Risk Management Risk Categories Strategic Credit Market Liquidity



















- Slides: 21

Risk Management

Risk Categories Strategic Credit Market Liquidity Operational Compliance/legal/regulatory Reputation

Operational Risk The risk of direct of indirect loss resulting from inadequate or failed internal processes, people and systems or from external events. Inadequate Information Systems Breaches in internal controls Fraud Unforeseen catastrophes

Inadequate Information Systems General Risks Physical access to the hardware Logical access to the IT systems Capacity management - prevents bottlenecks in all relevant systems component Emergency management Insufficient backup recovery measures-mitigate the consequences of system failures

Inadequate Information Systems 1. 2. 3. 4. 5. Application-oriented risks Data not correctly recorded due to system errors Data not correctly stored during period of validity Relevant data are not correctly included Calculations which are basis for information are not correct Due to systems failures the information processed by the application is not available in time.

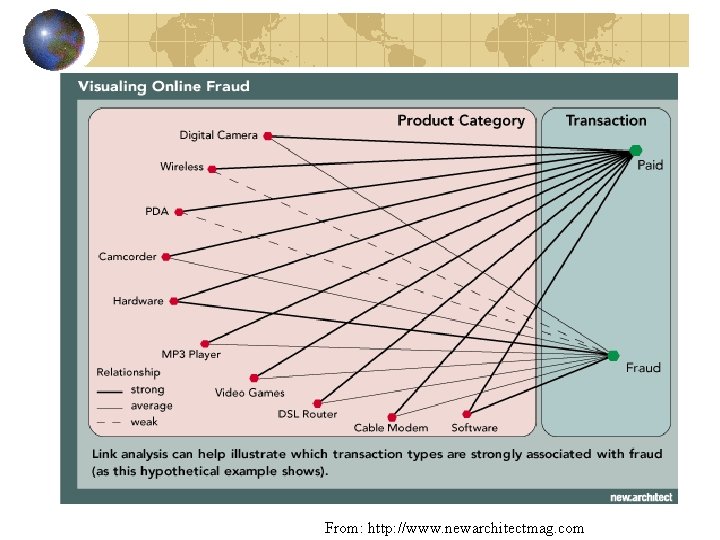
Fraud Management Categories 1. 2. 3. 4. 5. Check Fraud Debit card Fraud Electronic Payment Fraud ATM Deposit Fraud Account Take-over/Identity Theft

From: http: //www. newarchitectmag. com

Fraud Management Systems JAM (Java Agents for Meta Learning)

Obstacles in detecting Fraud Financial or Human resource shortage High volumes of claims, transactions or other information to be analyzed Cookie-cutter detection methods that miss new or unusual instances Lack of in-house expertise or training

Risk Management in EBanking

Technology Developments Advances in communications provide networked global access to information and delivery of products/services Internet has reached critical mass (60% of U. S. households) Some banks have 25 percent of customers banking online Increased competition from other industries and abroad Greater reliance on third party providers Advances in technology make the component functions of banking more easily divisible www. occ. treas. gov

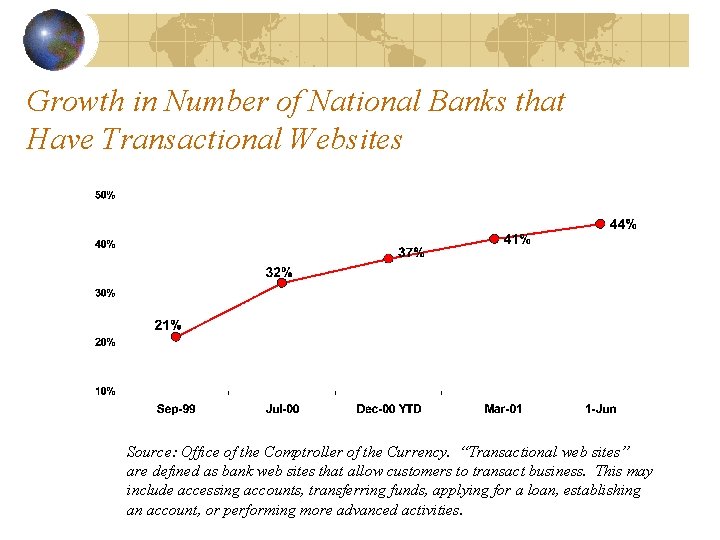
Growth in Number of National Banks that Have Transactional Websites Source: Office of the Comptroller of the Currency. “Transactional web sites” are defined as bank web sites that allow customers to transact business. This may include accessing accounts, transferring funds, applying for a loan, establishing an account, or performing more advanced activities.

