Rethinking Packet Classification for Global Network View of

Rethinking Packet Classification for Global Network View of Software. Defined Networking Author: Takeru Inoue, Toru Mano, Kimihiro Mizutani, Shin-ichi Minato, Osamu Akashi Conference: 2014 IEEE 22 nd International Conference on Network Protocols Presenter: Chih-Hsun Wang Date: 2015/10/07 Department of Computer Science and Information Engineering National Cheng Kung University, Taiwan R. O. C.
Introduction l l l In software-defined networking, applications are allowed to access a global view of the network. Unlike the conventional classification problem to search for the action taken at a single switch, the global network view requires to identify the network-wide behavior of the packet. Conventional classification methods, however, fail to well support network-wide behaviors, since the search space is complicatedly partitioned due to the combinations. National Cheng Kung University CSIE Computer & Internet Architecture Lab 2
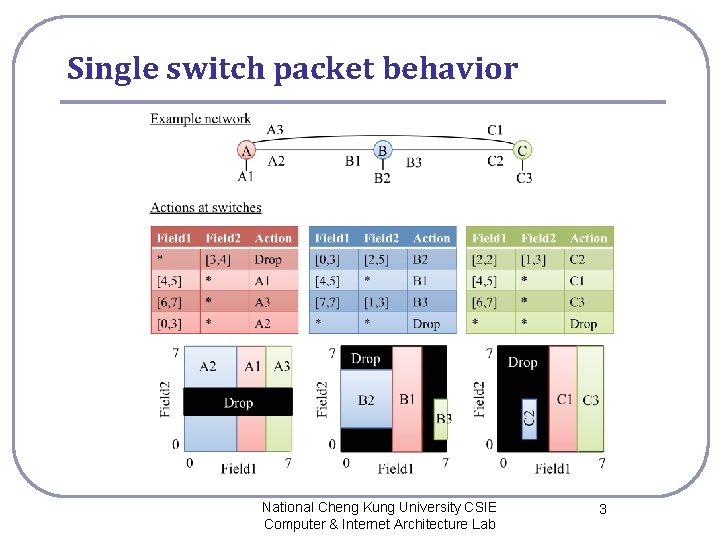
Single switch packet behavior National Cheng Kung University CSIE Computer & Internet Architecture Lab 3

Network-wide packet behavior National Cheng Kung University CSIE Computer & Internet Architecture Lab 4
Binary Decision Diagram l A Binary Decision Diagram (BDD) is a finite DAG with an unique initial node, where • all terminal nodes are labeled with 0 or 1. • all non-terminal nodes are labeled with a Boolean • Variable. Each non-terminal node has exactly two edges from that node to others; one labeled 0 and one labeled 1; represent them as a dashed line and a solid line respectively. National Cheng Kung University CSIE Computer & Internet Architecture Lab 5
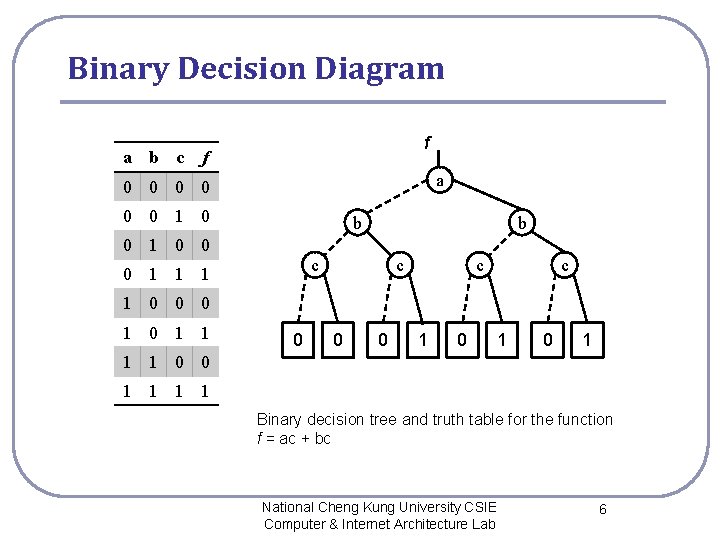
