Research and Development Initiatives Focused on Preventing Detecting















- Slides: 32

Research and Development Initiatives Focused on Preventing, Detecting, and Responding to Insider Misuse of Critical Defense Information Systems Results of a Three-Day Workshop August 16 -19, 1999 10/18/2021 1

Background § Three-day workshop held at RAND Santa Monica, August 16 -18, 1999; 35 invited participants § Sponsored by Army Research Lab, DARPA, NSA § Purpose: to recommend technical R&D initiatives addressing the insider threat to Do. D info systems § ASD/C 3 I report Do. D Insider Threat Mitigation Plan (June 1999) concentrated on near-term steps to be taken § § 10/18/2021 This workshop focused on longer-term technical R&D required Workshop is expected to be first in a series 2

Policy and Precursors to R&D Technical initiatives must have a supportive environment. Required are: l l l 10/18/2021 Guidance from legal and law enforcement communities re. attribution, collection, maintenance, processing and storage of data Clear definitions re. what are “critical assets” on a system Clarity regarding who is an “insider” Cost/benefit analysis of recommended measures Plans for technology transfer Support for multiple, diverse, concurrent approaches 3

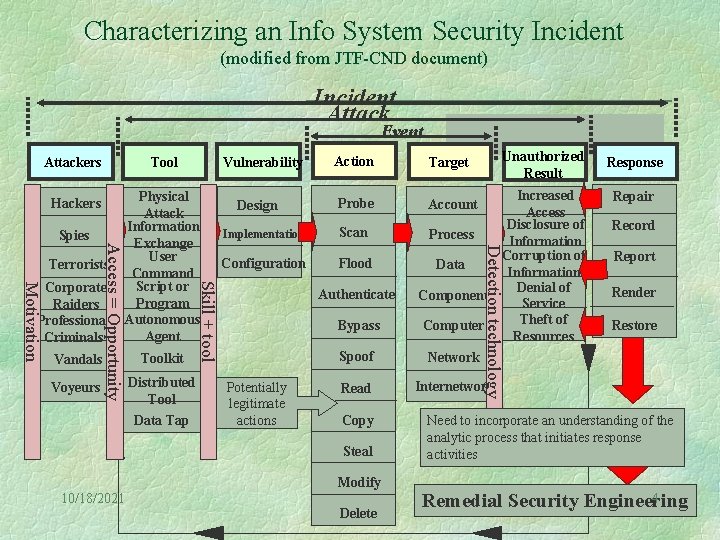
Characterizing an Info System Security Incident (modified from JTF-CND document) Incident Attack Event Attackers Tool Hackers Spies Vandals Voyeurs Toolkit Distributed Tool Data Tap Design Action Probe Implementation Scan Configuration Flood Authenticate Bypass Potentially legitimate actions Unauthorized Result Increased Access Disclosure of Process Information Corruption of Data Information Denial of Component Service Theft of Computer Resources Account Spoof Network Read Internetwork Copy Steal Modify 10/18/2021 Sandia Labs Target Detection technology Motivation Corporate Raiders Professional Criminals Physical Attack Information Exchange User Command Script or Program Autonomous Agent Skill + tool Access = Opportunity Terrorists Vulnerability Delete Response Repair Record Report Render Restore Need to incorporate an understanding of the analytic process that initiates response activities 4 Remedial Security Engineering

Workshop Developed Recommendations in 4 Categories 20 specific recommendations: • Threat (4) • Prevention (5) • Detection (6) • Response (5) 10/18/2021 5

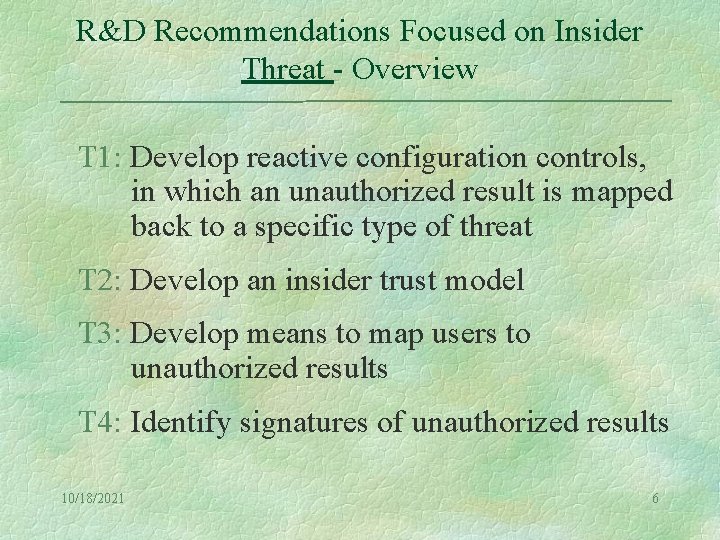
R&D Recommendations Focused on Insider Threat - Overview T 1: Develop reactive configuration controls, in which an unauthorized result is mapped back to a specific type of threat T 2: Develop an insider trust model T 3: Develop means to map users to unauthorized results T 4: Identify signatures of unauthorized results 10/18/2021 6

