Rethinking vulnerability prioritization in the modern threat landscape

Rethinking vulnerability prioritization in the modern threat landscape James Smith Senior Security Engineer for Tenable 1
Agenda NVD, FIRST, CVSS, Historical and other Vulnerability Trends Acronyms The Real World Make Things Smarter 2
Agenda NVD, FIRST, CVSS, Historical and other Vulnerability Trends Acronyms The Real World Make Things Smarter 3
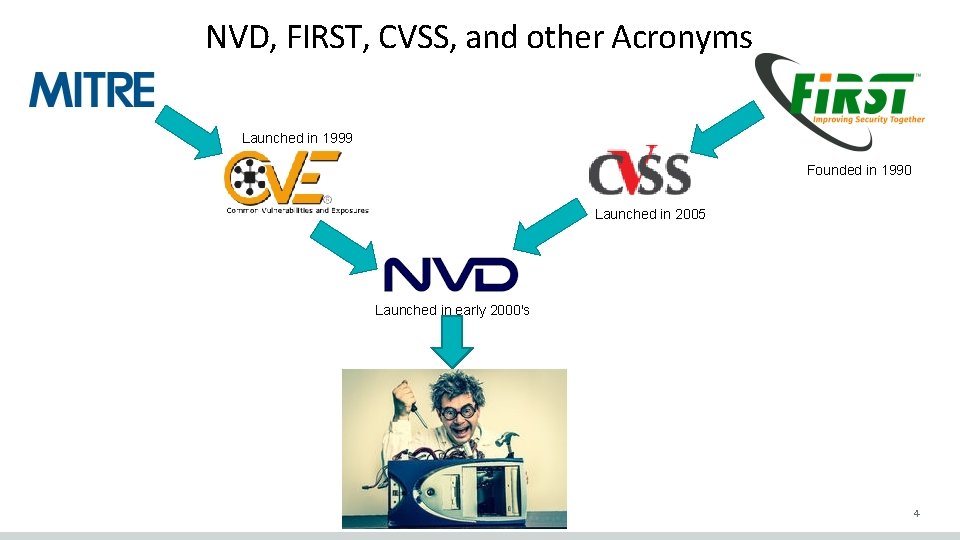
NVD, FIRST, CVSS, and other Acronyms Launched in 1999 Founded in 1990 Launched in 2005 Launched in early 2000's 4
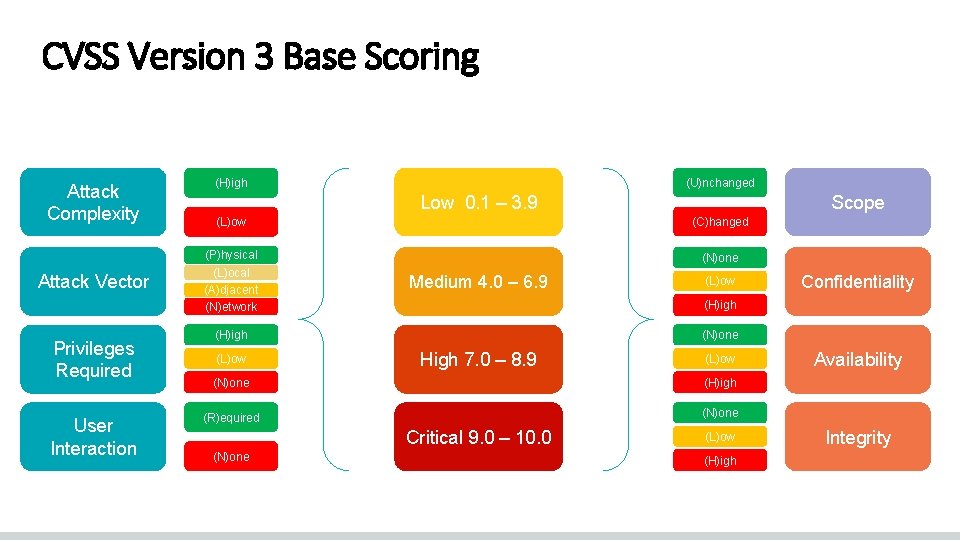
CVSS Version 3 Base Scoring Attack Complexity Attack Vector Privileges Required User Interaction (U)nchanged (H)igh Low 0. 1 – 3. 9 Scope (L)ow (C)hanged (P)hysical (L)ocal (A)djacent (N)etwork (N)one Medium 4. 0 – 6. 9 (N)one High 7. 0 – 8. 9 (L)ow (N)one (H)igh (R)equired (N)one Critical 9. 0 – 10. 0 (N)one Confidentiality (H)igh (L)ow (H)igh Availability Integrity
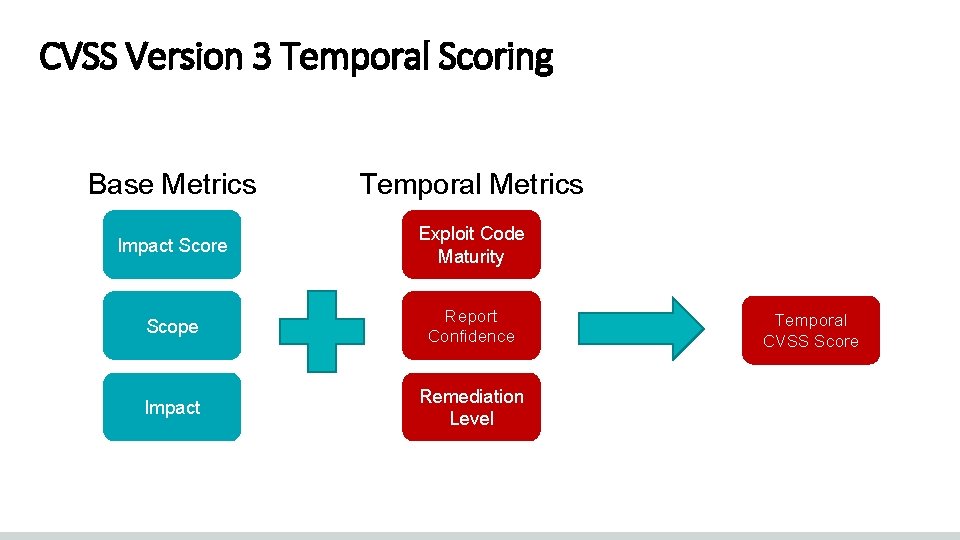
CVSS Version 3 Temporal Scoring Base Metrics Temporal Metrics Impact Score Exploit Code Maturity Scope Report Confidence Impact Remediation Level Temporal CVSS Score
