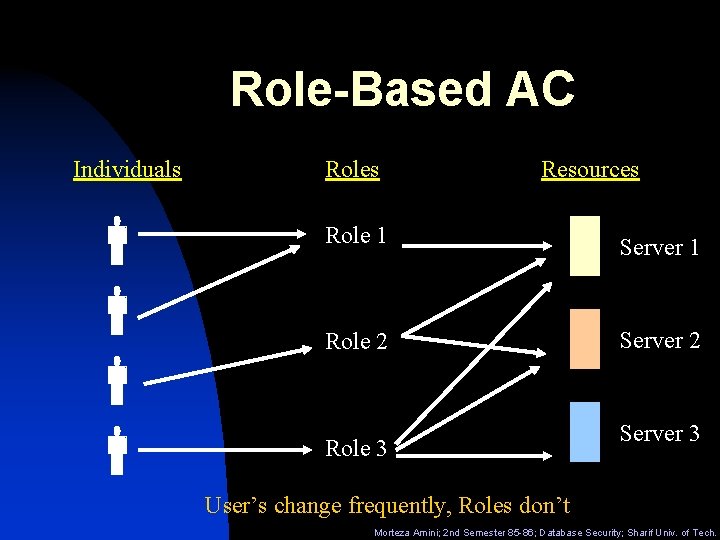
Role-Based AC Individuals Roles Resources Role 1 Server 1 Role 2 Server 2 Role 3 Server 3 User’s change frequently, Roles don’t Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.

Privilege n n Roles are engineered based on the principle of least privileged. A role contains the minimum amount of permissions to instantiate an object. A user is assigned to a role that allows him or her to perform only what’s required for that role. No single role is given more permission than the same role for another user. Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
Role-Based AC Framework n n Core Components Constraining Components u Hierarchical RBAC « General « Limited u Separation of Duty Relations « Static « Dynamic Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
Core Components n Defines: USERS u ROLES u OPERATIONS (ops) u OBJECTS (obs) u User Assignments (ua) u « assigned_users Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
Core Components (cont) u Permissions (prms) « Assigned Permissions « Object Permissions « Operation Permissions u Sessions « User Sessions « Available Session Permissions « Session Roles Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
Constraint Components n Role Hierarchies (rh) General u Limited u n Separation of Duties Static u Dynamic u Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
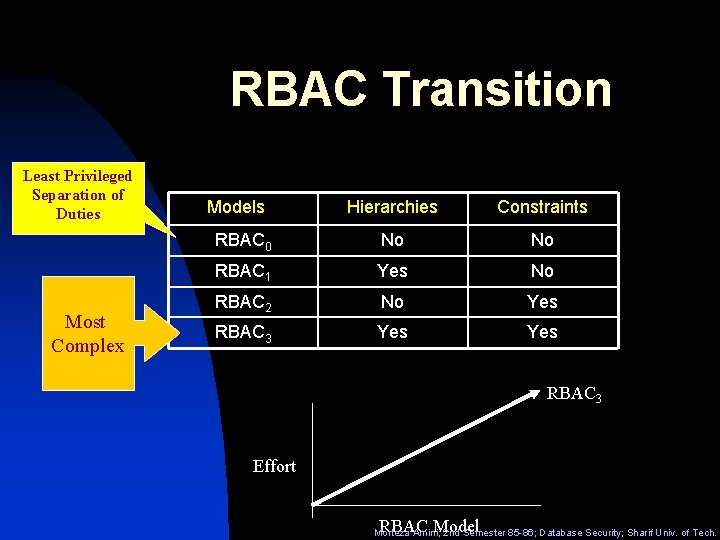
