Reliability and availability requirements engineering within the Unified

Reliability and availability requirements engineering within the Unified Process using a Dependability Analysis and Modeling profile Simona Bernardi, Università di Torino José Merseguer, Universidad de Zaragoza Robyn R. Lutz, Iowa State University
Outline l l Improve elicitation, documentation and analysis of R&A sw requirements within the Unified Process (UP) Extension of the requirement workflow to handle R&AR – – l 2 Step-by-step incremental process Use of a UML profile (DAM) to 1) specify R&AR and 2) characterize system faults/failures Application to an intrusion-tolerant, distributed firewall for critical information infrastructures (CRUTIAL IST project)
Motivation l l 3 Toward the definition of a methodology for the synergetic use of dependability techniques within the UP Why the Unified Process (UP) ? – Incremental & iterative: manages risks and handles changes in sw projects better than waterfall models – Uses UML as its specification language – Can be customized for different kind of sw systems/application domains UP pays little attention to non-functional reqs Several UML profiles exist that help to gather NFPs – MARTE OMG standard profile – DAM profile for dependability NFPs
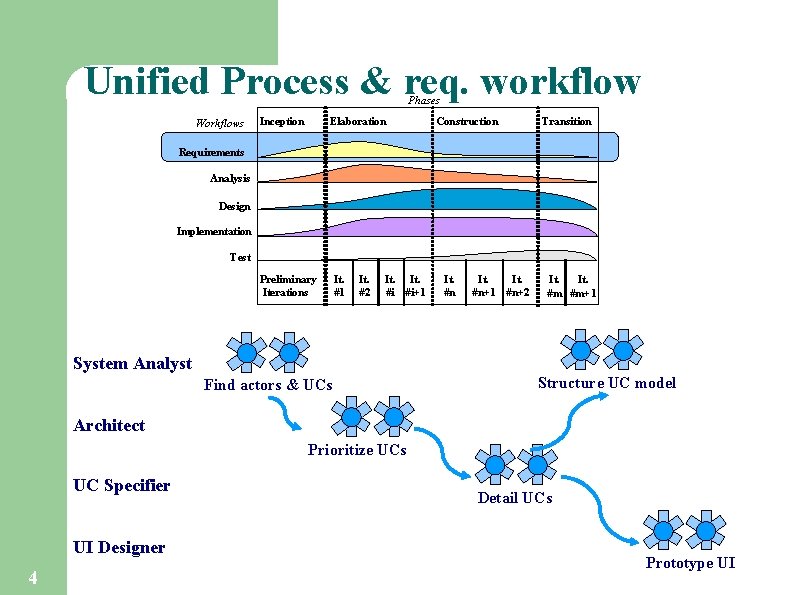
Unified Process & req. workflow Phases Workflows Inception Elaboration Construction Transition Requirements Analysis Design Implementation Test Preliminary Iterations It. #1 It. #2 It. #i #i+1 It. #n+1 #n+2 It. #m #m+1 System Analyst Find actors & UCs Structure UC model Architect Prioritize UCs UC Specifier UI Designer 4 Detail UCs Prototype UI

The set of dependability reqs specification techniques l l (Mis)Use cases IEEE Std. 830 -1998 – l l 5 IEEE Recommended practise for sw requirements specification DAM profile Fault Trees
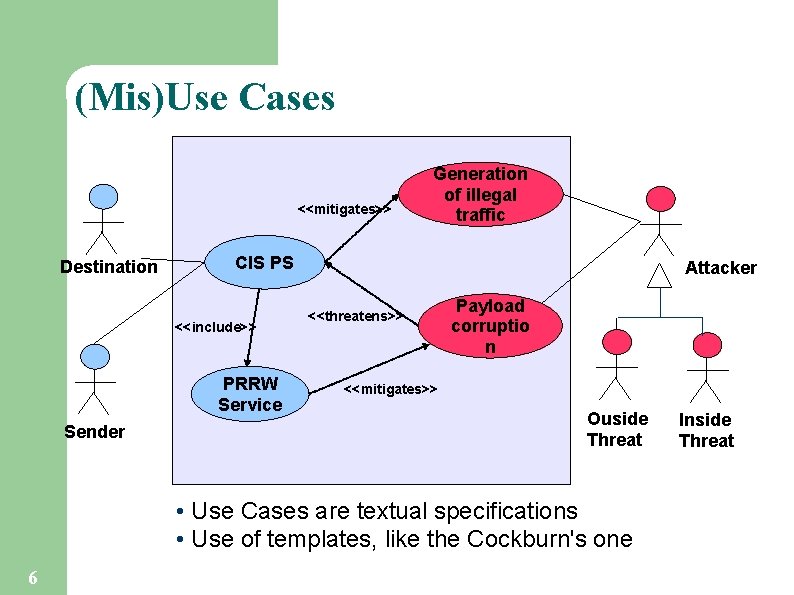
(Mis)Use Cases <<mitigates>> Destination CIS PS <<include>> PRRW Service Sender Generation of illegal traffic Attacker <<threatens>> Payload corruptio n <<mitigates>> Ouside Threat • Use Cases are textual specifications • Use of templates, like the Cockburn's one 6 Inside Threat
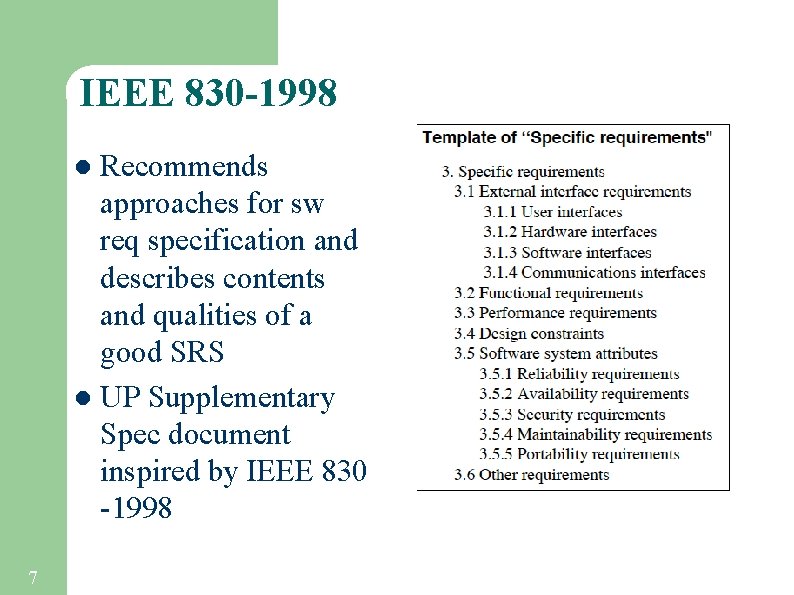
IEEE 830 -1998 Recommends approaches for sw req specification and describes contents and qualities of a good SRS l UP Supplementary Spec document inspired by IEEE 830 -1998 l 7