Binary Decision Diagram a b c f f a 0 0 0 1 0 b b 0 1 0 0 c 0 1 1 1 c c c 1 0 0 0 1 0 1 0 1 1 1 0 0 1 1 Binary decision tree and truth table for the function f = ac + bc National Cheng Kung University CSIE Computer & Internet Architecture Lab 6
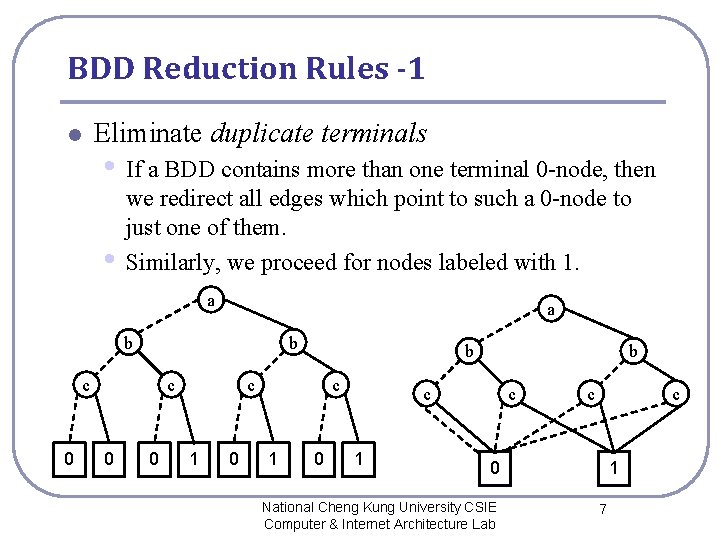
BDD Reduction Rules -1 Eliminate duplicate terminals l • If a BDD contains more than one terminal 0 -node, then • we redirect all edges which point to such a 0 -node to just one of them. Similarly, we proceed for nodes labeled with 1. a a b b c 0 0 b c 1 c c c 0 National Cheng Kung University CSIE Computer & Internet Architecture Lab 1 7
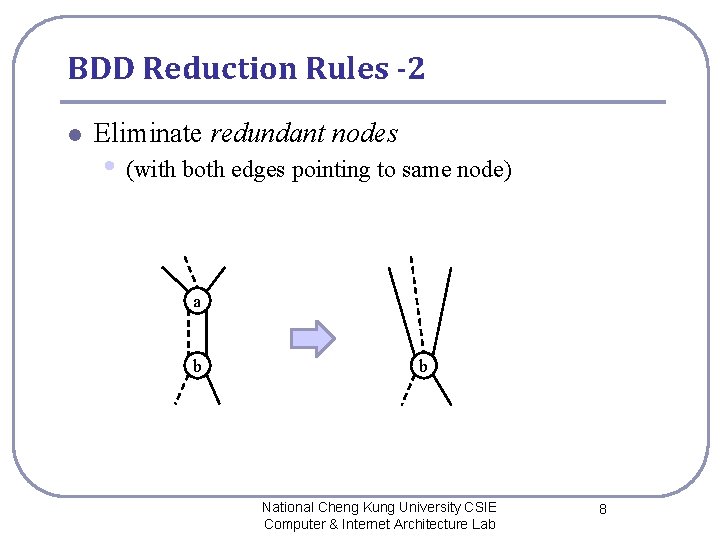
BDD Reduction Rules -2 l Eliminate redundant nodes • (with both edges pointing to same node) a b b National Cheng Kung University CSIE Computer & Internet Architecture Lab 8
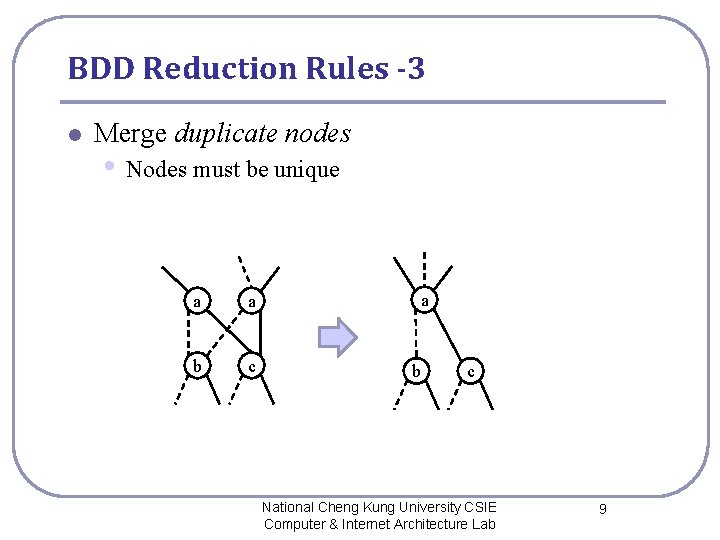
BDD Reduction Rules -3 l Merge duplicate nodes • Nodes must be unique a a b c National Cheng Kung University CSIE Computer & Internet Architecture Lab 9
