Remote Timing Attacks NICOLE HIPPOLITE Side Channel Attacks











- Slides: 20

Remote Timing Attacks NICOLE HIPPOLITE

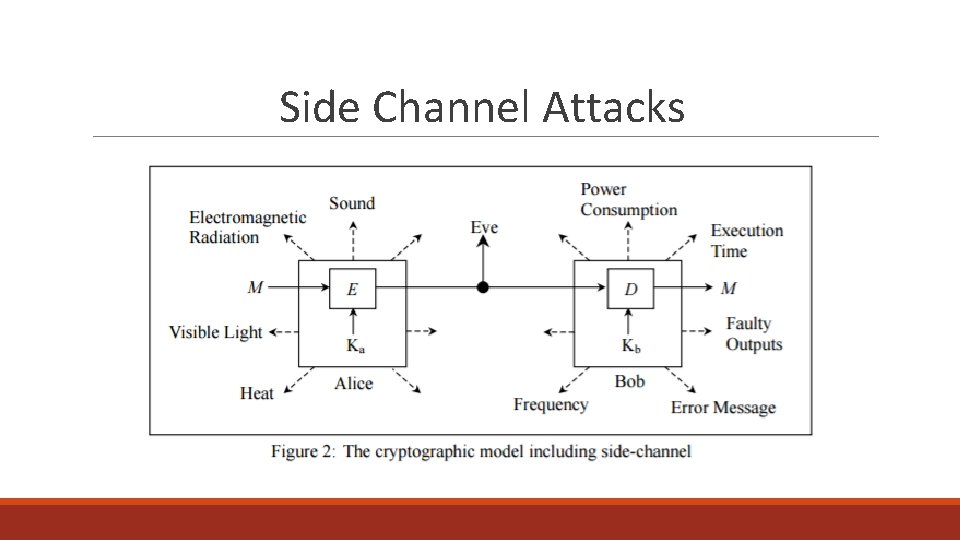
Side Channel Attacks A side channel attack is not a traditional attack ◦ Traditional attacks are things like brute force, ciphertext attack, plaintext attack etc. Attacks that exploit weaknesses in the encryption algorithm ◦ It is not based on mathematical theories but instead, experiments and analysing the results from external factors. ◦ Timing attacks, power consumption attacks, electromagnetic attacks etc. Timing attacks are a type of side channel attack

Side Channel Attacks

Timing Attacks First, gather timed data on a completed decryption of a ciphertext Measure time differences between key/input guesses and computational time taken for the correct key/input Given that an attacker knows the algorithm/implementation used, by analysing these computational times, they can deduce the private key.

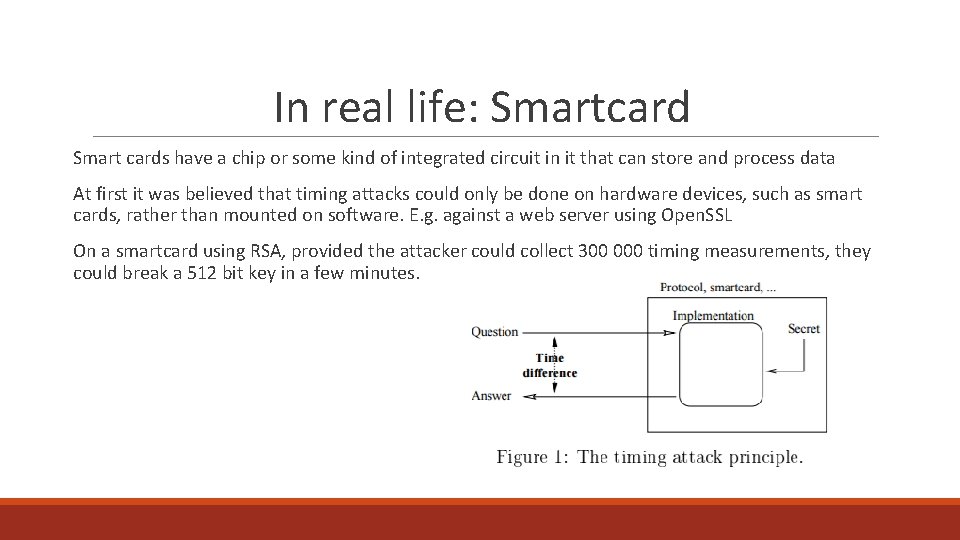
In real life: Smartcard Smart cards have a chip or some kind of integrated circuit in it that can store and process data At first it was believed that timing attacks could only be done on hardware devices, such as smart cards, rather than mounted on software. E. g. against a web server using Open. SSL On a smartcard using RSA, provided the attacker could collect 300 000 timing measurements, they could break a 512 bit key in a few minutes.

