Revealing the Secrets Source Code Disclosure Techniques and










![v Contact me: anant. kochhar[at]secureyes[dot]net v Contact me: anant. kochhar[at]secureyes[dot]net](https://slidetodoc.com/presentation_image/b0a1bc52a8c0414d3da7a1fc60708aad/image-39.jpg)
- Slides: 39

Revealing the Secrets: Source Code Disclosure, Techniques, and Impacts

I am… v Anant Kochhar, Senior Information Security Consultant with Secur. Eyes v Project Manager and Researcher v Malware Detection Techniques and v Real World Cracker Techniques

Unique Insecurities… v Each developer is unique v Each application is uniquely insecure. v Each developer is uniquely insecure.

Source Code Disclosure Types v Accidental Code Disclosure v Backup and Misc. Files v The Dirty Download Page

Accidental Disclosure v Part of the Source Code is available in the HTML source code. v When Dynamic pages are turned into Static pages: like from ‘. asp’ to ‘. html’ v Coder don’t remove the ASP code before publishing the HTML page. v Why? Because IE is very forgiving.

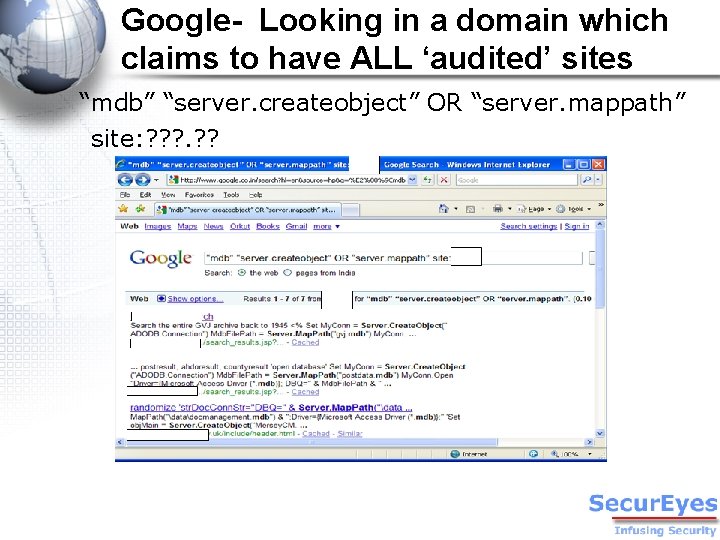
Google- Looking in a domain which claims to have ALL ‘audited’ sites “mdb” “server. createobject” OR “server. mappath” site: ? ? ?