RBAC Transition Least Privileged Separation of Duties Most Complex Models Hierarchies Constraints RBAC 0 No No RBAC 1 Yes No RBAC 2 No Yes RBAC 3 Effort RBAC Model Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
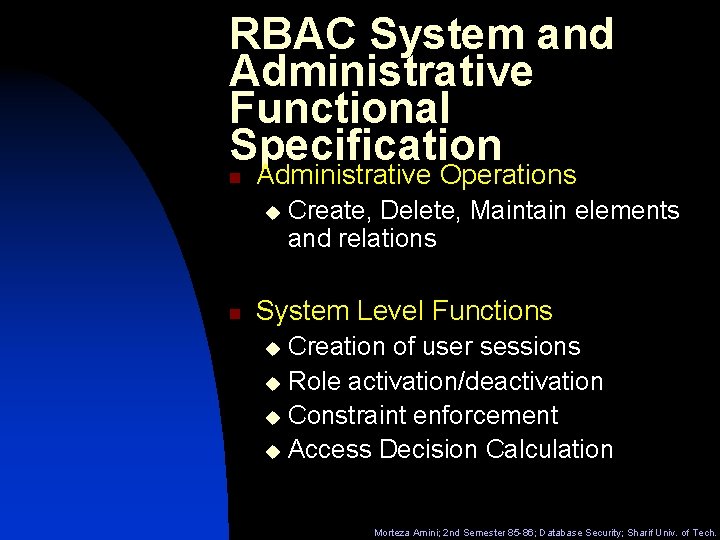
RBAC System and Administrative Functional Specification n Administrative Operations u n Create, Delete, Maintain elements and relations System Level Functions Creation of user sessions u Role activation/deactivation u Constraint enforcement u Access Decision Calculation u Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
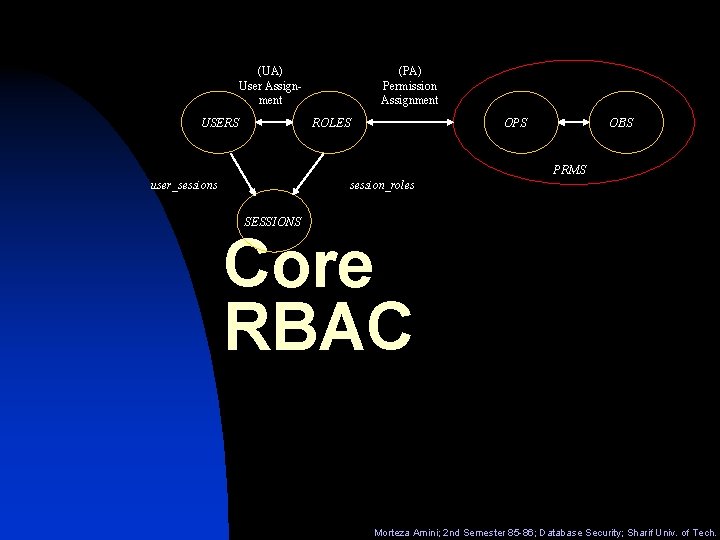
(UA) User Assignment USERS (PA) Permission Assignment ROLES OPS OBS PRMS user_sessions session_roles SESSIONS Core RBAC Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
USERS Process Intelligent Agent Person Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
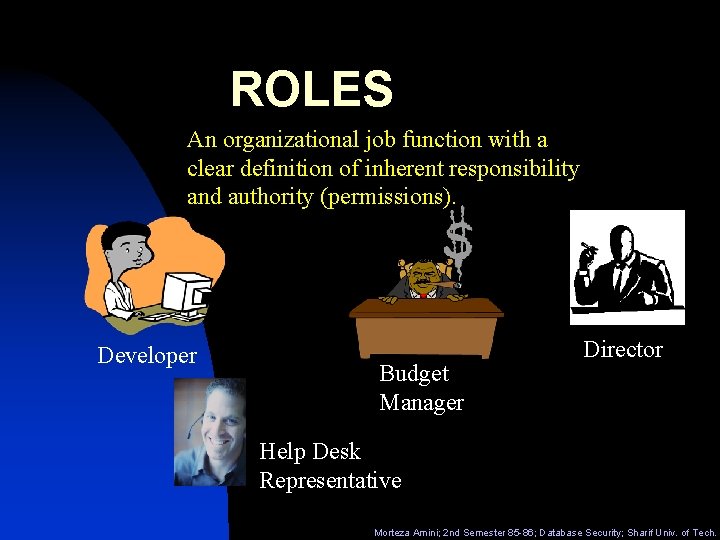
ROLES An organizational job function with a clear definition of inherent responsibility and authority (permissions). Developer Budget Manager Director Help Desk Representative Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.

OPS (operations) An execution of an a program specific function that’s invocated by a user. • Database – Update Insert Append Delete • Locks – Open Close • Reports – Create View Print • Applications - Read Write Execute SQL Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.

OBS (objects) An entity that contains or receives information, or has exhaustible system resources. • OS Files or Directories • DB Columns, Rows, Tables, or Views • Printer • Disk Space • Lock Mechanisms RBAC will deal with all the objects listed in the permissions assigned to roles. Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
