research at MSEC Vincent Naessens Jorn Lapon Jan












- Slides: 20

research at MSEC Vincent Naessens – Jorn Lapon – Jan Vossaert – Koen Decroix – Faysal Boukayoua – Laurens Lemaire



Overview • Research scope MSEC • RL 1: Identity Management on Mobile platforms • RL 2: Formal Security and Privacy Analysis • Applied research projects

Security research at KU Leuven • Department of Electrical Engineering • Cryptographic algoritms and protocols • Hardware support and embedded design • Department of Computer Science • Middleware for security • Methodological support • Technology driven • Close collaboration with industry

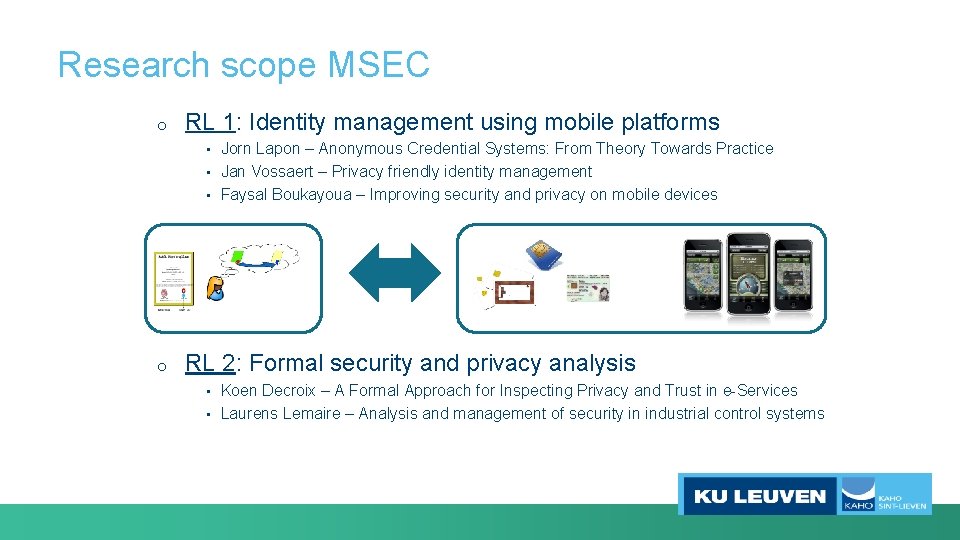
Research scope MSEC o RL 1: Identity management using mobile platforms Jorn Lapon – Anonymous Credential Systems: From Theory Towards Practice • Jan Vossaert – Privacy friendly identity management • Faysal Boukayoua – Improving security and privacy on mobile devices • o RL 2: Formal security and privacy analysis Koen Decroix – A Formal Approach for Inspecting Privacy and Trust in e-Services • Laurens Lemaire – Analysis and management of security in industrial control systems •

Identity management on mobile platforms • Extending the scope of Belgian e. ID technology (J. Lapon) Secure Storage 1. Identification 2. Authentication 3. Digital signature Proxy certificates

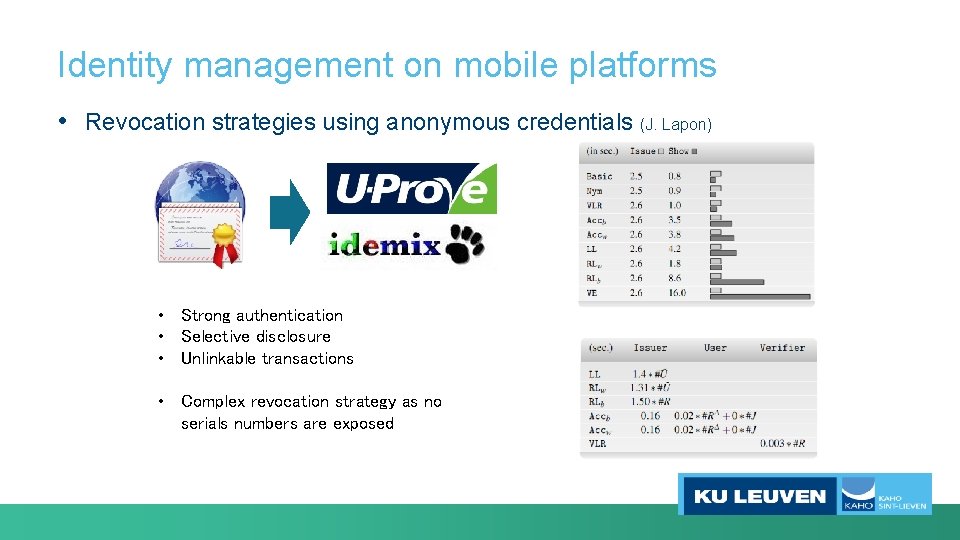
Identity management on mobile platforms • Revocation strategies using anonymous credentials (J. Lapon) • Strong authentication • Selective disclosure • Unlinkable transactions • Complex revocation strategy as no serials numbers are exposed

