Remote Control System The hacking suite for governmental


















































- Slides: 71

Remote Control System The hacking suite for governmental interception Mostapha Maanna Key Account Manager Alessandro Scarafile Field Application Engineer Milan - 30/08/2012

HACKINGTEAM Funded in 2003 Venture backed in 2007

Market leader in Italy for Ethical Hacking and Penetration Test. 2004 a new technology. RCS

Growing fast. Really fast. Customers in 5 continents.

A strong development team. A strong research team. Fast release cycles. You get new features every few months.

Committed to the best quality.

On site delivery. Comprehensive training. Dedicated access to our support.

Your data is yours. And yours only. No way for us to have access to your RCS.

You supervise the use of your RCS, to prevent abuse.

Can you intercept Skype calls? Can you open PGP encrypted files?

Skype adoption is growing fast. People trust it for confidential communications. Criminals too.

There’s more.

Everyone uses the Web. It’s cheap, easy and global.

The new Web is the social web. Highly dynamic. Vastly networked. Big data.

Actually, too much data. Difficult to correlate.

Tap a cable and try to figure out what’s happening. 99% of that is of no interest.

Interesting data often never gets to the Web. It stays on the device.

And that device may be out of reach. Linked to the Internet. But anywhere on Earth.

What you already have? Traditional passive interception. Not effective against encryption. You lose half the picture. Must pass through your network.

So what we want? Get access to secret data. Figure out the interesting parts. Reach them, anywhere they are.

Invisible to antiviruses. Autonomous on selective events. Easily adaptable. Management is straightforward.

Integrate it with your systems. Scale up to your needs. Prevent disclosure of your presence.

Traditional is good. Innovative is better.

Thinking about offensive interception? You should.

“Governments must have offensive IT capabilities. ” The Financial Times

“Spy on suspected terrorists by inserting a remote forensic agent on their computers. ” The Economist

A remote forensic agent. Clever idea. A sort of 007 for the digital age.

We have it.

Remote Control System


Evidence collection is always running. Configurable behavior. Autonomous.

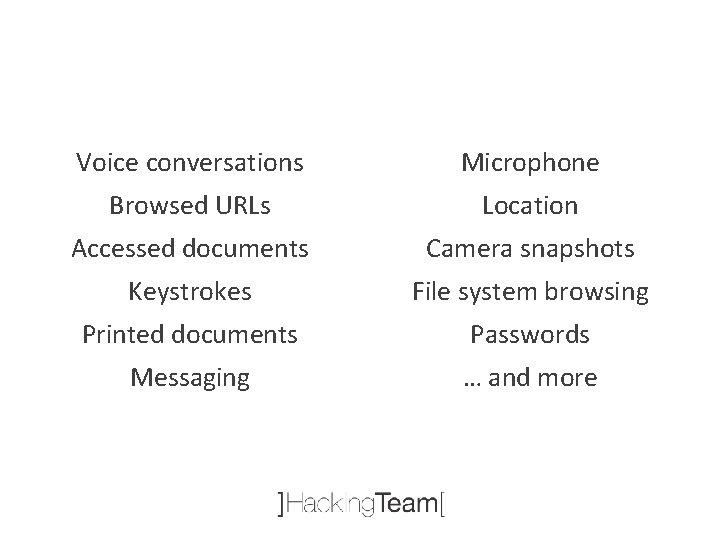
What kind of evidences can be collected?

Voice conversations Microphone Browsed URLs Location Accessed documents Camera snapshots Keystrokes File system browsing Printed documents Passwords Messaging … and more

RCS collected the evidences. They stay on remote device. How can we gather them?

Let’s talk about Desktops first.

Internet connection. Firewalls and proxies are passed through. Domain credentials are stolen.

Evidence can also be collected offline.

What about mobile platforms?

GPRS / UMTS / 3 G+. You can provide a custom APN.

Open Wi. Fi networks. Known protected networks. Access Points are automatically detected.

What happens if someone tracks the connection back?

Anonymizer Chain. Prevents disclosure of RCS server addresses. Configurable on-the-fly.


RCS is also flexible.

Real-time alerting system. Custom commands execution on remote target. Event-driven logic.

A few examples of event-driven logic.

When entering the meeting room, start the mic. On low battery, stop microphone capture. Special SMS is received, send back a SMS with position. Call is made or received, take a snapshot with the camera.

Combine them to suit your needs.

What if my target is very skilled?

Invisible to target user. Invisible to antivirus and anti-rootkits. Anti-forensic measures. Resistant to Deep. Freeze restoration.

How can I install it on desktop systems?

Embed RCS into common file formats (0 -day exploits). On-the-fly injection into downloaded applications. Webpage code injection during browsing.


I’m lucky. Physical access is granted.

Bootable CDROM or USB thumb drive.

What about installation on mobiles?

Memory Card. Active. Sync while synchronizing or charging. Embed RCS into smartphone applications. Over-the-Air installation.

Supported platforms?

Our agents are the best. On all platforms.

Install them on Windows.

Mac.

i. Phone.

i. Pad.

Windows Mobile.

Symbian.

Black. Berry.

Android.

Soon on Linux.

“Cool, but I have to install the agents first, and that’s the difficult part: you have to be an hacker to do that stuff. ”

Wrong. Remote Control System is easy. Everything is just one click away.

We’re going to show you. Demo time