ROGUE ACCESS POINT LOCALIZATION BY USING SIGNAL STRENGTH

ROGUE ACCESS POINT LOCALIZATION BY USING SIGNAL STRENGTH INDICATOR: A CASE STUDY IN EDUCATIONAL INSTITUTION Mardiana binti Mohamad Noor, Monash University Foundation Year, Sunway College Kuala Lumpur, Bandar Sunway, 47500 Selangor. mardiana@sunway. edu. my Wan Haslina binti Hassan, Communication System and Network (i. Kohza) Research Group, Malaysia. Japan International Institute of Technology (MJIIT), Universiti Teknologi Malaysia, Jalan Semarak, 54100 Kuala Lumpur wanhaslina@ic. utm. my
Blended Learning E- Learning platforms, particularly in Monash University Foundation Year (MUFY) is used to support blended learning Blended learning focuses on students’ participation in the lesson which is achieved through pre-class, inclass and post-class activities.

Bring Your Own Device (BYOD) Policy In order to encourage independent learning, Bring Your Own Device (BYOD) policy is implemented. However, technically, this policy is exposed to several network and cyber security issues and challenges.
Challenges in BYOD having a stable and scalable Wi. Fi network with an appropriate bandwidth provision concern of risks and security issues in Wi. Fi network i)to ensure only the authorized users and devices can access the network ii) presence of unauthenticated AP
Related Works One of the key factors and important elements in implementing BYOD in educational institution is data security [2]. Security threats such as: i) unauthorized access to sensitive data stored on the mobile devices ii) unauthorized access to data stored on the institution’s network iii) attacks from malicious software iv) the ability to impersonate an authorized user.

Related Works IT department in an institution is responsible for maintaining the network and ensure network reliability and security [3]. IT department should ensure secure communication through a Wi. Fi network.
Rogue Access Points (AP) Most of the mobile devices in a network such as smart phones, tablets and laptops may act as APs which can support multiple hotspots users in their own defined parameters. it may impose security breach (packet sniffing) to the users which are connected to the unauthorized access point (AP)
Case Study A case study in Sunway College Kuala Lumpur in mitigating the risks of the presence of unauthorized rogue APs The main objectives: i) ii) To detect the presence of rogue APs To locate and remove the rogue APs
Rogue AP Detection System Conventional: IT personnel to go around a premise with handheld sniffer such as Airwave according to the received signal strength (RSS) Laborious, not cost and resources effective, suffer infrastructural issues, and the signal can be evaded.
Rogue AP Detection System The proposed method: To implement the technique in Indoor Positioning System (IPS). The logarithmic relationship between the received signal strength (RSS) and separation distance which is based on the mechanisms of signal propagation is applied is investigated to find the distance between the rogue AP and a monitoring terminal.
Rogue AP Detection System Novelty: To introduce a factor model for in-building positioning system, hence an automated localization can be realized. The factor model is developed once, during the “offline” phase.

Offline Phase Offline phase includes: i) Data Collection ii) Finding path loss factor iii) Finding correction factor, α
Data Collection The relationship between separation distance between the AP and the monitoring terminal (MT) is observed. Samsung Tablet 3. 0 which is installed with sniffer software, Metageek in. SSIDer was used as the monitoring terminal (MT) to scan the network. The MT is placed in ten classrooms in the same building alternately (which are chosen randomly).
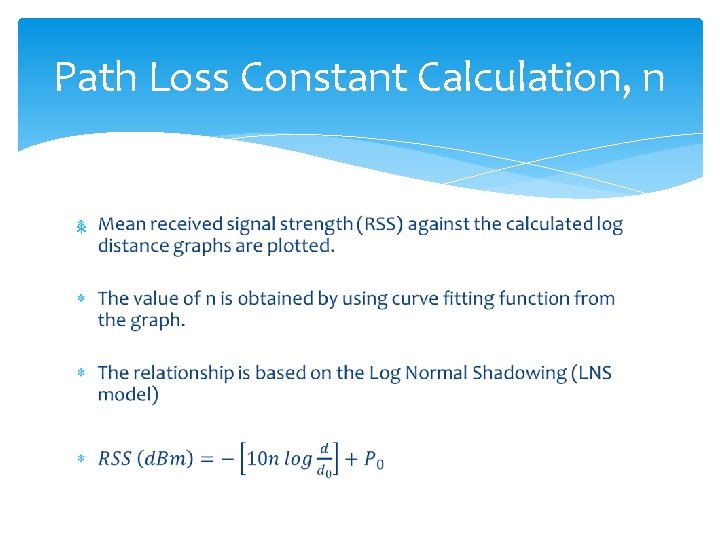
Path Loss Constant Calculation, n