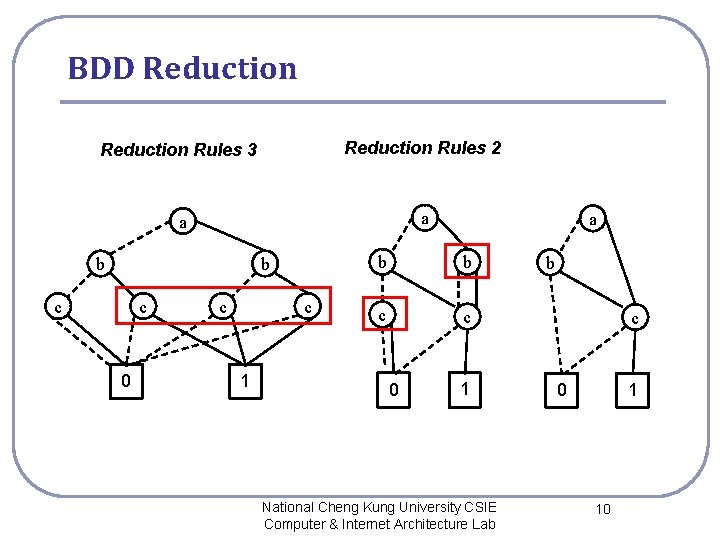
BDD Reduction Rules 3 Reduction Rules 2 a a b b c c 0 c c 1 a b b c c 0 1 National Cheng Kung University CSIE Computer & Internet Architecture Lab b c 1 0 10
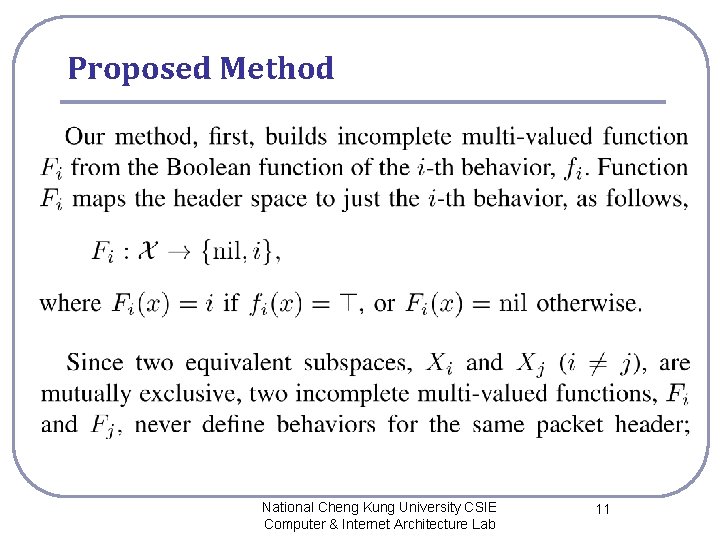
Proposed Method National Cheng Kung University CSIE Computer & Internet Architecture Lab 11
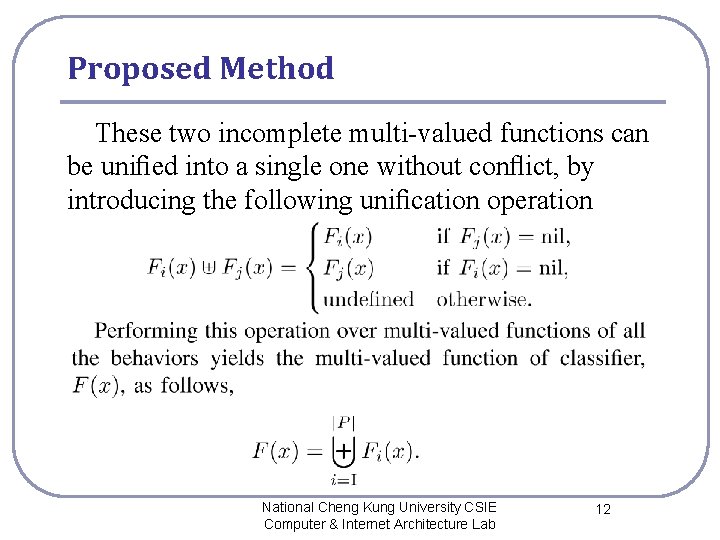
Proposed Method These two incomplete multi-valued functions can be unified into a single one without conflict, by introducing the following unification operation National Cheng Kung University CSIE Computer & Internet Architecture Lab 12
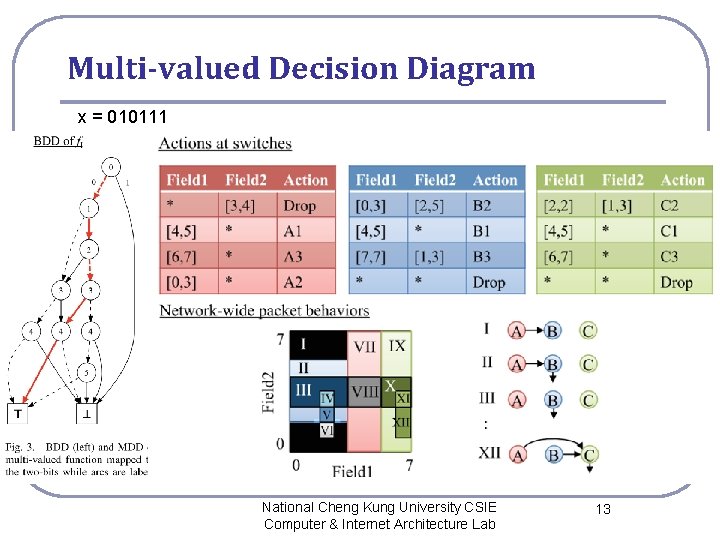
Multi-valued Decision Diagram x = 010111 National Cheng Kung University CSIE Computer & Internet Architecture Lab 13
