Role Based Access Control Models Presented By Ankit

Role Based Access Control Models Presented By Ankit Shah 2 nd Year Master’s Student
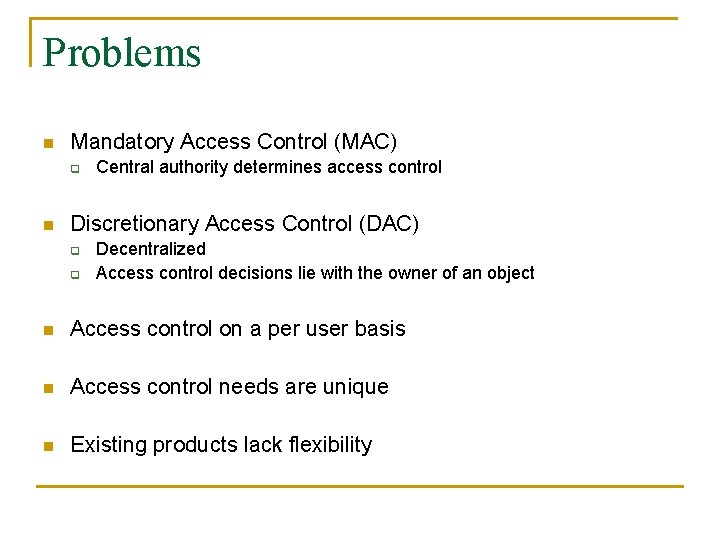
Problems n Mandatory Access Control (MAC) q n Central authority determines access control Discretionary Access Control (DAC) q q Decentralized Access control decisions lie with the owner of an object n Access control on a per user basis n Access control needs are unique n Existing products lack flexibility

Solution n Role Based Access Control q Permission associated with roles and users assigned to appropriate roles n Motivation q Organization style ü ü ü Competency Authority and responsibility Duty assignments - Security administration and review - Simple role-permission relationship - Ability to meet the changing needs of an organization
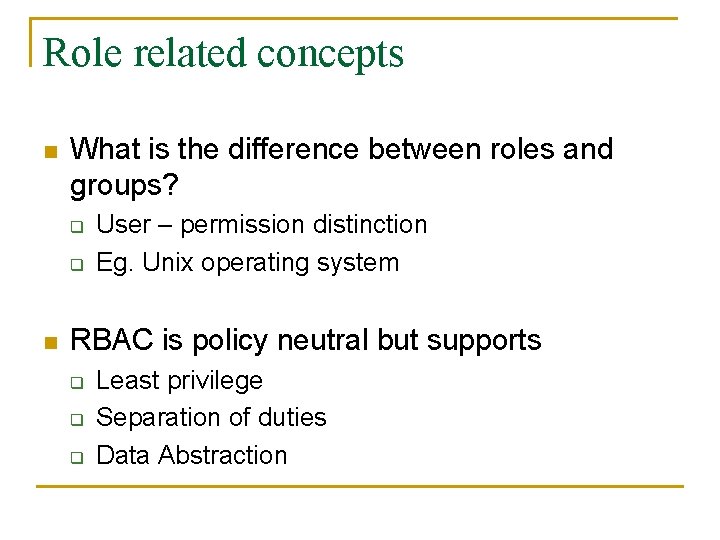
Role related concepts n What is the difference between roles and groups? q q n User – permission distinction Eg. Unix operating system RBAC is policy neutral but supports q q q Least privilege Separation of duties Data Abstraction
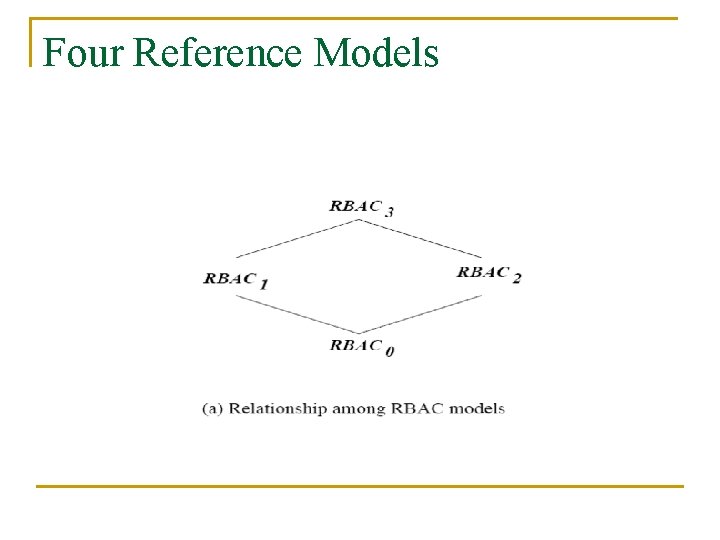
Four Reference Models
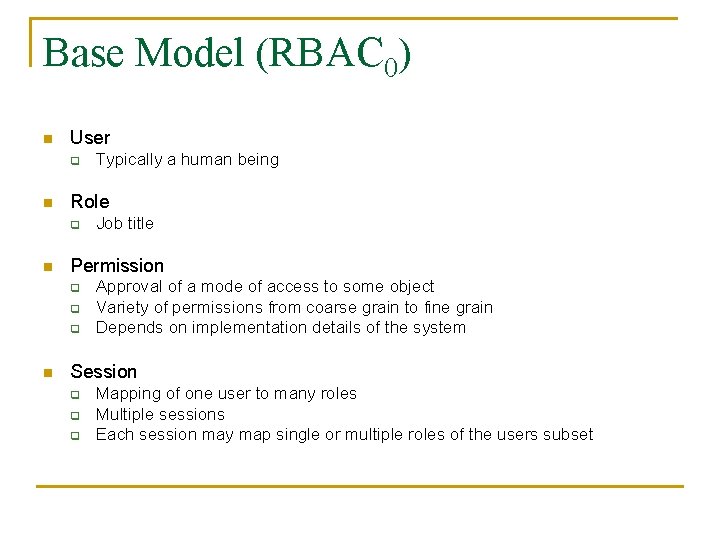