Agenda NVD, FIRST, CVSS, Historical and other Vulnerability Trends Acronyms The Real World Make Things Smarter 7
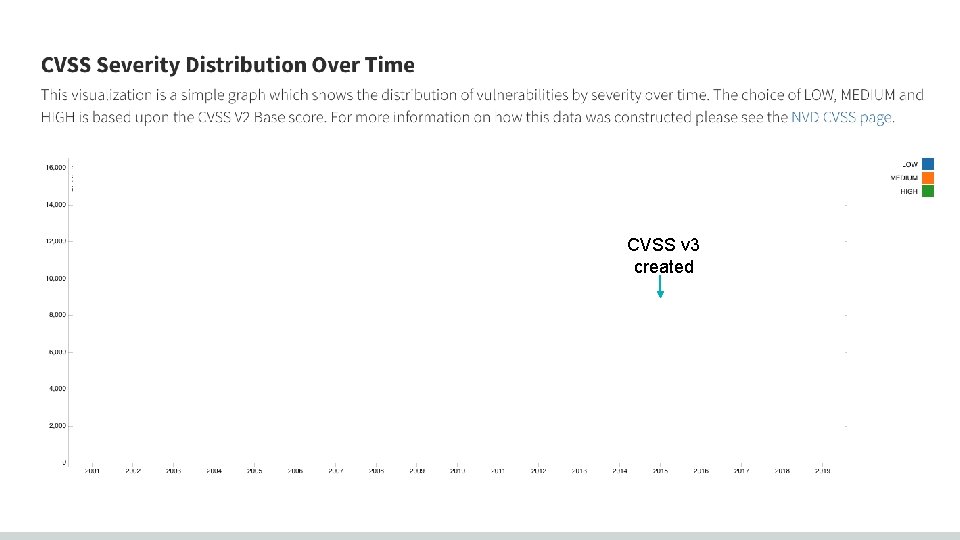
CVSS v 3 created
Agenda NVD, FIRST, CVSS, Historical and other Vulnerability Trends Acronyms The Real World Make Things Smarter 9

The Real World 10
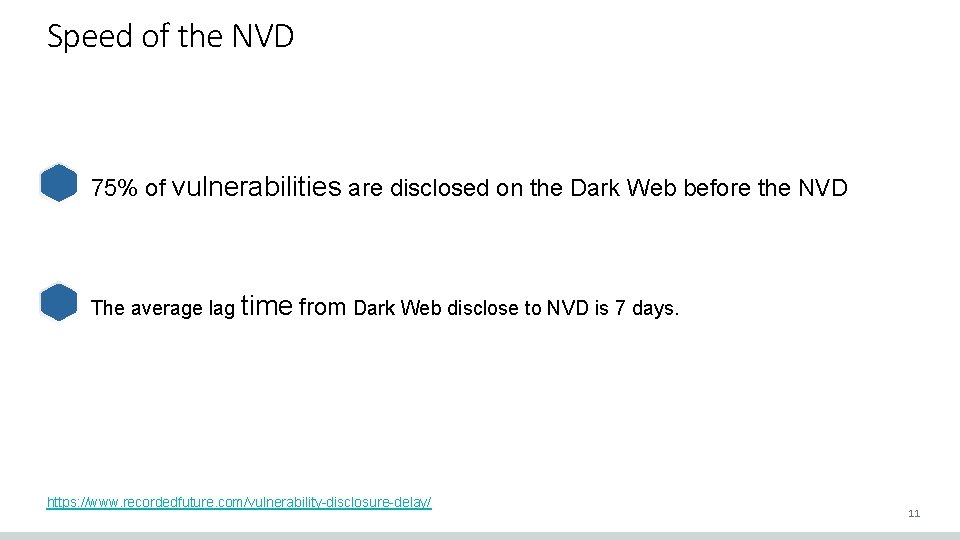
Speed of the NVD 75% of vulnerabilities are disclosed on the Dark Web before the NVD The average lag time from Dark Web disclose to NVD is 7 days. https: //www. recordedfuture. com/vulnerability-disclosure-delay/ 11
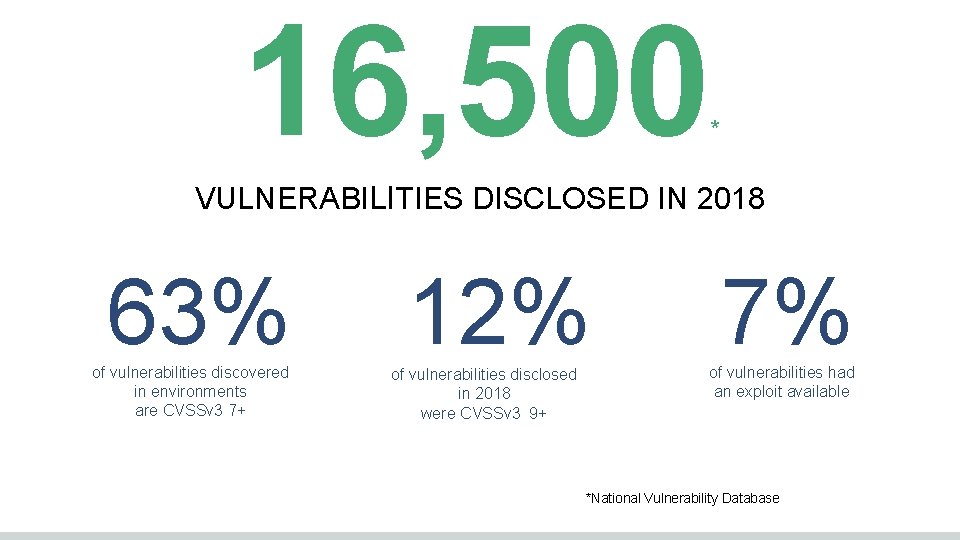
16, 500 * VULNERABILITIES DISCLOSED IN 2018 63% of vulnerabilities discovered in environments are CVSSv 3 7+ 12% of vulnerabilities disclosed in 2018 were CVSSv 3 9+ 7% of vulnerabilities had an exploit available *National Vulnerability Database
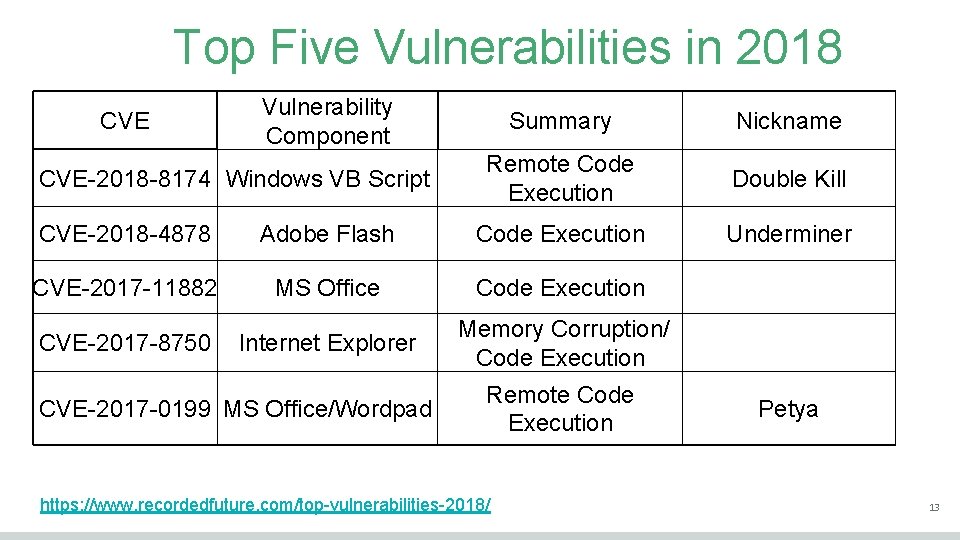
Top Five Vulnerabilities in 2018 CVE Vulnerability Component CVE-2018 -8174 Windows VB Script Summary Nickname Remote Code Execution Double Kill Underminer CVE-2018 -4878 Adobe Flash Code Execution CVE-2017 -11882 MS Office Code Execution CVE-2017 -8750 Internet Explorer Memory Corruption/ Code Execution CVE-2017 -0199 MS Office/Wordpad Remote Code Execution https: //www. recordedfuture. com/top-vulnerabilities-2018/ Petya 13