Multi-valued Decision Diagram l l An MDD, which is shown in Fig. 3 (right), is also an acyclic directed graph with a single root, but it can have more than two terminal nodes, nil, I, II, · · · , |P|. Each non-terminal node is labeled by aggregated bits, and it can have more than two children arcs, 0, 1, · · · , 2 K − 1. The maximum height is L/K. Other properties are the same as those of BDD. National Cheng Kung University CSIE Computer & Internet Architecture Lab 14
Multi-valued Decision Diagram l l In our method, a BDD is used to represent a Boolean function that maps the header space to a single packet behavior, while an MDD is used to express a multi-valued function. BDD of fi(x) is easily converted to MDD of Fi(x), by replacing ⊥ - and -terminals with niland i-terminals, respectively. National Cheng Kung University CSIE Computer & Internet Architecture Lab 15
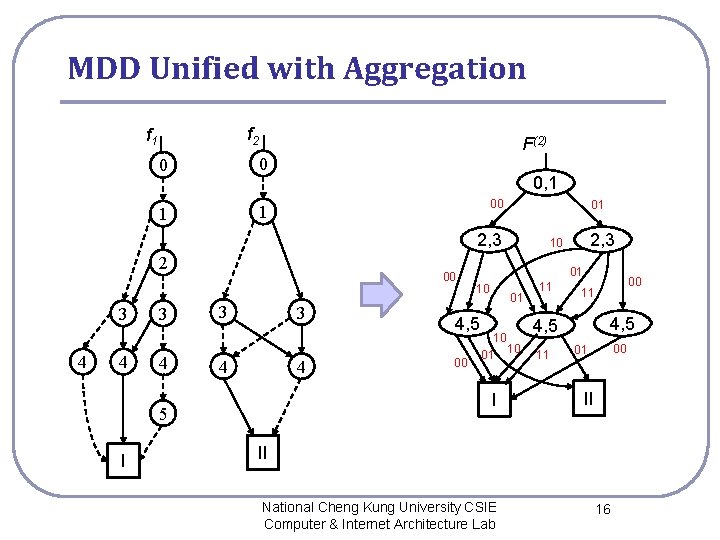
