Reversible Data Hiding with Improved Histogram Alteration Method

多媒體網路安全實驗室 Reversible Data Hiding with Improved Histogram Alteration Method Source: International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIHMSP), 2010 Sixth. Authors: Hsiang-Cheh Huang, Yueh-Hong Chen, and I-Hung Wang Speaker: Cheng Hsu Date: 2011/05/05

多媒體網路安全實驗室 Outline 1. Introduction 2. Related work 3. Proposed scheme 4. Experimental results 5. Conclusions 2

多媒體網路安全實驗室 1. Introduction v. Reversible data hiding: 1. Histogram-based scheme. 2. Difference expansion (DE) scheme. v. They consider the easily implemented algorithm, called histogram-based scheme in reversible data hiding, and they modify the difference between adjacent pixels for making data hiding possible. 3
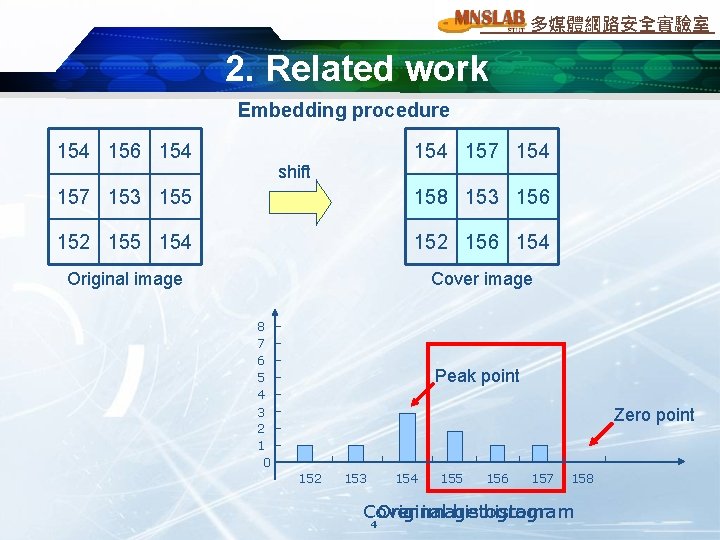
多媒體網路安全實驗室 2. Related work Embedding procedure 154 156 154 157 154 shift 157 153 155 158 153 156 152 155 154 152 156 154 Original image Cover image 8 7 6 5 4 Peak point 3 2 1 0 Zero point 152 153 154 155 156 157 158 Cover Original image histogram 4
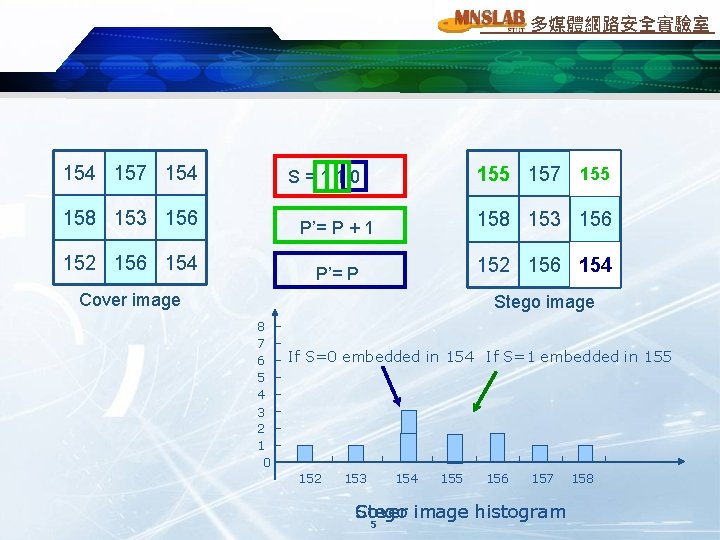
