Remote Access What is the Remote Access Domain
























- Slides: 28

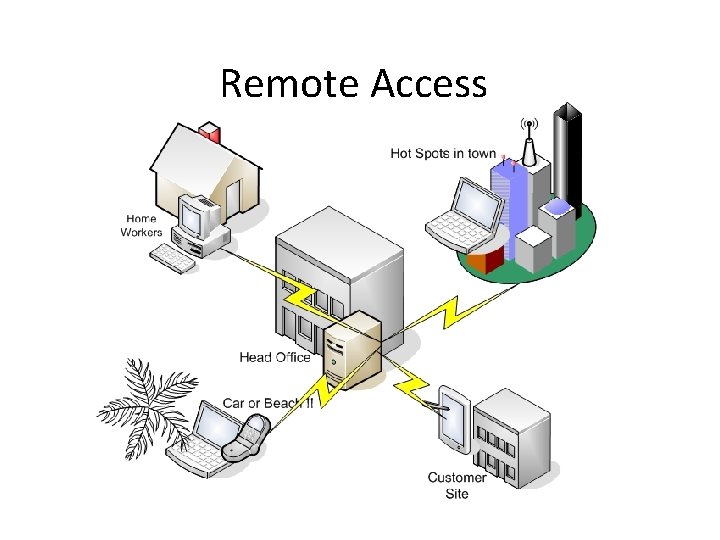
Remote Access

What is the Remote Access Domain? • remote access: the ability for an organization’s users to access its non-public computing resources from external locations other than the organization’s facilities

Dangers of Remote Access EPIDEMIC! Peeping Toms! www. top 10 always. com www. redbubble. com

Rule #1 • NEVER share logon credentials with anyone. www. simplenomics. com

Rule #2 • Use strong and memorable passwords. – www. passwordmeter. com

Rule #3 • Do not use public devices. – Library workstations – Kiosks – Web cafes • STARBUCKS www. patsyearnshaw. co. uk

Rule #4 • Do not use personal devices. – If use of personal device is necessary, no copying. www. puntacantv. com

Rule #5 • Use only company email for remote business. www. thinkprogress. org

Rule #6 • Implement anti-virus and anti-spyware. – Run them continuously. – Update them. www. dailyadvisor. net

Rule #7 • Ensure you are only connected to one network at a time. • No split-tunneling or dual homing. BAD

Rule #8 • Only use “administrator” profile to update profile or make system changes. www. iconfinder. com

Cloud computing • What is it? • What are and aren’t safe practices?

• Wireless technology standard for exchanging data over short distances using short-wavelength radio transmissions. – Disable when not being used – Use a PIN that is at least 8 characters long combining numbers and letters if possible

Infrared connection (Ir. DA) • Infrared technology allows computing devices to communicate via short-range wireless signals. – Turn off when not using – Requires line of site, don’t use in crowded area around a lot of people – To keep secure, do in a private area in close range (4 to 20 “ apart)

Near Field Communication (NFC)

Near Field Communication (NFC) • NFC uses Radio Frequency Identification Technology to transmit information over very short distances (centimeters or less) • Turn off when not using feature • Don’t use tags that aren’t secured • Don’t exchange info with individuals you don’t trust • Look at phone to see what actions the tag prompts. Is there anything suspicious?

Quick Response (QR) Codes • Use a QR scanner that shows the URL and asks if you want to go there. • Don’t give out personal information or login credentials to any sites you’re directed to. • Look out for suspicious QR Codes like ones on stickers stuck over original QR codes.

Cell Phone Basics Phones, tablets, etc. 1. Only download applications from sites you trust and only after checking each apps’ rating and reading the user reviews to make sure it is widely used and respected. 2. Set a password on your phone 3. Watch for suspicious links 4. Be careful what you do at unsecured Wi. Fi hotspots or don’t use at all. 5. Keep spyware from watching you *

Cell Phone Spyware • No good way to be 100% sure phone is not compromised • Factory reset done by provider should in theory remove any spyware (also lose all files, photos, etc. stored on the phone). • Anti Spyware apps do exist not certain how effective they are. • Generally requires physical contact with target phone to install. Could also get in through SMS messages and Bluetooth connections. • May notice strange sounds, background noise, decrease in battery life, phone being warm when it hasn’t been used, phone “lighting up for no reason.