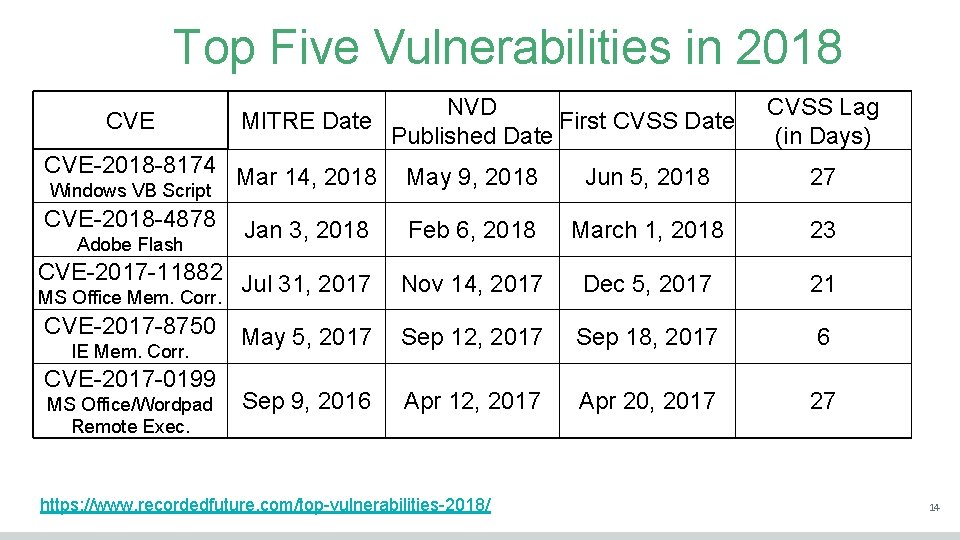
Top Five Vulnerabilities in 2018 CVE NVD MITRE Date First CVSS Date Published Date CVSS Lag (in Days) CVE-2018 -8174 Mar 14, 2018 May 9, 2018 Jun 5, 2018 27 CVE-2018 -4878 Feb 6, 2018 March 1, 2018 23 CVE-2017 -11882 Jul 31, 2017 Nov 14, 2017 Dec 5, 2017 21 CVE-2017 -8750 May 5, 2017 Sep 12, 2017 Sep 18, 2017 6 Sep 9, 2016 Apr 12, 2017 Apr 20, 2017 27 Windows VB Script Adobe Flash Jan 3, 2018 MS Office Mem. Corr. IE Mem. Corr. CVE-2017 -0199 MS Office/Wordpad Remote Exec. https: //www. recordedfuture. com/top-vulnerabilities-2018/ 14
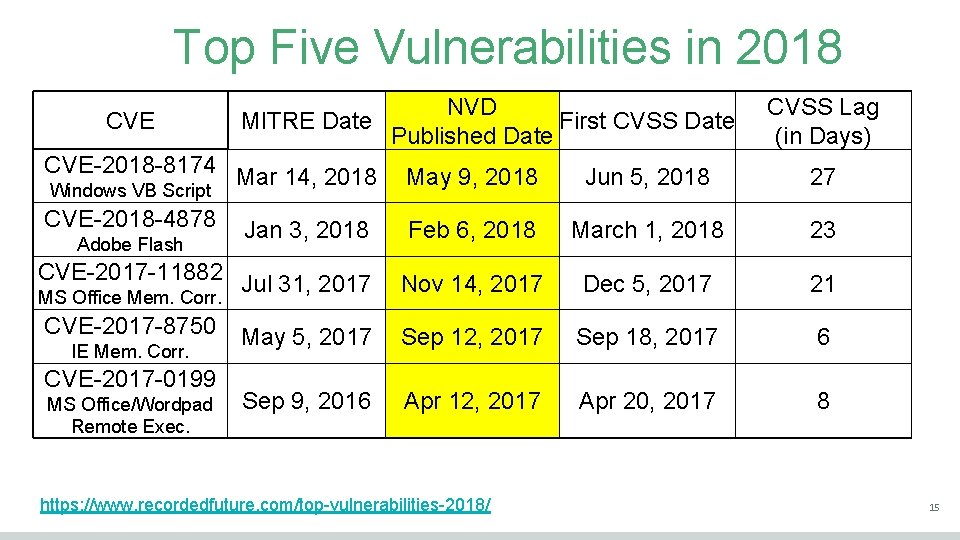
Top Five Vulnerabilities in 2018 CVE NVD MITRE Date First CVSS Date Published Date CVSS Lag (in Days) CVE-2018 -8174 Mar 14, 2018 May 9, 2018 Jun 5, 2018 27 CVE-2018 -4878 Feb 6, 2018 March 1, 2018 23 CVE-2017 -11882 Jul 31, 2017 Nov 14, 2017 Dec 5, 2017 21 CVE-2017 -8750 May 5, 2017 Sep 12, 2017 Sep 18, 2017 6 Sep 9, 2016 Apr 12, 2017 Apr 20, 2017 8 Windows VB Script Adobe Flash Jan 3, 2018 MS Office Mem. Corr. IE Mem. Corr. CVE-2017 -0199 MS Office/Wordpad Remote Exec. https: //www. recordedfuture. com/top-vulnerabilities-2018/ 15
