RIJNDAEL Arta Doci University Of Colorado Email adociouray


![Pseudo Code: Rijndael_Cipher (byte [] block_of_data, byte [] KEY) { Expand_Key(KEY, Expanded_KEY); Add_Key(State[], Expanded_KEY[0]); Pseudo Code: Rijndael_Cipher (byte [] block_of_data, byte [] KEY) { Expand_Key(KEY, Expanded_KEY); Add_Key(State[], Expanded_KEY[0]);](https://slidetodoc.com/presentation_image/04fc1838784c5edecaa6e27149b534f0/image-8.jpg)
![Pseudo Code (continued): Round(State, Expanded_KEY[i]) { Substitute_Bytes(State); Shift_Rows(State); Mix_Columns(State); Add_Key(State[], Expanded_KEY[i]); } Last_Round (State, Pseudo Code (continued): Round(State, Expanded_KEY[i]) { Substitute_Bytes(State); Shift_Rows(State); Mix_Columns(State); Add_Key(State[], Expanded_KEY[i]); } Last_Round (State,](https://slidetodoc.com/presentation_image/04fc1838784c5edecaa6e27149b534f0/image-9.jpg)









- Slides: 23

RIJNDAEL Arta Doci University Of Colorado. Email: adoci@ouray. cudenver. edu

Topics Covered • Introduction • Characteristics of Rijndael • Algorithm and its building blocks • Mathematics behind Rijndael • Conclusion

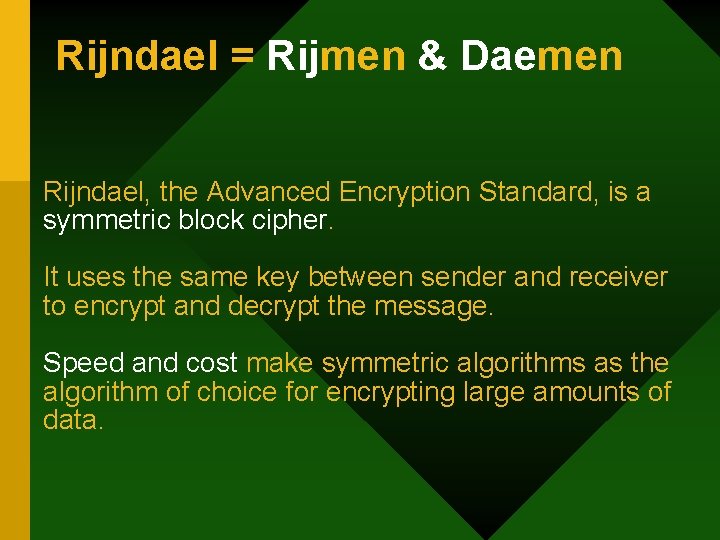
Rijndael = Rijmen & Daemen Rijndael, the Advanced Encryption Standard, is a symmetric block cipher. It uses the same key between sender and receiver to encrypt and decrypt the message. Speed and cost make symmetric algorithms as the algorithm of choice for encrypting large amounts of data.

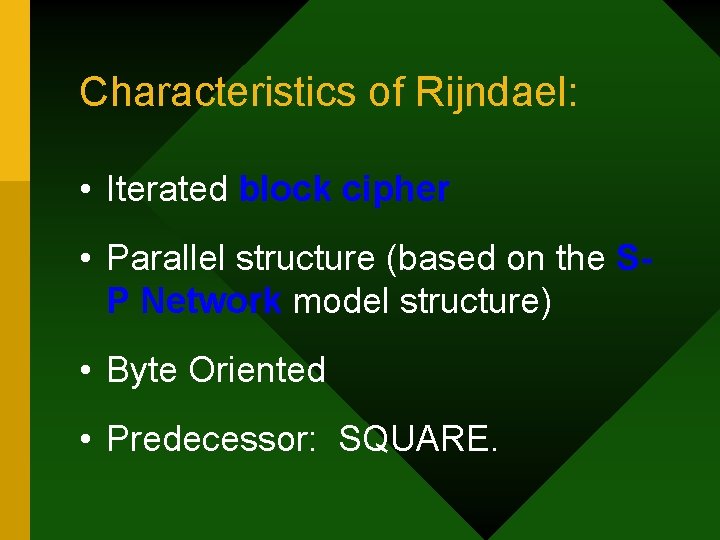
Characteristics of Rijndael: • Iterated block cipher • Parallel structure (based on the SP Network model structure) • Byte Oriented • Predecessor: SQUARE.