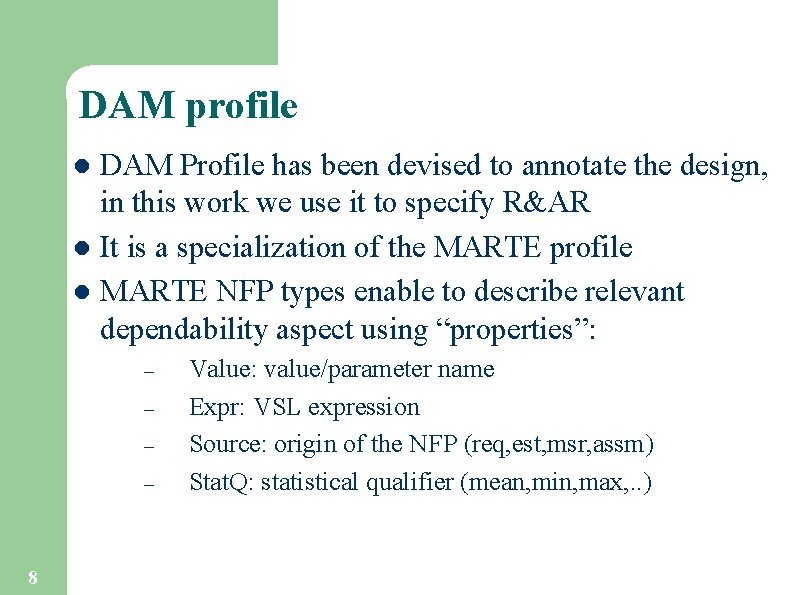
DAM profile DAM Profile has been devised to annotate the design, in this work we use it to specify R&AR l It is a specialization of the MARTE profile l MARTE NFP types enable to describe relevant dependability aspect using “properties”: l – – 8 Value: value/parameter name Expr: VSL expression Source: origin of the NFP (req, est, msr, assm) Stat. Q: statistical qualifier (mean, min, max, . . )

Fault Trees l 9 FTs are used to l Gather information about the potential contributing causes to threats l Trace the combination of faults/failures to misuse and use cases
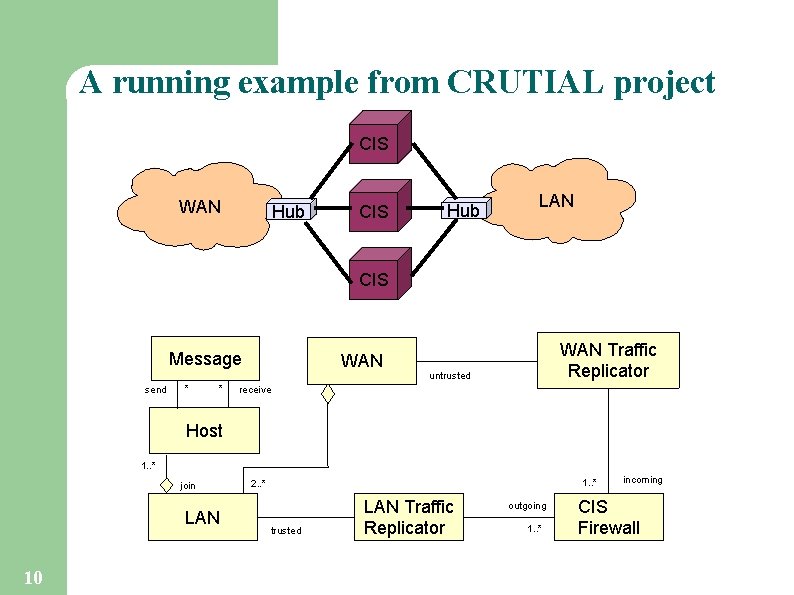
A running example from CRUTIAL project CIS WAN Hub CIS Hub LAN CIS Message send * * WAN Traffic Replicator untrusted receive Host 1. . * join LAN 10 1. . * 2. . * trusted LAN Traffic Replicator outgoing 1. . * incoming CIS Firewall
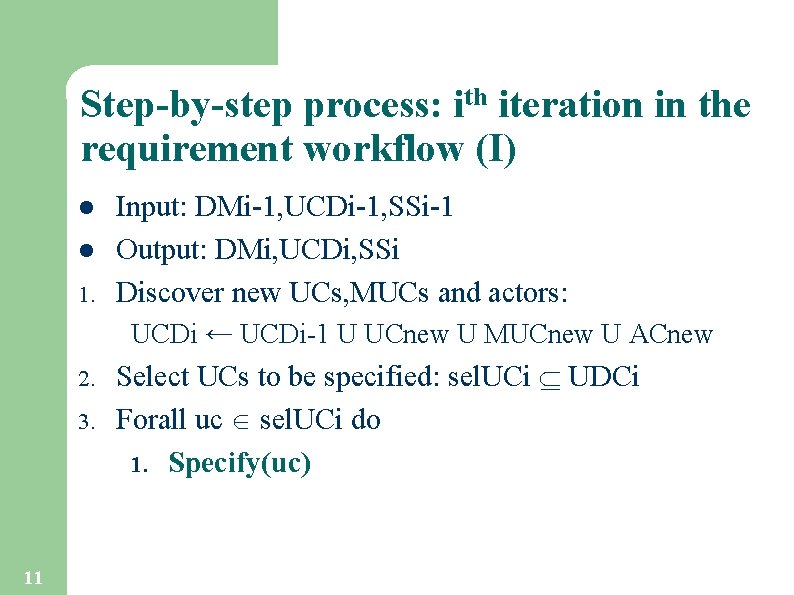
Step-by-step process: ith iteration in the requirement workflow (I) l l 1. Input: DMi-1, UCDi-1, SSi-1 Output: DMi, UCDi, SSi Discover new UCs, MUCs and actors: UCDi ← UCDi-1 U UCnew U MUCnew U ACnew 2. 3. 11 Select UCs to be specified: sel. UCi UDCi Forall uc sel. UCi do 1. Specify(uc)