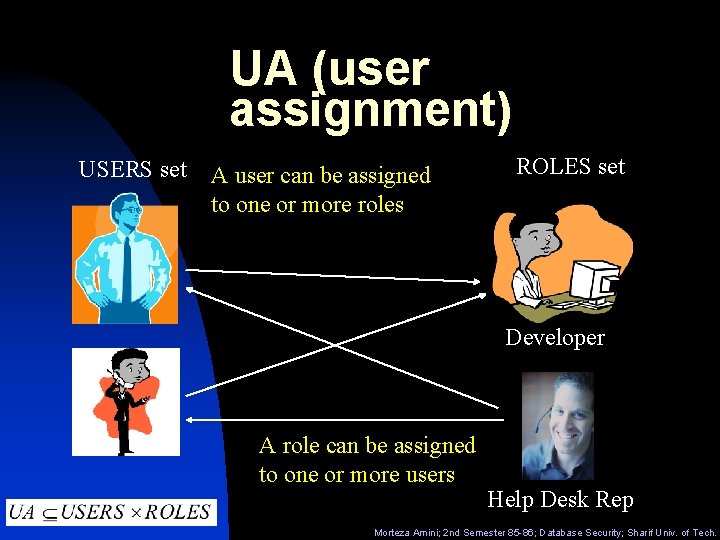
UA (user assignment) USERS set A user can be assigned to one or more roles ROLES set Developer A role can be assigned to one or more users Help Desk Rep Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
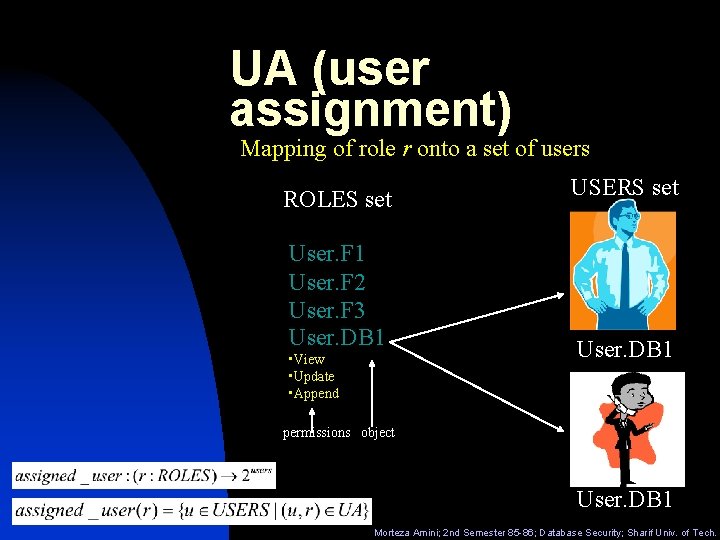
UA (user assignment) Mapping of role r onto a set of users ROLES set USERS set User. F 1 User. F 2 User. F 3 User. DB 1 • View • Update • Append permissions object User. DB 1 Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
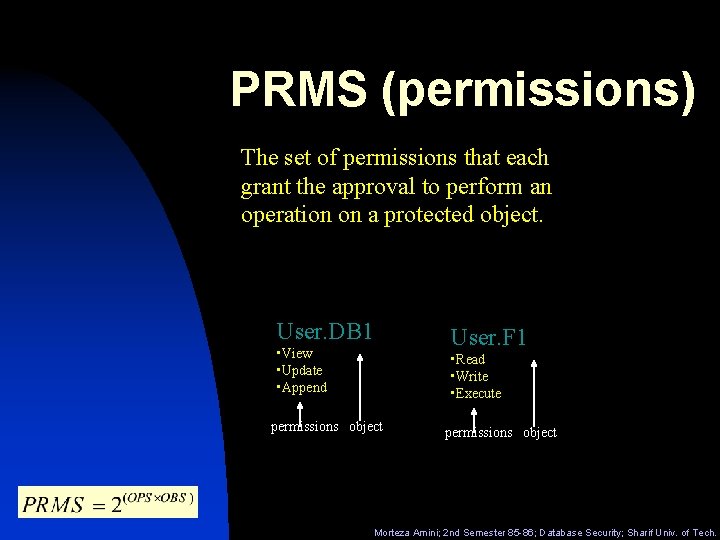
PRMS (permissions) The set of permissions that each grant the approval to perform an operation on a protected object. User. DB 1 User. F 1 • View • Update • Append • Read • Write • Execute permissions object Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
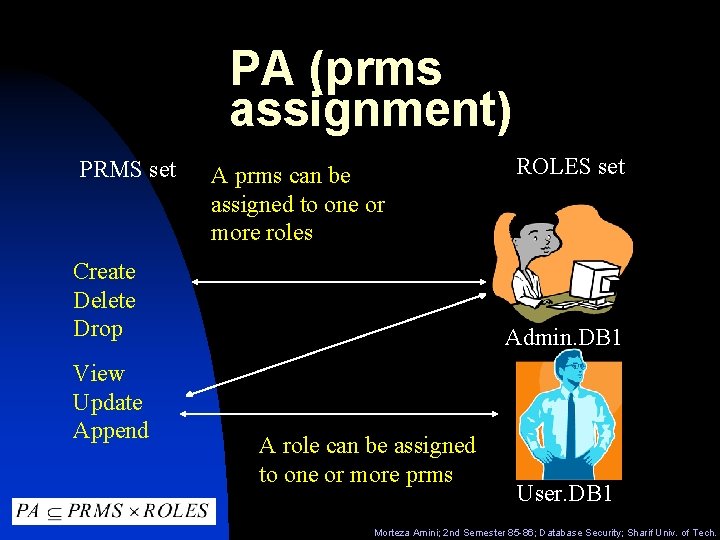
PA (prms assignment) PRMS set A prms can be assigned to one or more roles Create Delete Drop View Update Append ROLES set Admin. DB 1 A role can be assigned to one or more prms User. DB 1 Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
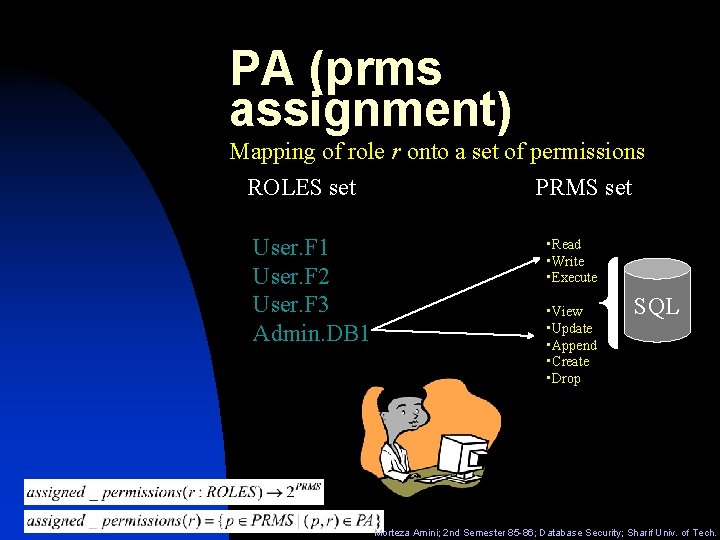
PA (prms assignment) Mapping of role r onto a set of permissions ROLES set PRMS set User. F 1 User. F 2 User. F 3 Admin. DB 1 • Read • Write • Execute • View • Update • Append • Create • Drop SQL Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.