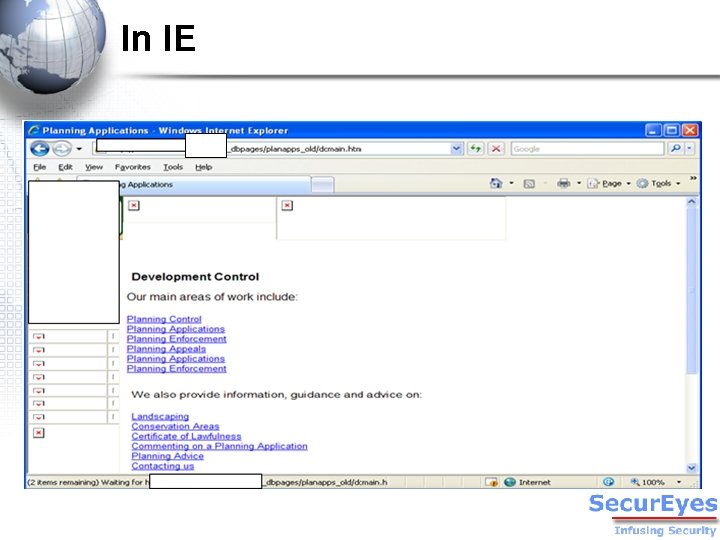
In IE

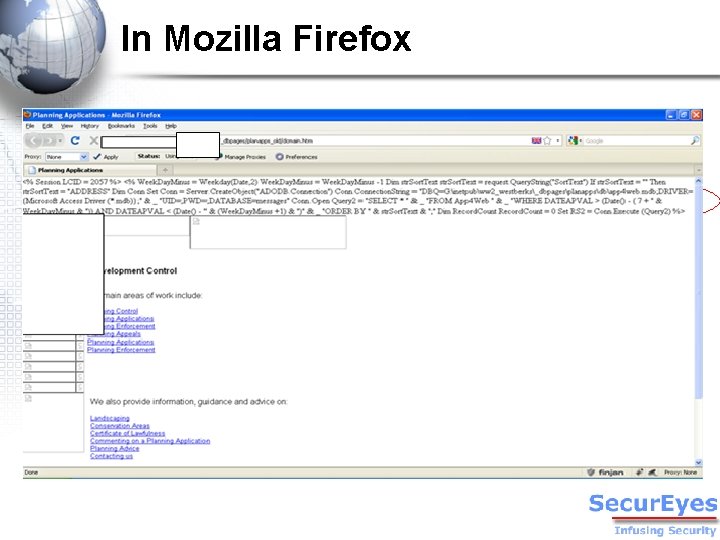
In Mozilla Firefox

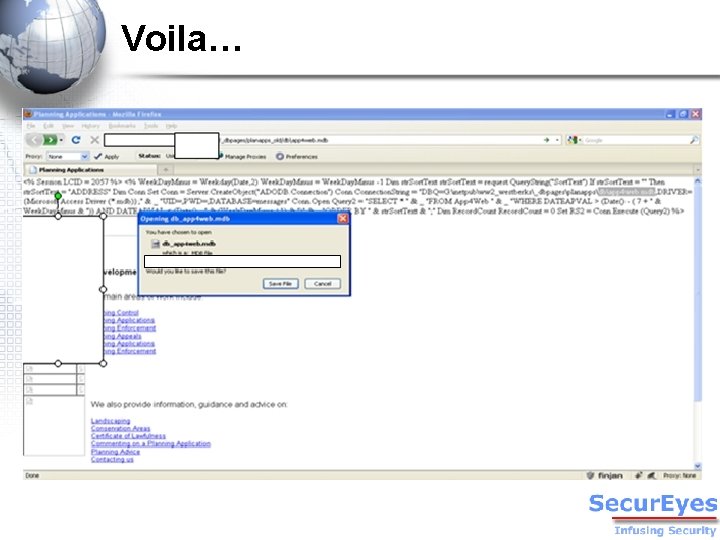
Voila…

How to avoid it… v Don’t be careless. – Go through the HTML source code of every page before it is published online. v Use both IE and Firefox to test a page.

Backup and Misc. Files v Source Codes stored in readable formats. v Coders save backup files in the website’s hosting folders. v Zipped files, ‘. bak’ extensions etc. v Coders often use bad extensions- like ‘. inc’- for ‘included’ configuration files.

How to discover… v Directory Listings. v Disclosure in HTML Source (Rare) v Other non-standard techniques.

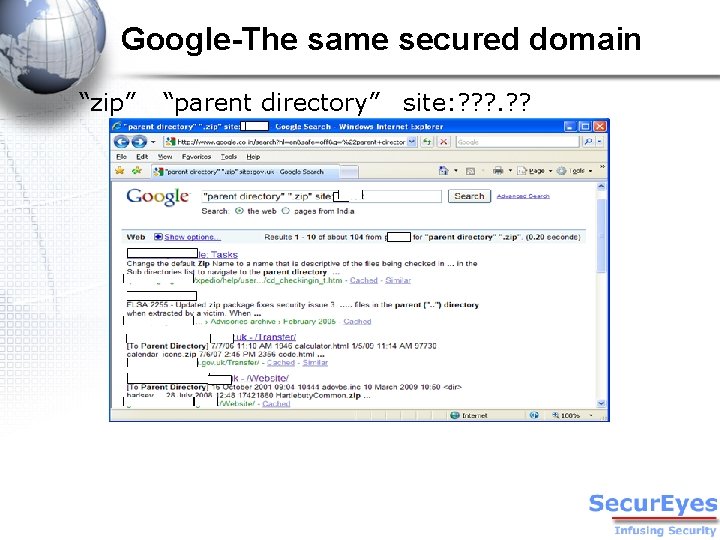
Google-The same secured domain “zip” “parent directory” site: ? ? ?

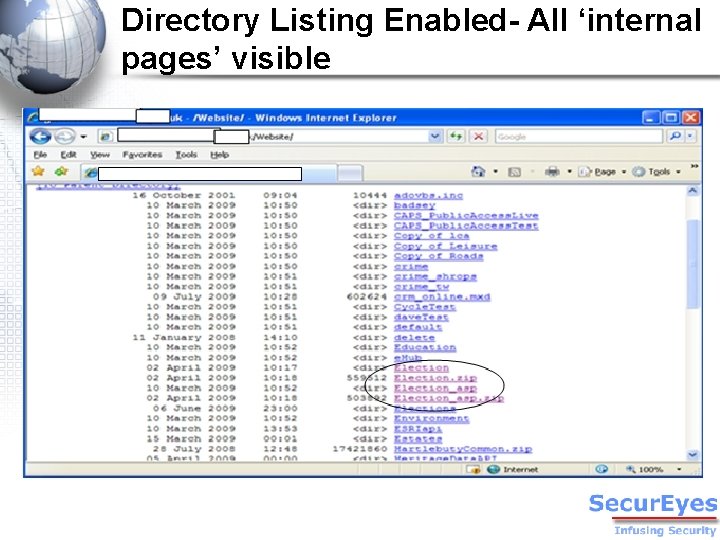
Directory Listing Enabled- All ‘internal pages’ visible