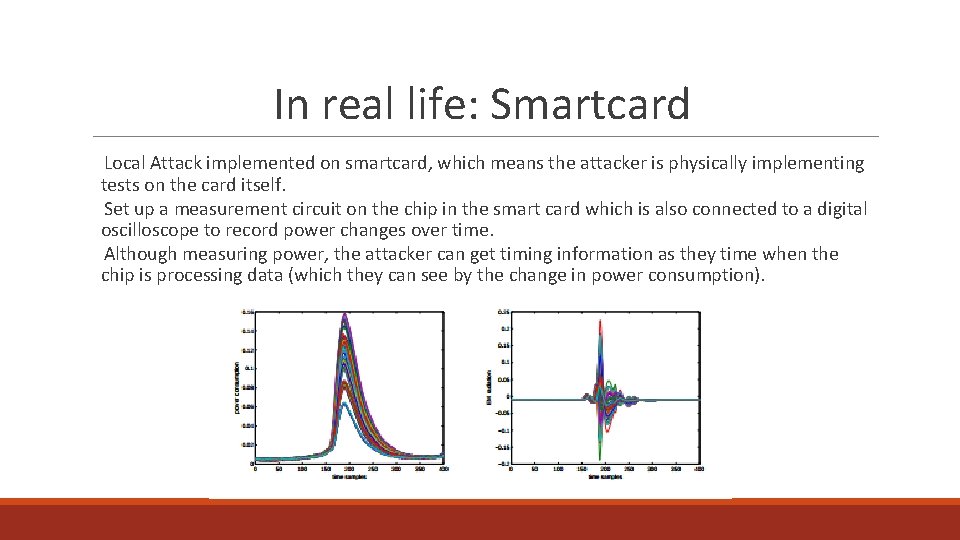
In real life: Smartcard Local Attack implemented on smartcard, which means the attacker is physically implementing tests on the card itself. Set up a measurement circuit on the chip in the smart card which is also connected to a digital oscilloscope to record power changes over time. Although measuring power, the attacker can get timing information as they time when the chip is processing data (which they can see by the change in power consumption).

Remote aspect of timing attacks To implement a Side Channel Attack, the attacker does not have to have possession of the system. Side channel information is visible to everyone, so as long as they know where to look/how to collect the information, they can access it remotely (from a distance). Attackers can gain timing data by eavesdropping on the communication between two parties in the area where decryption/authentication occurs and store all the data so they can compare their query times with it. Can also measure time through the queries they send as they can use code such as read_rdtsc_before() and read_rdtsc_after(), which returns the number of clock ticks that have occured.