SESSIONS The set of sessions that each user invokes. USER SESSION t es gu FIN 1. report 1 es in k vo admin user SQL DB 1. table 1 APP 1. desktop Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
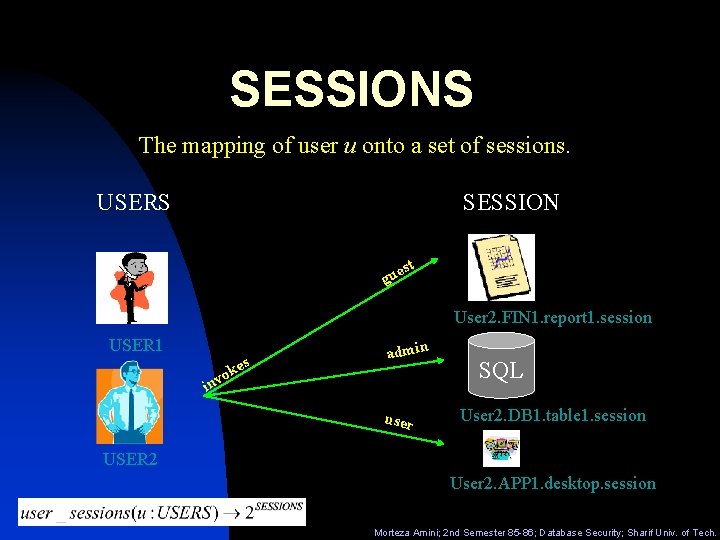
SESSIONS The mapping of user u onto a set of sessions. USERS SESSION t es gu User 2. FIN 1. report 1. session USER 1 es k vo in admin user SQL User 2. DB 1. table 1. session USER 2 User 2. APP 1. desktop. session Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
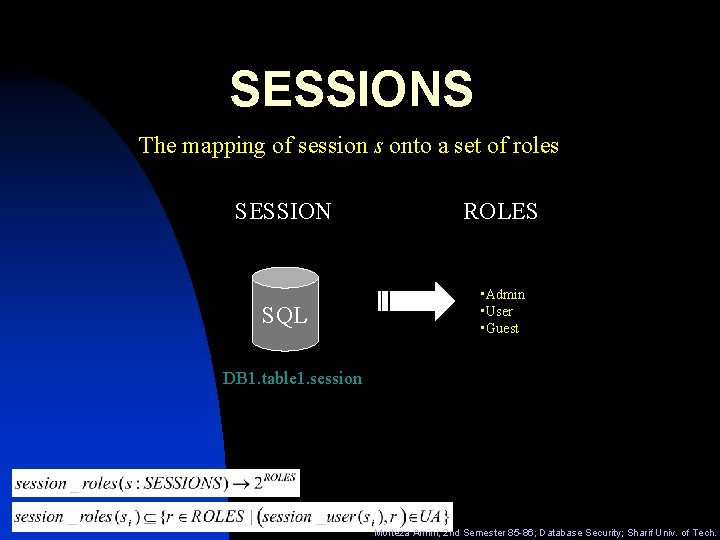
SESSIONS The mapping of session s onto a set of roles SESSION ROLES SQL • Admin • User • Guest DB 1. table 1. session Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
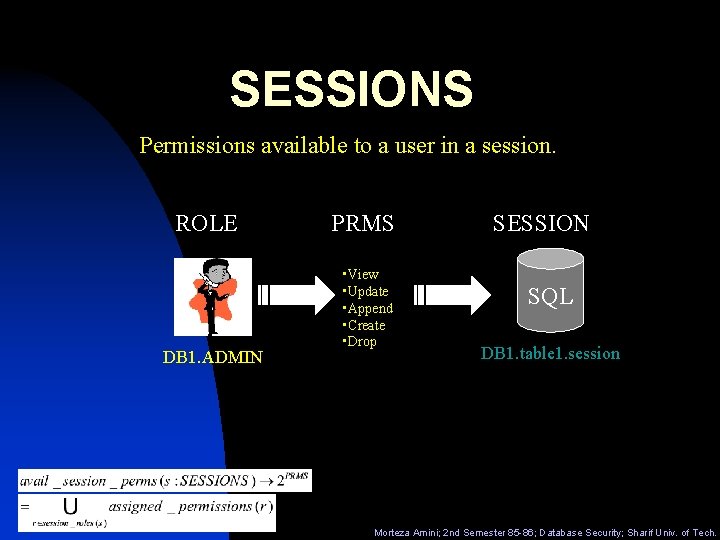
SESSIONS Permissions available to a user in a session. ROLE DB 1. ADMIN PRMS • View • Update • Append • Create • Drop SESSION SQL DB 1. table 1. session Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
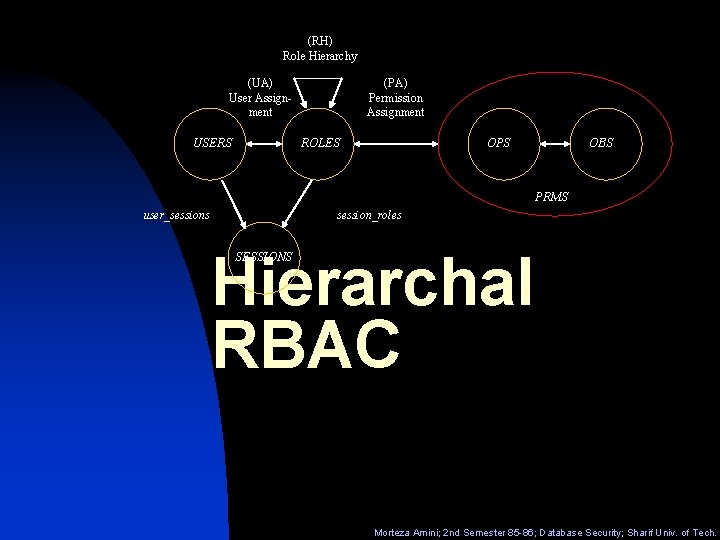
(RH) Role Hierarchy (UA) User Assignment USERS (PA) Permission Assignment ROLES OPS OBS PRMS user_sessions session_roles Hierarchal RBAC SESSIONS Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
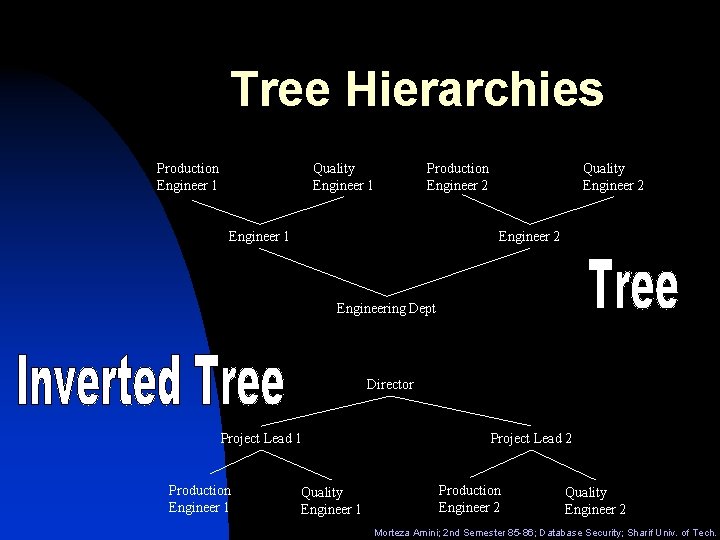