MDD Unified with Aggregation f 2 f 1 0 0 1 1 F(2) 0, 1 00 01 2, 3 2 3 4 4 3 4 00 3 3 4 4 10 01 10 I 5 I 01 4, 5 00 2, 3 10 11 4, 5 11 00 01 II II National Cheng Kung University CSIE Computer & Internet Architecture Lab 16
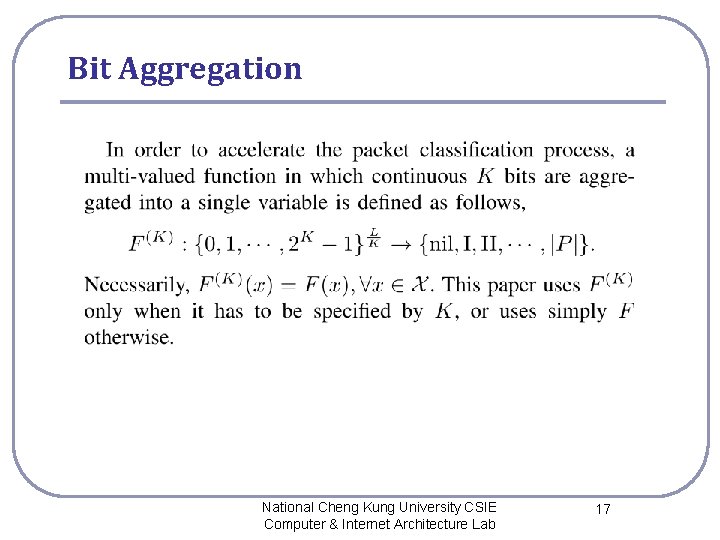
Bit Aggregation National Cheng Kung University CSIE Computer & Internet Architecture Lab 17
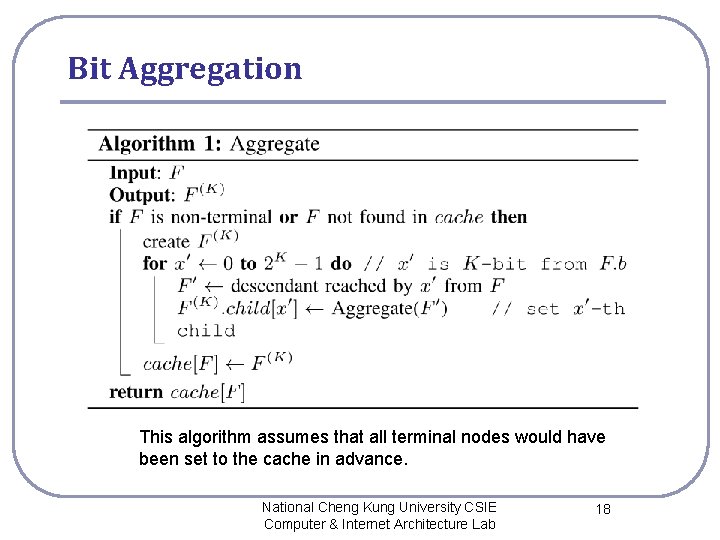
Bit Aggregation This algorithm assumes that all terminal nodes would have been set to the cache in advance. National Cheng Kung University CSIE Computer & Internet Architecture Lab 18

Search A packet header is represented as an array of K-bit elements; i. e. , i-th K-bit element on the header can be accessed by index i, like pkt[i]. National Cheng Kung University CSIE Computer & Internet Architecture Lab 19
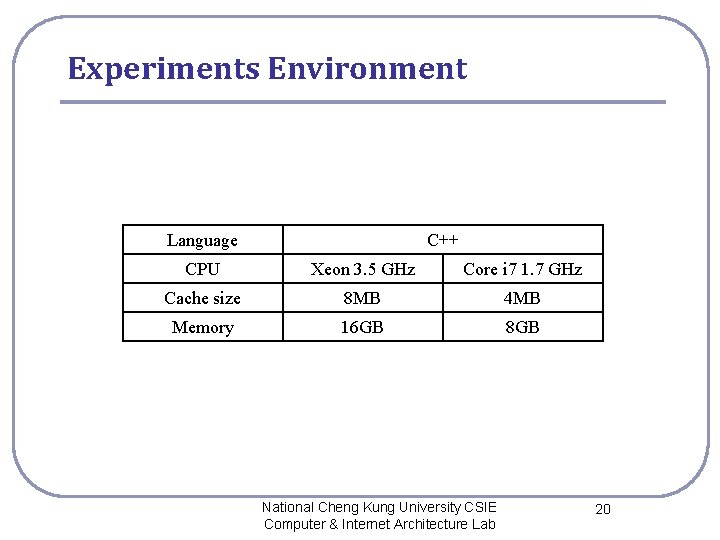
Experiments Environment Language C++ CPU Xeon 3. 5 GHz Core i 7 1. 7 GHz Cache size 8 MB 4 MB Memory 16 GB 8 GB National Cheng Kung University CSIE Computer & Internet Architecture Lab 20