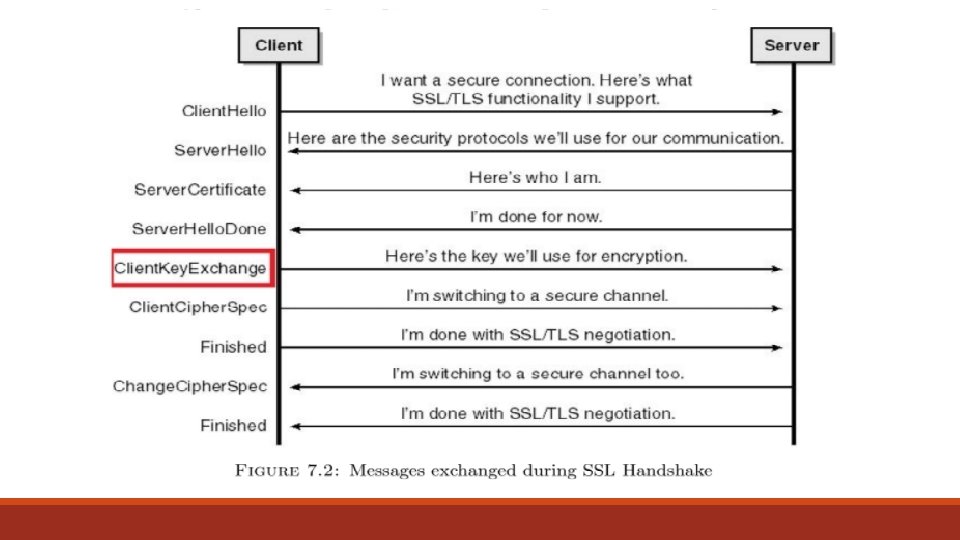
In real life: Open. SSL An attacker sets up an attack client to send messages to the server to decrypt and measure the time it takes to do this. The attacker can target the Client Key Exchange message during the SSL handshake in order to attack the web server as this is where the server decrypts the message using the private key. In a breakthrough in remote timing attacks, Brumley and Boneh showed that it can take ~2 hours to break a 1024 bit RSA private key used in Open. SSL.


Cryptosystems susceptible to timing attacks RSA AES Cache timing Digital signature Algorithm El. Gamal SSL/TLS … I will focus on RSA

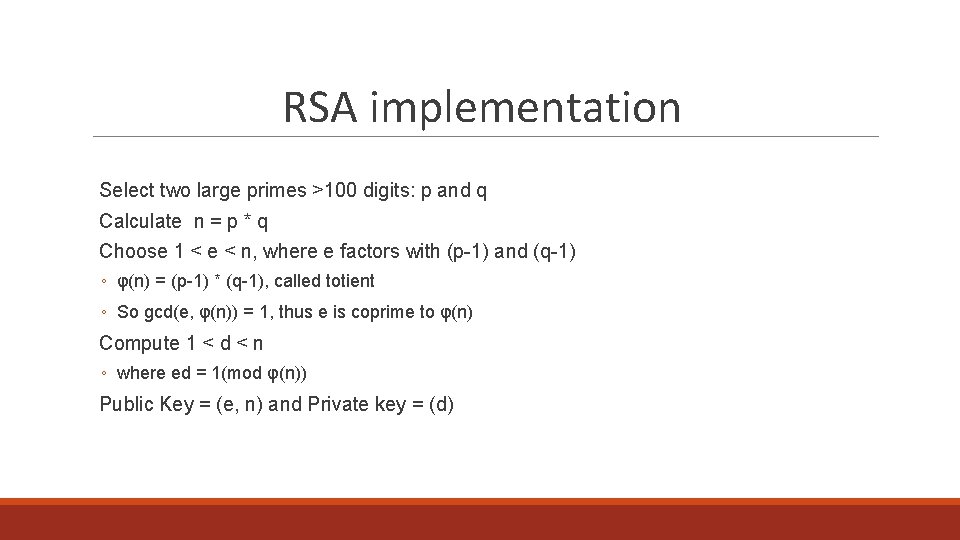
RSA implementation Select two large primes >100 digits: p and q Calculate n = p * q Choose 1 < e < n, where e factors with (p-1) and (q-1) ◦ φ(n) = (p-1) * (q-1), called totient ◦ So gcd(e, φ(n)) = 1, thus e is coprime to φ(n) Compute 1 < d < n ◦ where ed = 1(mod φ(n)) Public Key = (e, n) and Private key = (d)

Timing attacks on RSA is a common public key cryptosystem to be exploited by timing attacks Encryption: c = me mod n Decryption: m = cd mod n Can use simple multiplication, square and multiply or other, more complex, theorems for modular exponentiation

Simple multiplication Modular exponentiation multiplies the number as many times as the value of the exponent: ◦ 25 = 2 x 2 x 2 This means that the execution time is directly related to the exponent value.