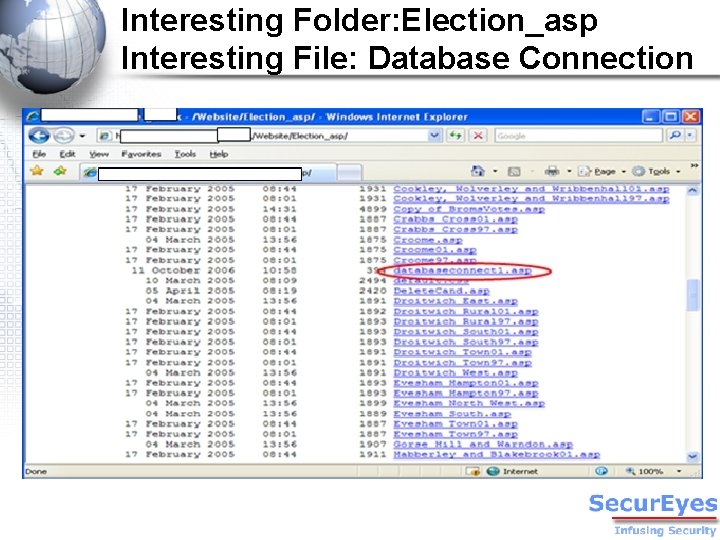
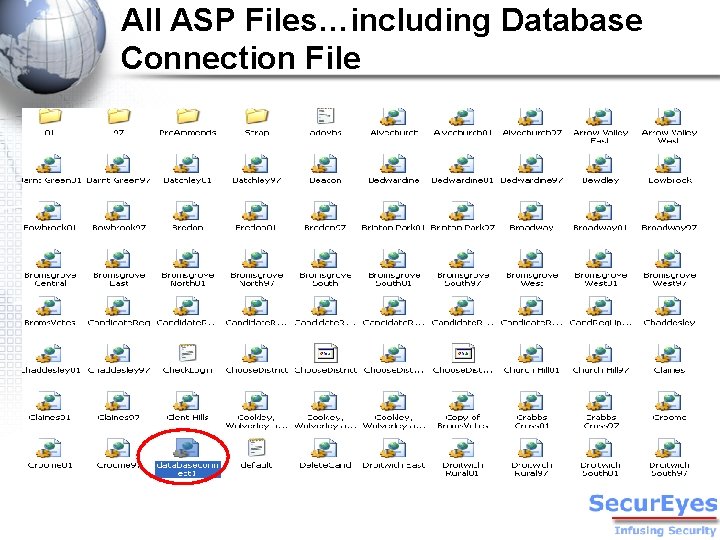
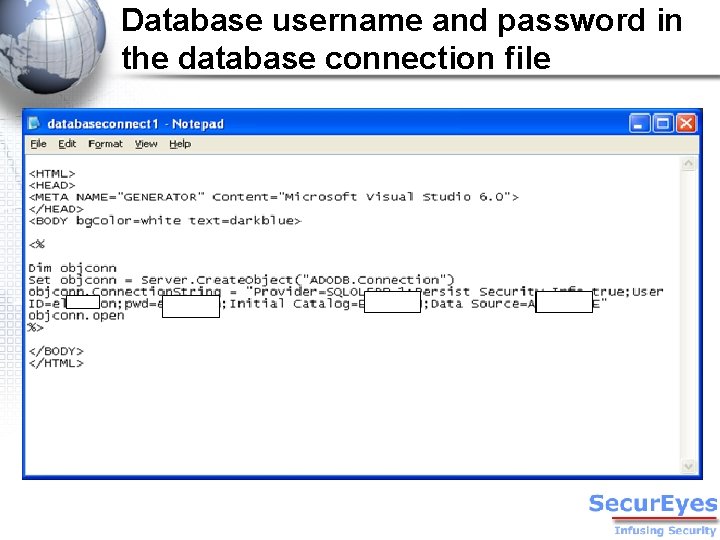
Interesting Folder: Election_asp Interesting File: Database Connection