多媒體網路安全實驗室 154 157 154 155 157 154 S=110 158 153 156 152 156 154 P’= P + 1 158 153 156 P’= P 152 156 154 Cover image Stego image 8 7 6 5 4 If S=0 embedded in 154 If S=1 embedded in 155 3 2 1 0 152 153 154 155 156 157 Cover Stego image histogram 5 158
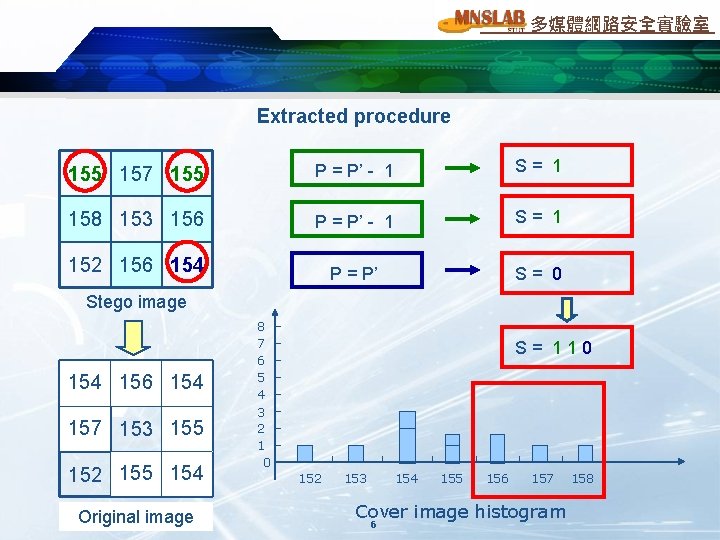
多媒體網路安全實驗室 Extracted procedure 155 157 155 P = P’ - 1 S= 1 158 153 156 P = P’ - 1 S= 1 152 156 154 P = P’ S= 0 Stego image 154 155 156 157 154 155 157 158 153 155 156 152 155 156 154 Cover image Original image 8 7 6 5 4 S= 110 3 2 1 0 152 153 154 155 156 157 Cover image histogram 6 158
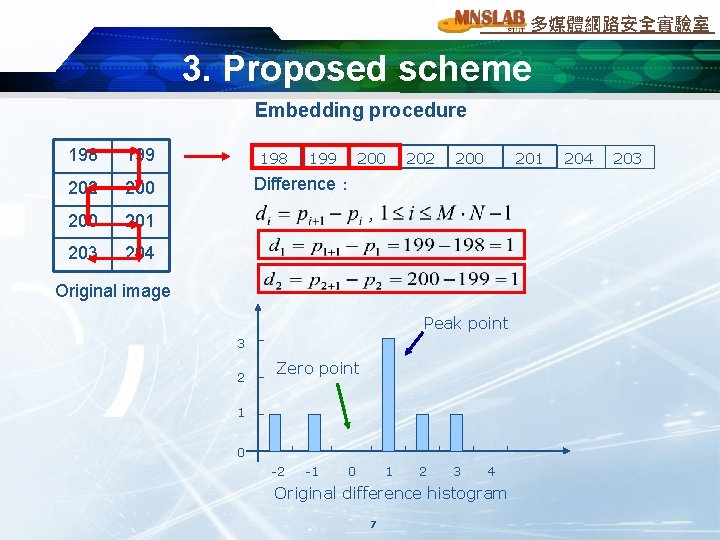
多媒體網路安全實驗室 3. Proposed scheme Embedding procedure 198 199 202 200 201 203 204 198 199 200 202 200 201 Difference: Original image Peak point 3 2 Zero point 1 0 -2 -1 0 1 2 3 4 Original difference histogram 7 204 203
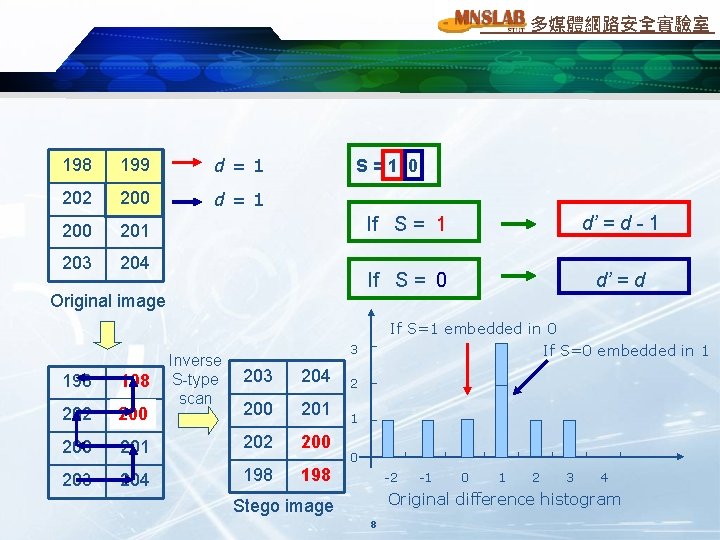
多媒體網路安全實驗室 198 199 d=1 202 200 d=1 200 201 203 204 S=1 0 Original image If S = 1 d’ = d - 1 If S = 0 d’ = d If S=1 embedded in 0 Inverse S-type scan 203 204 200 201 202 200 204 198 198 202 200 203 If S=0 embedded in 1 3 2 1 0 -2 -1 0 1 2 3 4 Original difference histogram Stego image 8