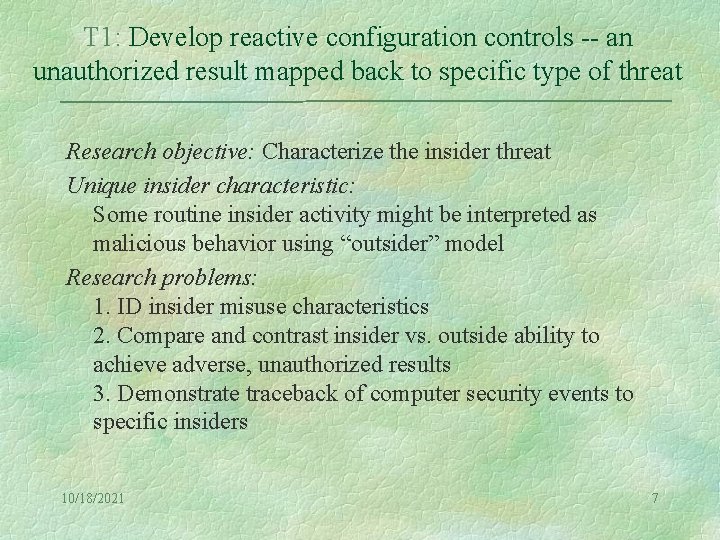
T 1: Develop reactive configuration controls -- an unauthorized result mapped back to specific type of threat Research objective: Characterize the insider threat Unique insider characteristic: Some routine insider activity might be interpreted as malicious behavior using “outsider” model Research problems: 1. ID insider misuse characteristics 2. Compare and contrast insider vs. outside ability to achieve adverse, unauthorized results 3. Demonstrate traceback of computer security events to specific insiders 10/18/2021 7

T 2: Develop an insider trust model Research objective: Develop a model of trust covering the full breadth of organizational roles authorizing degrees of technical configuration control privilege Unique insider characteristic: The attributes of the trust relationship are the key distinguishing factors separating insider from outsider Research problems: 1. A characterization schema with insider roles and privileges, covering the full spectrum of military operations 2. Develop parametric sensitivity criteria useful in recognizing attempted unauthorized escalation of privilege, before a security-breaching event 10/18/2021 8

T 3: Develop means to map users to unauthorized results Research objective: Given a system anomaly, determine if an insider did it, and if so, which one (Note: This recommendation is similar to D 3; see it for details. ) 10/18/2021 9

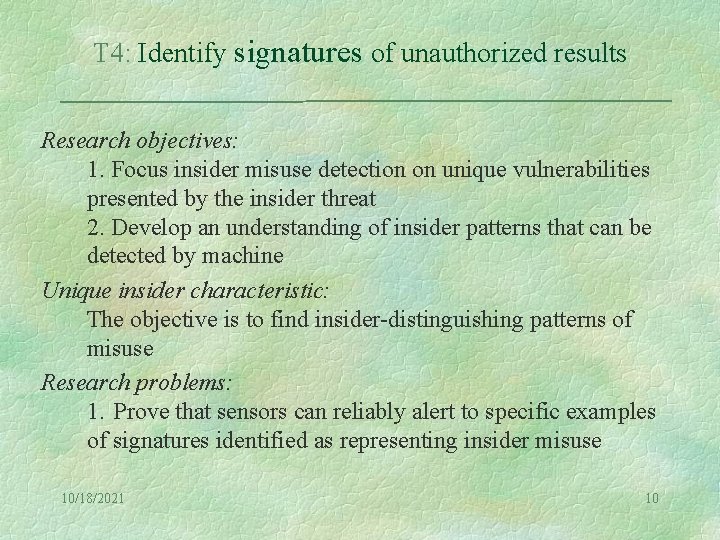
T 4: Identify signatures of unauthorized results Research objectives: 1. Focus insider misuse detection on unique vulnerabilities presented by the insider threat 2. Develop an understanding of insider patterns that can be detected by machine Unique insider characteristic: The objective is to find insider-distinguishing patterns of misuse Research problems: 1. Prove that sensors can reliably alert to specific examples of signatures identified as representing insider misuse 10/18/2021 10

R&D Recommendations Focused on Insider Prevention - Overview P 1: Develop authentication components P 2: Develop access control components P 3: Develop system integrity components P 4: Develop a bidirectional trusted path to the security system P 5: Develop attribution components 10/18/2021 11

