Reliability of Wireless Sensors with Code Attestation for

Reliability of Wireless Sensors with Code Attestation for Intrusion Detection Presented by: Yating Wang

Outline �Background �Code attestation �Problem definition �Modeling �Calculation �Performance and Analysis �Conclusion
Background Security properties: authentication secrecy data integrity Security issues for Wireless Sensor Networks(WSN) Outsider attacks (key management) Insider attacks (Intrusion detection) •
Code Attestation �A software based method (verifier) �Assumption: original codes must be changed when sensors are compromised �Basic method: the trusted verifier evaluates the sensor compromised or not by comparing memory value (hash value) with its original value.
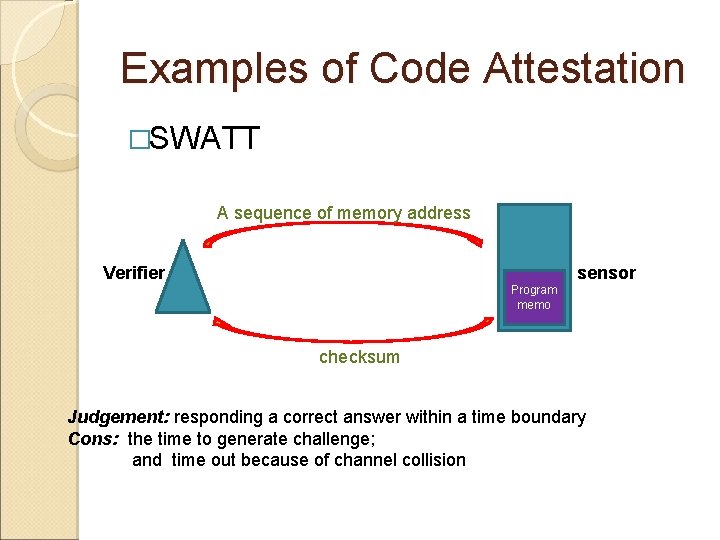
Examples of Code Attestation �SWATT A sequence of memory address Verifier sensor Program memo checksum Judgement: responding a correct answer within a time boundary Cons: the time to generate challenge; and time out because of channel collision
