Risk Vulnerability Assessment Penetration Test Approach VA PT

Risk (Vulnerability) Assessment & Penetration Test Approach VA PT Approach Confidential 1

Content About Docutek The real Difference — We Take Your Security Personally Our mission is to deliver the most comprehensive, accurate, and thorough information security assessments in the industry. We focus exclusively on what we do best — penetration testing and IT security and vulnerability assessments. VA PT Approach Confidential 2
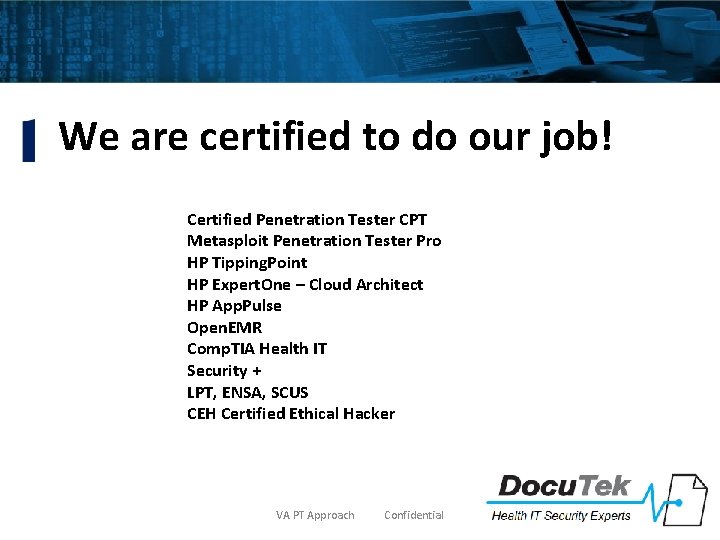
We are certified to do our job! Certified Penetration Tester CPT Metasploit Penetration Tester Pro HP Tipping. Point HP Expert. One – Cloud Architect HP App. Pulse Open. EMR Comp. TIA Health IT Security + LPT, ENSA, SCUS CEH Certified Ethical Hacker VA PT Approach Confidential 3
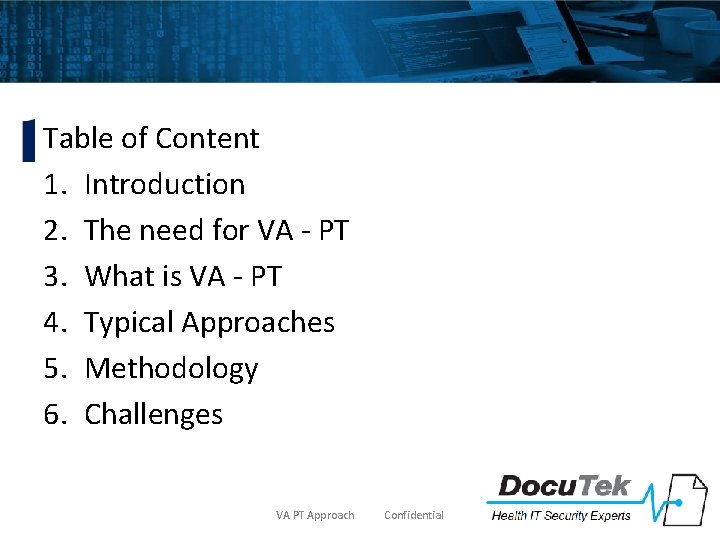
Content Table of Content 1. Introduction 2. The need for VA - PT 3. What is VA - PT 4. Typical Approaches 5. Methodology 6. Challenges VA PT Approach Confidential 4

