Reverse Engineering vehicles Burpsuite Style Hardwear io 2016
Reverse Engineering vehicles Burpsuite Style Hardwear. io 2016 Javier Vazquez Vidal & Henrik Ferdinand Nölscher @fjvva @s 1 ckcc @codewhitesec

Who are we? § Javier is a Hardware Security Specialist § Works at Code White as a Product Security Engineer § He is from Cadiz (Spain) § Enjoys reversing products that are interesting, or could potentially be more fun § Likes cake (when it’s not a lie) and bbqs

Who are we? § Ferdi works as Hardware Security Researcher at Code White in Ulm § Among many things, he likes attacking hardware and software systems, lasers § Prefers BBQs over cake

Current Car Hacking status § Focus is on the CAN bus § Replay attacks and/or packet injection § Some researchers also found remote exploits to take control of certain vehicles § There are some tools to help understand the UDS protocol

So, where are the goodies? § UDS is not the only protocol § TP 2. 0 (Tunneling Protocol) is the CAN version of KWP 2000 § Both offer a series of services which are very interesting, but often not taken into consideration § With use of these services, a lot of Information can be gathered and modified

What is UDS? § UDS stands for Unified Diagnostics Service § It is present in all modern cars § Provides access to the Services offered by ECUs § It takes place on the top of the CAN protocol (Layer 4) § Allows to perform transmissions of up to 256 bytes § It is just a Transport Protocol
What types of transmissions exist in UDS? § Single frame transmissions (7 bytes or less payload length) § Multiple frame transmissions (more than 7 bytes payload length)
What kind of frames exist in UDS? § No ACK request, part of multiframe transmission(0 x 20) § ACK request, part of multiframe transmission (0 x 10) § No ACK request, single frame (0 x 00) § ACK (0 x 30) § NACK/Repeat transmission
What is TP 2. 0? § TP stands for Tunneling protocol § It is present in some ECUs and used for internal communications § It is a port of the K-LINE protocol (KWP 2000) § It takes place on the top of the CAN protocol (Layer 4) § Allows to perform transmissions of up to 256 bytes § It is just a Transport Protocol
What types of transmissions exist in TP 2. 0? § Single frame transmissions (5 bytes or less payload length) § Multiple frame transmissions (more than 5 bytes payload length)
What kind of frames exist in TP 2. 0 transmissions? § No ACK request, with following frames(0 x 20) § ACK request, with following frames(0 x 00) § No ACK request, last frame (0 x 30) § ACK request, last frame (0 x 10) § ACK (0 x. B 0) § NACK/Repeat transmission (0 x 90)
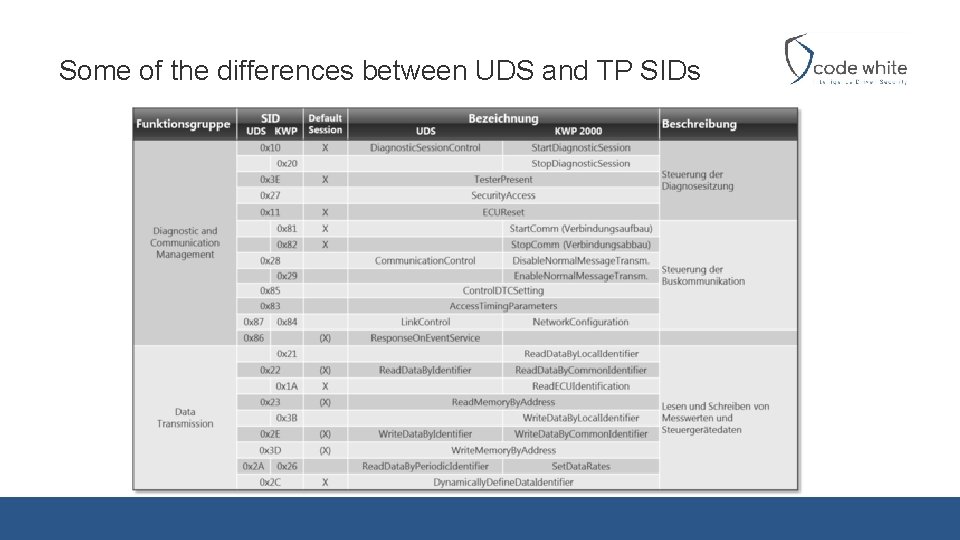
Some of the differences between UDS and TP SIDs