UC specify activity l l 12 Textual description of the UC using Cockburn template R&AR from the Special Requirement section – Application of DAM profile for rewriting them in a standard and disciplined form
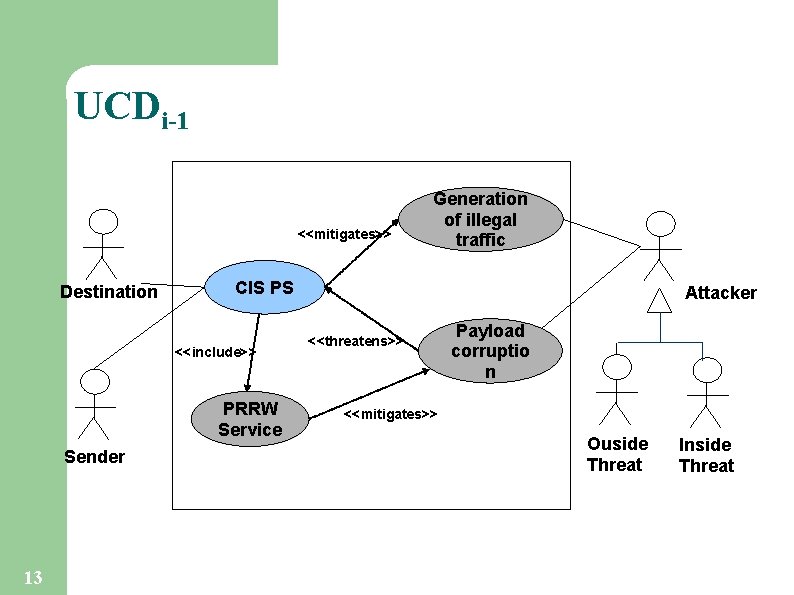
UCDi-1 <<mitigates>> Destination CIS PS <<include>> PRRW Service Sender 13 Generation of illegal traffic Attacker <<threatens>> Payload corruptio n <<mitigates>> Ouside Threat Inside Threat
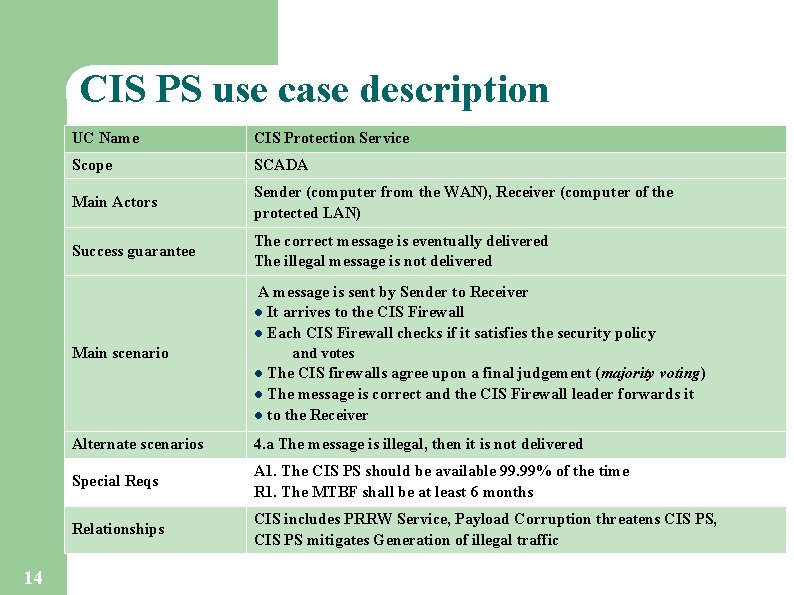
CIS PS use case description UC Name CIS Protection Service Scope SCADA Main Actors Sender (computer from the WAN), Receiver (computer of the protected LAN) Success guarantee The correct message is eventually delivered The illegal message is not delivered A message is sent by Sender to Receiver l It arrives to the CIS Firewall l Each CIS Firewall checks if it satisfies the security policy Main scenario and votes The CIS firewalls agree upon a final judgement (majority voting) l The message is correct and the CIS Firewall leader forwards it l to the Receiver l 14 Alternate scenarios 4. a The message is illegal, then it is not delivered Special Reqs A 1. The CIS PS should be available 99. 99% of the time R 1. The MTBF shall be at least 6 months Relationships CIS includes PRRW Service, Payload Corruption threatens CIS PS, CIS PS mitigates Generation of illegal traffic
