RIJNDAEL 23 Add Round Key Sub Bytes RIJNDAEL









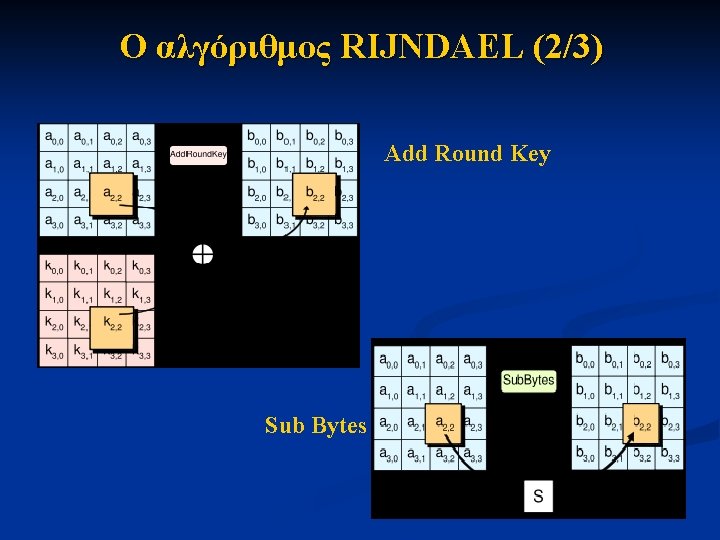
Ο αλγόριθμος RIJNDAEL (2/3) Add Round Key Sub Bytes
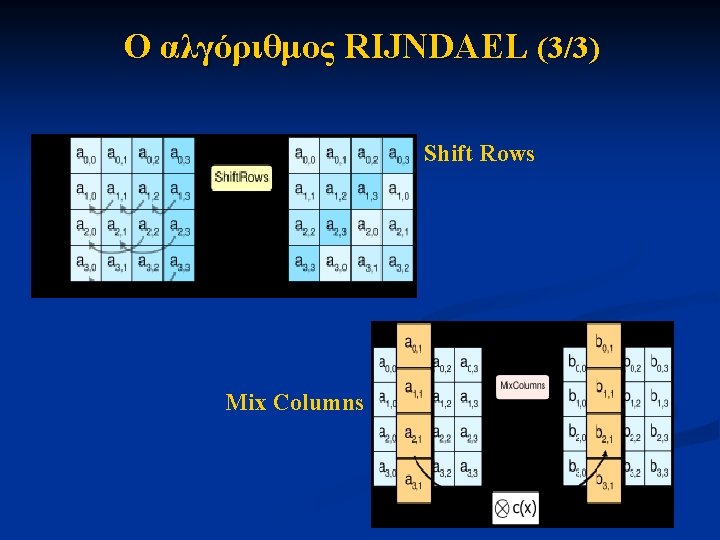
Ο αλγόριθμος RIJNDAEL (3/3) Shift Rows Mix Columns





Απόδοση λογισμικού Camellia (128 -bit keys) n Σε Pentium III n n 309 cycles/block (Assembly) = 469 Mbps (1. 13 GHz) Συγκρίσιμη ταχύτητα με άλλους AES finalists RC 6 Rijndael Twofish Camellia Mars Serpent 229 238 288 309 312. Encryption time [cycles/block] 759
![Σύγκριση Απόδοσης Camellia σε υλοποίηση Hardware (128 -bit keys) Μέγεθος [Kgates] MARS RC 6 Σύγκριση Απόδοσης Camellia σε υλοποίηση Hardware (128 -bit keys) Μέγεθος [Kgates] MARS RC 6](http://slidetodoc.com/presentation_image_h2/e1b134150ce84444cfbe021119bc70d9/image-21.jpg)
Σύγκριση Απόδοσης Camellia σε υλοποίηση Hardware (128 -bit keys) Μέγεθος [Kgates] MARS RC 6 Rijndael Serpent Twofish Camellia DES 2, 936 1, 643 613 504 432 273 54 Ρυθμός [Mbit/s] 226 204 1, 950 932 394 1, 171 1, 161


Κρυπτογραφική έρευνα-οργανισμοί Ευρώπη ECRYPT (Network of Excellence in Cryptology) contract number IST-2002 -507932 e-Stream (2004 -2008) e-Bats (2004 -2008) (benchmarking) n NESSIE (New European Schemes for Signatures, Integrity, and Encryption) contract n number IST-1999 -12324 (2000 -2004)

Αμερική n n NIST -National Institute of Standards and Technology FIPS -Federal Information Processing Standards Ιαπωνία n CRYPTREC - Cryptography Research and Evaluation Committees (2000 -2005) Διεθνής n n n IACR -The International Association for Cryptologic Research CDT -The Center for Democracy and Technology EPIC -Electronic Privacy Information Center