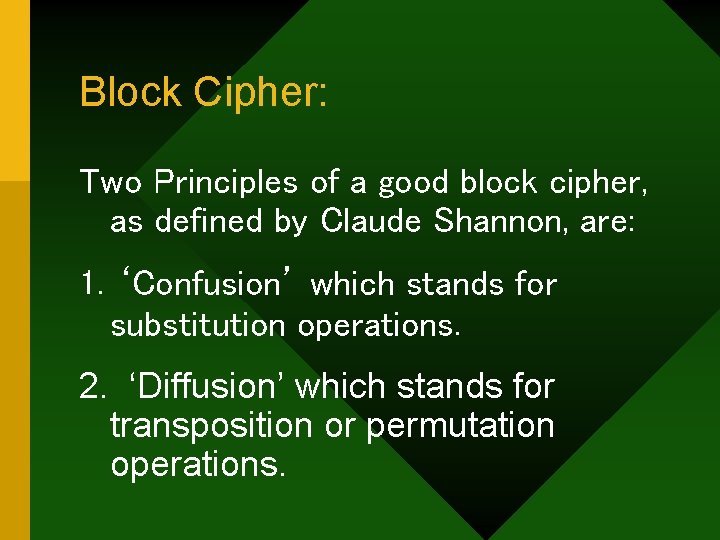
Block Cipher: Two Principles of a good block cipher, as defined by Claude Shannon, are: 1. ‘Confusion’ which stands for substitution operations. 2. ‘Diffusion’ which stands for transposition or permutation operations.

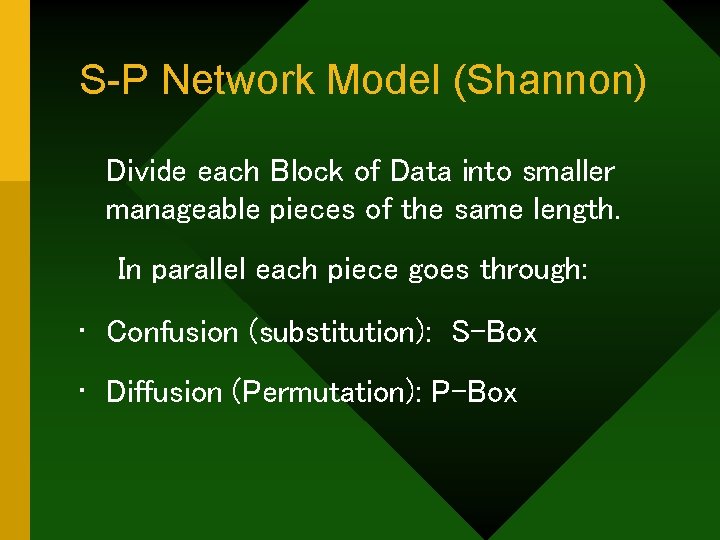
S-P Network Model (Shannon) Divide each Block of Data into smaller manageable pieces of the same length. In parallel each piece goes through: • Confusion (substitution): S-Box • Diffusion (Permutation): P-Box