Simple multiplication timing weakness So an attacker would eavesdrop to get the plaintext and computation time but wants to figure out the decryption key. Lets say key = 10 He makes a guess (encrypts the plaintext with his key guess ), 11, which returns a time greater than the computational time. Then he guesses 9, which returns a time smaller than the computational time. So he knows key = 10 (for simplicity assume key = whole number)

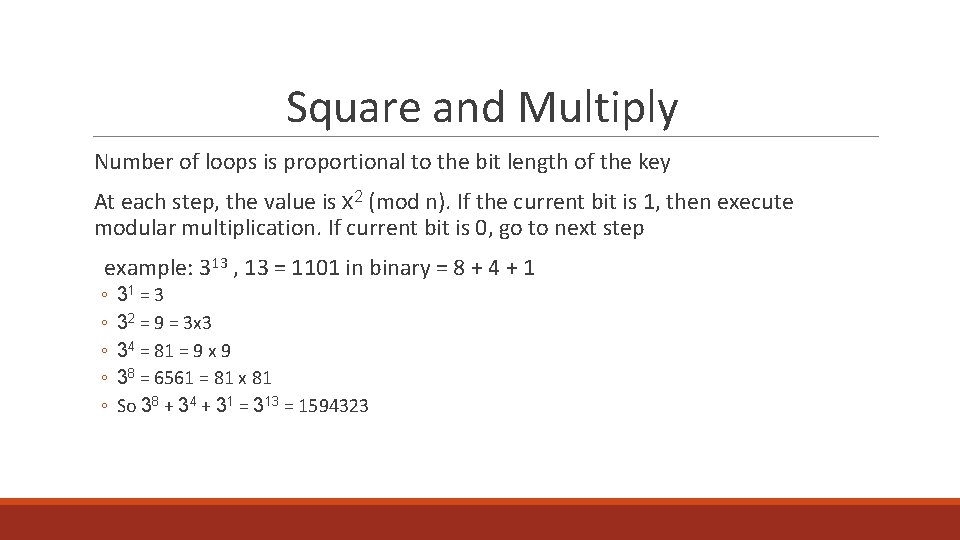
Square and Multiply Number of loops is proportional to the bit length of the key At each step, the value is x 2 (mod n). If the current bit is 1, then execute modular multiplication. If current bit is 0, go to next step example: 313 , 13 = 1101 in binary = 8 + 4 + 1 ◦ ◦ ◦ 31 = 3 32 = 9 = 3 x 3 34 = 81 = 9 x 9 38 = 6561 = 81 x 81 So 38 + 34 + 31 = 313 = 1594323