Correction Factor, α
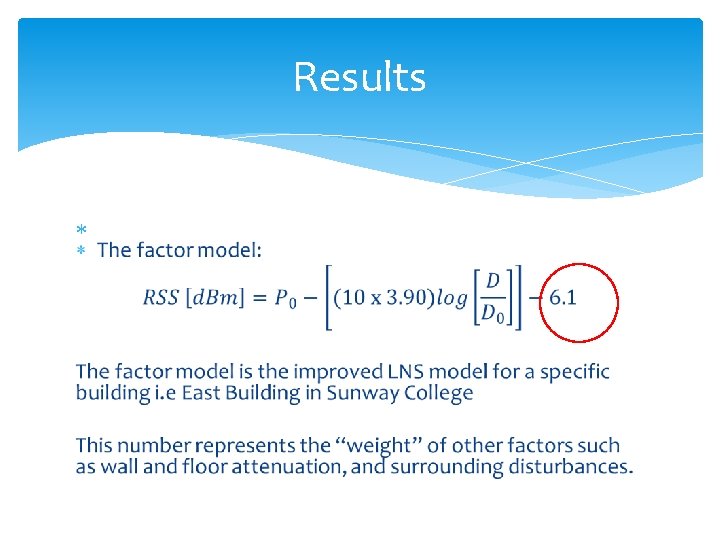
Results
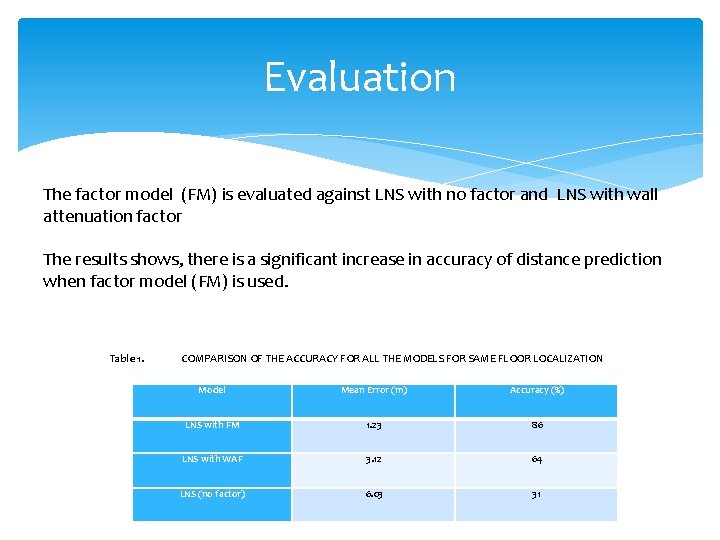
Evaluation The factor model (FM) is evaluated against LNS with no factor and LNS with wall attenuation factor The results shows, there is a significant increase in accuracy of distance prediction when factor model (FM) is used. Table 1. COMPARISON OF THE ACCURACY FOR ALL THE MODELS FOR SAME FLOOR LOCALIZATION Model Mean Error (m) Accuracy (%) LNS with FM 1. 23 86 LNS with WAF 3. 12 64 LNS (no factor) 6. 03 31
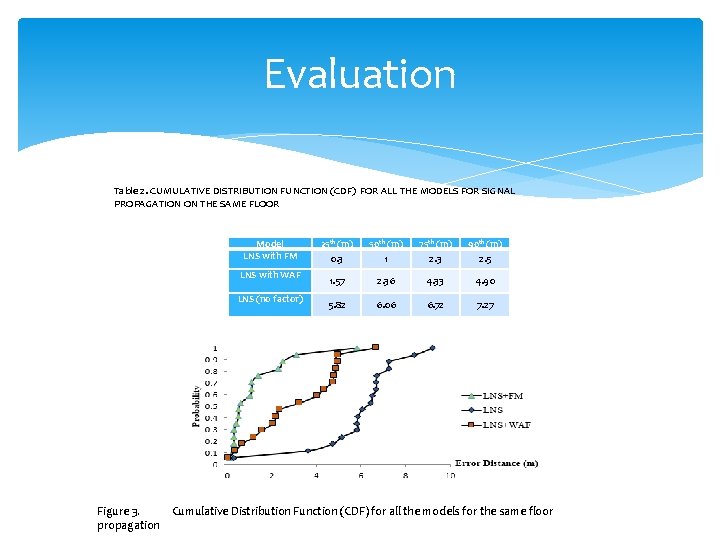
Evaluation Table 2. CUMULATIVE DISTRIBUTION FUNCTION (CDF) FOR ALL THE MODELS FOR SIGNAL PROPAGATION ON THE SAME FLOOR Model LNS with FM LNS with WAF LNS (no factor) Figure 3. propagation 25 th (m) 50 th (m) 75 th (m) 90 th (m) 0. 3 1 2. 3 2. 5 1. 57 2. 36 4. 33 4. 90 5. 82 6. 06 6. 72 7. 27 Cumulative Distribution Function (CDF) for all the models for the same floor
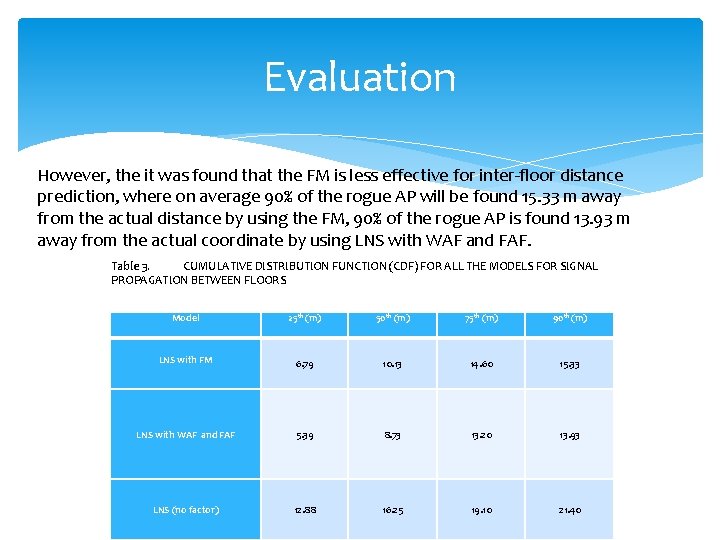