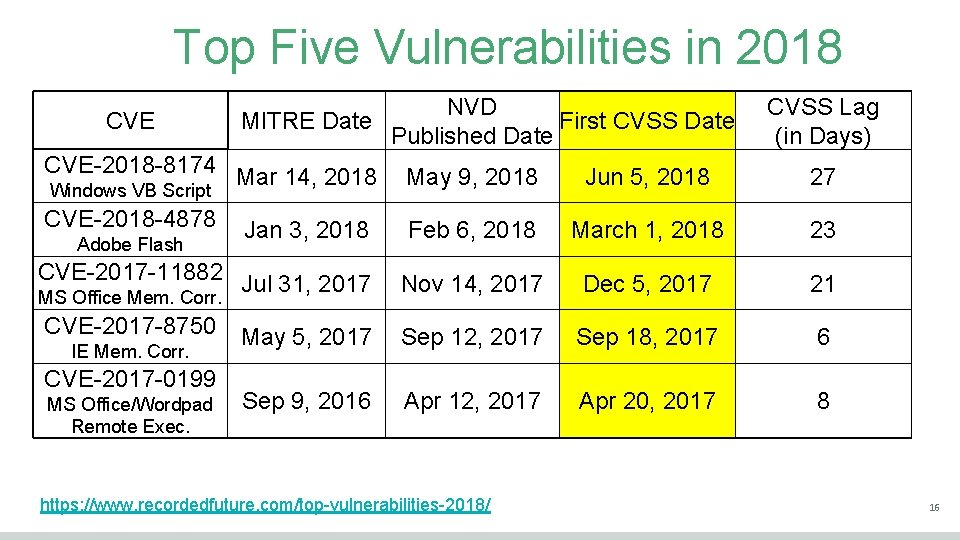
Top Five Vulnerabilities in 2018 CVE NVD MITRE Date First CVSS Date Published Date CVSS Lag (in Days) CVE-2018 -8174 Mar 14, 2018 May 9, 2018 Jun 5, 2018 27 CVE-2018 -4878 Feb 6, 2018 March 1, 2018 23 CVE-2017 -11882 Jul 31, 2017 Nov 14, 2017 Dec 5, 2017 21 CVE-2017 -8750 May 5, 2017 Sep 12, 2017 Sep 18, 2017 6 Sep 9, 2016 Apr 12, 2017 Apr 20, 2017 8 Windows VB Script Adobe Flash Jan 3, 2018 MS Office Mem. Corr. IE Mem. Corr. CVE-2017 -0199 MS Office/Wordpad Remote Exec. https: //www. recordedfuture. com/top-vulnerabilities-2018/ 16
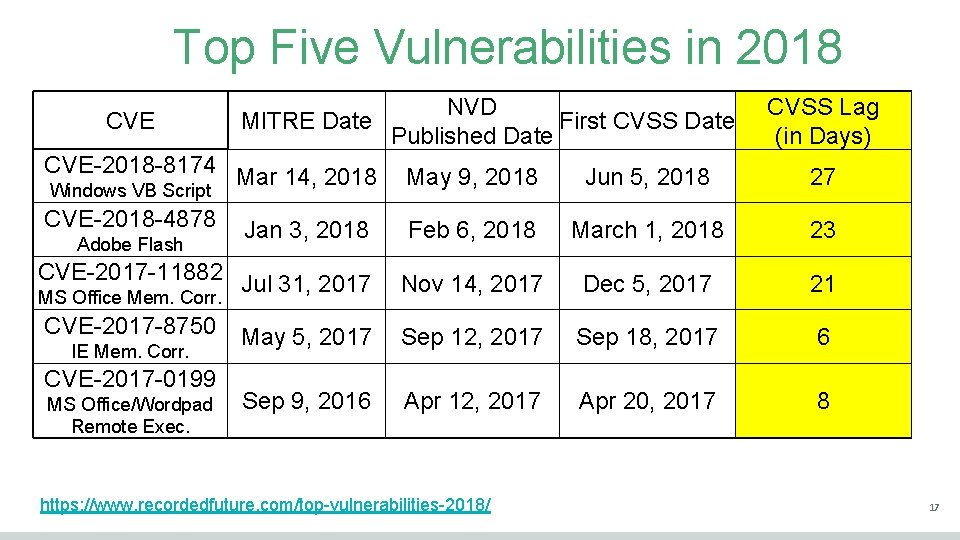
Top Five Vulnerabilities in 2018 CVE NVD MITRE Date First CVSS Date Published Date CVSS Lag (in Days) CVE-2018 -8174 Mar 14, 2018 May 9, 2018 Jun 5, 2018 27 CVE-2018 -4878 Feb 6, 2018 March 1, 2018 23 CVE-2017 -11882 Jul 31, 2017 Nov 14, 2017 Dec 5, 2017 21 CVE-2017 -8750 May 5, 2017 Sep 12, 2017 Sep 18, 2017 6 Sep 9, 2016 Apr 12, 2017 Apr 20, 2017 8 Windows VB Script Adobe Flash Jan 3, 2018 MS Office Mem. Corr. IE Mem. Corr. CVE-2017 -0199 MS Office/Wordpad Remote Exec. https: //www. recordedfuture. com/top-vulnerabilities-2018/ 17