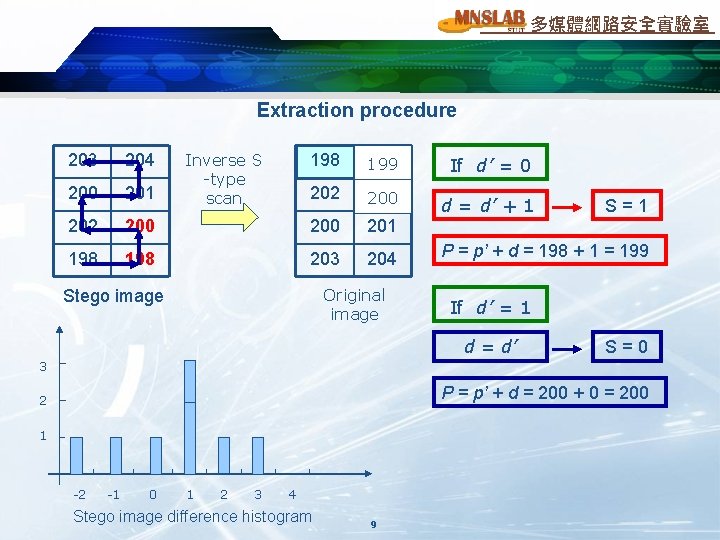
多媒體網路安全實驗室 Extraction procedure 203 204 200 201 202 198 Inverse S -type scan 198 199 If d’ = 0 202 200 d = d’ + 1 200 201 198 203 204 Original image Stego image S=1 P = p’ + d = 198 + 1 = 199 If d’ = 1 d = d’ S=0 3 P = p’ + d = 200 + 0 = 200 2 1 -2 -1 0 1 2 3 4 Stego image difference histogram 9
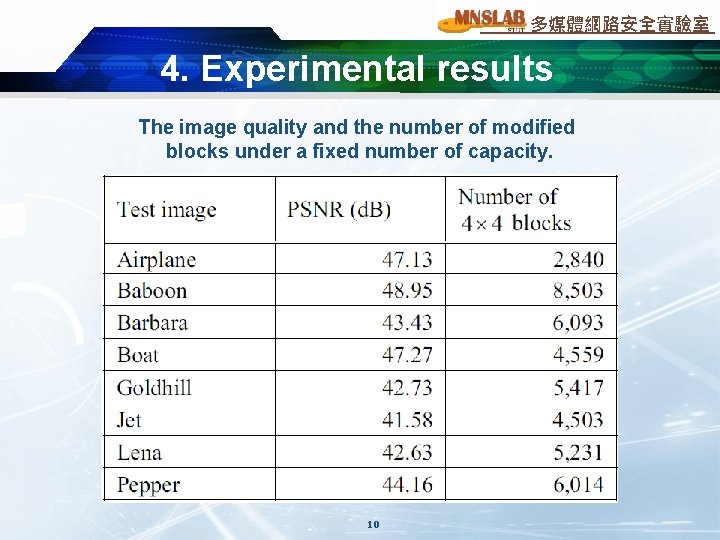
多媒體網路安全實驗室 4. Experimental results The image quality and the number of modified blocks under a fixed number of capacity. 10
![多媒體網路安全實驗室 Comparisons between maximal capacity and that in [2]. 11 多媒體網路安全實驗室 Comparisons between maximal capacity and that in [2]. 11](http://slidetodoc.com/presentation_image_h2/430747455a2bf8fadd7cecda2ff97965/image-11.jpg)
多媒體網路安全實驗室 Comparisons between maximal capacity and that in [2]. 11

多媒體網路安全實驗室 5. Conclusions v. In this paper, they proposed an improved reversible data hiding scheme by modifying the histogram of original image with its inherent characteristics. v. In comparison with conventional scheme [2], more capacity with their scheme can be embedded. 12

- Slides: 13