Identity management on mobile platforms • Privacy preserving smartcard authentication (J. Vossaert) • Weak security • No personalisation • No user control • Single point of attack • Static set of attributes • Limited user control 1. Increased flexibility 2. User control 3. Online/offline services

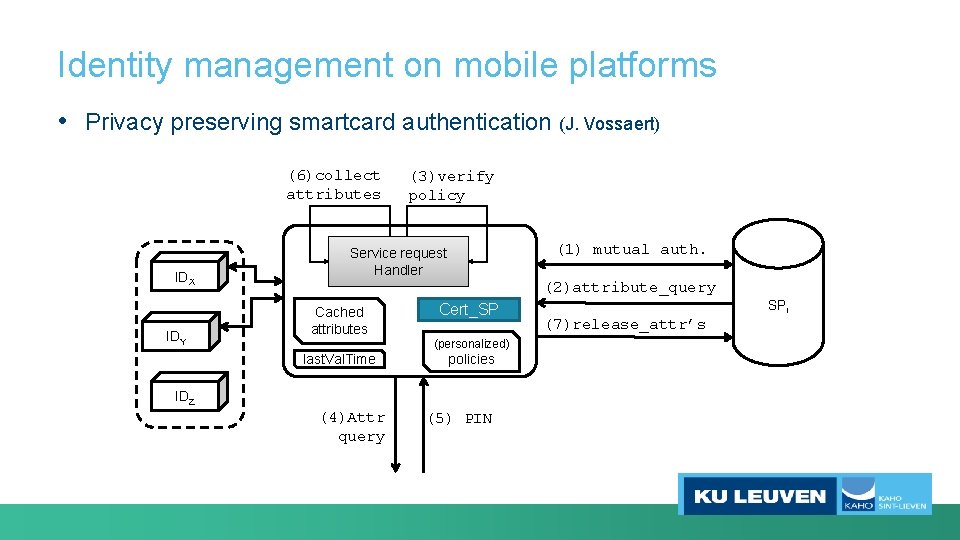
Identity management on mobile platforms • Privacy preserving smartcard authentication (J. Vossaert) (6)collect attributes IDX IDY (3)verify policy (1) mutual auth. Service request Handler (2)attribute_query Cached attributes last. Val. Time Cert_SP (personalized) policies IDZ (4)Attr query (5) PIN (7)release_attr’s SPi

Identity management on mobile platforms • Client-Side Biometric Verification based on Trusted Computing (J. Vossaert) [2] [4] [3] • Secure authentication • Biometric attestation • Selective disclosure 1. Fingerprint templates are not exposed 2. Solution based on trusted computing technology [1]

Identity management on mobile platforms • Improving secure data storage in Android (F. Boukayoua) • KDF slows down brute force attacks • Secure element online attacks • Closed system • Open system • Security based on passcode • Offline attacks

Identity management on mobile platforms • Improving secure data storage in Android (F. Boukayoua) • No denial-of-service attacks • Prevention of key stealing • No dictionary attacks • Decryption keys are protected [2] [1] Context aware security decisions to constrain data and credential availability

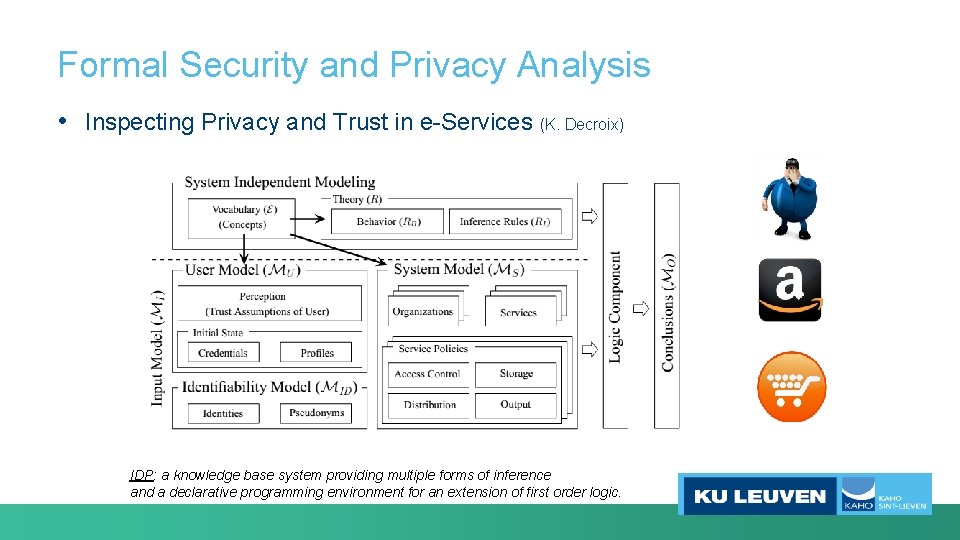
Formal Security and Privacy Analysis • Inspecting Privacy and Trust in e-Services (K. Decroix) • • Modeling complex interations in advanced electronic services Reasing about profiles compiled by service providers Evaluating the impact of authentication technologies on privacy Studying impact on trust on user selection