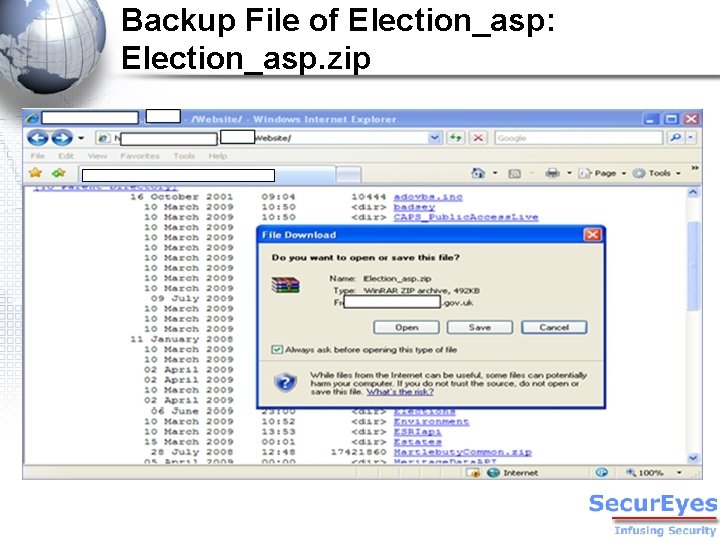
Backup File of Election_asp: Election_asp. zip

All ASP Files…including Database Connection File

Database username and password in the database connection file

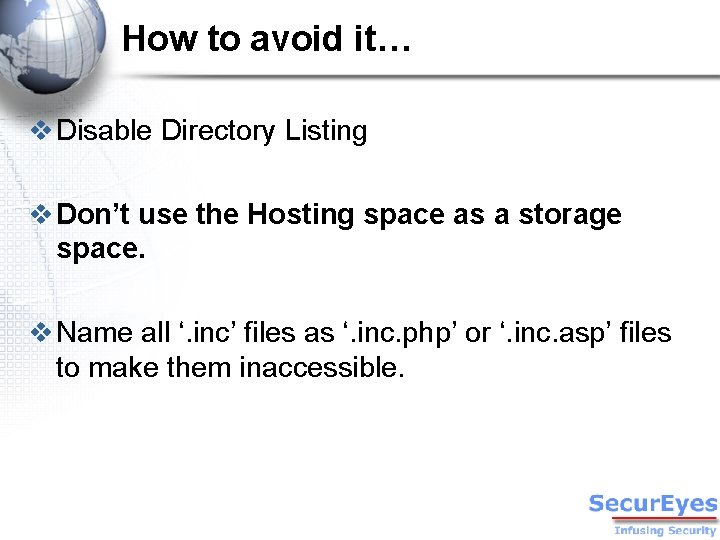
How to avoid it… v Disable Directory Listing v Don’t use the Hosting space as a storage space. v Name all ‘. inc’ files as ‘. inc. php’ or ‘. inc. asp’ files to make them inaccessible.

The Dirty Download Page v Better known as ‘Insecure Direct Object Ref. ’ v Paper in December 2007: http: //secureyes. net/downloads/Source_Code_Discl osure_over_HTTP. pdf v Many white hats have contacted me regarding it. v Translated into Spanish- which is flattering and scary v Not the target audience.

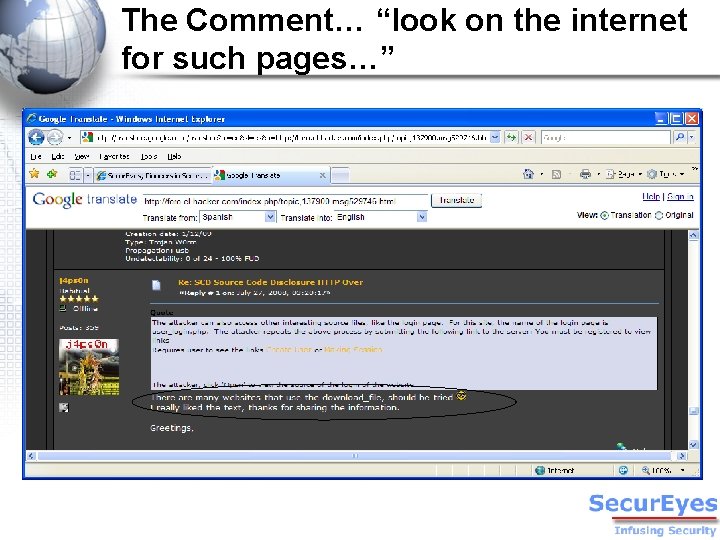
The Comment… “look on the internet for such pages…”