Content Introduction Intr n o tio c u d VA PT Approach Confidential 5
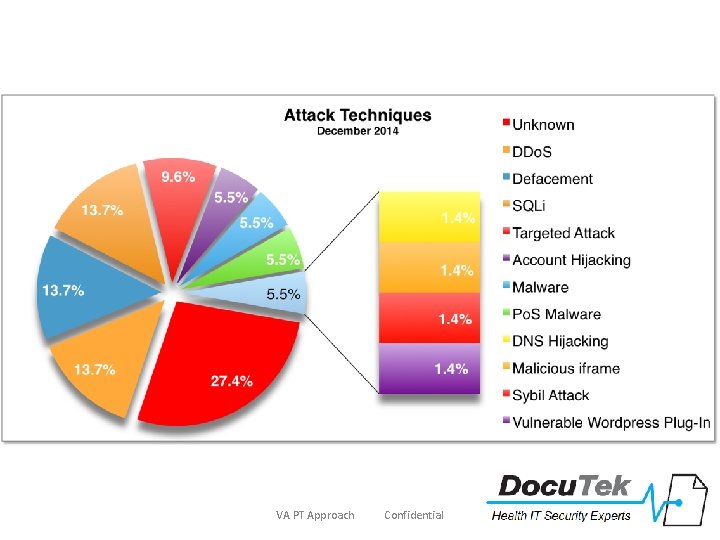
VA PT Approach Confidential 6
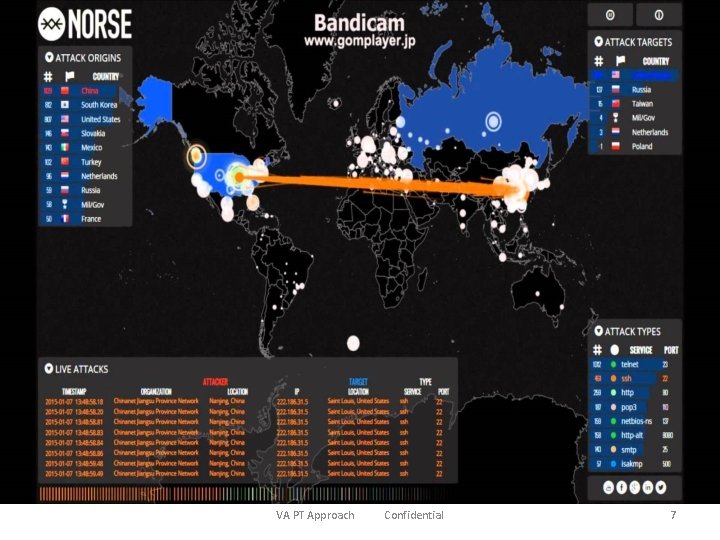
VA PT Approach Confidential 7
VA PT Approach Confidential 8

Before you start • • • Business Associate – Compliance BA Risk Analysis – Always Insurance – Just in case (Cyber. Edge AIG) Contract – Peace of mind Alliances – Do not go in alone VA PT Approach Confidential 9

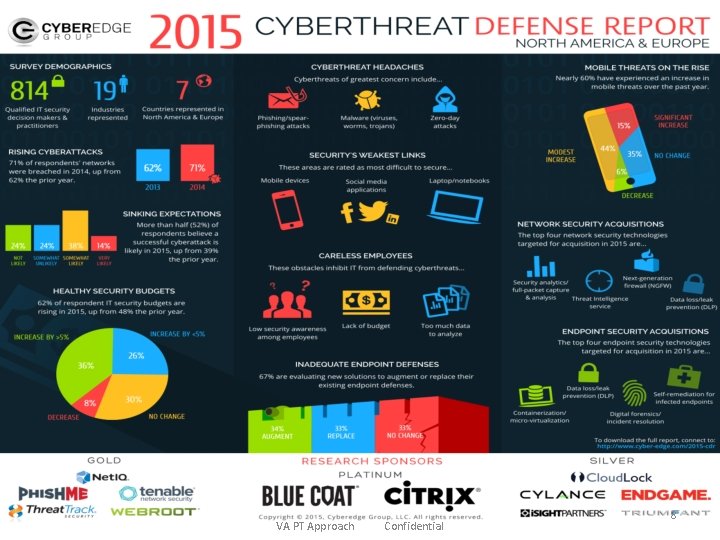
Need for VA – PT Highest Security Risk • To improve information security awareness • To assess risk • To mitigate risk immediately • To reinforce the information security process • To assist in decision making processes • To Validate that current security mechanisms are working • Compliance to various security standards and regulations such as ISO 27001, IT ACT 2000, SOX, HIPAA, PCI, etc VA PT Approach Confidential 10