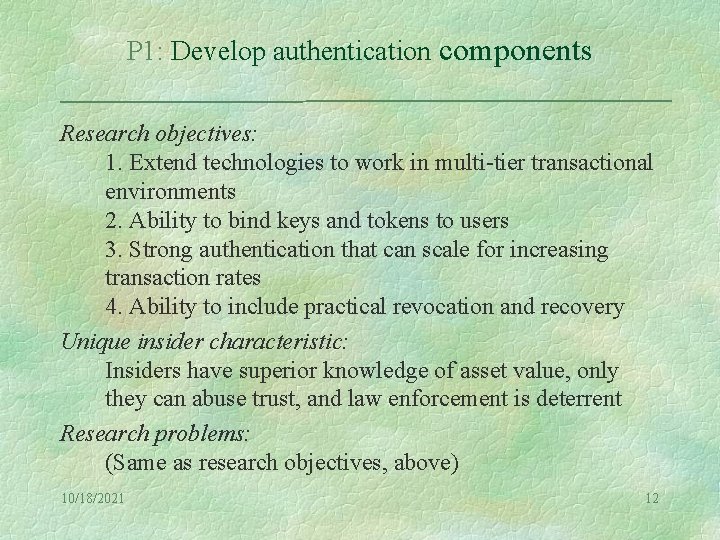
P 1: Develop authentication components Research objectives: 1. Extend technologies to work in multi-tier transactional environments 2. Ability to bind keys and tokens to users 3. Strong authentication that can scale for increasing transaction rates 4. Ability to include practical revocation and recovery Unique insider characteristic: Insiders have superior knowledge of asset value, only they can abuse trust, and law enforcement is deterrent Research problems: (Same as research objectives, above) 10/18/2021 12

P 2: Develop access control components Research objectives: 1. Development of finer-grained access control that is affordable 2. Inter-platform access control management 3. Reducing mgmt. cost of implementation/maintenance of access controls 4. New types of access control to reduce vulnerability to trusted insiders Unique insider characteristic: Insiders have superior knowledge of asset value, only they can abuse trust, and law enforcement is deterrent Research problems: 1. Expert-system-based access control automation able to translate natural language policy statements into machine-level policy 2. Meta-access control system for cross-platform access management 3. Ability to prevent insider misuse by security administrators and other privileged users 10/18/2021 13

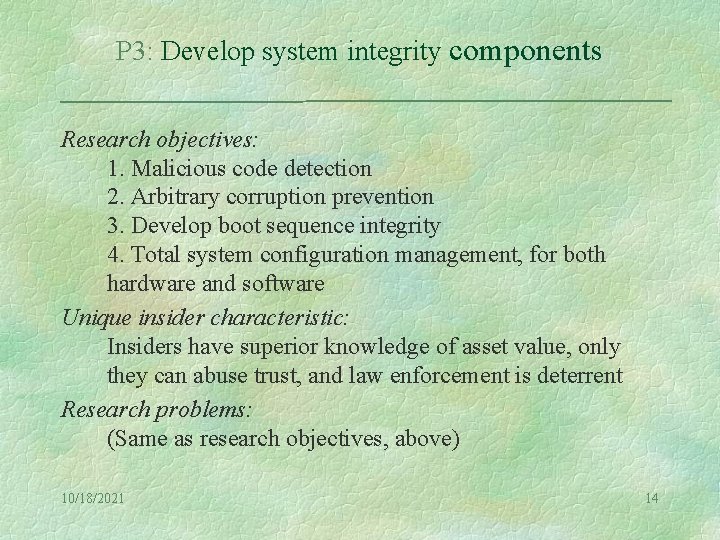
P 3: Develop system integrity components Research objectives: 1. Malicious code detection 2. Arbitrary corruption prevention 3. Develop boot sequence integrity 4. Total system configuration management, for both hardware and software Unique insider characteristic: Insiders have superior knowledge of asset value, only they can abuse trust, and law enforcement is deterrent Research problems: (Same as research objectives, above) 10/18/2021 14

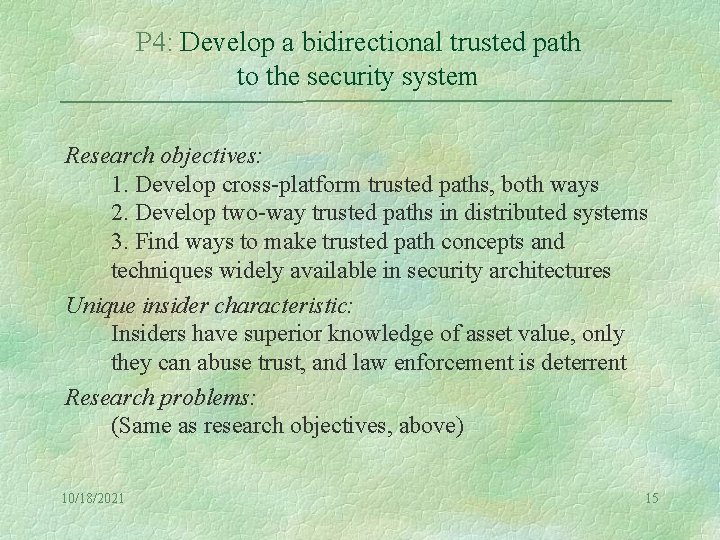
P 4: Develop a bidirectional trusted path to the security system Research objectives: 1. Develop cross-platform trusted paths, both ways 2. Develop two-way trusted paths in distributed systems 3. Find ways to make trusted path concepts and techniques widely available in security architectures Unique insider characteristic: Insiders have superior knowledge of asset value, only they can abuse trust, and law enforcement is deterrent Research problems: (Same as research objectives, above) 10/18/2021 15