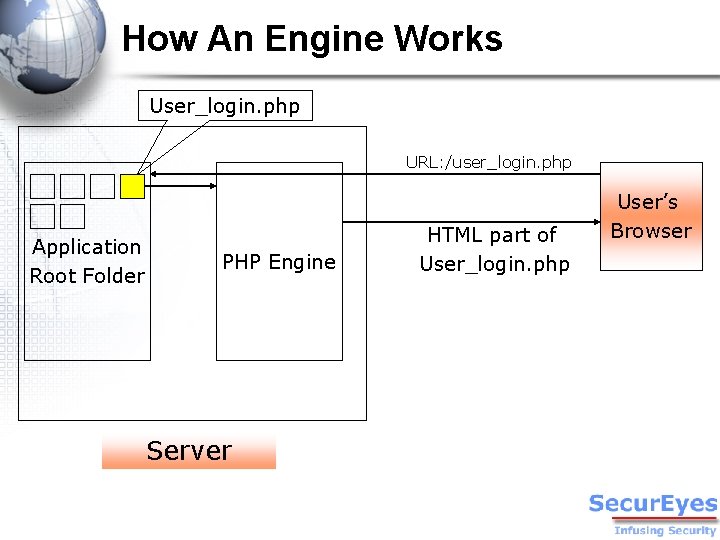
How An Engine Works User_login. php URL: /user_login. php Application Root Folder PHP Engine Server HTML part of User_login. php User’s Browser

The site’s root folder

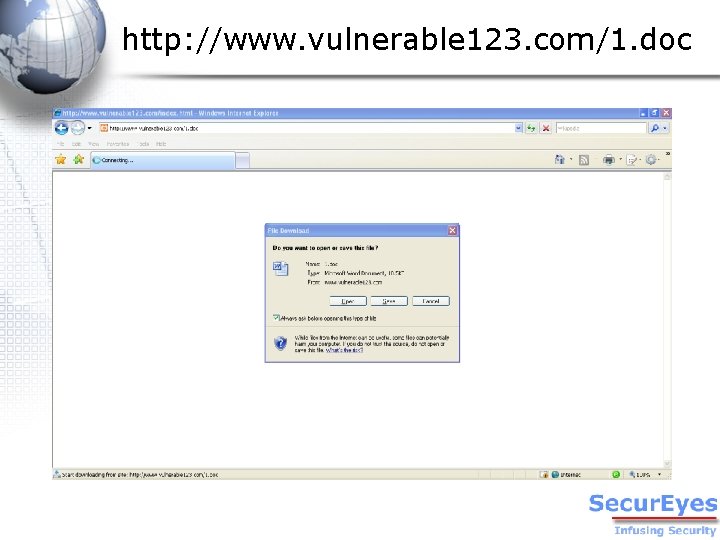
http: //www. vulnerable 123. com/1. doc

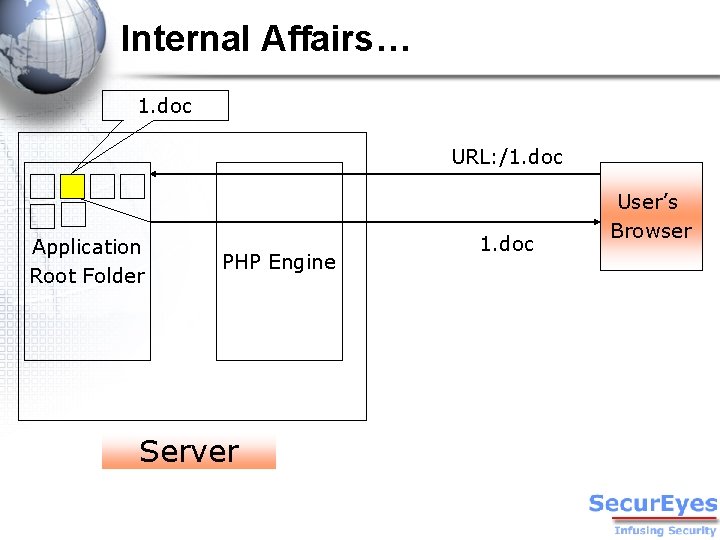
Internal Affairs… 1. doc URL: /1. doc Application Root Folder PHP Engine Server 1. doc User’s Browser

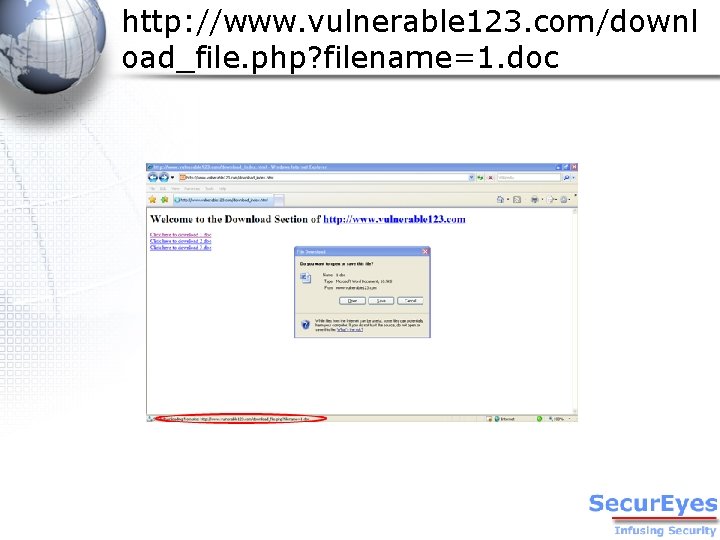
The Other Method… Stream the static content files through a dynamic page: 1) Filename passed as a parameter to the dynamic page- hereby called the ‘download’ page. 2) The download page looks for the file in the hosting folder 3) And upon finding it, streams it to the user’s browser.

