RESPONSIBLE DATA WHAT IS IT AND WHY SHOULD

RESPONSIBLE DATA: WHAT IS IT AND WHY SHOULD WE CARE? Danna Ingleton Responsible Data Program Manager, engine room @ingleton danna@theengineroom. org

How technology & data can help
User-led design - THE PANIC BUTTON panicbutton. io

Data as evidence - Medi. Capt help clinicians more effectively collect, document, and preserve forensic medical evidence of sexual violence to support the local prosecution of these crimes http: //physiciansforhumanrights. org/medicapt/
Micro-tasking platforms to process data http: //www. chimpandsee. org/#/
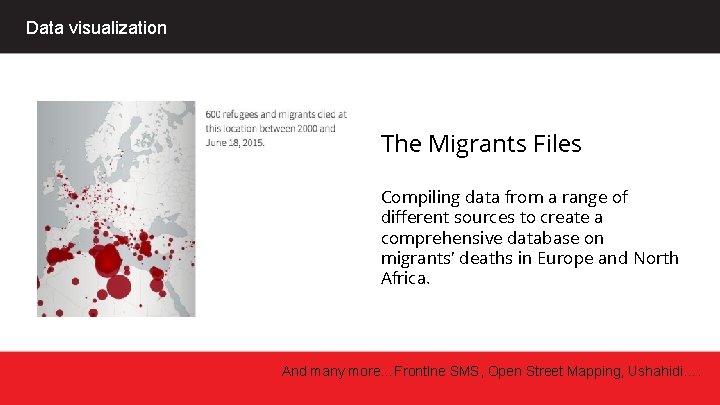
Data visualization The Migrants Files Compiling data from a range of different sources to create a comprehensive database on migrants' deaths in Europe and North Africa. And many more…Frontlne SMS, Open Street Mapping, Ushahidi….

RESPONSIBLE DATA

Do. So how does RESPONSIBLE DATA fit into this landscape? Responsible data is: "The duty to ensure people’s rights to consent, privacy security and ownership around the information processes of collection, analysis, storage, presentation and reuse of data, while respecting the values of transparency and openness. ” “Responsible data isn’t just about technical security and encryption, but about prioritising the dignity, respect and privacy of the people we work with. ” How to Practice Responsible Development Data http: //the-engine-room. github. io/rdf-primer/

Data is information is people.

MORE REASONS THAT THIS IS IMPORTANT

Types of harms - TO THE INDIVIDUAL OR COMMUNITY People can be put at risk of harm (physical, psychosocial and/or reputational): ● if they, or something about them, are identified directly ● if several sources are combined to identify them ● if data is collected in a discriminatory way Image: Payam Boromand

types of harms - TO THE ORGANIZATION Organisations can damage their reputation if that are perceived not to respect agency, fair representation and consent

Responsible Data simply means doing our best to think through these issues and mitigate against them as part of our project planning

DATA PROJECT CYCLE

Responsible Data Considerations in the Project Cycle
GENERATION: What kind of data do you need?
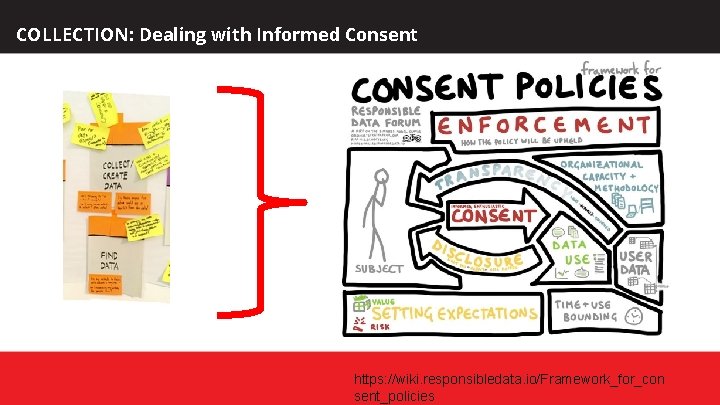
COLLECTION: Dealing with Informed Consent https: //wiki. responsibledata. io/Framework_for_con sent_policies