P 5: Develop attribution components Research objectives: 1. Be able to attribute specific actions to individual users Unique insider characteristic: Insiders may have access to the attribution mechanisms, so they must be hardened against insider misuse Research problems: (Similar to D 3, below) 10/18/2021 16

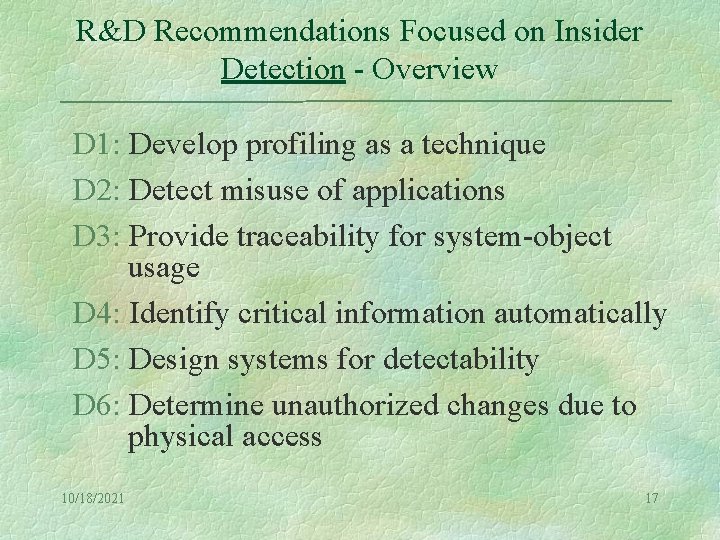
R&D Recommendations Focused on Insider Detection - Overview D 1: Develop profiling as a technique D 2: Detect misuse of applications D 3: Provide traceability for system-object usage D 4: Identify critical information automatically D 5: Design systems for detectability D 6: Determine unauthorized changes due to physical access 10/18/2021 17

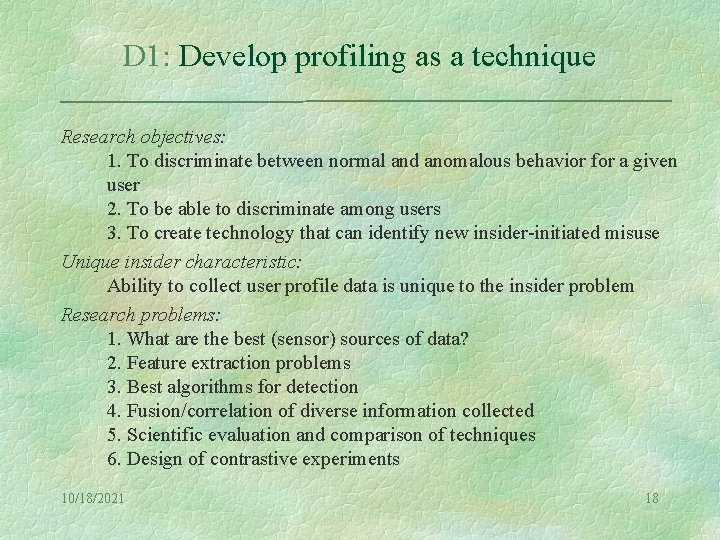
D 1: Develop profiling as a technique Research objectives: 1. To discriminate between normal and anomalous behavior for a given user 2. To be able to discriminate among users 3. To create technology that can identify new insider-initiated misuse Unique insider characteristic: Ability to collect user profile data is unique to the insider problem Research problems: 1. What are the best (sensor) sources of data? 2. Feature extraction problems 3. Best algorithms for detection 4. Fusion/correlation of diverse information collected 5. Scientific evaluation and comparison of techniques 6. Design of contrastive experiments 10/18/2021 18

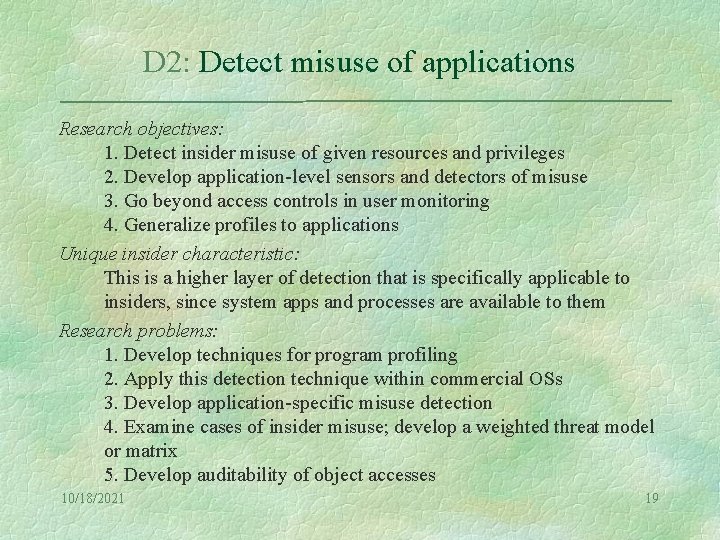
D 2: Detect misuse of applications Research objectives: 1. Detect insider misuse of given resources and privileges 2. Develop application-level sensors and detectors of misuse 3. Go beyond access controls in user monitoring 4. Generalize profiles to applications Unique insider characteristic: This is a higher layer of detection that is specifically applicable to insiders, since system apps and processes are available to them Research problems: 1. Develop techniques for program profiling 2. Apply this detection technique within commercial OSs 3. Develop application-specific misuse detection 4. Examine cases of insider misuse; develop a weighted threat model or matrix 5. Develop auditability of object accesses 10/18/2021 19