Technology-based Banking Products & Services Balance inquiry Transaction information Funds transfer Cash Management Bill payment Bill presentment Loan applications Stored Value-application: Stored-value cards are a substitute for cash, gift certificates and check payments. Monetary value is added to the stored-value account before the card is used, with the value either being funded by the cardholder directly, or by the card program operator in commercial applications www. occ. treas. gov

Technology-based Banking Products & Services Aggregation Electronic Finder Automated clearinghouse (ACH) Transactions Internet Payments Wireless Banking Certification Authority Data Storage-Digital Data Storage (DDS) is a format for storing and backing up computer data on tape that evolved from the Digital Audio Tape (DAT) technology.

Key Technology Risks Vendor Risk Issues Security, Data Integrity, and Confidentiality Authentication, Identity Verification, and Authorization Strategic and Business Risks Business Continuity Planning Permissibility, Compliance, Legal Issues, and Computer Crimes Cross Border and International Banking www. occ. treas. gov

Security and Privacy Increases in security events and vulnerabilities According to 2001 FBI/CSI survey, 70% reported that the Internet is the point of cyber attacks, up from 59% in 2000 Gramm-Leach-Bliley Act of 1999 requires banks to establish administrative, technical & physical safeguards to protect the privacy of customers’ nonpublic customer records and information www. occ. treas. gov

Key Elements of Security Program Reviewing physical and logical security: Review intrusion detection and response capabilities to ensure that intrusions will be detected and controlled Seek necessary expertise and training, as needed, to protect physical locations and networks from unauthorized access Maintain knowledge of current threats facing the bank and the vulnerabilities to systems Assess firewalls and intrusion detection programs at both primary and back-up sites to make sure they are maintained at current industry best practice levels www. occ. treas. gov

Key Elements of Security Program Reviewing physical and logical security (cont’d): Verify the identity of new employees, contractors, or third parties accessing your systems or facilities. If warranted, perform background checks. Evaluate whether physical access to all facilities is adequate. Work with service provider(s) and other relevant customers to ensure effective logical and physical security controls. www. occ. treas. gov

Authentication Reliable customer authentication is imperative for Ebanking Effective authentication can help banks reduce fraud, reputation risk, disclosure of customer information, and promote the legal enforceability of their electronic agreements Methods to authenticate customers: Passwords & PINS Digital certificates & PKI (Public Key Infrastructure) Physical devices such as tokens Biometric identifiers www. occ. treas. gov

OCC Technology Risks Supervision Program The Office of the Comptroller of the Currency charters, regulates, and supervises national banks to ensure a safe, sound, and competitive banking system that supports the citizens, communities, and economy of the United States. Guidance -- Focus on risk analysis, measurement, controls, and monitoring Risk-based examinations of banks and third party service providers (as authorized by the Bank Service Company Act of 1962) Training and Technology Integration Project External outreach and co-ordination Licensing process for Internet-primary banks and novel activities www. occ. treas. gov

References www. occ. treas. gov www. newarchitectmag. com http: //www. cs. columbia. edu/~sal/JAM/PROJECT/ Gerrit Jan van den Brink (2002), Operational Risk: The challenge for banks. http: //dinkla. net/fraud/products. html
 Market risk assessment
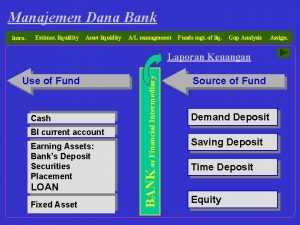
Market risk assessment Alm liquidity
Alm liquidity Liquidity risk definition
Liquidity risk definition Example of liquidity risk
Example of liquidity risk Risk projection
Risk projection Project risk categories
Project risk categories Io model strategic management
Io model strategic management Analysing the 6 strategic options megxit
Analysing the 6 strategic options megxit Stored liquidity management
Stored liquidity management Balanced liquidity management strategy
Balanced liquidity management strategy Liquidity management strategies
Liquidity management strategies European collateral management system
European collateral management system Liquidity and reserve management
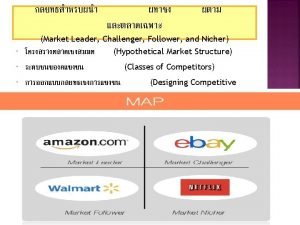
Liquidity and reserve management Market leader follower challenger nicher
Market leader follower challenger nicher Market segmentation and positioning
Market segmentation and positioning Enterprise risk management framework for credit unions
Enterprise risk management framework for credit unions Credit risk management and advisory goldman sachs
Credit risk management and advisory goldman sachs Credit risk types
Credit risk types Elements of financial risk management
Elements of financial risk management Metodo irb
Metodo irb Credit risk management framework
Credit risk management framework This can be avoided by giving credit where credit is due.
This can be avoided by giving credit where credit is due.