http: //www. vulnerable 123. com/downl oad_file. php? filename=1. doc

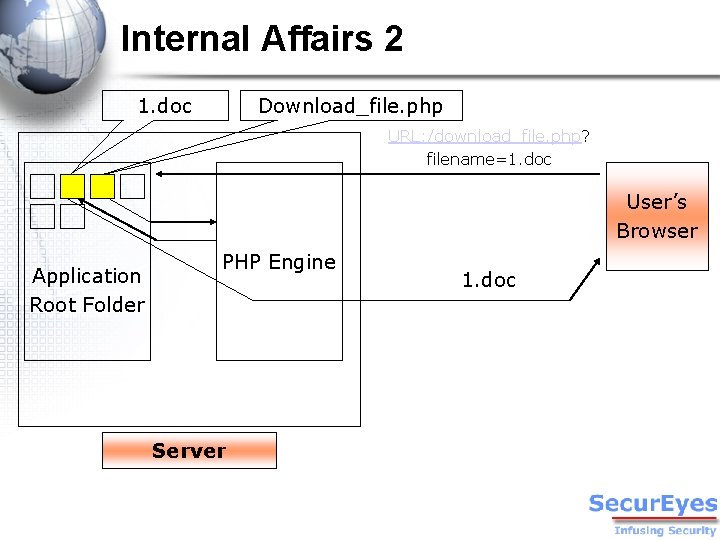
Internal Affairs 2 1. doc Download_file. php URL: /download_file. php? filename=1. doc User’s Browser Application Root Folder PHP Engine Server 1. doc

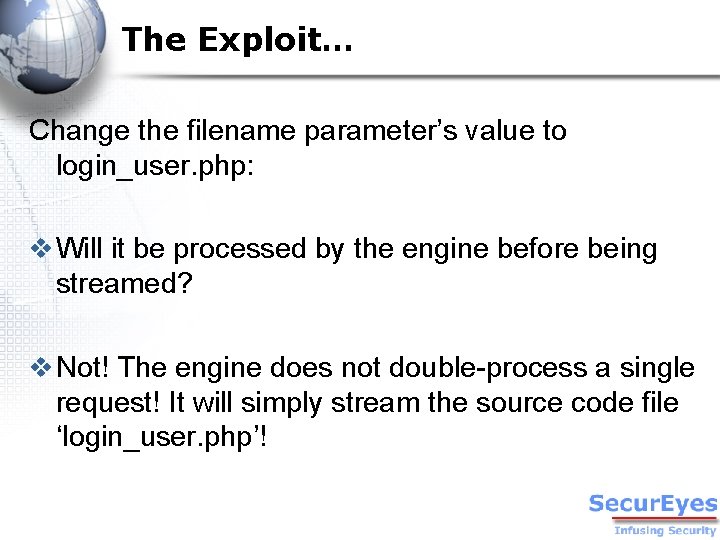
The Exploit… Change the filename parameter’s value to login_user. php: v Will it be processed by the engine before being streamed? v Not! The engine does not double-process a single request! It will simply stream the source code file ‘login_user. php’!

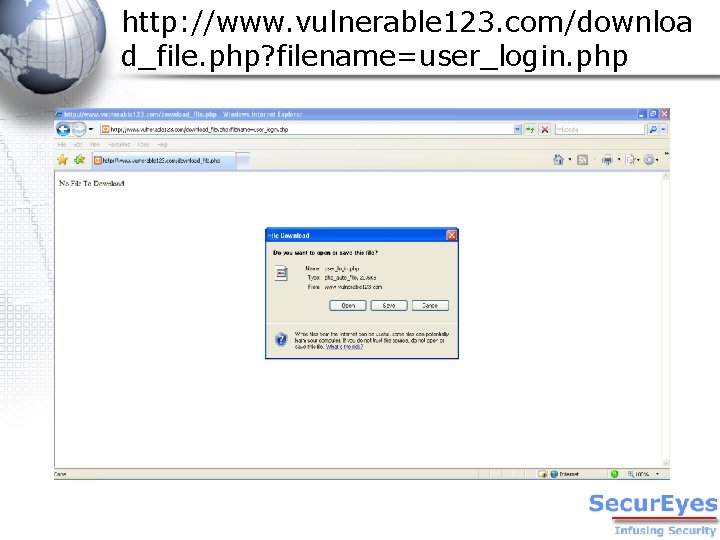
http: //www. vulnerable 123. com/downloa d_file. php? filename=user_login. php