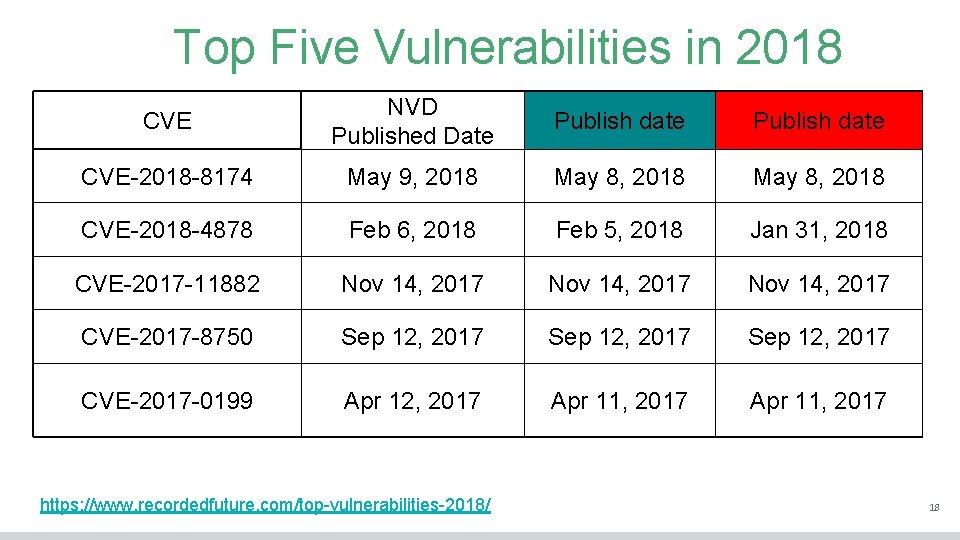
Top Five Vulnerabilities in 2018 CVE NVD Published Date Publish date CVE-2018 -8174 May 9, 2018 May 8, 2018 CVE-2018 -4878 Feb 6, 2018 Feb 5, 2018 Jan 31, 2018 CVE-2017 -11882 Nov 14, 2017 CVE-2017 -8750 Sep 12, 2017 CVE-2017 -0199 Apr 12, 2017 Apr 11, 2017 https: //www. recordedfuture. com/top-vulnerabilities-2018/ 18
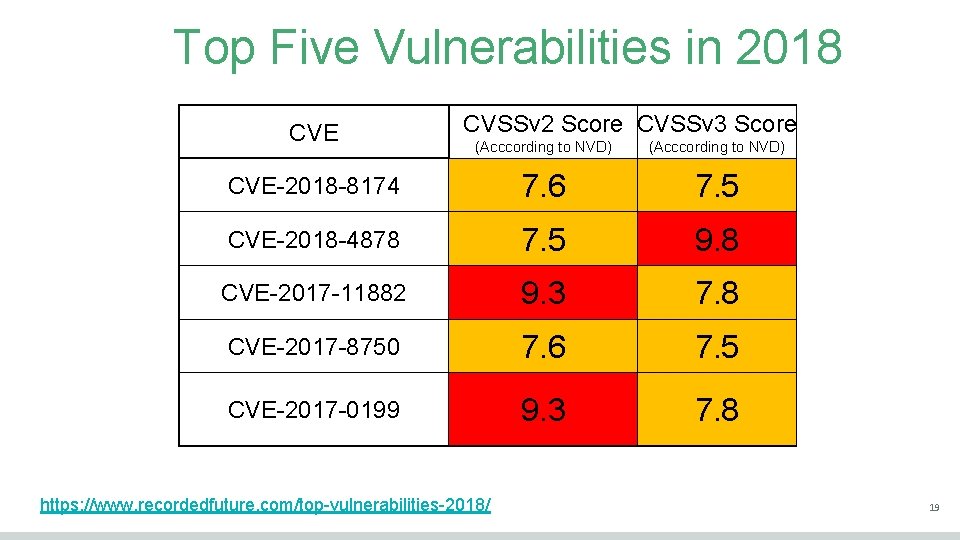
Top Five Vulnerabilities in 2018 CVE CVSSv 2 Score CVSSv 3 Score (Acccording to NVD) CVE-2018 -8174 7. 6 7. 5 CVE-2018 -4878 7. 5 9. 8 CVE-2017 -11882 9. 3 7. 8 CVE-2017 -8750 7. 6 7. 5 CVE-2017 -0199 9. 3 7. 8 https: //www. recordedfuture. com/top-vulnerabilities-2018/ 19
Agenda NVD, FIRST, CVSS, Historical and other Vulnerability Trends Acronyms The Real World Make Things Smarter 20

How Do We Make Prioritization Smarter? We need a process to learn from experience with respect to vulnerability prioritization and measure that performance to ensure we're improving based on that experience. Tom Mitchell, 1997, author of Machine Learning https: //www. amazon. ca/Machine-Learning-Thomas-Mitchell/dp/0070428077 How do we apply machine learning to vulnerability prioritization? 21

Time For A Video! 22