The most interesting Services § Security. Access (0 x 27): Allows access to restricted Services § Read. Memory. By. Address (0 x 23): Allows to read certain memory addresses § Read/Write. Data. By. ID(0 x 22/0 x 2 E): Allows to read/write certain parameters § Request. Upload(0 x 35): Service used to retrieve firmware from the ECU § Routine. Control(0 x 31): Allows to start “routines”, which have different effects

Say hello to the CANBadger!
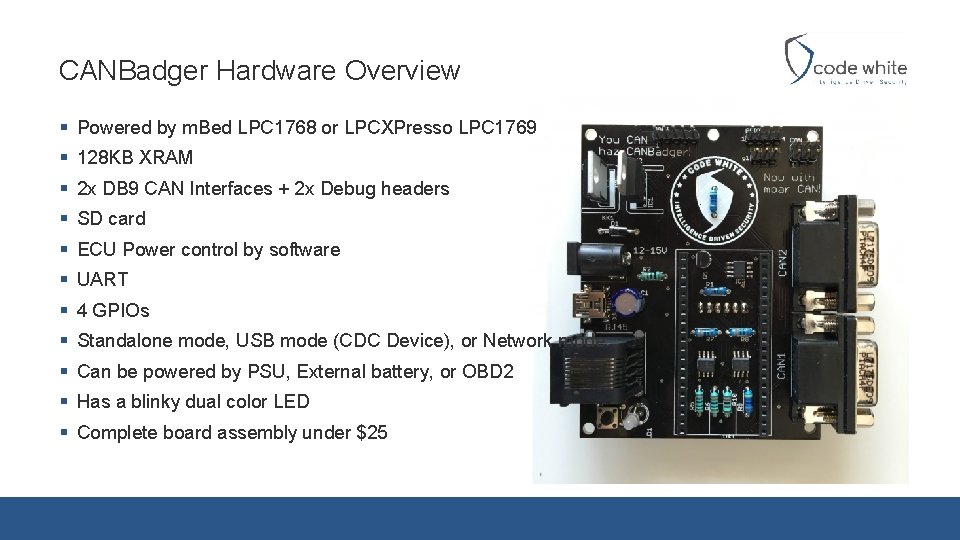
CANBadger Hardware Overview § Powered by m. Bed LPC 1768 or LPCXPresso LPC 1769 § 128 KB XRAM § 2 x DB 9 CAN Interfaces + 2 x Debug headers § SD card § ECU Power control by software § UART § 4 GPIOs § Standalone mode, USB mode (CDC Device), or Network mode § Can be powered by PSU, External battery, or OBD 2 § Has a blinky dual color LED § Complete board assembly under $25
CANBadger POC Firmware Features § All actions are handled by the CANBadger firmware § Supports UDS, TP 2. 0 and RAW CAN § Diagnostics Sessions are interactive (realtime) § MITM with rules stored in SD § Hijack Security. Access § Emulate SIDs/PIDs from log § Dump Data Transfers to SD § Log UDS and TP 2. 0 traffic with very detailed verbosity in standard or bridge mode § Log RAW CAN traffic in standard or bridge mode § Detect CAN speed § Ethernet for use with GUI
