RFID Authentication Minimizing Tag Computation CHES 2006 Rump




- Slides: 10

RFID Authentication : Minimizing Tag Computation CHES 2006 Rump Session, Yokohama. Japan 2006. 10. 11. Ph. D. Jin Kwak Kyushu University, JAPAN jkwak@security. re. kr or jkwak@itslab. csce. kyushu-u. ac. jp

Background - Definition of RFID - Radio Frequency Identification RFID (Radio Frequency Identification) is data carrier technology that transmits information via signal in the radio frequency portion of the electromagnetic spectrum. [GS 1 US] 2

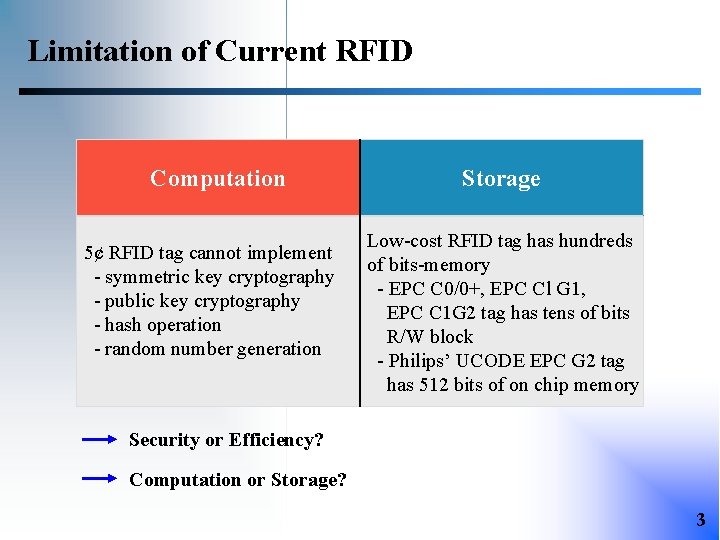
Limitation of Current RFID Computation 5¢ RFID tag cannot implement - symmetric key cryptography - public key cryptography - hash operation - random number generation Storage Low-cost RFID tag has hundreds of bits-memory - EPC C 0/0+, EPC Cl G 1, EPC C 1 G 2 tag has tens of bits R/W block - Philips’ UCODE EPC G 2 tag has 512 bits of on chip memory Security or Efficiency? Computation or Storage? 3

Assumptions Limited successive tag queries Limited interleaving The probability that an attacker can successively transmit a Query to targeted RFID tags in different locations before updating the RFID tags’ identification data is very low The mobility of RFID tags and password mechanism restrict the attacker’s ability to perform attack 4