predictive prioritization of vulnerabilities • Data science approach to Vulnerability Management • Focus time and resources 23
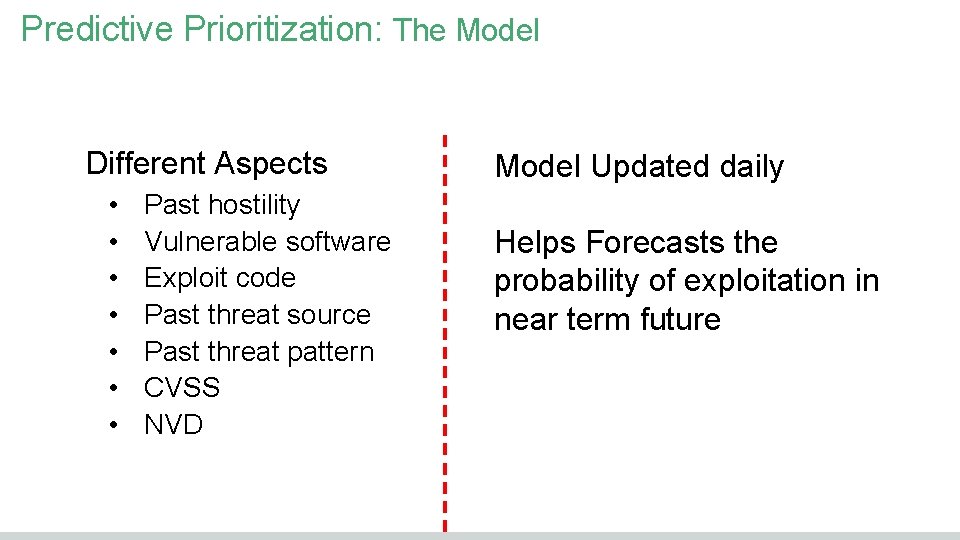
Predictive Prioritization: The Model Different Aspects • • Past hostility Vulnerable software Exploit code Past threat source Past threat pattern CVSS NVD Model Updated daily Helps Forecasts the probability of exploitation in near term future
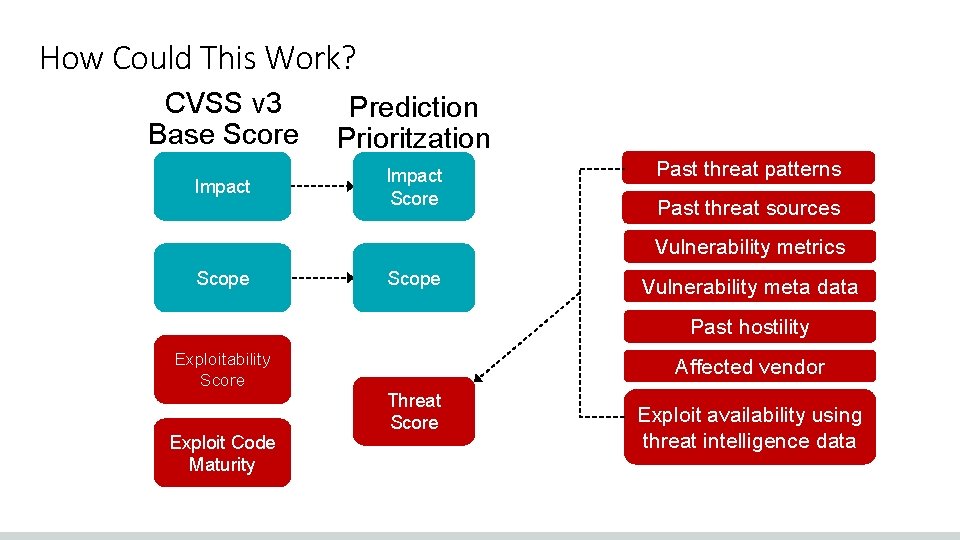
How Could This Work? CVSS v 3 Base Score Prediction Prioritzation Impact Score Past threat patterns Past threat sources Vulnerability metrics Scope Vulnerability meta data Past hostility Exploitability Score Exploit Code Maturity Affected vendor Threat Score Exploit availability using threat intelligence data
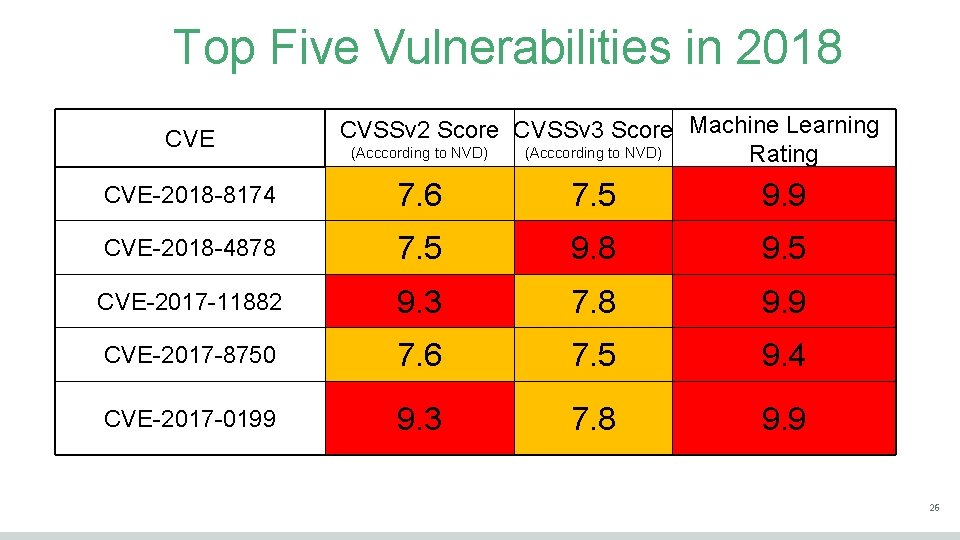
Top Five Vulnerabilities in 2018 CVE CVSSv 2 Score CVSSv 3 Score Machine Learning (Acccording to NVD) Rating CVE-2018 -8174 7. 6 7. 5 9. 9 CVE-2018 -4878 7. 5 9. 8 9. 5 CVE-2017 -11882 9. 3 7. 8 9. 9 CVE-2017 -8750 7. 6 7. 5 9. 4 CVE-2017 -0199 9. 3 7. 8 9. 9 26
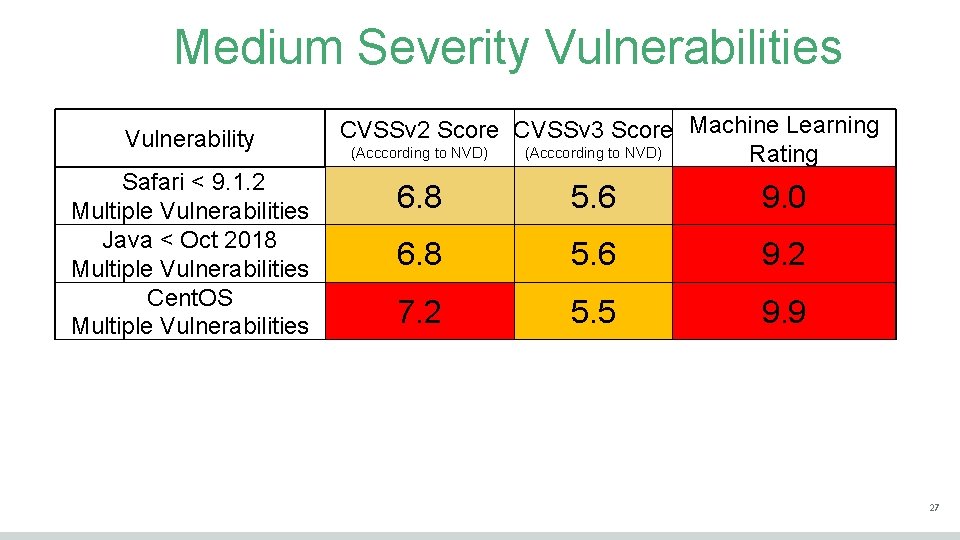