Protocol Analysis § Many SIDs already included in firmware § Extremely fast to add support for new SIDs § High verbosity § Logging and parsing is done by the CANBadger firmware § Logs are stored in the SD card and can be viewed and retrieved without removing it § Works with UDS and TP 2. 0
TP 2. 0 and UDS Interactive Session § No scripting required § Allows to perform actions on the go § Built-in scanners for SID parameters
CANBadger Server Purpose: § Make using the Can. Badger even easier § Use multiple Can. Badgers in parallel § Programmable access to automate Can. Badgers § Fuzzing § Automated testing
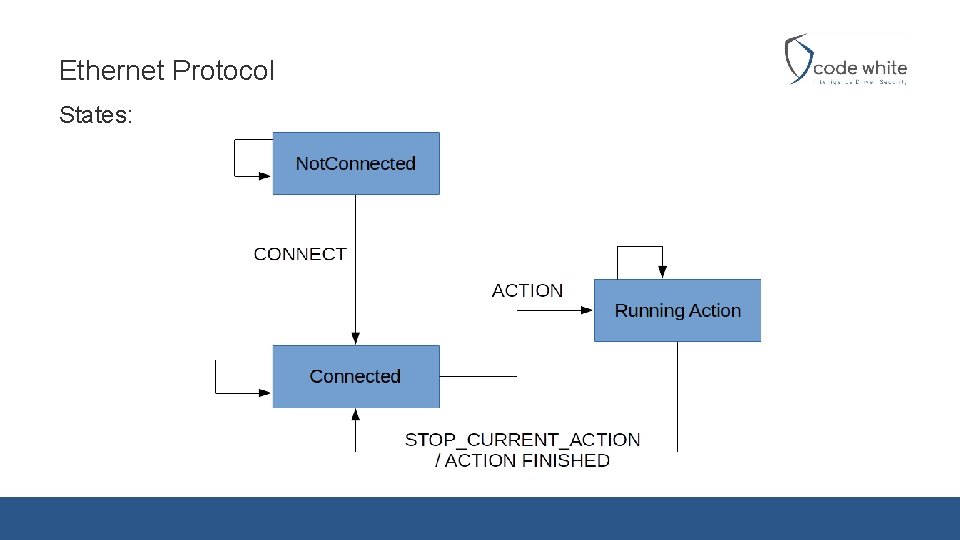
Ethernet Protocol States:
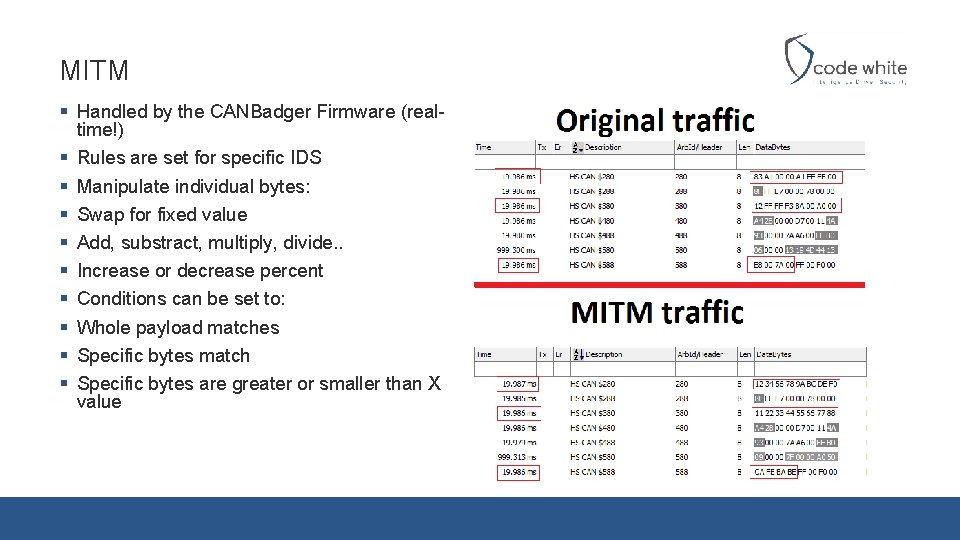
MITM § Handled by the CANBadger Firmware (realtime!) § Rules are set for specific IDS § Manipulate individual bytes: § Swap for fixed value § Add, substract, multiply, divide. . § Increase or decrease percent § Conditions can be set to: § Whole payload matches § Specific bytes match § Specific bytes are greater or smaller than X value