Hospitals and Medical Devices Found Prone To Hacking Due To Network Security Flaw Thousands of healthcare organizations around the world, along with the medical devices and equipment that connect to their systems, are leaving themselves open to cyber attacks because of a crucial mis-configuration of a network security protocol. VA PT Approach Confidential 11
What is VA – PT ? • A form of Stress testing, which exposes weaknesses or flaws in a computer system • Art of finding an Open door • A valued Assurance Assessment tool • PT can be used to find Flaws in • – Specifications, Architecture, Implementation, Software, Hardware, And many more……………… Vulnerability assessment is the process of identifying and quantifying vulnerabilities in a system. A vulnerability assessment is what most companies generally do, as the systems they are testing are live production systems and can’t afford to be disrupted by active exploits which might crash the system. VA PT Approach Confidential 12
Typical Approach • Typical Approach – It is also know as “complete knowledge” testing • WHITEBOX Testing • BLACKBOX Testing VA PT Approach Confidential 13
WHITEBOX Testing It is also known as “complete knowledge” testing Testers are given full information about the target system they are supposed to attack Information TESTING includes: • Technology overviews • Data flow & Network diagrams • Code snippets Benefits: • Reveals more vulnerabilities and may be faster • Compared to replicate an attack from a criminal hacker that knows the company infrastructure very well • This hacker may be an employee of the company itself, doing an internal attack VA PT Approach Confidential 14
BLACKBOX Testing • The tester simulates an inside Employee. The tester is given an account on the internal network and standard access to the network. This test assesses internal threats from employees within the Company. • The relative merits of all these approaches are debatable. • In most cases it is preferable to assume a worst-case scenario and provide the testers with as much information as they require, assuming that any determined attacker would already have acquired this. VA PT Approach Confidential 15
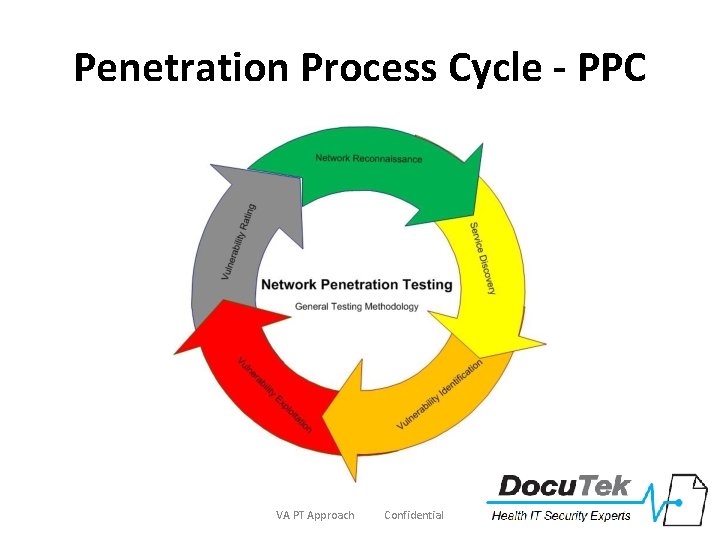
Penetration Process Cycle - PPC VA PT Approach Confidential 16