Medium Severity Vulnerabilities Vulnerability Safari < 9. 1. 2 Multiple Vulnerabilities Java < Oct 2018 Multiple Vulnerabilities Cent. OS Multiple Vulnerabilities CVSSv 2 Score CVSSv 3 Score Machine Learning (Acccording to NVD) Rating 6. 8 5. 6 9. 0 6. 8 5. 6 9. 2 7. 2 5. 5 9. 9 27
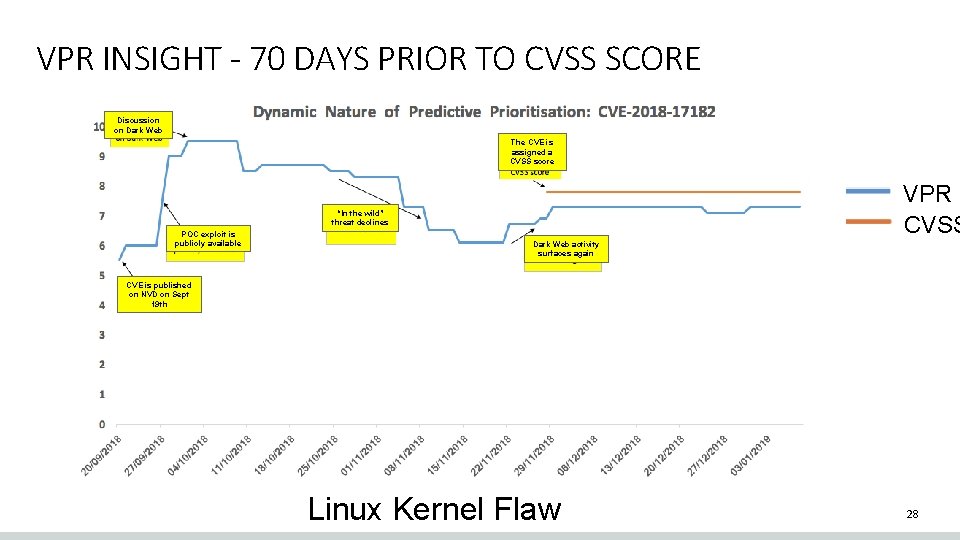
VPR INSIGHT - 70 DAYS PRIOR TO CVSS SCORE Discussion on Dark Web The CVE is assigned a CVSS score VPR CVSS “In the wild” threat declines POC exploit is publicly available Dark Web activity surfaces again CVE is published on NVD on Sept 19 th Linux Kernel Flaw 28
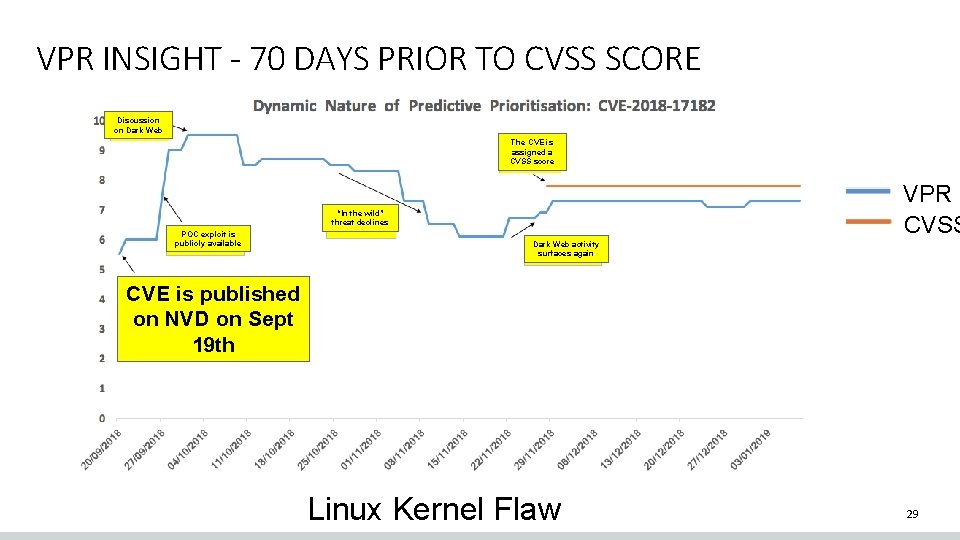
VPR INSIGHT - 70 DAYS PRIOR TO CVSS SCORE Discussion on Dark Web The CVE is assigned a CVSS score VPR CVSS “In the wild” threat declines POC exploit is publicly available Dark Web activity surfaces again CVE is published on NVD on Sept 19 th Linux Kernel Flaw 29
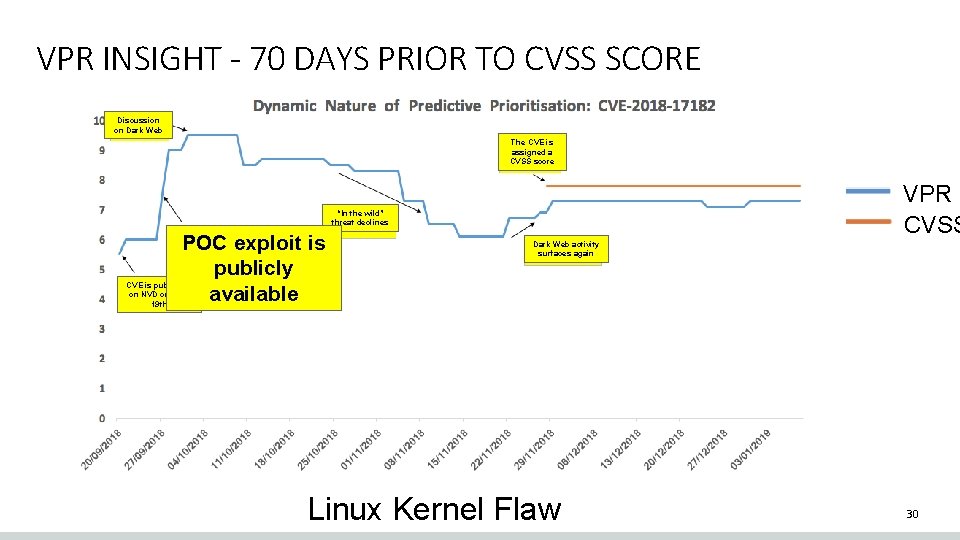
VPR INSIGHT - 70 DAYS PRIOR TO CVSS SCORE Discussion on Dark Web The CVE is assigned a CVSS score VPR CVSS “In the wild” threat declines POC exploit is publicly available Dark Web activity surfaces again CVE is published on NVD on Sept 19 th Linux Kernel Flaw 30
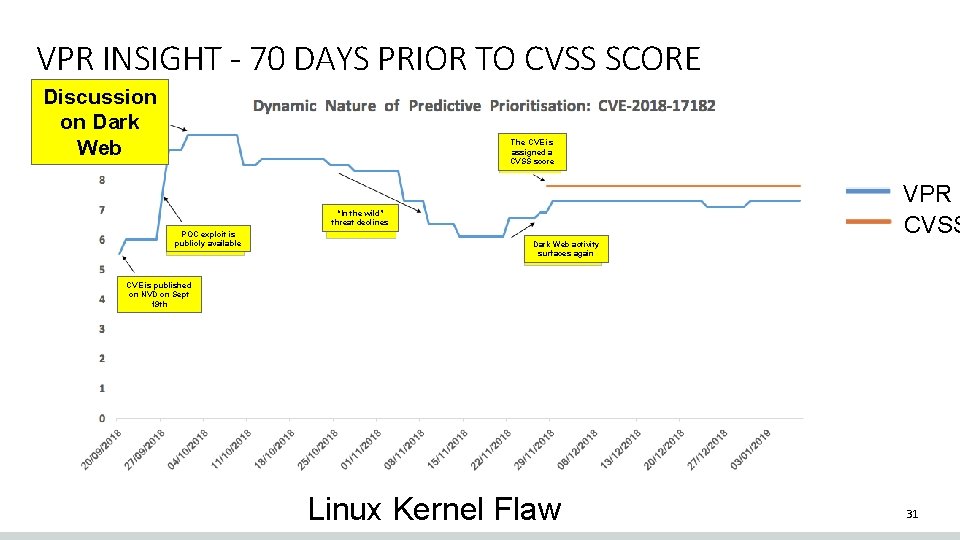