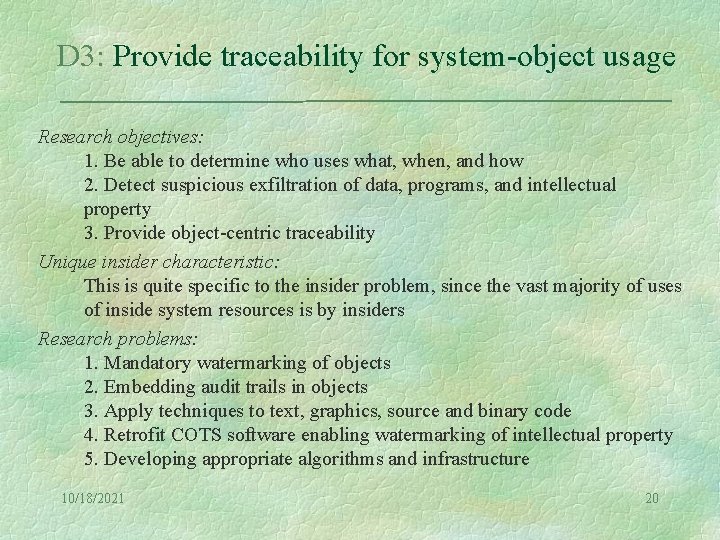
D 3: Provide traceability for system-object usage Research objectives: 1. Be able to determine who uses what, when, and how 2. Detect suspicious exfiltration of data, programs, and intellectual property 3. Provide object-centric traceability Unique insider characteristic: This is quite specific to the insider problem, since the vast majority of uses of inside system resources is by insiders Research problems: 1. Mandatory watermarking of objects 2. Embedding audit trails in objects 3. Apply techniques to text, graphics, source and binary code 4. Retrofit COTS software enabling watermarking of intellectual property 5. Developing appropriate algorithms and infrastructure 10/18/2021 20

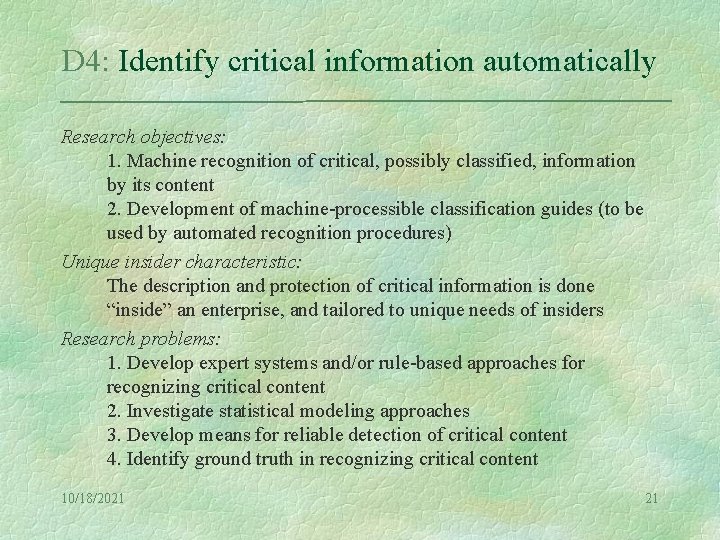
D 4: Identify critical information automatically Research objectives: 1. Machine recognition of critical, possibly classified, information by its content 2. Development of machine-processible classification guides (to be used by automated recognition procedures) Unique insider characteristic: The description and protection of critical information is done “inside” an enterprise, and tailored to unique needs of insiders Research problems: 1. Develop expert systems and/or rule-based approaches for recognizing critical content 2. Investigate statistical modeling approaches 3. Develop means for reliable detection of critical content 4. Identify ground truth in recognizing critical content 10/18/2021 21

D 5: Design systems for detectability Research objectives: 1. Develop system architectures that channel insider misuse into enclaves 2. Regulate passage among enclaves by “gates” that are instrumented for observation and response Unique insider characteristic: The intent is to make an insider an “outsider” to enclaves for which access is not immediately needed or authorized Research problems: 1. Design of gateways internal to a system that partition it into enclaves with separately controllable permissions 2. Resolution of the tension between system/data redundancy (for robustness) and concentration of critical assets within specific enclaves 3. Strategic deployment of sensors or “tripwires” based on enclaves 10/18/2021 22