Evaluation However, the it was found that the FM is less effective for inter-floor distance prediction, where on average 90% of the rogue AP will be found 15. 33 m away from the actual distance by using the FM, 90% of the rogue AP is found 13. 93 m away from the actual coordinate by using LNS with WAF and FAF. Table 3. CUMULATIVE DISTRIBUTION FUNCTION (CDF) FOR ALL THE MODELS FOR SIGNAL PROPAGATION BETWEEN FLOORS Model 25 th (m) 50 th (m) 75 th (m) 90 th (m) LNS with FM 6. 79 10. 13 14. 60 15. 33 LNS with WAF and FAF 5. 39 8. 73 13. 20 13. 93 LNS (no factor) 12. 88 16. 25 19. 10 21. 40
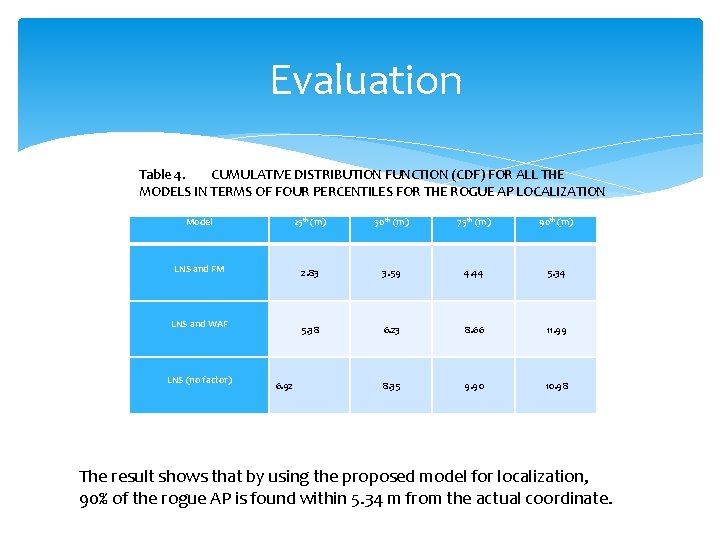
Evaluation Table 4. CUMULATIVE DISTRIBUTION FUNCTION (CDF) FOR ALL THE MODELS IN TERMS OF FOUR PERCENTILES FOR THE ROGUE AP LOCALIZATION Model 25 th (m) 50 th (m) 75 th (m) 90 th (m) LNS and FM 2. 83 3. 59 4. 44 5. 38 6. 23 8. 66 11. 99 8. 35 9. 90 10. 98 LNS and WAF LNS (no factor) 6. 92 The result shows that by using the proposed model for localization, 90% of the rogue AP is found within 5. 34 m from the actual coordinate.