VPR INSIGHT - 70 DAYS PRIOR TO CVSS SCORE Discussion on Dark Web The CVE is assigned a CVSS score VPR CVSS “In the wild” threat declines POC exploit is publicly available Dark Web activity surfaces again CVE is published on NVD on Sept 19 th Linux Kernel Flaw 31
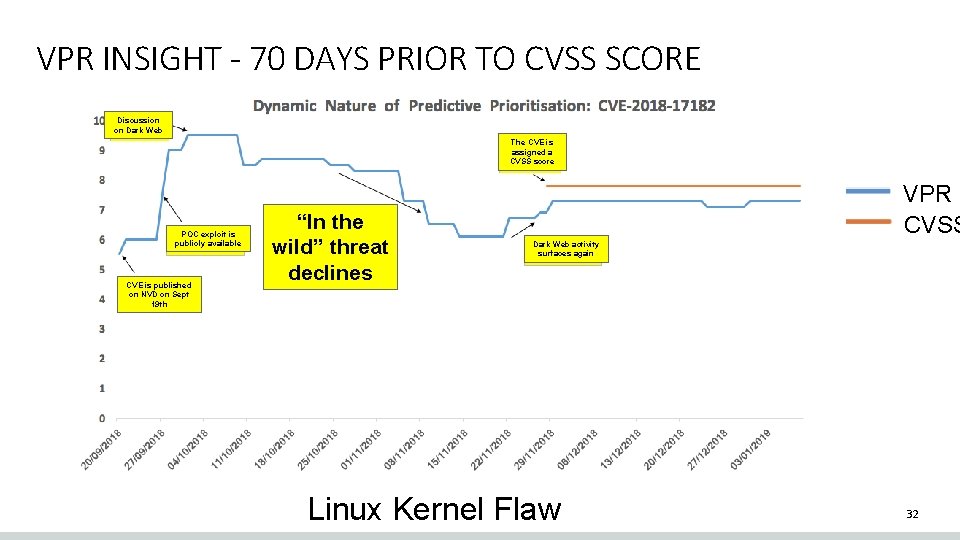
VPR INSIGHT - 70 DAYS PRIOR TO CVSS SCORE Discussion on Dark Web The CVE is assigned a CVSS score POC exploit is publicly available CVE is published on NVD on Sept 19 th “In the wild” threat declines VPR CVSS Dark Web activity surfaces again Linux Kernel Flaw 32
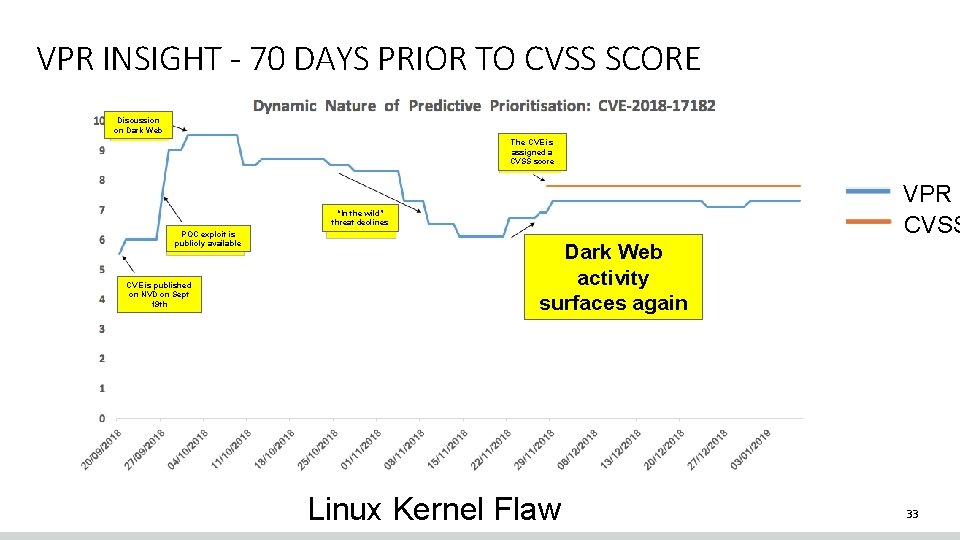
VPR INSIGHT - 70 DAYS PRIOR TO CVSS SCORE Discussion on Dark Web The CVE is assigned a CVSS score VPR CVSS “In the wild” threat declines POC exploit is publicly available CVE is published on NVD on Sept 19 th Dark Web activity surfaces again Linux Kernel Flaw 33
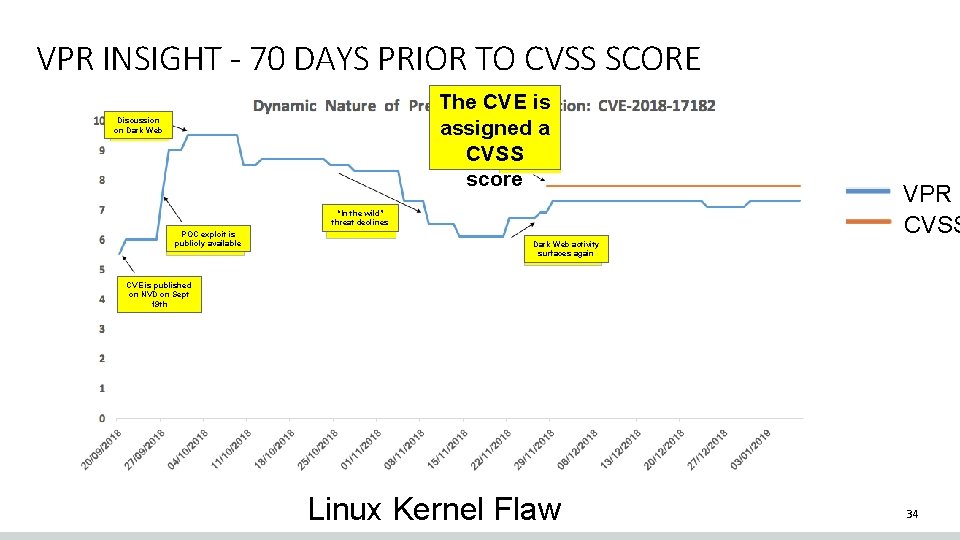
VPR INSIGHT - 70 DAYS PRIOR TO CVSS SCORE The CVE is assigned a CVSS score Discussion on Dark Web “In the wild” threat declines POC exploit is publicly available VPR CVSS Dark Web activity surfaces again CVE is published on NVD on Sept 19 th Linux Kernel Flaw 34
Agenda NVD, FIRST, CVSS, Historical and other Vulnerability Trends Acronyms The Real World Make Things Smarter 35
- Slides: 35