Social Networking

Examples of Social Networking Platforms Blogs, micro blogs Wikis Photo and video sharing, podcasts Virtual worlds, exp. WOW Social news, web conferencing, and webcasting • Facebook, Twitter, Foursquare, Youtube, Yahoo groups, etc. • • •

What is Social Networking? • Means of interaction among people in which they create, share, and exchange information and ideas in virtual communities and networks • Depend on mobile and web-based applications to create a platform in which user content can be shared • Communication between organizations, communities and individuals

Social Networking Guidelines • Do not post discriminatory, harassing, or threating messages or images • Do not post anything that would embarrass you or the company and thereby affect the company’s reputation • Do not share confidential material, trade secrets, or proprietary information • Respect copyright, fair use, and disclosure laws

Social Networking Guidelines • Make sure when posting information that you use a disclaimer that the ideas are your own and are in no way affiliated with the company • Restrict social networking to personal time and not during company time • Do not share personal information about employees, vendors, or clients

Risks of Social Networking • Malicious applications can compromise network security • The company reputation could be in jeopardy • Once information is public the more vulnerable you become • Exploitation • Data leaks • Impersonation

Sources • http: //csrc. nist. gov/publications/nistpubs/800 -46 -rev 1/sp 800 -46 r 1. pdf • http: //www. rd. com/advice/saving-money/5 -simple-steps-to-keep-your-cell-phonesecure/ • http: //simson. net/ref/security_cellphones. htm • http: //www. personalprotectionsystems. ca/the-digital-sheepdog/my-son-brandonrocking-it. html • http: //www. rd. com/advice/saving-money/5 -simple-steps-to-keep-your-cell-phonesecure/ • http: //csrc. nist. gov/publications/nistpubs/800 -114/SP 800 -114. pdf • http: //electronics. howstuffworks. com/how-secure-is-nfc-tech. htm • http: //www. onlineqrlab. com/qr-code-nfc-security. php • http: //www. tripwire. com/state-of-security/it-security-data-protection/malicious-qr -codes • http: //www. forbes. com/sites/andygreenberg/2012/07/27/how-to-bust-your-bossor-loved-one-for-installing-spyware-on-your-phone/ • http: //technet. microsoft. com/en-us/library/cc 737210(v=ws. 10). aspx • http: //www. csoonline. com/article/217829/infrared-networking-seeing-infrared

Sources Continued • http: //www. forbes. com/sites/andygreenberg/2012/07/27/how-to-bust-your-bossor-loved-one-for-installing-spyware-on-your-phone/ • http: //pugetsoundblogs. com/side-street-news/2011/03/05/is-there-spyware-onyour-cell-phone/#axzz 2 NARjbf. RN • http: //www. ehow. com/how_4811719_prevent-cell-phone-spyware. html • http: //www. wired. com/politics/security/news/2005/07/68370 • http: //www. youtube. com/watch? feature=player_embedded&v=y. K 97 Drk. FJF 0 • http: //www. mobile-spy. com/ • http: //csrc. nist. gov/publications/nistpubs/800 -46 -rev 1/sp 800 -46 r 1. pdf • http: //www. rd. com/advice/saving-money/5 -simple-steps-to-keep-your-cell-phonesecure/ • http: //simson. net/ref/security_cellphones. htm • http: //www. personalprotectionsystems. ca/the-digital-sheepdog/my-son-brandonrocking-it. html

Sources Continued • NIST Special Publication 800 -46 • http: //aws. amazon. com/vpc/faqs/ • Columbia University Remote Access Acceptable Usage Policy • http: //www. babson. edu/offices-services/itsc/about/policies/Pages/remoteaccess. aspx