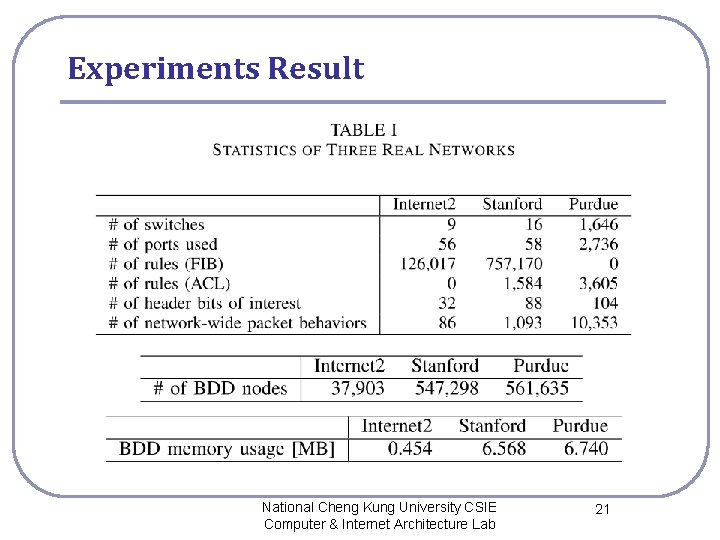
Experiments Result National Cheng Kung University CSIE Computer & Internet Architecture Lab 21
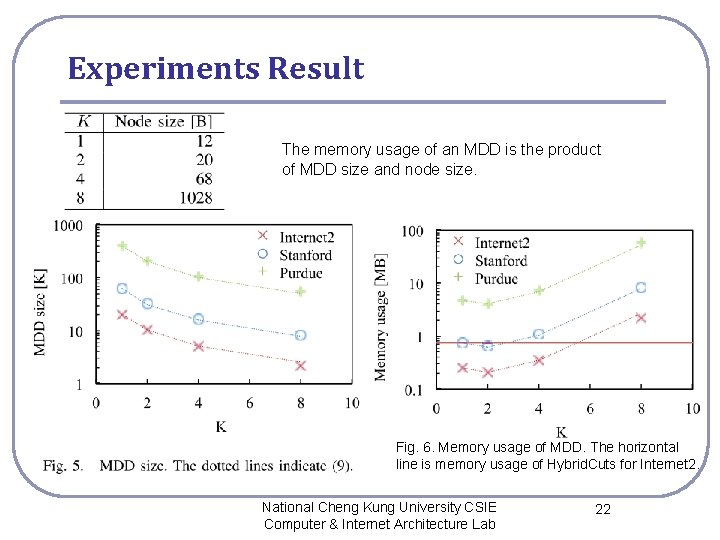
Experiments Result The memory usage of an MDD is the product of MDD size and node size. Fig. 6. Memory usage of MDD. The horizontal line is memory usage of Hybrid. Cuts for Internet 2. National Cheng Kung University CSIE Computer & Internet Architecture Lab 22
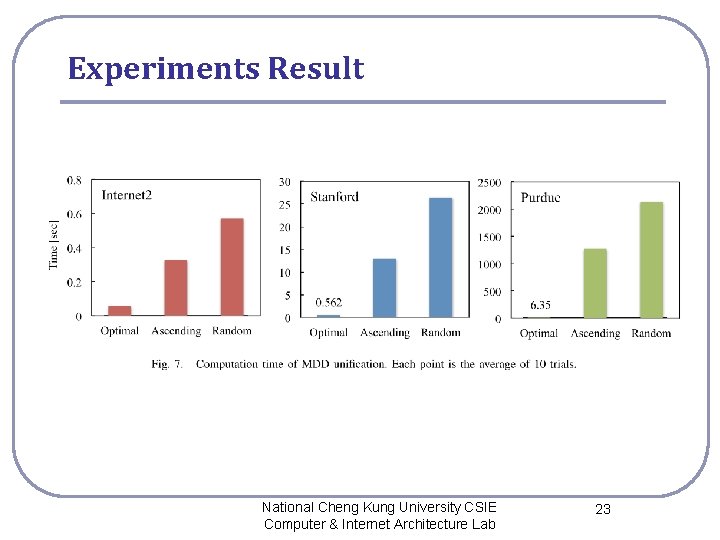
Experiments Result National Cheng Kung University CSIE Computer & Internet Architecture Lab 23
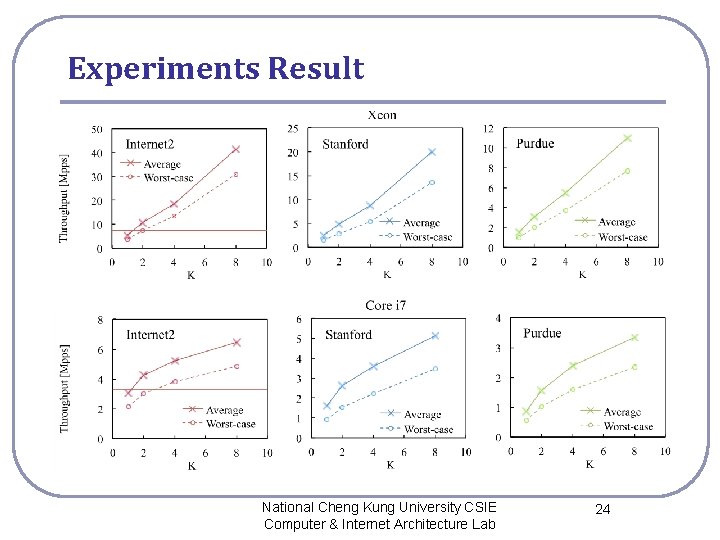
Experiments Result National Cheng Kung University CSIE Computer & Internet Architecture Lab 24
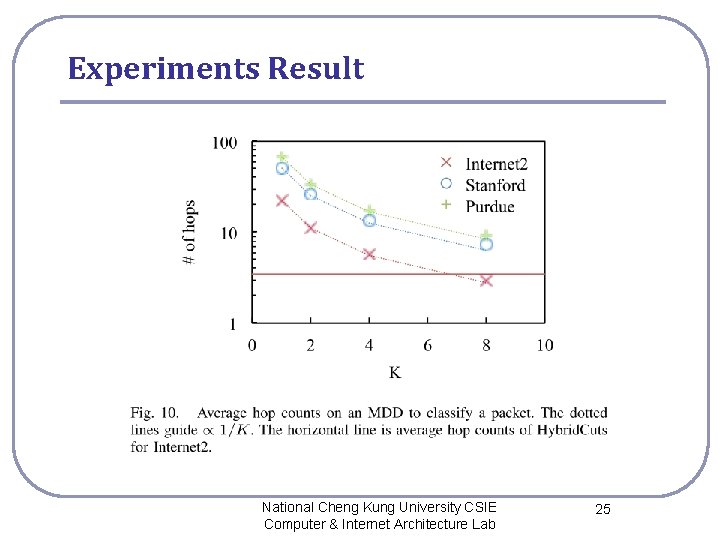
Experiments Result National Cheng Kung University CSIE Computer & Internet Architecture Lab 25
- Slides: 25