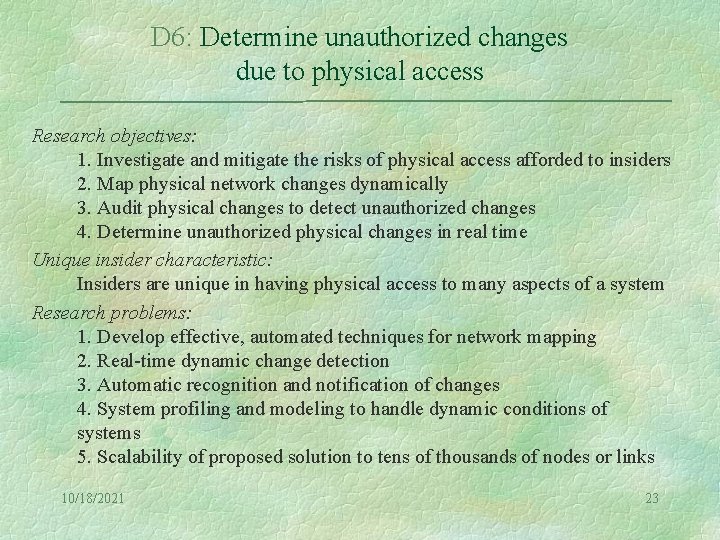
D 6: Determine unauthorized changes due to physical access Research objectives: 1. Investigate and mitigate the risks of physical access afforded to insiders 2. Map physical network changes dynamically 3. Audit physical changes to detect unauthorized changes 4. Determine unauthorized physical changes in real time Unique insider characteristic: Insiders are unique in having physical access to many aspects of a system Research problems: 1. Develop effective, automated techniques for network mapping 2. Real-time dynamic change detection 3. Automatic recognition and notification of changes 4. System profiling and modeling to handle dynamic conditions of systems 5. Scalability of proposed solution to tens of thousands of nodes or links 10/18/2021 23

R&D Recommendations Focused on Insider Response - Overview R 1: Develop a capability for monitoring privacyenhanced systems, such as those using encryption R 2: Incorporate practical autonomic system response into production systems R 3: Develop data correlation tools, including data reduction forensics, and visualization tools focused on internal misuse R 4: Develop a capability for surveillance of nonnetworked components R 5: Consider deception technologies specifically applicable to the insider threat 10/18/2021 24

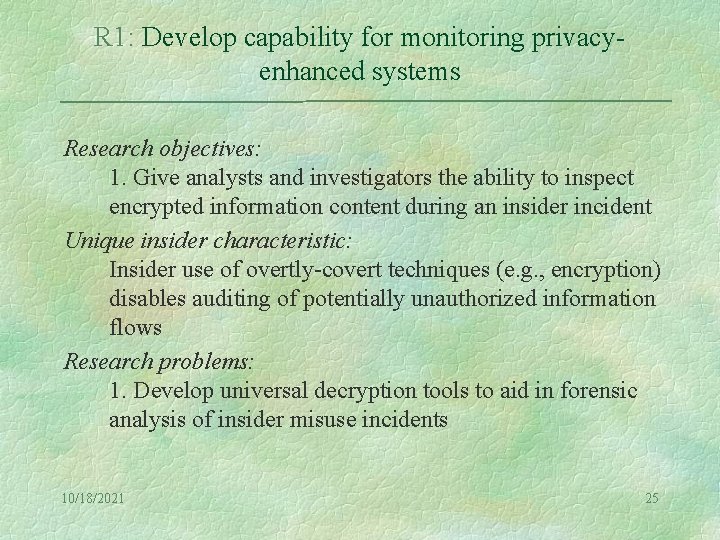
R 1: Develop capability for monitoring privacyenhanced systems Research objectives: 1. Give analysts and investigators the ability to inspect encrypted information content during an insider incident Unique insider characteristic: Insider use of overtly-covert techniques (e. g. , encryption) disables auditing of potentially unauthorized information flows Research problems: 1. Develop universal decryption tools to aid in forensic analysis of insider misuse incidents 10/18/2021 25

R 2: Incorporate practical autonomic* system response into production systems Research objectives: 1. Create environmentally aware management technology that can dynamically modify privilege authorizations and exposure to risk 2. Ensure that the technology cannot be spoofed by an insider 3. Develop threat response mechanisms that are resistant to misuse 4. Improve the general survivability of software products Unique insider characteristic: Insiders have distinguished signatures/patterns of misuse Research problems: 1. Identify insider misuse characteristics 2. Automatic recognition and notification of changes 3. System profiling and modeling that can handle dynamic conditions 4. Watermark and digital signature technologies to tag artifacts as evidence in insider misuse investigations 10/18/2021 *Autonomic: Due to internal causes or influences; spontaneous 26