Tree Hierarchies Production Engineer 1 Quality Engineer 1 Production Engineer 2 Engineer 1 Quality Engineer 2 Engineering Dept Director Project Lead 1 Production Engineer 1 Quality Engineer 1 Project Lead 2 Production Engineer 2 Quality Engineer 2 Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
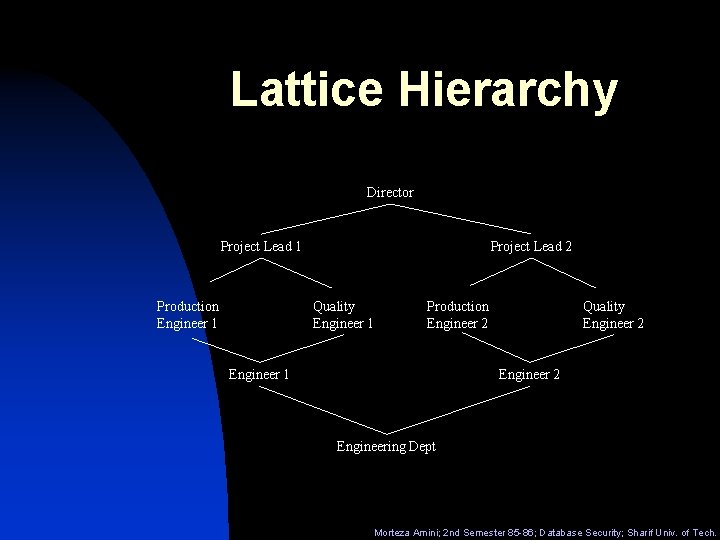
Lattice Hierarchy Director Project Lead 1 Production Engineer 1 Project Lead 2 Quality Engineer 1 Production Engineer 2 Engineer 1 Quality Engineer 2 Engineering Dept Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
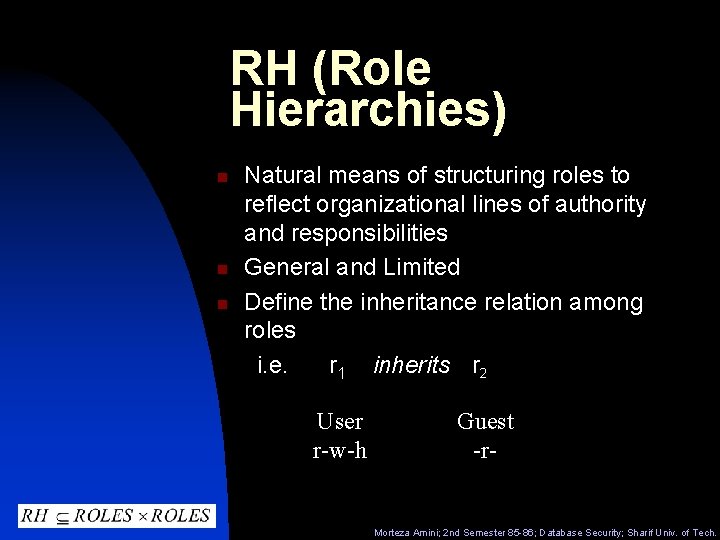
RH (Role Hierarchies) n n n Natural means of structuring roles to reflect organizational lines of authority and responsibilities General and Limited Define the inheritance relation among roles i. e. r 1 inherits r 2 User r-w-h Guest -r- Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
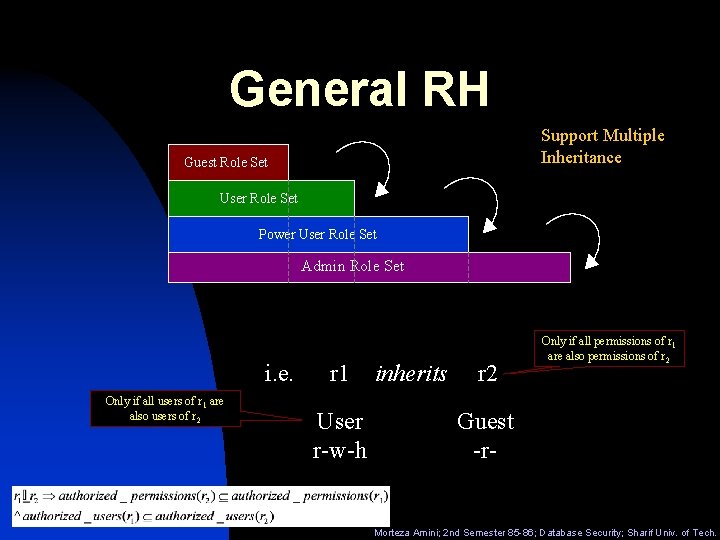
General RH Support Multiple Inheritance Guest Role Set User Role Set Power User Role Set Admin Role Set i. e. Only if all users of r 1 are also users of r 2 r 1 User r-w-h inherits r 2 Only if all permissions of r 1 are also permissions of r 2 Guest -r- Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
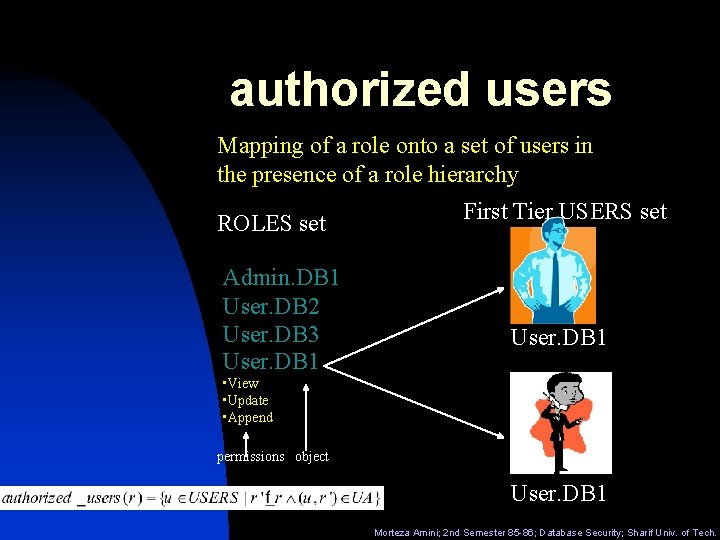
authorized users Mapping of a role onto a set of users in the presence of a role hierarchy ROLES set Admin. DB 1 User. DB 2 User. DB 3 User. DB 1 First Tier USERS set User. DB 1 • View • Update • Append permissions object User. DB 1 Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