![Βιβλιογραφία [1] D. Kahn, Codebreakers: The Story of Secret Writing, Macmillan, 1967 [2] H. Βιβλιογραφία [1] D. Kahn, Codebreakers: The Story of Secret Writing, Macmillan, 1967 [2] H.](http://slidetodoc.com/presentation_image_h2/e1b134150ce84444cfbe021119bc70d9/image-36.jpg)
Βιβλιογραφία [1] D. Kahn, Codebreakers: The Story of Secret Writing, Macmillan, 1967 [2] H. Feistel, "Cryptographic coding for data bank privacy, " IBM Corp. Res. Rep. RC 2827, Mar. 1970. (I-B 4, III-B, SFR) [3] Diffie, W. & Hellman, M. E. (1976), ‘New directions in cryptography’, IEEE Trans. Inform. Theory IT-22 (6) 644– 654. [4] R. Rivest, A. Shamir, L. Adleman, ”A Method for Obtaining Digital Signatures and Public-Key Cryptosystems”, Communications of the ACM 21, 2 (Feb. 1978), 120 -126 [5] T. El Gamal. A public key cryptosystem and signature scheme based on discrete logarithms. IEEE Trans. Inform. Theory, 31: 469 --472, 1985 [6] National Institute of Standards and Technology, NST FIPS PUB 186, Digital Signature Standard, U. S. Department of Commerce, May, 1994 [7] J. Nechvatal, E. Barker, L. Bassham, W. Burr, M. Dworkin, J. Foti and E. Roback, “Report on the Development of the Advanced Encryption Standard (AES)” , Journal of Research of the National Institute of Standards and Technology, 2000, Volume 106, pp. 511– 576
![[8] Dworkin, M. , "Recommendation for Block Cipher Modes of Operation Methods and Techniques", [8] Dworkin, M. , "Recommendation for Block Cipher Modes of Operation Methods and Techniques",](http://slidetodoc.com/presentation_image_h2/e1b134150ce84444cfbe021119bc70d9/image-37.jpg)
[8] Dworkin, M. , "Recommendation for Block Cipher Modes of Operation Methods and Techniques", NIST Special Publication 800 -38 A, December 2001 [9] CNSS Policy No. 15, Fact Sheet No. 1, National Policy on the Use of the Advanced Encryption Standard (AES) to Protect National Security Systems and National Security Information , June 2003 [10] N. Ferguson, R. Schroeppel, D. Whiting, “A simple algebraic representation of Rijndael “, Selected Areas in Cryptography, Proc. SAC 2001, Lecture Notes in Computer Science 2259, pp. 103– 111, Springer Verlag, 2001 [11] K. Aoki and H. Lipmaa, “Fast Implementations of AES Candidates”, Third Advanced Encryption Standard Candidate Conference, 2000, pages 106– 120 [12] H. Lipmaa, Fast Implementations of AES and IDEA for Pentium 3 and 4, October 2005, http: //home. cyber. ee/helger/implementations [13] A. Hodjat, I. Verbauwhede, “A 21. 54 Gbit/s fully pipelined AES processor on FPGA”, Field–Programmable Custom Computing Machines 2004 (FCCM’ 04), 12 th Annual IEEE Symposium, pages 308 – 309 [14] B. Schneier, J. Kelsey, D. Whiting, D. Wagner, C. Hall and N. Ferguson, “Performance Comparison of the AES Submissions”, Proc. Second AES Candidate Conference, NIST, 1999, pp. 15 -34
![[15] A. Lenstra, Key Length, Contribution to “The Handbook of Information Security”, 2004, http: [15] A. Lenstra, Key Length, Contribution to “The Handbook of Information Security”, 2004, http:](http://slidetodoc.com/presentation_image_h2/e1b134150ce84444cfbe021119bc70d9/image-38.jpg)
[15] A. Lenstra, Key Length, Contribution to “The Handbook of Information Security”, 2004, http: //cm. bell-labs. com/who/akl/key_lengths. pdf [16] ECRYPT Yearly Report on Algorithms and Keysizes 2005, http: //www. ecrypt. eu. org/documents/D. SPA. 16 -1. 0. pdf [17] J. Buchmann, Einf¨uhrung in die Kryptographie, Springer, 2001, ISBN: 3 -540 -41283 -2, also available in English ISBN: 0 -387 -21156 -X [18] K. Aoki et. , al. “Camellia: A 128 -Bit Block Cipher Suitable for Multiple Platforms- Design and Analysis”, Selected Areas in Cryptography 2000, pp 39– 56 [19] Matsui, M. , Nakajima, J. , and S. Moriai, "A Description of the Camellia Encryption Algorithm", RFC 3713, April 2004 [20] NIST, FIPS PUB 197, "Advanced Encryption Standard (AES), "November 2001. http: //csrc. nist. gov/publications/fips 197/fips-197 [21] Frankel, S. , Glenn, R. , and S. Kelly, "The AES-CBC Cipher Algorithm and Its Use With IPsec, " RFC 3602, September 2003 [22] A. Lenstra, Unbelievable Security, 2001, http: //www. win. tue. nl/~klenstra/aes_match. pdf
![[23] The NESSIE project (New European Schemes for Signatures, Integrity and Encryption), http: //www. [23] The NESSIE project (New European Schemes for Signatures, Integrity and Encryption), http: //www.](http://slidetodoc.com/presentation_image_h2/e1b134150ce84444cfbe021119bc70d9/image-39.jpg)
[23] The NESSIE project (New European Schemes for Signatures, Integrity and Encryption), http: //www. cosic. esat. kuleuven. ac. be/nessie [24] NIST Computer Security Division, http: //csrc. nist. gov/ [25] Arjen Lenstra and E. Verheul, ”Selecting Cryptographic Key Sizes”, 2001, http: //citeseer. ist. psu. edu/287428. html [26] RSA Security, PKCS #1: RSA Cryptography Standard, http: //www. rsasecurity. com/rsalabs/node. asp? id=2125 [27] Ilya Mironov Microsoft Research, Silicon Valley Campus mironov@microsoft. com November 14, 2005 [IACR] http: //www. iacr. org/ [CDT] http: //www. cdt. org/crypto/ [EPIC ] http: //www. epic. org/epic/about. html [NSA] www. nsa. gov [CRYPTREC] Information-technology Promotion Agency (IPA), Japan, http: //www. ipa. go. jp/security/enc/CRYPTREC/index-e. html
- Slides: 40