Base Model (RBAC 0) n User q n Role q n Job title Permission q q q n Typically a human being Approval of a mode of access to some object Variety of permissions from coarse grain to fine grain Depends on implementation details of the system Session q q q Mapping of one user to many roles Multiple sessions Each session may map single or multiple roles of the users subset
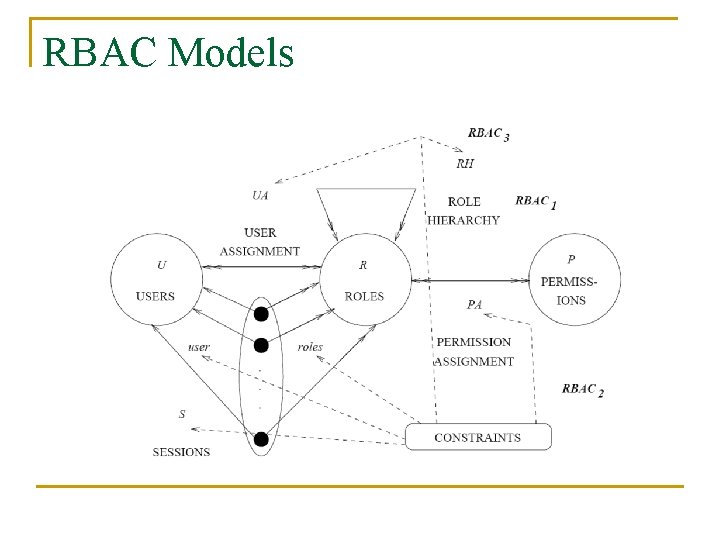
RBAC Models
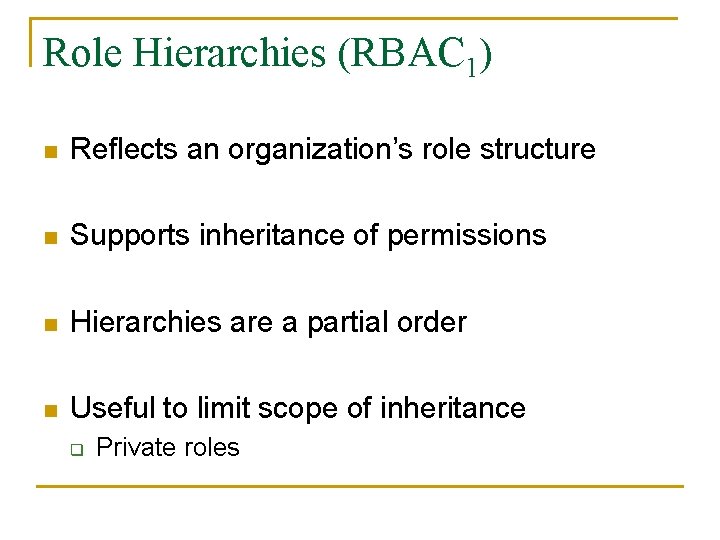
Role Hierarchies (RBAC 1) n Reflects an organization’s role structure n Supports inheritance of permissions n Hierarchies are a partial order n Useful to limit scope of inheritance q Private roles
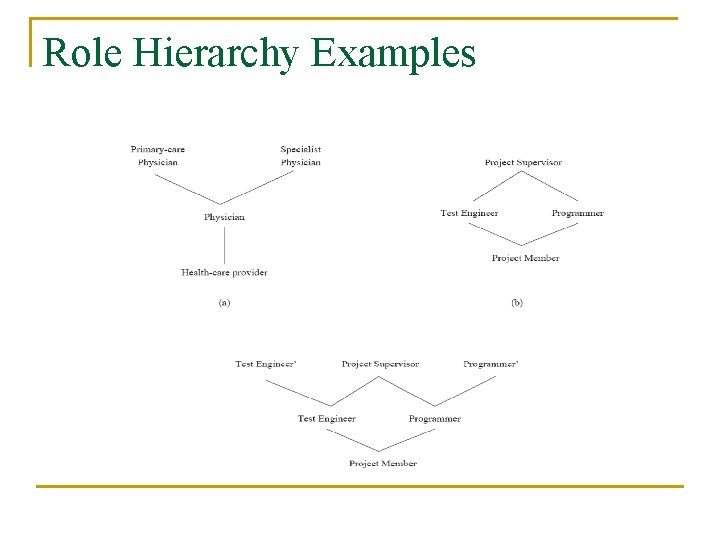
Role Hierarchy Examples
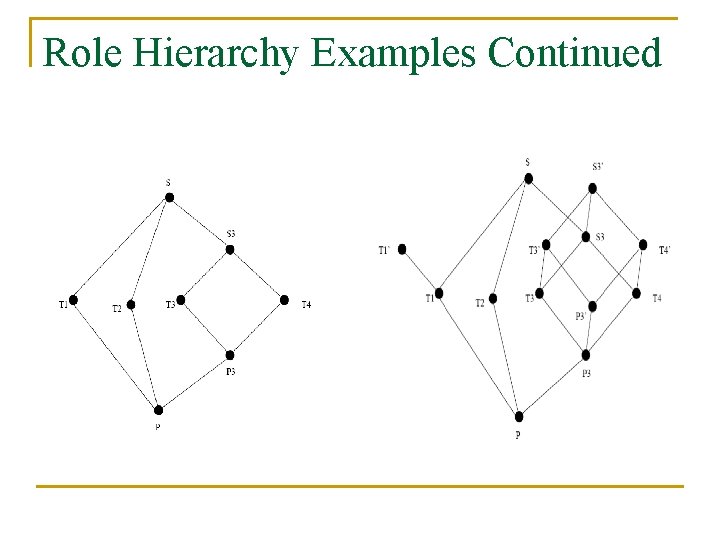
Role Hierarchy Examples Continued
Constraints (RBAC 2) n Argued to be the principal motivation n Is a convenience when RBAC is centralized n When decentralized becomes a mechanism for restriction n Types of Constraints q q q n Effective only if suitable discipline is observed q q n Mutually exclusive roles/ permissions Cardinality constraints Prerequisite roles Mapping one user to more than one u-id Mapping one permission to more than one p-id Role Hierarchies can be considered a constraint