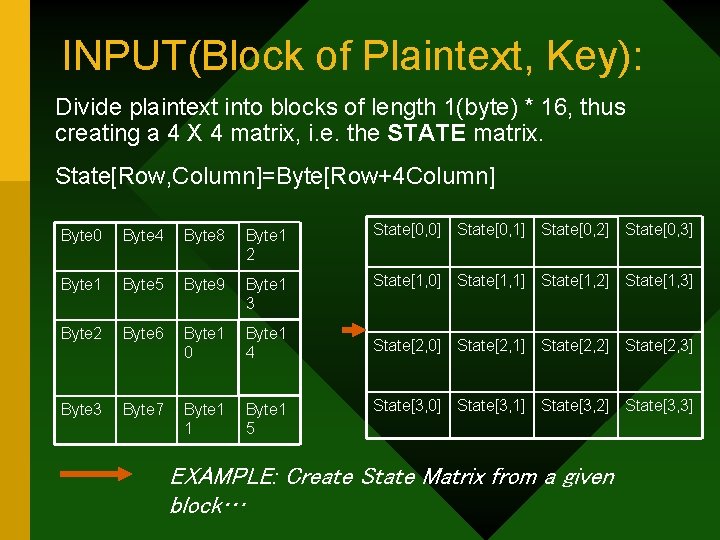
INPUT(Block of Plaintext, Key): Divide plaintext into blocks of length 1(byte) * 16, thus creating a 4 X 4 matrix, i. e. the STATE matrix. State[Row, Column]=Byte[Row+4 Column] Byte 0 Byte 4 Byte 8 Byte 1 2 State[0, 0] State[0, 1] State[0, 2] State[0, 3] Byte 1 Byte 5 Byte 9 Byte 1 3 State[1, 0] State[1, 1] State[1, 2] State[1, 3] Byte 2 Byte 6 Byte 1 0 Byte 1 4 Byte 3 Byte 7 Byte 1 1 Byte 1 5 State[2, 0] State[2, 1] State[2, 2] State[2, 3] State[3, 0] State[3, 1] State[3, 2] State[3, 3] EXAMPLE: Create State Matrix from a given block…
![Pseudo Code RijndaelCipher byte blockofdata byte KEY ExpandKeyKEY ExpandedKEY AddKeyState ExpandedKEY0 Pseudo Code: Rijndael_Cipher (byte [] block_of_data, byte [] KEY) { Expand_Key(KEY, Expanded_KEY); Add_Key(State[], Expanded_KEY[0]);](https://slidetodoc.com/presentation_image/04fc1838784c5edecaa6e27149b534f0/image-8.jpg)
Pseudo Code: Rijndael_Cipher (byte [] block_of_data, byte [] KEY) { Expand_Key(KEY, Expanded_KEY); Add_Key(State[], Expanded_KEY[0]); DO (Nr – 1 times) ROUND(State, Expanded_KEY[i]); Last_Round (State, Expanded_KEY[Nr]); }
![Pseudo Code continued RoundState ExpandedKEYi SubstituteBytesState ShiftRowsState MixColumnsState AddKeyState ExpandedKEYi LastRound State Pseudo Code (continued): Round(State, Expanded_KEY[i]) { Substitute_Bytes(State); Shift_Rows(State); Mix_Columns(State); Add_Key(State[], Expanded_KEY[i]); } Last_Round (State,](https://slidetodoc.com/presentation_image/04fc1838784c5edecaa6e27149b534f0/image-9.jpg)
Pseudo Code (continued): Round(State, Expanded_KEY[i]) { Substitute_Bytes(State); Shift_Rows(State); Mix_Columns(State); Add_Key(State[], Expanded_KEY[i]); } Last_Round (State, Expanded_KEY[Nr]) { Substitute_Bytes(State); Shift_Rows(State); Add_Key(State[], Expanded_KEY[i]); }

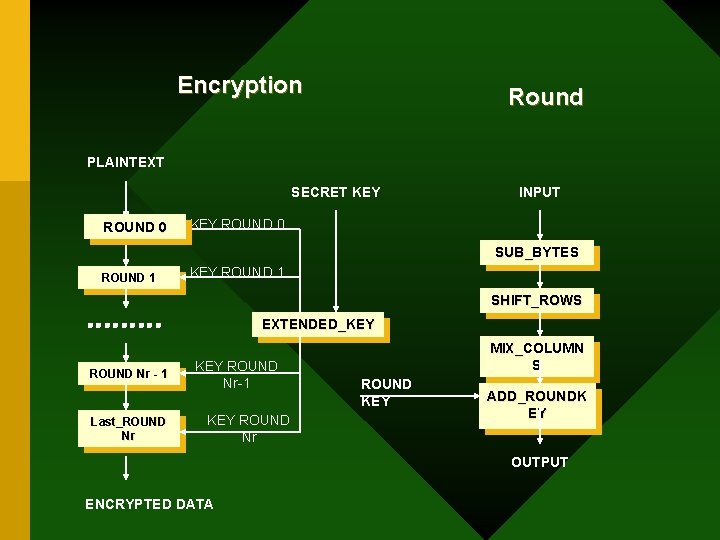
Encryption Round PLAINTEXT SECRET KEY ROUND 0 INPUT KEY ROUND 0 SUB_BYTES SUB_ ROUND 1 KEY ROUND 1 SHIFT_ROWS EXTENDED_KEY ROUND Nr - 1 Last_ROUND Nr KEY ROUND Nr-1 KEY ROUND Nr MIX_COLUMN MIX_ S ROUND KEY ADD_ROUNDK EY OUTPUT ENCRYPTED DATA

Number of Rounds Block size is fixed at 128 bits; key can be 128, 192, or 256. Nr is the number of rounds which is a function of Nk(Block length divided by 32 ), and Nb(Key length divided by 32 ) Nr Nb Nk 4 6 8 10 12 14

Expand_Key This procedure will 1. Expand the key From a cipher Key of bytes [4][Nk] to another array of (4) * (Nb*(Nr + 1)) = 4* (10 + 1) = 44 bytes. 2. Select a round key for each round. This procedure avoids: 1. Weak Keys by introducing asymmetry. 2. Key-related attacks(Biham) 3. Cipher keys that are partially known or that can be chosen by an imposter.