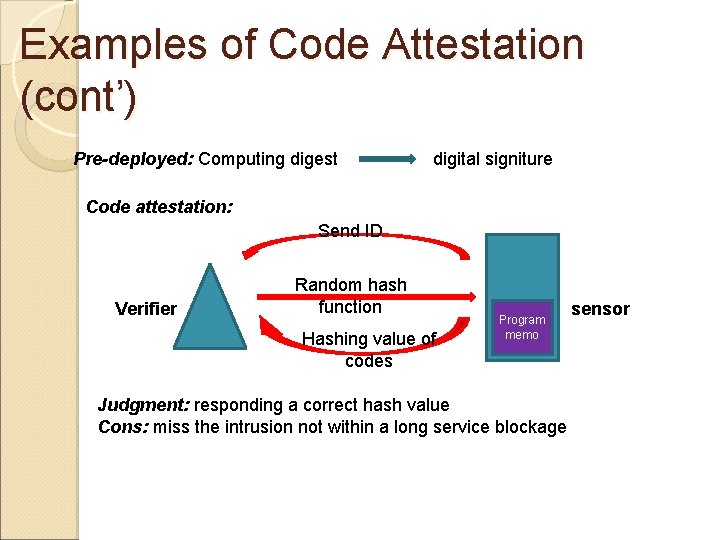
Examples of Code Attestation (cont’) Pre-deployed: Computing digest digital signiture Code attestation: Send ID Verifier Random hash function Hashing value of codes Program memo Judgment: responding a correct hash value Cons: miss the intrusion not within a long service blockage sensor
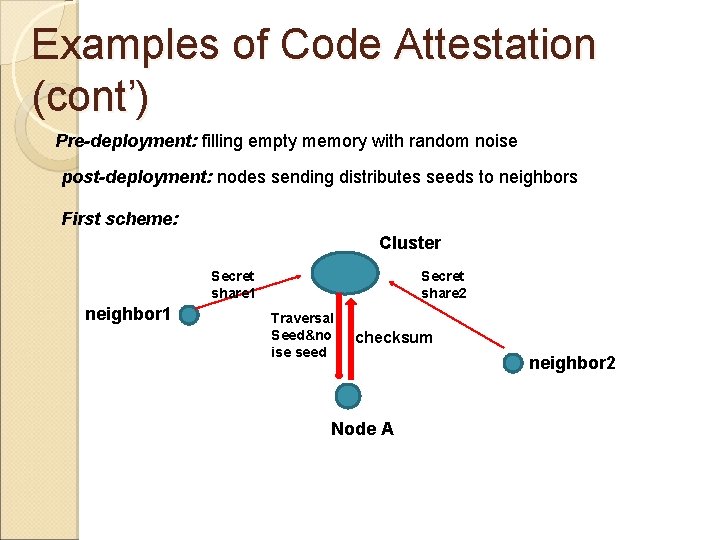
Examples of Code Attestation (cont’) Pre-deployment: filling empty memory with random noise post-deployment: nodes sending distributes seeds to neighbors First scheme: Cluster Secret share 1 neighbor 1 Secret share 2 Traversal Seed&no ise seed checksum Node A neighbor 2
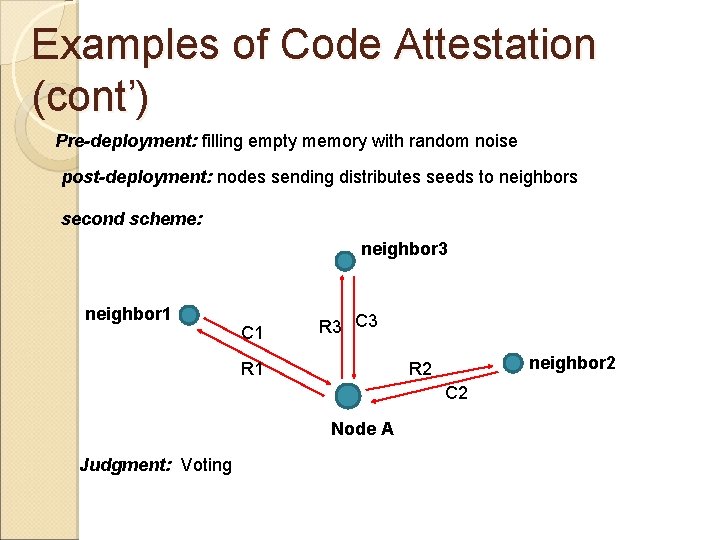
Examples of Code Attestation (cont’) Pre-deployment: filling empty memory with random noise post-deployment: nodes sending distributes seeds to neighbors second scheme: neighbor 3 neighbor 1 C 1 R 3 C 3 R 1 neighbor 2 R 2 C 2 Node A Judgment: Voting