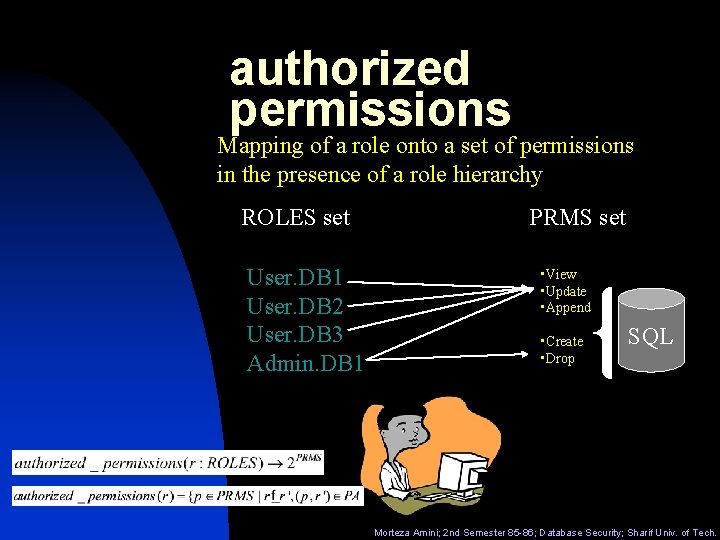
authorized permissions Mapping of a role onto a set of permissions in the presence of a role hierarchy ROLES set User. DB 1 User. DB 2 User. DB 3 Admin. DB 1 PRMS set • View • Update • Append • Create • Drop SQL Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
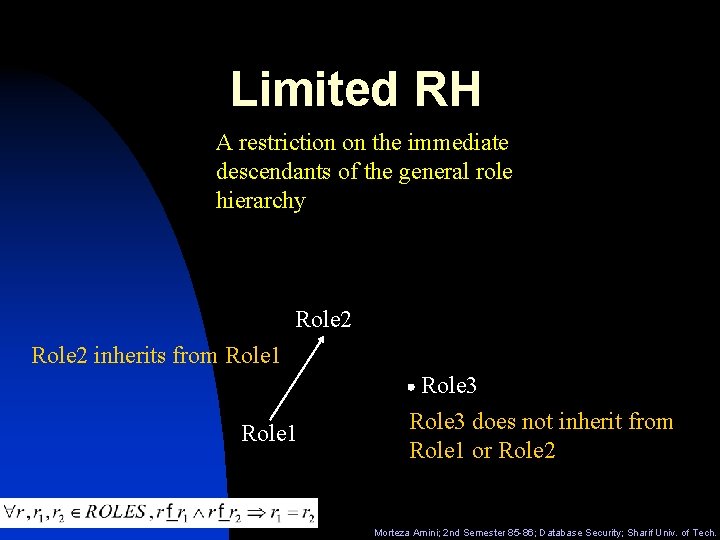
Limited RH A restriction on the immediate descendants of the general role hierarchy Role 2 inherits from Role 1 Role 3 does not inherit from Role 1 or Role 2 Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
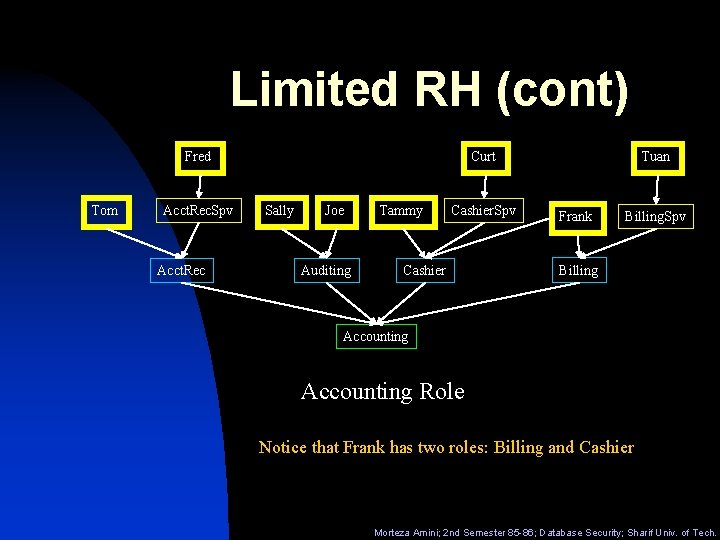
Limited RH (cont) Fred Tom Acct. Rec. Spv Acct. Rec Curt Sally Joe Auditing Tammy Cashier. Spv Cashier Tuan Frank Billing. Spv Billing Accounting Role Notice that Frank has two roles: Billing and Cashier Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.

(RH) Role Hierarchy SSD (UA) User Assignment USERS (PA) Permission Assignment ROLES OPS OBS PRMS user_sessions session_roles Constrained RBAC SESSIONS DSD Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.