Consolidated Model (RBAC 3) n Combines Constraints and Role Hierarchies n Issues raised q q q Constraints can apply to the role hierarchy itself Violation of mutual exclusion constraint may be acceptable Specify mutual exclusion of private roles without any conflict

Management Model n Till now, we assumed the presence of a single security officer n Normally have a small administrative team to mange RBAC n Propagation of rights
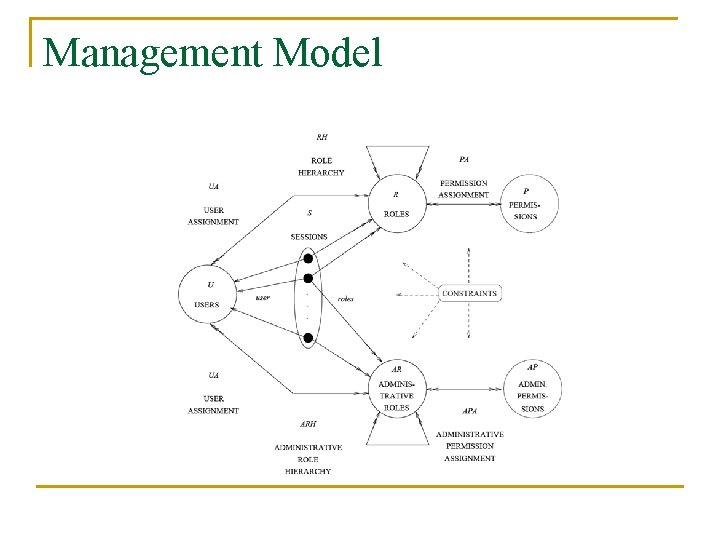
Management Model
Management Model Proposed n Administrative roles and permissions are disjoint from regular roles and permissions n Administrative authority can be viewed as the ability to modify user assignments, permissions, assignment and role hierarchy relations. n Mirror copy of the top half with ARBAC 0 -3 for different levels of sophistication n Issues q How to scope administrative authority in administrative roles q Scope permissions and users of an administrative role
Management Model Continued
Critique n Was published in 1996 and a lot of improvements have been proposed to these models n Issues are raised in the consolidated and management models but no solution is proposed n Lacked a related work section giving us an overview of similar work done and how the proposed model is superior

Questions
- Slides: 18