Methodology 1. 2. 3. 4. 5. 6. 7. Scope / Goal Definition Information Gathering Information Analysis & Planning Vulnerability Detection Attack & Penetration / Privilege Escalation Result Analysis & Reporting Clean Up VA PT Approach Confidential 17
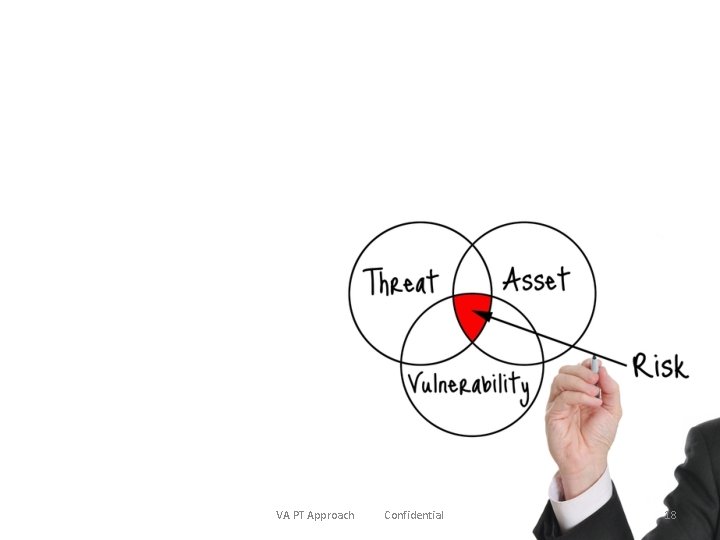
VA PT Approach Confidential 18

1. Scope/Goal Definition Which attacker profile the tester will use • Hacker with no knowledge about the target • Hacker with knowledge about the target • Internet user with access Which System or network the test will be conducted Duration of Test VA PT Approach Confidential 19

VA PT Approach Confidential 20

2. Information Gathering Information about the Target • Who is: ARIN ; RIPE ; APNIC • Google: General Information; Financial, Phone Book, Google Hacking Databases; Web Searching • DNS Retrieval, SOA Record, MX Records, NS Records, A Records etc. • Tools / Websites: Cheops-ng, Sam Spade, www. dnstuff. com • Social Engineering • Dumpster Diving • Web Site Copy VA PT Approach Confidential 21

VA PT Approach Confidential 22
3. Vulnerability Detection Manual Detection • Manually probe the target host from common misconfiguration or flaws because a vulnerability scanner can fail to identify certain vulnerabilities. Ex: Database configuration etc…. – Open TCP Ports – Closed TCP Ports – Open UDP Ports – Closed UDP Ports – Service Probing VA PT Approach Confidential 23

VA PT Approach Confidential 24
4. Information Analysis & Planning – Collating the information gathered in previous stages. – Preparation of High level attack planning. • Overall Approach • Target identification VA PT Approach Confidential 25
VA PT Approach Confidential 26
5. Penetration & Privilege Escalation • HAS Two Sub Stages • Attack & Penetration – Known / available exploit selection – Tester acquires publicly available s/w for exploiting. – Exploit customization – Customize exploits s/w program to work as desired. – Exploit development – Develop own exploit if no exploit program available – Exploit testing – Exploit must be tested before formal Test to avoid damage. – Attack – Use of exploit to gain unauthorized access to target. VA PT Approach Confidential 27

VA PT Approach Confidential 28
Penetration & Privilege Escalation • Privilege Escalation – What can be done with acquired access / privileges • Alter • Damage • What not VA PT Approach Confidential 29

VA PT Approach Confidential 30

6. Result Analysis & Reporting • Organize Data/related results for Management Reporting • Consolidation of Information gathered • Analysis and Extraction of General conclusions • Recommendations VA PT Approach Confidential 31

VA PT Approach Confidential 32

7. Cleanup – Cleaning of all that has been done during the testing • Any System alterations • Exploits VA PT Approach Confidential 33

Challenges • Quality & Experience of Pen Testers • Quality & Effectiveness of Tools • Usage of Globally Accepted Methodology such as OSSTMM, OWASP etc • Ensuring all the findings are reported to the Management • Follow stringent program to Fix Vulnerabilities • Conduct Periodic Testing VA PT Approach Confidential 34
DOCUTEK 7000 N Plaza Austin, TX 78753 USA www. docutekservices. com osanchez@docutekservices. com 787. 407. 9074 VA PT Approach Confidential 35
- Slides: 35