Conclusion An alternative method is proposed which is to detect and locate the rogue AP by using the properties of signal strengths which are transmitted from the rogue AP itself, when there is no information regarding the rogue AP is known. LNS model is proposed in this research for distance prediction. Hence, a factor is introduced to the existing LNS model and the factor is found empirically from series of experiments which were conducted in East Building Sunway College. The improved LNS with the correction factor is called factor model (FM).

Conclusion The accuracy of FM in the distance prediction is improved up to 86 percent as compared to the localization by using the LNS without the suggested factor and there is 90 percent of the chances that the rogue AP is found within 5. 34 m from its actual position.
![References REFERENCES [1] Attewell J. (2017), Bring Your Own Device For Schools. European Schoolnet References REFERENCES [1] Attewell J. (2017), Bring Your Own Device For Schools. European Schoolnet](http://slidetodoc.com/presentation_image_h2/5e3700be274276e9bb7125a2b98dccd3/image-23.jpg)
References REFERENCES [1] Attewell J. (2017), Bring Your Own Device For Schools. European Schoolnet 2017. [2] Kock D. R and Futcher A. L (2016), Mobile Devices Usage in Educational Institution in South Africa. Information Security for South Africa ISSA 2016, 27 -34 [3] Macareg T. (2013). Bring Your Own Device (BYOD): Issues and Implementation In Local Colleges and Universities in the Philippines. Retrieved August 21, 2017, from https: //researchgate. net/publication/313649980 [4] Calhoun. (2009). Control and Provisioning of Wireless Access Points (CAPWAP) Protocol Binding for IEEE 802. 11. Retrieved March 5, 2015, from https: //tools. ietf. org/html/rfc 5416 [5] Aruba Network (2013). Air. Wave Visual. RF Location and Mapping Improving Operations Efficiency Throughout the Wireless Network Lifecycle Visual. RF Overview Making the Airwaves Visible. CA: Aruba Network Inc. [6] Beyah R. , Kangude S. , Strickland B. and Copeland J. (2004). Rogue Access Point Detection Using Temporal Traffic Characteristics. IEEE Global Telecommunications Conference. 29 Nov - 3 Dec. Dallas: IEEE, 2271– 2275. [7] Seidel, S. Y. and Rappaport, T. S. (1992). 914 MHz Path Loss Prediction Models for Indoor Wireless Communications in Multifloored Buildings. IEEE Transaction on Antenna and Propagation. 40(2), 207 -215. [8] Ringle, Christian M. , Wende, Sven, Will, A. (2005). Smart PLS 2. 0 M 3. Retrieved June 2015 from http: //www. smartpls. com.
- Slides: 23