Problem Definition �Problem: the trade-off between energy consumption and code attestation; when should we trigger code attestation �Purpose: Maximizing reliability measured by Mean Time to Fail(MTTF) * Fail: either the sensor’s energy is depleted; or the sensor returns false
Modeling System activities � Periodic sensing (plus transmitting) sensing interval – T; unit energy consumption – Es;
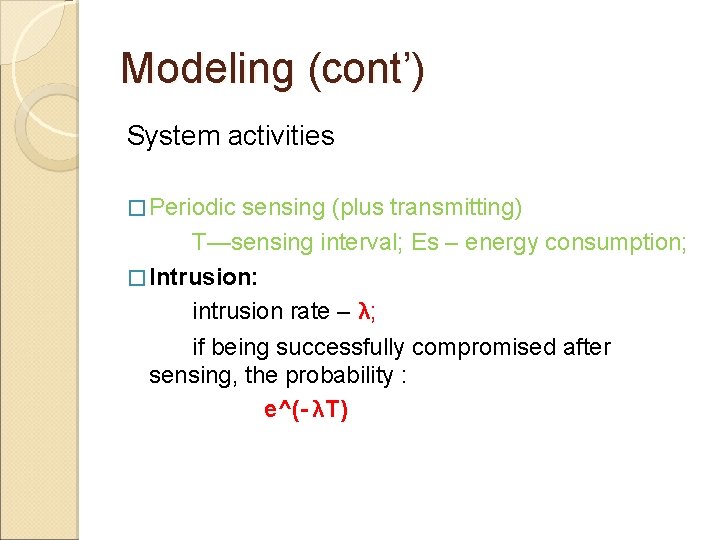
Modeling (cont’) System activities � Periodic sensing (plus transmitting) T—sensing interval; Es – energy consumption; � Intrusion: intrusion rate – λ; if being successfully compromised after sensing, the probability : e^(- λT)
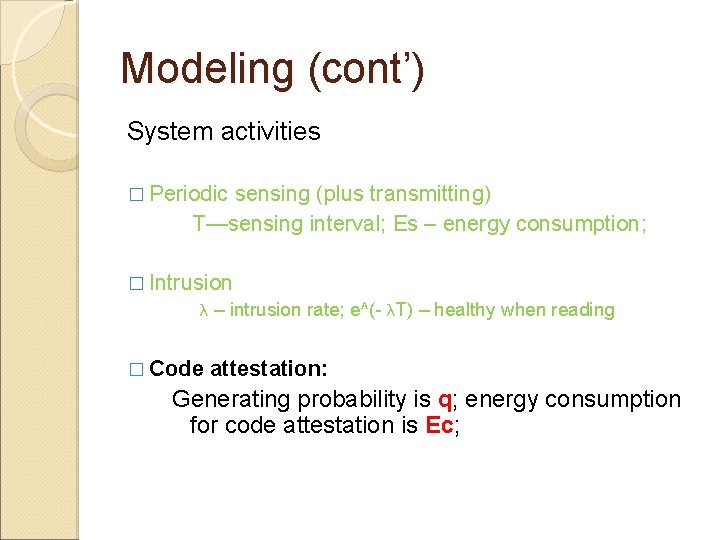
Modeling (cont’) System activities � Periodic sensing (plus transmitting) T—sensing interval; Es – energy consumption; � Intrusion λ – intrusion rate; e^(- λT) – healthy when reading � Code attestation: Generating probability is q; energy consumption for code attestation is Ec;
