RISK MANAGEMENT IN THE APPROACH TO PHYSICAL SECURITY



























- Slides: 29

RISK MANAGEMENT IN THE APPROACH TO PHYSICAL SECURITY PLANNING ED HAMILTON 22 MAY 2000

RISK MANAGEMENT • A systematic process designed IN THE APPROACH TO PHYSICAL SECURITY develop. PLANNING rational and cost to effective physical security program. EDstrategies to protect HAMILTON 22 MAY 2000 critical facility assets.

PURPOSE OF RISK MANAGEMENT • Select countermeasures appropriate to the RISK level of MANAGEMENT risk that management is willing to IN THE APPROACH accept. TO PHYSICAL SECURITY PLANNING ED HAMILTON 22 MAY 2000

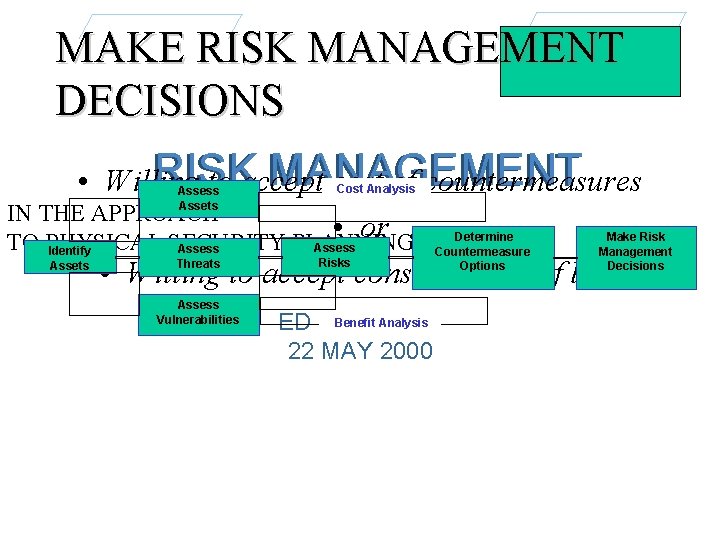
PROCEDURES OF RISK MANAGEMENT • 1) Identify assets to be protected. • 2) Assess assets. RISK MANAGEMENT • 3) Assess threats. IN THE APPROACH • 4) Assess vulnerabilities. TO PHYSICAL SECURITY PLANNING • 5) Assess risks. • 6) Determine countermeasures options and estimate ED costs. HAMILTON • 7) Make risk management 22 MAY 2000 decisions.

IDENTIFY ASSETS • Material Intellectual Property RISK MANAGEMENT • Equipment Reputation IN THE APPROACH TO PHYSICAL SECURITY PLANNING • Facilities Personnel ED HAMILTON • Processes 22 MAY Records 2000

ASSESS ASSETS • What is the impact of loss, damage, compromise, or Activists interruption of. Political operations? • What does the. Drug/Alcohol facility stand to. Impaired IN THE APPROACH Mentally Unstable TO PHYSICALlose? SECURITY PLANNING • What does an. Disgruntled adversary stand to And they can be: gain? Mischief Makers Insiders • What is the impact of loss on ED HAMILTON Outsiders national security? 22 MAY Both (Collusion) • What is the potential impact 2000 on peoples’ lives? • What is the cost of replacement or repair? RISK MANAGEMENT • • Prioritize according to overall impact. Assign weighted scores.

ASSESS THREATS • Who are the adversaries? • Terrorists • Anarchists • Extremists IN THE APPROACH • Fanatics TO PHYSICAL SECURITY PLANNING • Criminals RISK MANAGEMENT Revenge Labor unrest Competition Greed Vandalism Ego Curiosity ED HAMILTON 22 MAY 2000 Opportunity No discernible motive

ASSESS THREATS (CONT. ) • What are their motives or goals? • Assassination • Extortion • Destruction of military assets IN THE APPROACH • Sabotage TO PHYSICAL SECURITY PLANNING • Espionage • Destruction of vital equipment • National harm ED HAMILTON • Propaganda 22 MAY 2000 • Theft • Perceived right RISK MANAGEMENT

ASSESS THREATS (CONT. ) • What are their characteristics? • Knowledgeable, skilled, and well equipped. • Use of sophisticated penetration aids and methods. • Highly organized. Stay-behind. IN THE APPROACH • Dedicated. Plant covert devices. TO PHYSICAL SECURITY PLANNING • Alone or in groups. Stealth. • Familiar with security systems and operations. RISK MANAGEMENT Arson. ED HAMILTON Diversionary tactics. 22 MAY 2000 Stand-off surveillance.