Add_Key will be called 1. Once in the beginning of rounds 2. Nr-1 times in the Round 3. Once in the final round. It just XOR-s the 16 bytes of the state with the 16 bytes of key (for the 128 bit key). EXAMPLE: Add_Key illustrated….

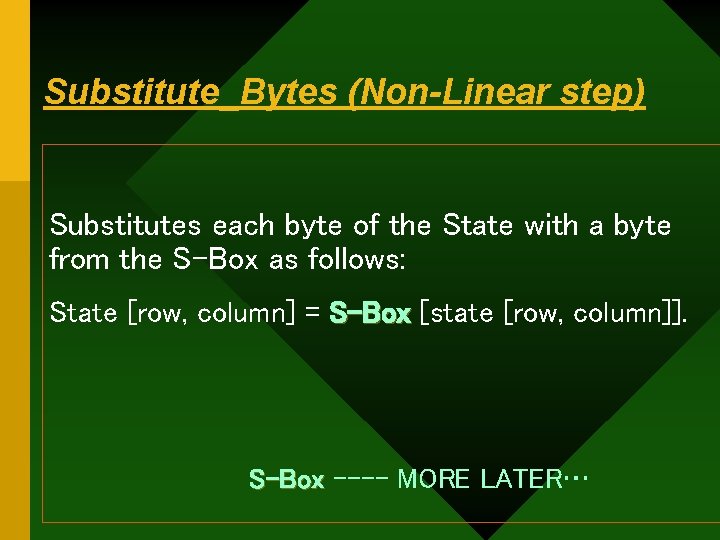
Substitute_Bytes (Non-Linear step) Substitutes each byte of the State with a byte from the S-Box as follows: State [row, column] = S-Box [state [row, column]]. S-Box ---- MORE LATER…

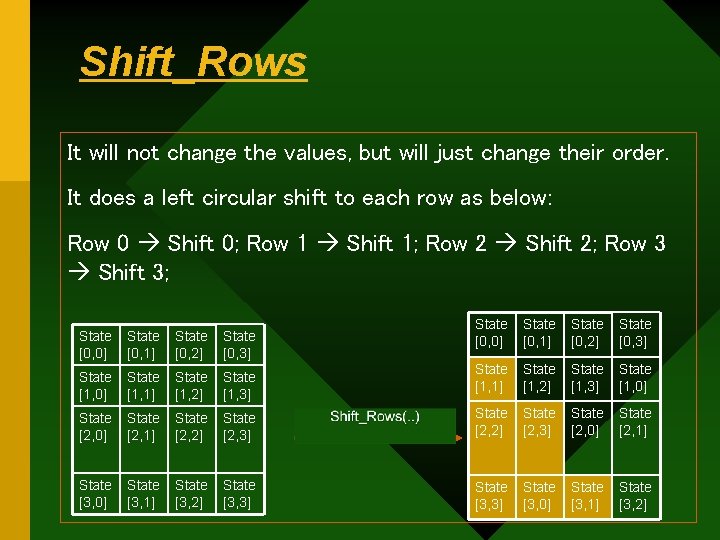
Shift_Rows It will not change the values, but will just change their order. It does a left circular shift to each row as below: Row 0 Shift 0; Row 1 Shift 1; Row 2 Shift 2; Row 3 Shift 3; State [0, 0] State [0, 1] State [0, 2] State [0, 3] State [1, 1] State [1, 2] State [1, 3] State [1, 0] State [2, 3] State [2, 2] State [2, 3] State [2, 0] State [2, 1] State [3, 3] State [3, 0] State [3, 1] State [3, 2] State [0, 0] State [0, 1] State [0, 2] State [0, 3] State [1, 0] State [1, 1] State [1, 2] State [1, 3] State [2, 0] State [2, 1] State [2, 2] State [3, 0] State [3, 1] State [3, 2]