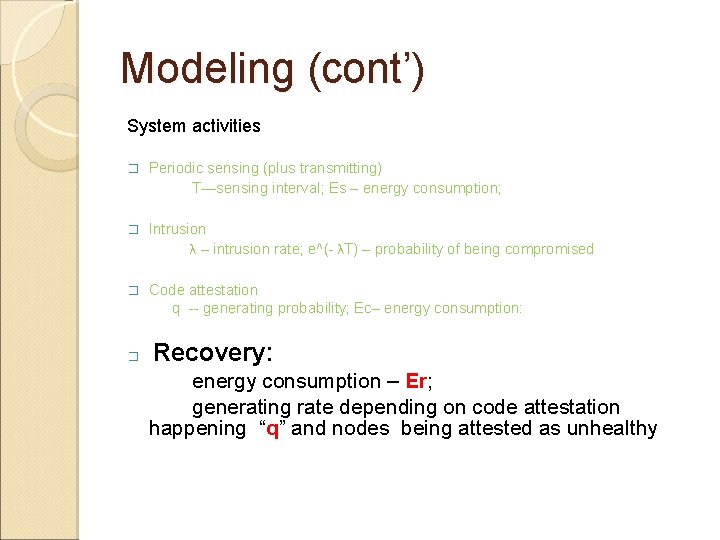
Modeling (cont’) System activities � Periodic sensing (plus transmitting) T—sensing interval; Es – energy consumption; � Intrusion λ – intrusion rate; e^(- λT) – probability of being compromised � Code attestation q -- generating probability; Ec– energy consumption: � Recovery: energy consumption – Er; generating rate depending on code attestation happening “q” and nodes being attested as unhealthy

Calculation �Recovery probability case 1: compromised before sensing prob(x<T) = 1 -e^(- λT) code attestation generated before sensing: prob(attestation happening) = q(1 -e ^(λT) ) the false node being recovered: prob 1(recover) = q(1 -e ^(- λT) )(1 -Pfn)