ASSESS THREATS (CONT. ) • What are their methods? • Forcible entry. • Covert entry (in collusion with insider). IN THE APPROACH • Authorized entry (insider). TO PHYSICAL SECURITY PLANNING • Extortion of insider. • Unescorted walk-in. • Bypass entry controls. ED HAMILTON MAY 2000 • Technical spoofing or 22 jamming. RISK MANAGEMENT

ASSESS THREATS (CONT. ) • Adversarial Analysis: • Technically feasible to defeat. • Opportunity. IN THE APPROACH • Incentive. TO PHYSICAL SECURITY PLANNING • Specific to each asset. • Assign weighted score to each feasible threat for each asset. ED HAMILTON • Select worst case score for each asset. 22 MAY 2000 RISK MANAGEMENT

ASSESS VULNERABILITIES (CONT. ) ASSESS VULNERABILITIES RISK MANAGEMENT • What weaknesses could be exploited to result in loss, damage, compromise, or disruption? IN THE APPROACH • Determine functional requirements of the physical TO PHYSICAL SECURITY PLANNING security system. • Assess physical, technical, and operational aspects ED HAMILTON of the site. 22 MAY 2000

RISK MANAGEMENT • Physical Aspects • Perimeter barriers • Building construction and layout IN THE APPROACH • Facility layout PLANNING TO PHYSICAL SECURITY • Access roads • Response vehicles and equipment ED HAMILTON 22 MAY 2000

ASSESS VULNERABILITIES (CONT. ) • RISK Technical Aspects MANAGEMENT • Existing physical security systems and equipment IN THE APPROACH • Communications TO PHYSICAL SECURITY • Power and signal. PLANNING distribution infrastructure • Lighting ED HAMILTON 22 MAY 2000

ASSESS VULNERABILITIES (CONT. ) • Operational Aspects • Personnel RISK MANAGEMENT • Concept of operations IN THE APPROACH TO PHYSICAL SECURITY PLANNING ED HAMILTON 22 MAY 2000

ASSESS VULNERABILITIES (CONT. ) • Concept of Operations: • Pre-planned, integrated operation of: RISK MANAGEMENT • Personnel • Procedures IN THE APPROACH • Equipment TO PHYSICAL SECURITY PLANNING • First: • Detain, or • Destroy Delay, Detect, and ED HAMILTON 22 MAY 2000 Determine Then: Deter,

ASSESS VULNERABILITIES (CONT. ) • Location of Facility: • High threat area RISK MANAGEMENT • Nearness of outside human activity • Accessibility of facility IN THE APPROACH • Proximity. SECURITY of other building TO PHYSICAL PLANNING • Nearness of response forces • Vehicle access roads ED HAMILTON 22 MAY 2000

ASSESS VULNERABILITIES (CONT. ) • RISK Measure of Effectiveness of existing security system --MANAGEMENT Timely Detection. IN THE APPROACH • Timely Detection --- Minimum cumulative probability detection while enough time remains to respond TO PHYSICALof. SECURITY PLANNING • • Identify adversary paths to target What deterrents must adversary overcome? How much delay time do they provide? ED HAMILTON What is the probability of detection? 22 MAY 2000

ASSESS VULNERABILITIES (CONT. ) • Adversary is successful if: • He (she) is quicker than response forces. RISK MANAGEMENT • (Detection is not a concern. ) IN THE APPROACH TO PHYSICAL SECURITY PLANNING • He (she) escapes detection. • (Time is not a concern. ) ED HAMILTON 22 MAY 2000

ASSESS VULNERABILITIES (CONT. ) MANAGEMENT • RISK ASSESS (Analytical System and Software for Evaluating Safeguards and Security) IN THE APPROACH TO PHYSICAL SECURITY PLANNING • EASI (Estimate of Adversary Sequence Interruption) ED HAMILTON MAY 2000 • SAVI (System 22 Analysis of Vulnerability to Intrusion)