Mathematics Behind Rijndael… • Field • Finite Field • Inverses

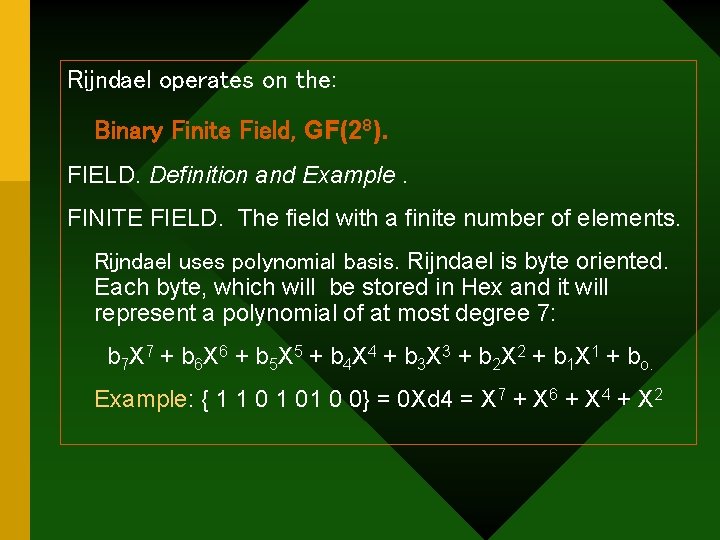
Rijndael operates on the: Binary Finite Field, GF(28). FIELD. Definition and Example. FINITE FIELD. The field with a finite number of elements. Rijndael uses polynomial basis. Rijndael is byte oriented. Each byte, which will be stored in Hex and it will represent a polynomial of at most degree 7: b 7 X 7 + b 6 X 6 + b 5 X 5 + b 4 X 4 + b 3 X 3 + b 2 X 2 + b 1 X 1 + bo. Example: { 1 1 01 0 0} = 0 Xd 4 = X 7 + X 6 + X 4 + X 2

FINITE FIELD GF(2 ^ 8) The set of all polynomials of degree at most 7 with coefficients GF(2) and with the two defined operations: Addition: Just XOR-in Multiplication: Shift to the left. and modulo an irreducible polynomial. Galois Theorem: For any prime p and integer n, there exists a field of order pn and it is unique. Cyclic Group Theorem: GF (pn)*, i. e. multiplicative Group, is cyclic; The nonzero elements are powers of some primitive root. Example: HOW do we construct such a field? Irreducible? Primitive Root?

Finding the multiplicative inverse… Multiplicative inverses in GF(256) using Look Up Tables: 1. Example: Building Log Table. 2. Building Anti Log Table. Reverse the Log process {03}(06) ={55}; {06} = {03}(55). 3. Building Inverse Table(using Log/Antilog). g (x) has as inverse g (ff ) – ( x). Example: {12}= {03} (e 0), so the inverse will be g (ff ) – ( e 0) =g 1 f = {aa}

S-BOX The only non-linear step … S-Box is based on the mapping: X -> X – 1 ; where X – 1 represents multiplicative inverse in the field 1. Replaces each byte with its inverse GF (28), g (a); beside 00 mapped to itself. 2. Applies an affine transformation (a bitwise modulo-two matrix, XOR-ed with the hexadecimal number 63. EXAMPLE: Lets find SRD [12]. ? ?

Mix_Columns multiplies two numbers: (A column that is considered as a polynomial) * (A mixing polynomial (modulo x 4 + 1)). Mixing polynomial is {03}*x 3 + {01} * x 2 + {01} * x + {02}. It should be relatively prime with the polynomial x 4 + 1={11}=(x+1)4, Thus, the fixed polynomial will have an inverse (mod x 4 + 1) and we can decrypt…. .

Conclusion • Secure – Excellent resistance to known attacks. • Elegant mathematical structure • Efficient

Q&A
 Arta doci
Arta doci Vincent rijmen and joan daemen
Vincent rijmen and joan daemen Rijndael block cipher
Rijndael block cipher Musli bajraktari
Musli bajraktari Alketa doci dinamo
Alketa doci dinamo Beware of greeks bearing gifts
Beware of greeks bearing gifts Doci ce maca na vratanca
Doci ce maca na vratanca Grafika inxhinierike
Grafika inxhinierike Eiliat
Eiliat Femme fatale literatura
Femme fatale literatura Druga deklinacija
Druga deklinacija Droga na szczyt dobosz doci
Droga na szczyt dobosz doci Perumahan arta bina ciherang
Perumahan arta bina ciherang Educatia este arta de a face omul etic
Educatia este arta de a face omul etic Palatul dogilor interior
Palatul dogilor interior Arta in grecia antica
Arta in grecia antica Arta bizantina
Arta bizantina Nu-ti voi lasa drept bunuri dupa moarte
Nu-ti voi lasa drept bunuri dupa moarte Tema nuvelei alexandru lapusneanul
Tema nuvelei alexandru lapusneanul Arta romei antice
Arta romei antice Scrisul si literatura in orientul antic
Scrisul si literatura in orientul antic Penggalan
Penggalan Stilul romanic
Stilul romanic Arta medievala stilul romanic si gotic
Arta medievala stilul romanic si gotic