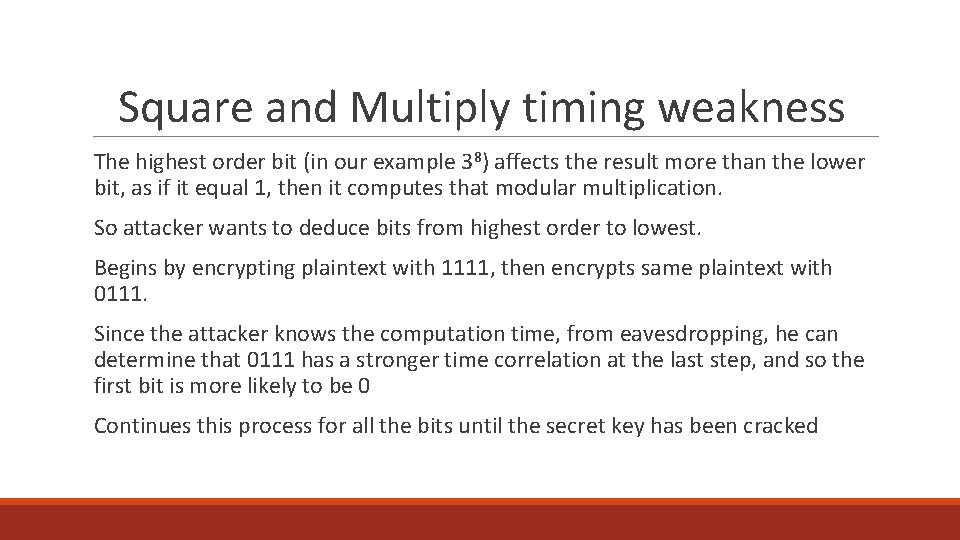
Square and Multiply timing weakness The highest order bit (in our example 38) affects the result more than the lower bit, as if it equal 1, then it computes that modular multiplication. So attacker wants to deduce bits from highest order to lowest. Begins by encrypting plaintext with 1111, then encrypts same plaintext with 0111. Since the attacker knows the computation time, from eavesdropping, he can determine that 0111 has a stronger time correlation at the last step, and so the first bit is more likely to be 0 Continues this process for all the bits until the secret key has been cracked

I’ve just scratched the surface These are just an introduction as to how timing attacks work, there are many more examples for more complicated cryptosystems such as elliptic curve cryptosystems and AES, as well as exploitations on algorithms that are supposed to prevent side channel attacks, such as Montgomery’s ladder and the lattice algorithm (These can be exploited if not implemented correctly).

Countermeasures One of the main ways to prevent timing attacks is to make it so the computation time for decryption is constant or randomised regardless of the input. ◦ E. g. Can be done by avoiding conditional operations (equal time) ◦ E. g. can be done by waiting random time before moving onto next execution For RSA, a typical method implemented to prevent timing attacks is called blinding.

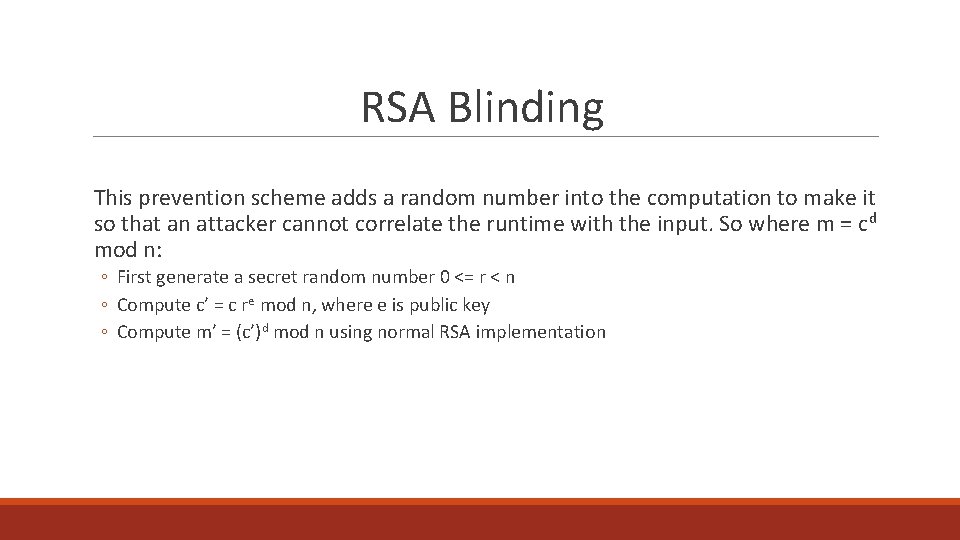
RSA Blinding This prevention scheme adds a random number into the computation to make it so that an attacker cannot correlate the runtime with the input. So where m = c d mod n: ◦ First generate a secret random number 0 <= r < n ◦ Compute c’ = c re mod n, where e is public key ◦ Compute m’ = (c’)d mod n using normal RSA implementation

Questions? ? ?