ASSESS VULNERABILITIES (CONT. ) • RISK Assign weighted score to most feasible MANAGEMENT threat to each asset and/or that threat IN THE APPROACH presenting the lowest measure of TO PHYSICAL SECURITY PLANNING effectiveness (timely detection). ED HAMILTON 22 MAY 2000

ASSESS RISKS • The level of risk is specific to each asset. • Up to this point, we have: • Identified assets, IN THE APPROACH • Assessed SECURITY assets, TO PHYSICAL PLANNING • Assessed threats, and • Assessed vulnerabilities. ED HAMILTON 22 MAY 2000 RISK MANAGEMENT

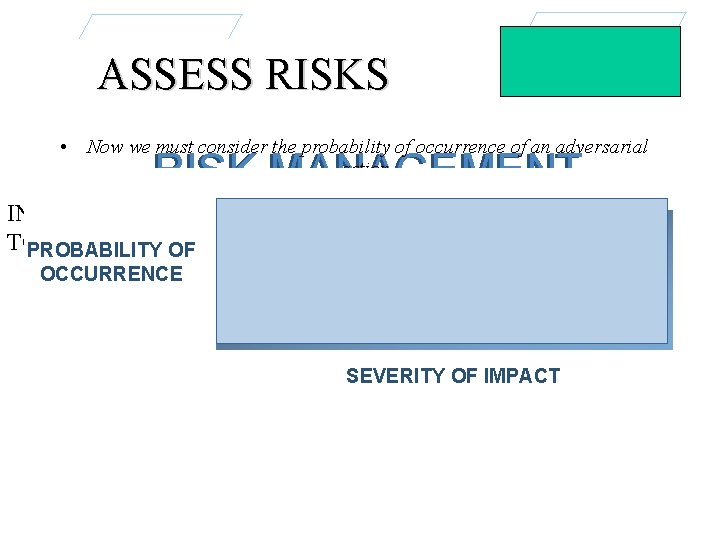
ASSESS RISKS • Now we must consider the probability of occurrence of an adversarial action. RISK MANAGEMENT IN THE APPROACH • PROBABILITY = THREAT X VULNERABILITY TO PHYSICAL OF SECURITY PLANNING PROBABILITY OCCURRENCE • Worst case threat to each asset. EDvulnerability HAMILTON • Worst case of that asset. 22 MAY 2000 SEVERITY OF IMPACT

ASSESS RISKS (CONT. ) • RISK =MANAGEMENT IMPACT X PROBABILITY RISK IN THE APPROACH TO PHYSICAL SECURITY PLANNING ED HAMILTON 22 MAY 2000

ASSESS RISKS (CONT. ) • Prioritize assets according to severity of impact of loss, damage, compromise, or disruption of operations. • Select quantified (scored) worst case threat to that asset. IN THE APPROACH • Select quantified. PLANNING (scored) worst case vulnerability to TO PHYSICAL SECURITY that asset. • Calculate probability of occurrence. • Calculate risk. ED HAMILTON RISK MANAGEMENT 22 MAY 2000

DETERMINE COUNTERMEASURES • Consider all of the options. OPTIONS • Do nothing • RISK Upgrade existing system MANAGEMENT • Augment existing system IN THE APPROACH • Replace existing system TO PHYSICAL SECURITY PLANNING • Modify concept of operation • • Retrain personnel Re-equip personnel ED HAMILTON Relocate assets 22 MAY 2000 Re-evaluate physical security objectives

DETERMINE COUNTERMEASURES OPTIONS • RISK Consider costs of countermeasure options: MANAGEMENT • Purchase or development IN THE APPROACH • Installation and test TO PHYSICAL SECURITY PLANNING • • • Training Operation Maintenance and ED logistics HAMILTON Life expectancy 22 MAY 2000 Perform trade-off studies and cost-benefit analyses

MAKE RISK MANAGEMENT DECISIONS RISK MANAGEMENT • Willing to accept cost of countermeasures IN THE APPROACH • or TO PHYSICAL SECURITY PLANNING • Willing to accept consequences of loss Assets Identify Assets Assess Threats Assess Vulnerabilities Cost Analysis Assess Risks Determine Countermeasure Options Benefit Analysis ED HAMILTON 22 MAY 2000 Make Risk Management Decisions