Separation of Duties n n n Enforces conflict of interest policies employed to prevent users from exceeding a reasonable level of authority for their position. Ensures that failures of omission or commission within an organization can be caused only as a result of collusion among individuals. Two Types: u u Static Separation of Duties (SSD) Dynamic Separation of Duties (DSD) Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
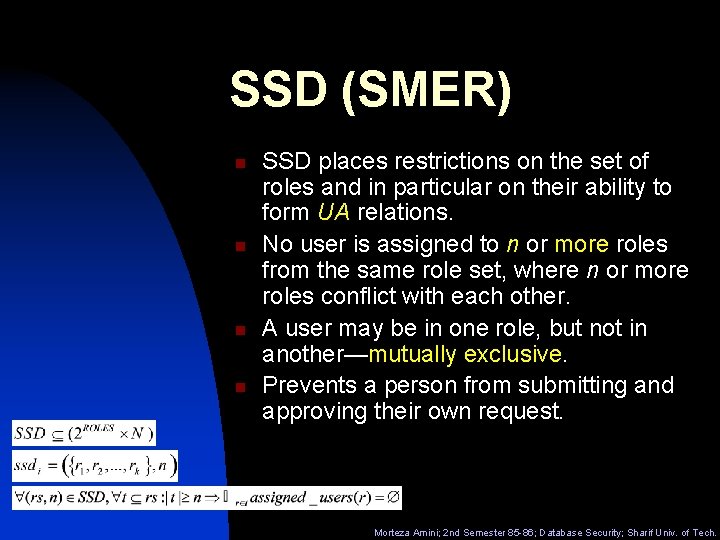
SSD (SMER) n n SSD places restrictions on the set of roles and in particular on their ability to form UA relations. No user is assigned to n or more roles from the same role set, where n or more roles conflict with each other. A user may be in one role, but not in another—mutually exclusive. Prevents a person from submitting and approving their own request. Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
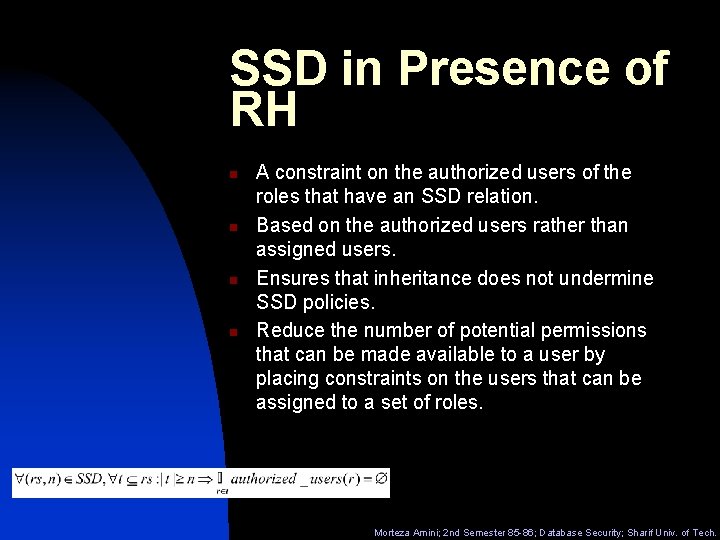
SSD in Presence of RH n n A constraint on the authorized users of the roles that have an SSD relation. Based on the authorized users rather than assigned users. Ensures that inheritance does not undermine SSD policies. Reduce the number of potential permissions that can be made available to a user by placing constraints on the users that can be assigned to a set of roles. Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
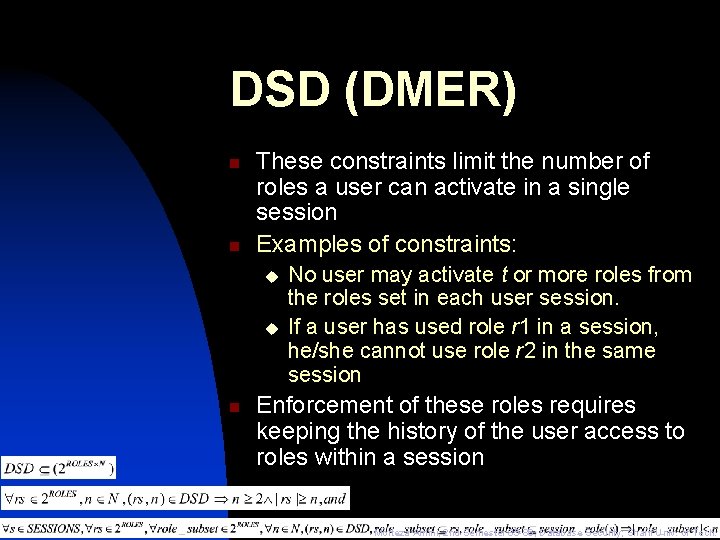