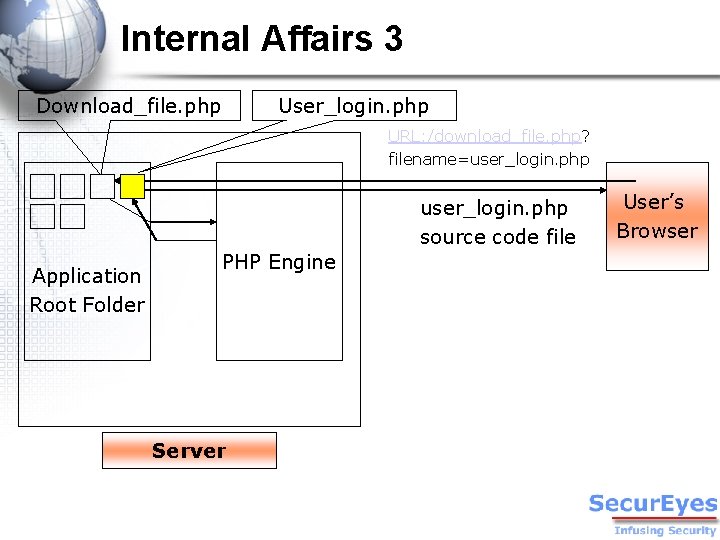
Internal Affairs 3 Download_file. php User_login. php URL: /download_file. php? filename=user_login. php source code file Application Root Folder PHP Engine Server User’s Browser

Google A URL which contains: v A Dynamic Page extension. ext: php OR ext: jsp OR ext: aspx v A Static File extension in the URL (somewhere): inurl: doc OR inurl: pdf OR inurl: xls OR inurl: txt OR inurl: ppt OR inurl: htm

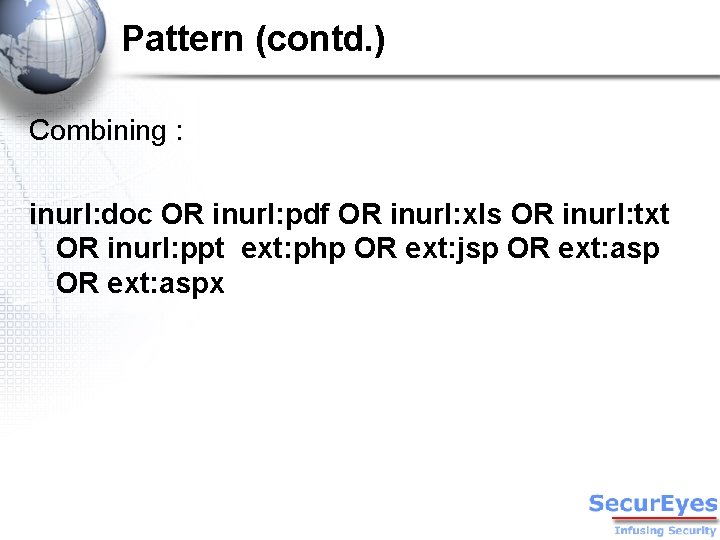
Pattern (contd. ) Combining : inurl: doc OR inurl: pdf OR inurl: xls OR inurl: txt OR inurl: ppt ext: php OR ext: jsp OR ext: aspx

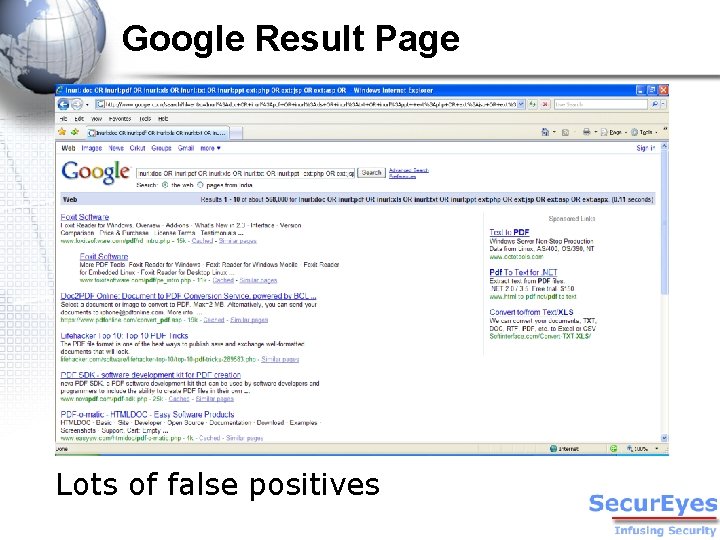
Google Result Page Lots of false positives