Canbadger Server
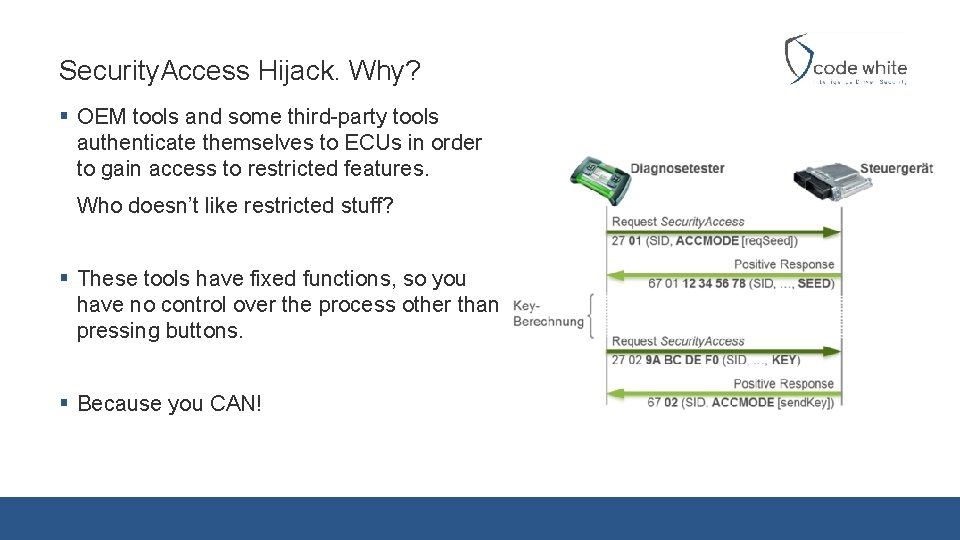
Security. Access Hijack. Why? § OEM tools and some third-party tools authenticate themselves to ECUs in order to gain access to restricted features. Who doesn’t like restricted stuff? § These tools have fixed functions, so you have no control over the process other than pressing buttons. § Because you CAN!

Security. Access Hijack. How? § Wait for a Security. Access request in transparent bridge mode § Switch to the desired type of Diagnostics Session § Security. Access auth is forwarded § Success? Cut off the external tool and take control over the Session!
Upload and Download Capture § Firmware updates can be distributed over UDS and TP § To grab the data, the Can. Badger does the following: § Log CAN traffic to SD § Parse CAN traffic and look for transfers § Write binary file to the SD
So, we survived the demos (hopefully!) § What else can the CANBadger do? § Dump TP and UDS transfers, which are used for firmware updates § Spoof OBD 2 data thru MITM and Emulator § Use GPIO pins for bootloading (Tricore f. ex) § Manipulate other signals via UART pins

Hacking instructions § Main IDE we used for firmware is LPCXpresso § Has code limit in free version § For python, you just need python 2. 7 and pip § For quick modifications you can also use the mbed online compiler § Export to Keil/IAR/Coo. Cox is possible

Hacking instructions § Code and schematics are GPL § Everything has been published on Github: gutenshit. github. io/CANBadger § You are encouraged to create issues for: § Feature Requests § Bugs § Enhancements
Thanks! § To all of you for being here today! § To Code White for their support and trust in the project § To our family and friends for supporting us even when we run out of coffee Javier Vazquez @fjvva javier. vazquez. vidal@code-white. com Ferdinand Nölscher @s 1 ckcc ferdinand. noelscher@code-white. com
- Slides: 29