Calculation (cont’) � Case 2: uncompromised in a sensing round; prob(x>T) = e^(-λT) the code attestation still happened though prob(attestation happening) = q*e ^(-λT) recovery triggered prob 2(recovery) = q*e ^(-λT)*Pfp So the probability of recovery happening during code attestation is: θ = (prob 1 + prob 2)/q
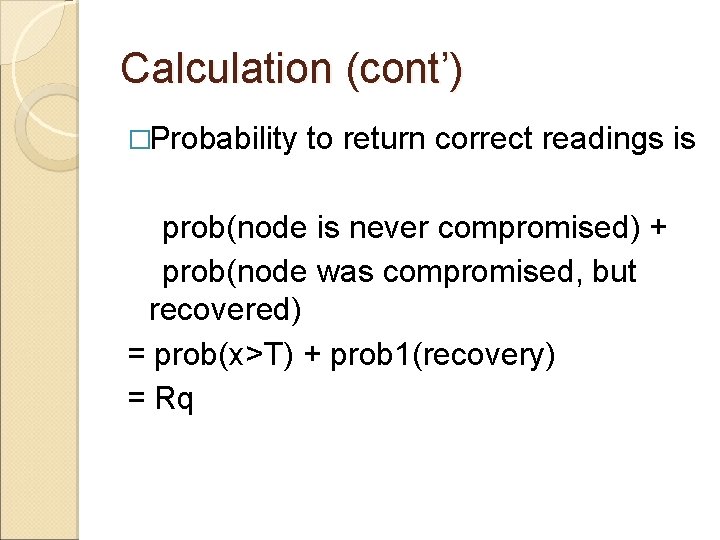
Calculation (cont’) �Probability to return correct readings is prob(node is never compromised) + prob(node was compromised, but recovered) = prob(x>T) + prob 1(recovery) = Rq
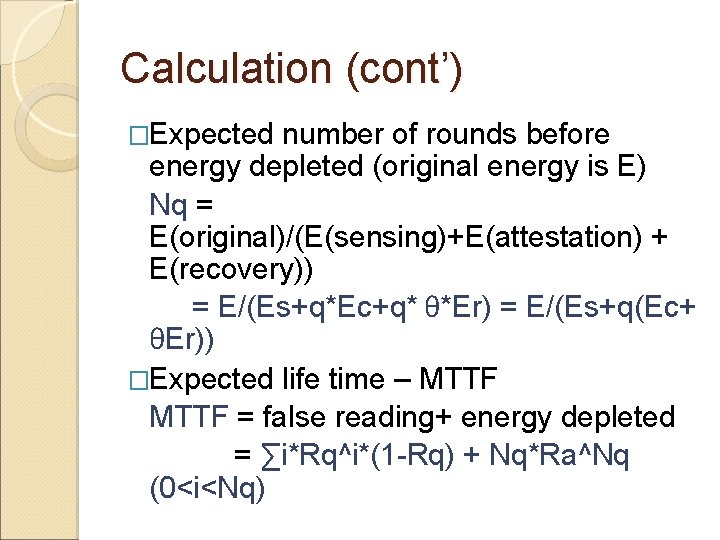
Calculation (cont’) �Expected number of rounds before energy depleted (original energy is E) Nq = E(original)/(E(sensing)+E(attestation) + E(recovery)) = E/(Es+q*Ec+q* θ*Er) = E/(Es+q(Ec+ θEr)) �Expected life time – MTTF = false reading+ energy depleted = ∑i*Rq^i*(1 -Rq) + Nq*Ra^Nq (0<i<Nq)
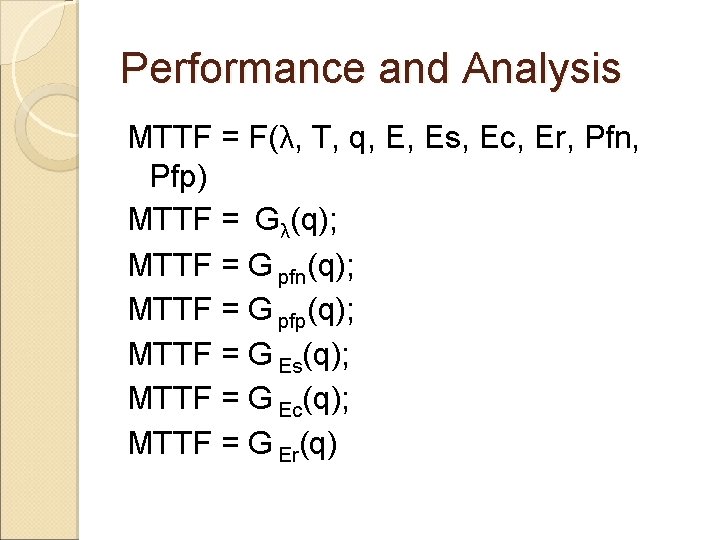
Performance and Analysis MTTF = F(λ, T, q, E, Es, Ec, Er, Pfn, Pfp) MTTF = Gλ(q); MTTF = G pfn(q); MTTF = G pfp(q); MTTF = G Es(q); MTTF = G Ec(q); MTTF = G Er(q)