TRANSFER & STORAGE: Where do you keep your data? Why? How? How you store or transfer data? - If sharing with other organisations, check they understanding the data’s sensitivity - Choose secure hosting providers - When to use encryption - Data sharing policies and agreements
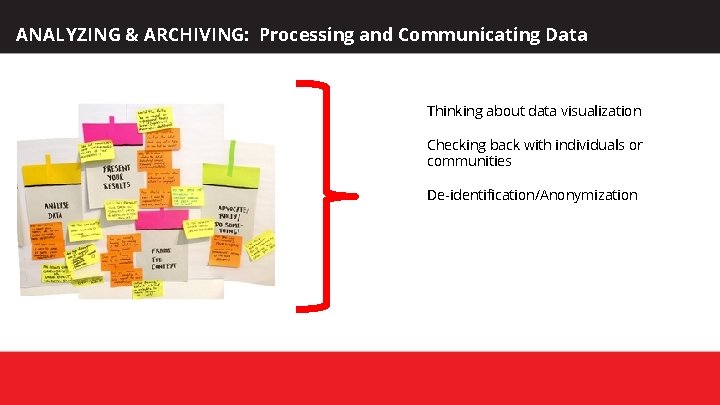
ANALYZING & ARCHIVING: Processing and Communicating Data Thinking about data visualization Checking back with individuals or communities De-identification/Anonymization
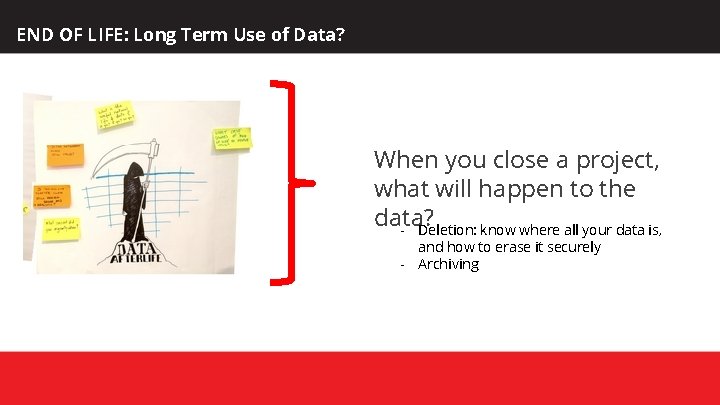
END OF LIFE: Long Term Use of Data? When you close a project, what will happen to the data? - Deletion: know where all your data is, and how to erase it securely - Archiving

Follow the conversation Resources and events: responsibledata. io #responsibledata @engnroom, @ingleton

Now consider these questions…. any gaps emerging? Risk Can any of the reports being sent be expected to upset anyone? Would it be a problem if government or anyone else gained access to information sent over the platform? What capacities do they have to discover that reports are made and what they contain? What are likely responses by those upset? Can using the platform (or participating in any other way) identify individuals or groups with specific groups or opinions? Can specific reports be traced back to the reporters (either through phone numbers, IP addresses, mandatory SIM card registration or contextual information and guesswork)? Will the system either explicitly or automatically collect any personal information that might be valuable for commercial or criminal activity? socially sensitive, and which individuals would reasonably expect to consider private? Users What technology will people sending reports be using, and does this match the design? Who is trained to use the platform? How does this group relate to the rest of the population? Does this training include security training? Does this group train others, and what components are included in that secondary training? What are users’ incentives for participating? How do these incentives impact local power and political dynamics? Is there any chance that the benefits of participating will put users at risk? Is participation in the platform worth users’ investment (in terms of time, cost and risk)? What expectations do users and communities have about how the platfrom will be used and what it will lead to? Are these expectations realistic and inline with project expectations? How has risk been communicated to users and communities? Is there a difference between these two and is it justified? Information Security Is any of the information collected made publicly available? If some of the information is not made public, why not, and why that information? Do users and communities know which information will be made publicly available? How is information stored? If it is stored online, how hard would it be for someone to access it through hacking, legal means or by snooping during transmission? If it is stored by the project in digital or paper format, how hard would it be for someone gain access, by hacking, sneaking or guessing passwords? Who has access to the information? Do different people within the organization have access to different information in the system? Are these levels of access necessary and appropriate? Who could gain access to information that should not have access to it, and how?
- Slides: 23