Formal Security and Privacy Analysis • Inspecting Privacy and Trust in e-Services (K. Decroix) IDP: a knowledge base system providing multiple forms of inference and a declarative programming environment for an extension of first order logic.

Formal Security and Privacy Analysis • Analysing security in industrial control systems (L. Lemaire) • Input 1. Modeling ICS and SCADA systems 2. Modeling advanced attacks • Output/feedback 1. Analysing the impact of security vulnerabilities 2. Evaluating accountabilities 3. Proposing countermeasures

Applied research projects • Agency for Innovation by Science and Technology o Strategic Basic Research Di. Co. Mas – Distributed Collaboration using MAS architectures • Mob. Com – A Mobile Companion • • Middle/long term valorisation; user group: R&D departments o Technology Transfer Projects e. IDea – Developing advanced applications for the Belgian e. ID • Wiscy – Developing secure wireless environments • Secure. Apps – Developing secure Mobile applications • • Short/middle term valorisation; user group: SMEs

Applied research projects

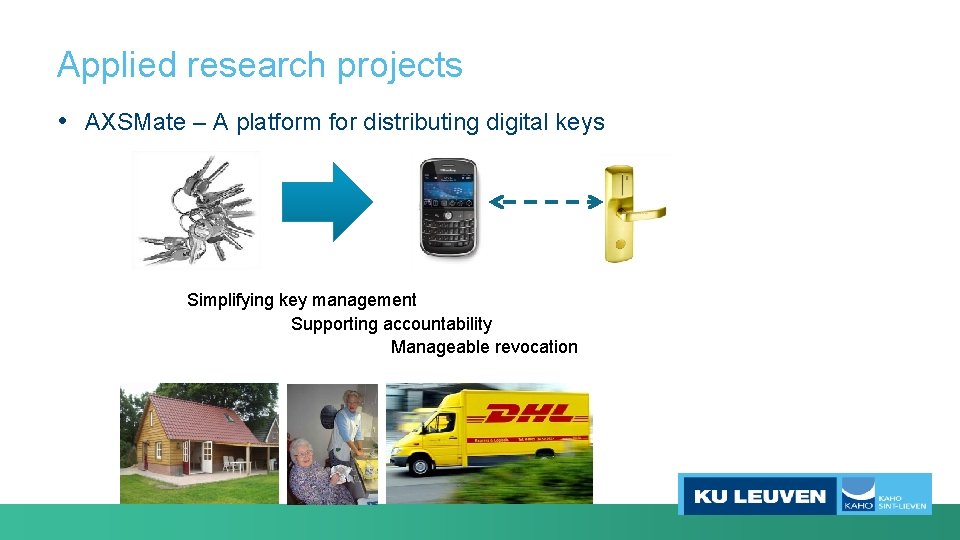
Applied research projects • AXSMate – A platform for distributing digital keys Simplifying key management Supporting accountability Manageable revocation

Applied research projects • Torekes – An alternative currency system o Increase social interaction in poor districts o Attract students by alternative payment method
 Dr jorn dyerberg
Dr jorn dyerberg Jorn altmann
Jorn altmann Jörn ostermann
Jörn ostermann Jég rácstípus
Jég rácstípus Fématom
Fématom Msec doorlopende leerlijn
Msec doorlopende leerlijn Research report vs research proposal
Research report vs research proposal Site:slidetodoc.com
Site:slidetodoc.com Research appendices example
Research appendices example Definition of research design
Definition of research design Scope of research definition
Scope of research definition Research plan
Research plan Contrast applied research and basic research
Contrast applied research and basic research Scope and objectives of research problem
Scope and objectives of research problem Research instrument in experimental research
Research instrument in experimental research Longitudinal research and cross sectional research
Longitudinal research and cross sectional research Causal comparative research meaning
Causal comparative research meaning Chapter 3 methodology
Chapter 3 methodology Applied vs fundamental research
Applied vs fundamental research Basic research vs applied research
Basic research vs applied research Explanatory reseach
Explanatory reseach