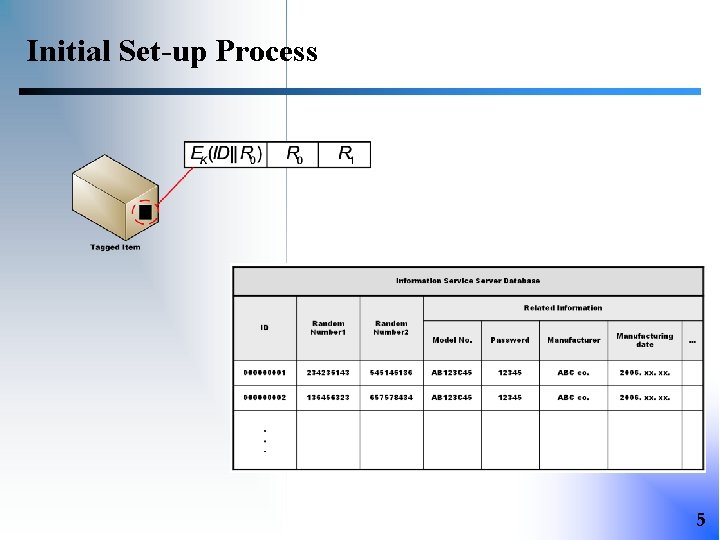
Initial Set-up Process 5

Authentication Process(1/2) 6

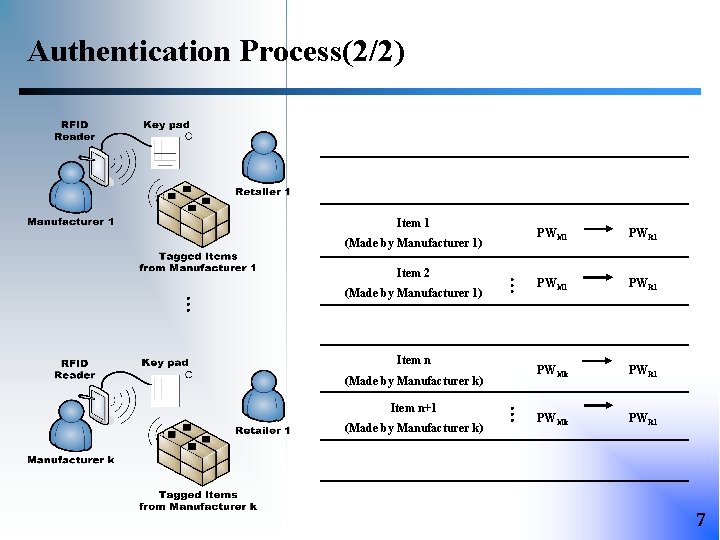
Authentication Process(2/2) Item 1 (Made by Manufacturer 1) … Item 2 Item n (Made by Manufacturer k) … Item n+1 Current New Password PWM 1 PWR 1 PWMk PWR 1 7

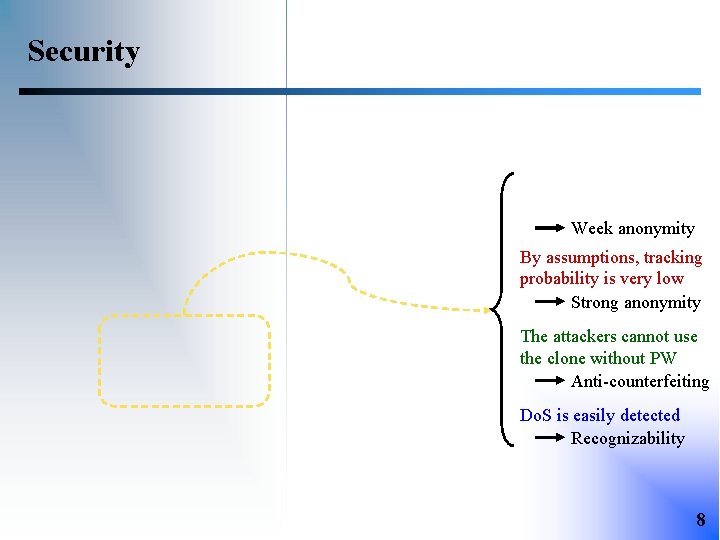
Security Without PW, the attackers cannot obtain ID Week anonymity By assumptions, tracking probability is very low Strong anonymity The attackers cannot use the clone without PW Anti-counterfeiting Do. S is easily detected Recognizability 8

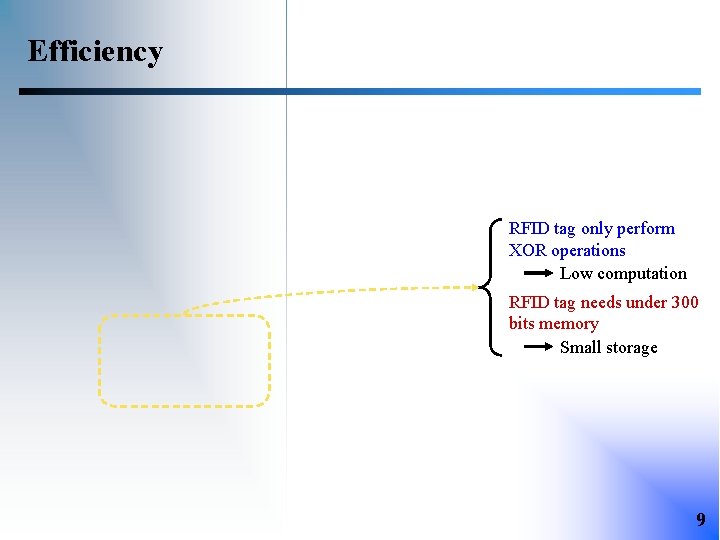
Efficiency RFID tag only perform XOR operations Low computation RFID tag needs under 300 bits memory Small storage 9

Thanks … Please e-mail to jkwak@security. re. kr or jkwak@itslab. csce. kyushu-u. ac. jp 10