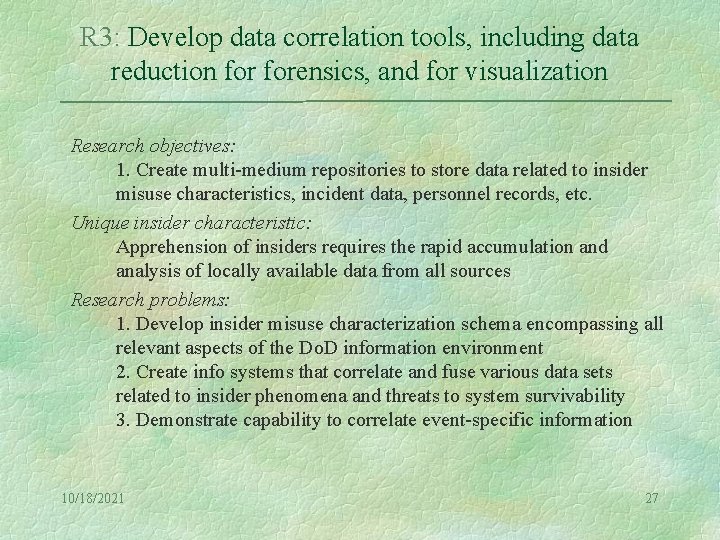
R 3: Develop data correlation tools, including data reduction forensics, and for visualization Research objectives: 1. Create multi-medium repositories to store data related to insider misuse characteristics, incident data, personnel records, etc. Unique insider characteristic: Apprehension of insiders requires the rapid accumulation and analysis of locally available data from all sources Research problems: 1. Develop insider misuse characterization schema encompassing all relevant aspects of the Do. D information environment 2. Create info systems that correlate and fuse various data sets related to insider phenomena and threats to system survivability 3. Demonstrate capability to correlate event-specific information 10/18/2021 27

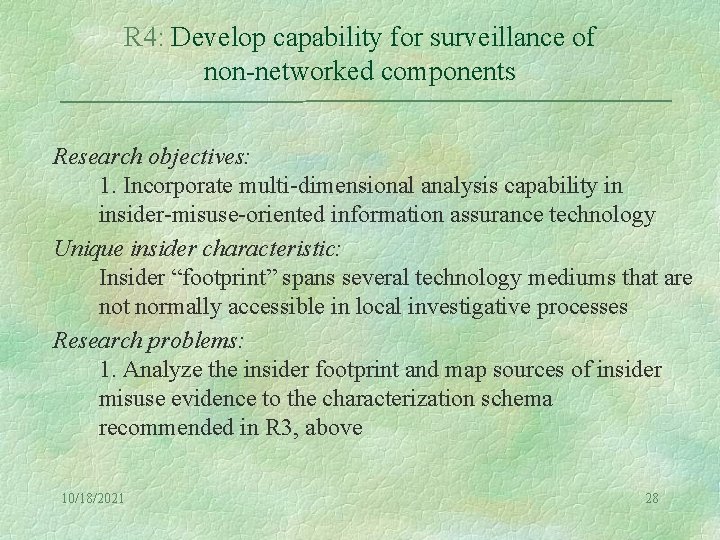
R 4: Develop capability for surveillance of non-networked components Research objectives: 1. Incorporate multi-dimensional analysis capability in insider-misuse-oriented information assurance technology Unique insider characteristic: Insider “footprint” spans several technology mediums that are not normally accessible in local investigative processes Research problems: 1. Analyze the insider footprint and map sources of insider misuse evidence to the characterization schema recommended in R 3, above 10/18/2021 28

R 5: Consider deception technologies specifically applicable to the insider threat Research objectives: 1. Develop deception techniques for information systems tailored to discovering malicious activities by insiders 2. Develop policies and procedures guiding use of these techniques Unique insider characteristic: Use of deception is believed to be a powerful way of discovering malicious insider activities, and determining their interests and intent Research problems: 1. Discover what system aspects are amenable to the introduction of deceptive techniques 2. How can such techniques be introduced without negative impacts? 3. Can these techniques be used to discover misuse by highly trusted individuals, such as sysadmins? 4. Can they be installed in a manner that prevents their misuse? 5. What are legal implications of using deception in info systems? 10/18/2021 29

DIO Organizations and Activities Study 35 Organizations Assessed Protection CERTs • Joint Task Force • Computer Network Defense • US Space Command • • National Infrastructure Protection Center • Air Force Computer Emergency Response Team Army Computer Emergency Response Team Navy Computer Incident Response Team • Defense Logistics Agency CERT • National Security Agency (X Group) • Carnegie Mellon University CERT/CC IW • Air Force Information Warfare Center • Land Information Warfare Activity • Naval Information Warfare Activity • Fleet Information Warfare Center • Information Operations Technology Center 10/18/2021 LE/CI • Air Force Office of Special Investigations • US Army Criminal Investigation Directorate • US Army Military Intelligence • Naval Criminal Investigation Service • Defense Criminal Investigative Service Network Operations • Air Force Network Operations Center • Army Network Systems Operations Center • Naval Computer and Telecommunications Command • Global Network Operations Security Center Intelligence • Joint Staff - J 2 • Defense Intelligence Agency • Air Intelligence Agency Support • Joint Command Control Warfare Center • Joint Spectrum Center • Do. D Computer Forensics Laboratory • Defense Advanced Research Projects Agency • Joint C 4 ISR Battle Center • Army Research Lab Other • National Aeronautics and Space Administration • Joint Warfare Analysis Center 30 [Source: U. S. Department of Defense]