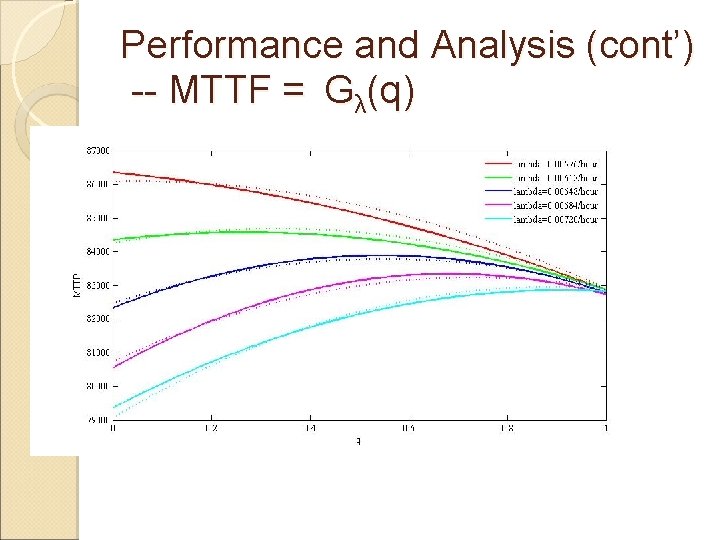
Performance and Analysis (cont’) -- MTTF = Gλ(q)
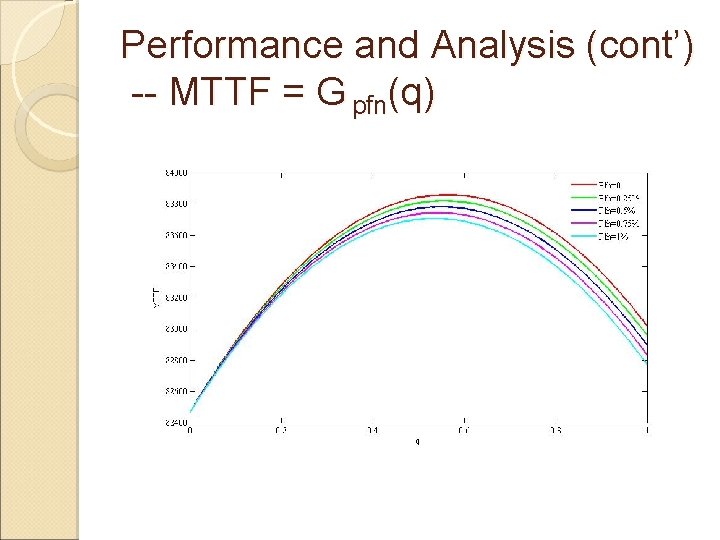
Performance and Analysis (cont’) -- MTTF = G pfn(q)
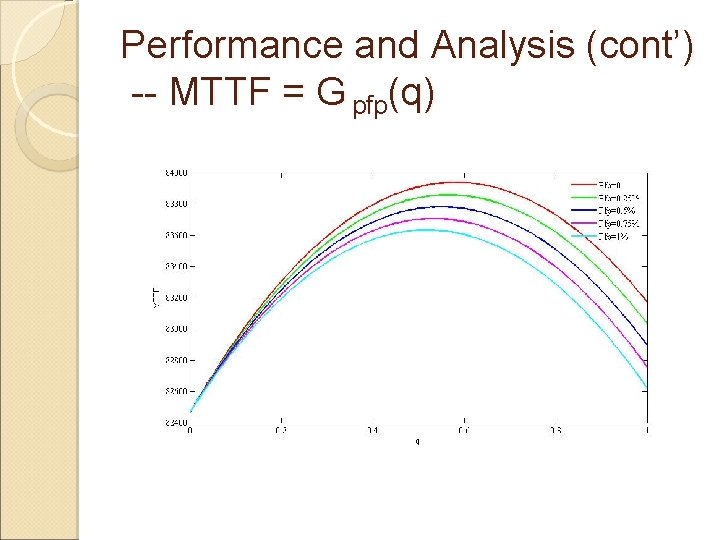
Performance and Analysis (cont’) -- MTTF = G pfp(q)
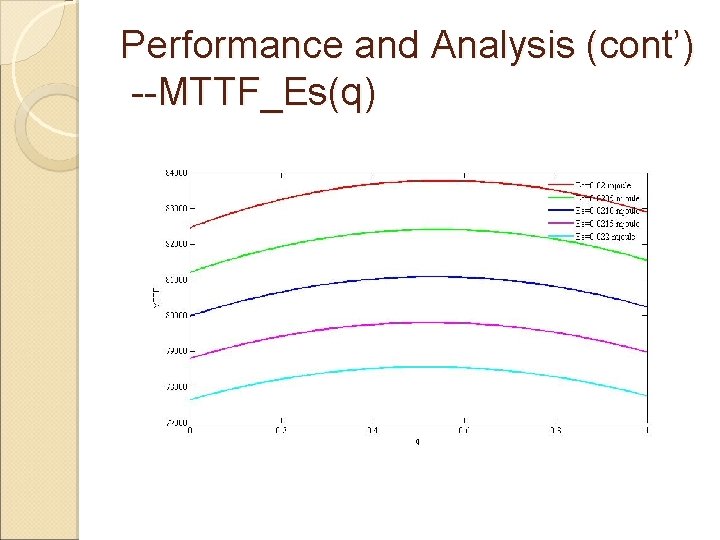
Performance and Analysis (cont’) --MTTF_Es(q)
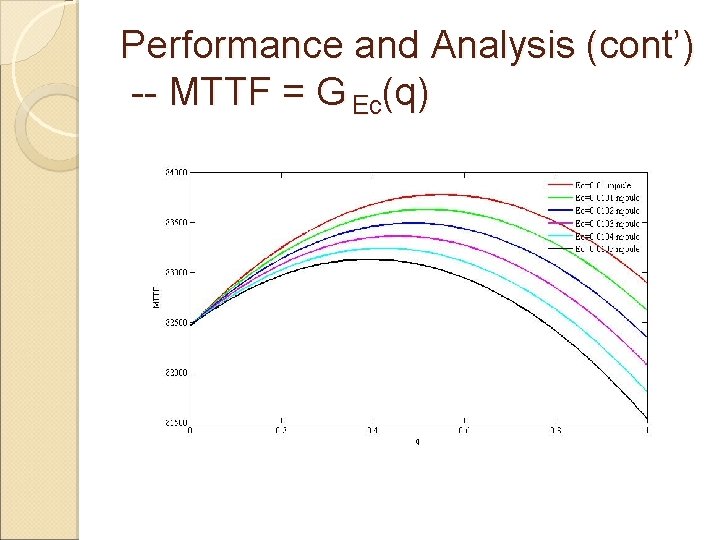
Performance and Analysis (cont’) -- MTTF = G Ec(q)
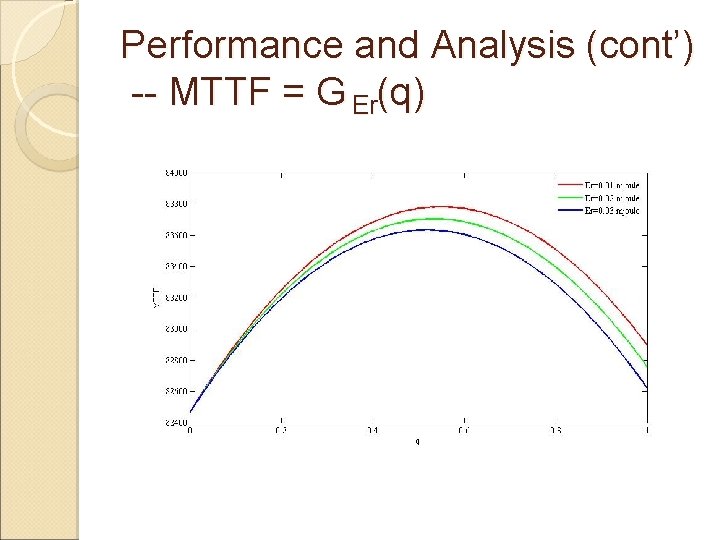
Performance and Analysis (cont’) -- MTTF = G Er(q)
Conclusion �Developing a probability model to analyze how often code attestation should be generated to maximize the lifetime; �Results showing that there is always an optimal q which can make sensor’s reliability maximized �Showing that code attestation should be generated more frequently when λ is high, Pfn(Pfp) is low, Ec is low, or Er is low compared with Es
- Slides: 25