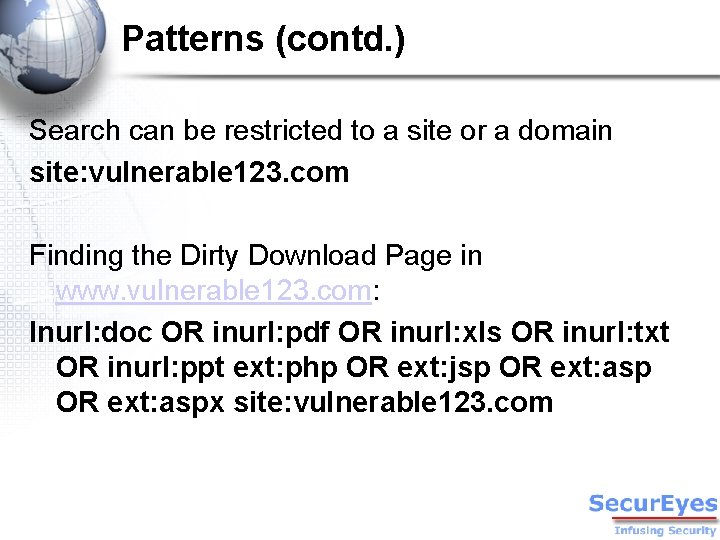
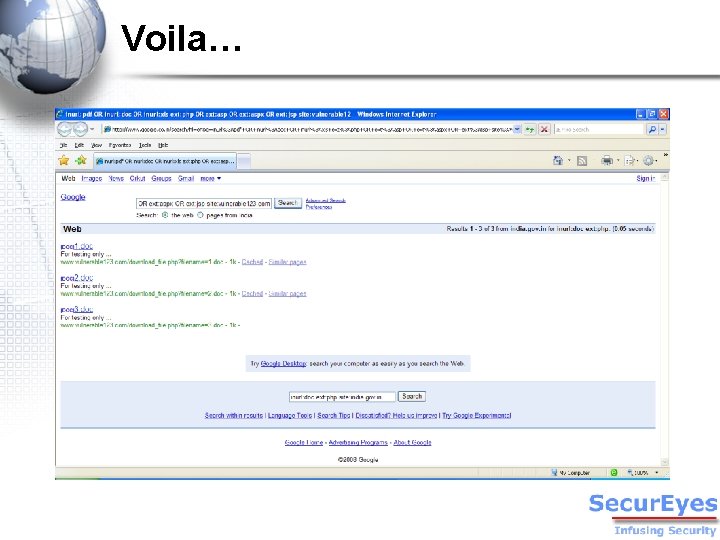
Patterns (contd. ) Search can be restricted to a site or a domain site: vulnerable 123. com Finding the Dirty Download Page in www. vulnerable 123. com: Inurl: doc OR inurl: pdf OR inurl: xls OR inurl: txt OR inurl: ppt ext: php OR ext: jsp OR ext: aspx site: vulnerable 123. com

Voila…

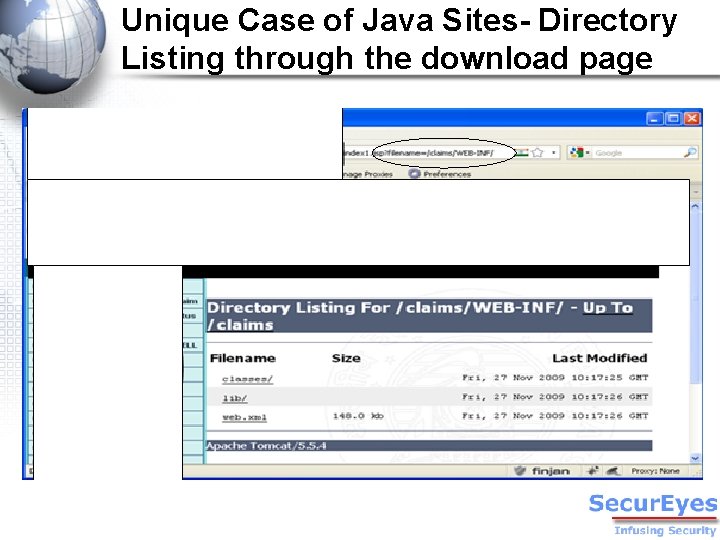
Unique Case of Java Sites- Directory Listing through the download page

Recommended Resolutions v Indirectly refer internal objects. v For example, index the downloadable files, and pass index numbers instead of file names. v File Extensions Validations can be bypassed: Null Byte Injection
![v Contact me anant kochharatsecureyesdotnet v Contact me: anant. kochhar[at]secureyes[dot]net](https://slidetodoc.com/presentation_image/b0a1bc52a8c0414d3da7a1fc60708aad/image-39.jpg)
v Contact me: anant. kochhar[at]secureyes[dot]net