DSD (DMER) n n These constraints limit the number of roles a user can activate in a single session Examples of constraints: u u n No user may activate t or more roles from the roles set in each user session. If a user has used role r 1 in a session, he/she cannot use role r 2 in the same session Enforcement of these roles requires keeping the history of the user access to roles within a session Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
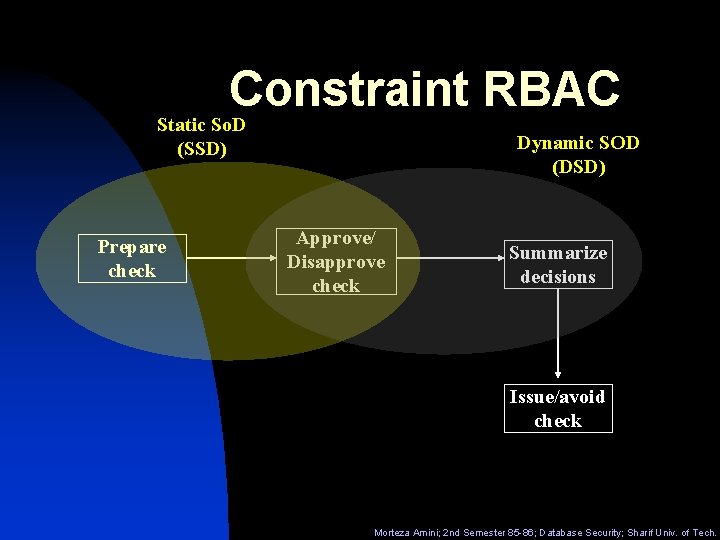
Constraint RBAC Static So. D (SSD) Prepare check Dynamic SOD (DSD) Approve/ Disapprove check Summarize decisions Issue/avoid check Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
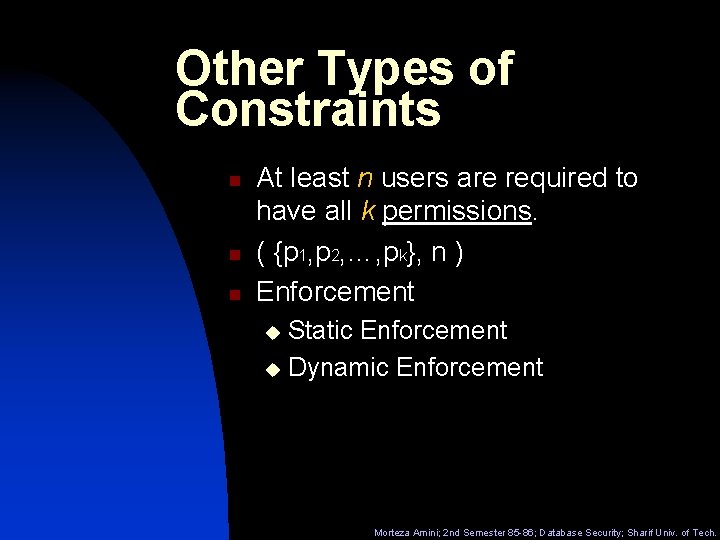
Other Types of Constraints n n n At least n users are required to have all k permissions. ( {p 1, p 2, …, pk}, n ) Enforcement Static Enforcement u Dynamic Enforcement u Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.

So. D Example n Purchase Process 1) Order goods and record details of order 2) Receive invoice and check against order 3) Receive goods and check against invoice 4) Authorize payment against invoice n A set of So. D requirements: u u ssd: No user performs (1) and (3). At least 3 users to perform all 4 steps Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.

QUESTIONS…COMMENTS? ? Morteza Amini; 2 nd Semester 85 -86; Database Security; Sharif Univ. of Tech.
- Slides: 47