Workshop Attendees Adams, Robert Air Force Information Warfare Center 250 Hall Rd #139 San Antonio, TX 78243 Christy, James ASDC 3 I/DIAP Ste. 1101, 1215 Jefferson Davis Highway, Arlington, Va 22202 Hunker, Jeffrey National Security Council White House #303 Washington DC 20504 Skolochenko, Steven Office of Information Systems Security 1500 Penn. Ave. NW, Annex, Rm. 3090, Washington, DC 20220 Alvarez, Jorge Space and Naval Warfare Systems Center 53560 Hull Street San Diego, CA 92152 Cowan, Crispin Oregon Graduate Institute P. O. Box 91000 Portland, OR 97291 Jaeger, Jim Lucent Technologies Box 186, Columbia, MD 21045 Skroch, Michael DARPA/ISO 3701 N. Fairfax Dr. Arlington, VA 22203 Anderson, Robert RAND Corporation P. O. Box 2138 Santa Monica, CA 90407 Dunn, Timothy Army Research Lab 2800 Powder Mill Road Adelphi, MD 20783 Anderson, Karl NSA R 2 9800 Savage Road Ft. Meade, MD 20755 Dunphy, Brian Defense Information Systems Agency 701 S. Courthouse Rd D 333 Arlington VA Arnold, Richard GTE GSC 1000 Wilson Blvd. Ste 810 Arlington, VA 22209 Ghosh, Anup K. Reliable Software Technologies 21351 Ridgetop Circle, Ste 400 Dulles, VA 20166 Barnes, Anthony Army Research Lab C 41 Systems Branch, AMSRL-SL-EI Ft. Monmouth, NJ 07703 -5602 Gligor, Virgil University of Maryland Electrical/Computer Engineering, AVW 1333, College Park, MD 20742 Bencivenga, Angelo Army Research Lab 2800 Powder Mill Road Adelphi, MD 20783 Gilliom, Laura Sandia National Labs P. O. Box 5800 -0455 Albuquerque NM Bozek, Thomas Office of the Secretary of Defense / C 3 I 6000 Defense, Rm 3 E 194 Pentagon Goldring, Tom NSA R 23 9800 Savage Road Ft. Meade, MD 20755 Brackney, Richard NSA R 2, R&E Bldg 9800 Savage Road Ft. Meade, MD 20755 Hotes, Scott NSA R 225 R&E Bldg 9800 Savage Road Ft. Meade, MD 20755 10/18/2021 Longstaff, Thomas CERT/CC 4500 Fifth Avenue Pittsburgh, PA 15213 Lunt, Teresa Xerox PARC 3333 Coyote Hill Road Palo Alto, CA 94304 Matzner, Sara U. Texas at Austin Applied Research Labs Information Systems Laboratory, P. O. Box 8029, Austin Texas 78713 Maxion, Roy Carnegie Mellon University 5000 Forbes Avenue Pittsburgh, PA 15213 Mc. Govern, Owen DISA Letterkenny Army Depot Chambersburg, PA 17201 -4122 Merritt, Larry D. NSA 9800 Savage Road Ft. George G. Meade, MD 20755 Neumann, Peter G SRI International 333 Ravenswood Ave. Menlo Park, CA 94025 Solo, David Citibank 666 Fifth Ave. , 3 rd Floor/Zone 6 New York, NY 10103 Teslich, Robyne Lawrence Livermore National Laboratory PO Box 808, Room L-52 Livermore CA 94550 Tung, Brian USC Information Sciences Institute 4676 Admiralty Way Ste. 1001, Marina del Rey, CA 90292 van Wyk, Kenneth Para-Protect 5600 General Washington Drive ste. B-212 Alexandria, VA 22312 Walczak, Paul Army Research Laboratory 2800 Powder Mill Road Adelphi, MD 20783 Zissman, Marc Mit Lincoln Laboratory 244 Wood Street Lexington, MA 20420 31

Bibliography (partial) NTISSIC draft, Advisory Memorandum on the Insider Threat to U. S. Government Information Systems (IS), in pdf and Word formats. This was deemed essential reading for participants before the workshop. Do. D Insider Threat Mitigation Plan: Final Report of the Insider Threat Integrated Process Team, June 1999 FOUO. Essential reading before the workshop. NIST bulletin, Threats to Computer Systems, March 1994 Neumann, Peter. The Challenges of Insider Misuse. August 1999 10/18/2021 32