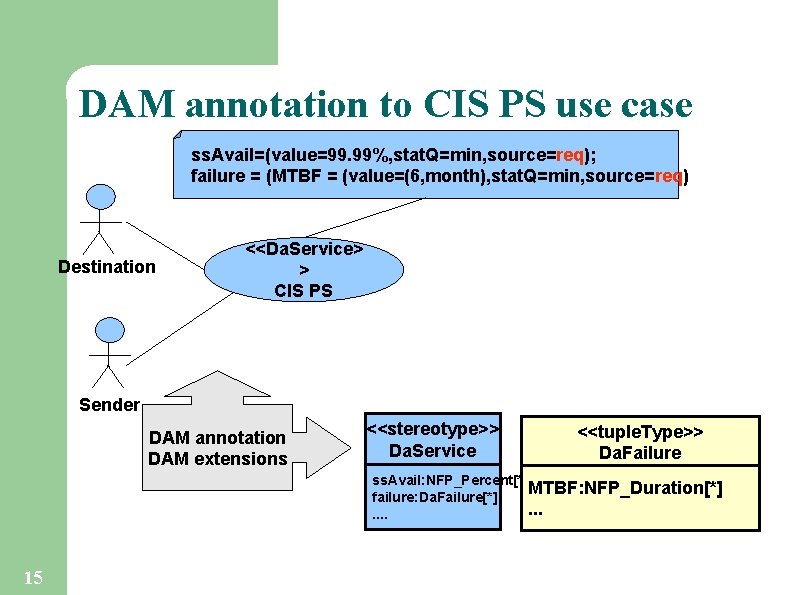
DAM annotation to CIS PS use case ss. Avail=(value=99. 99%, stat. Q=min, source=req); failure = (MTBF = (value=(6, month), stat. Q=min, source=req) Destination <<Da. Service> > CIS PS Sender DAM annotation DAM extensions <<stereotype>> Da. Service <<tuple. Type>> Da. Failure ss. Avail: NFP_Percent[*] MTBF: NFP_Duration[*] failure: Da. Failure[*]. . . . 15
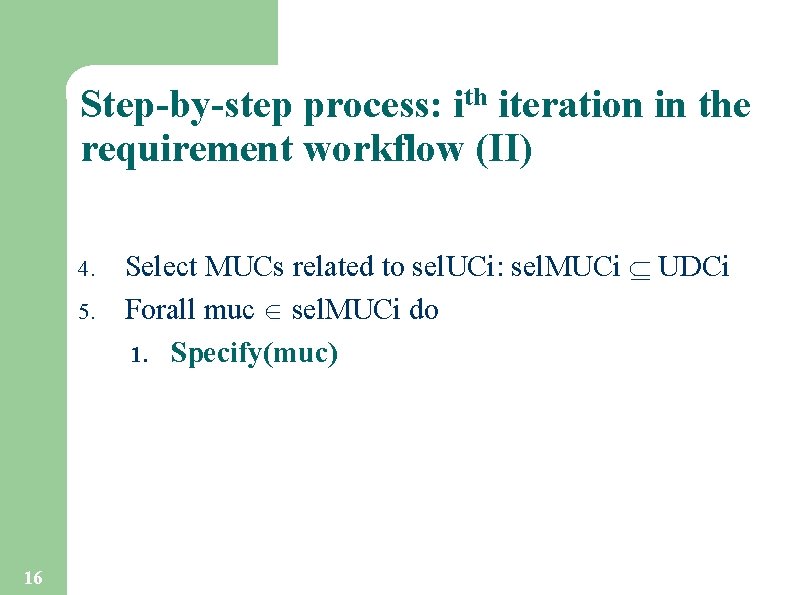
Step-by-step process: ith iteration in the requirement workflow (II) 4. 5. 16 Select MUCs related to sel. UCi: sel. MUCi UDCi Forall muc sel. MUCi do 1. Specify(muc)
MUC specify activity • Textual description of the MUC using Cockburn template • Threats information from Success guarantee, Main/Alternate scenario and Other Reqs sections • Application of the DAM profile to characterize from both a qualitative/quantitative viewpoints faults/failures • Faults Trees are used to formally specify UCD relationships • Among Negative Actor actions and Misuse Case success • Among Misuse Cases and related Use Case 17
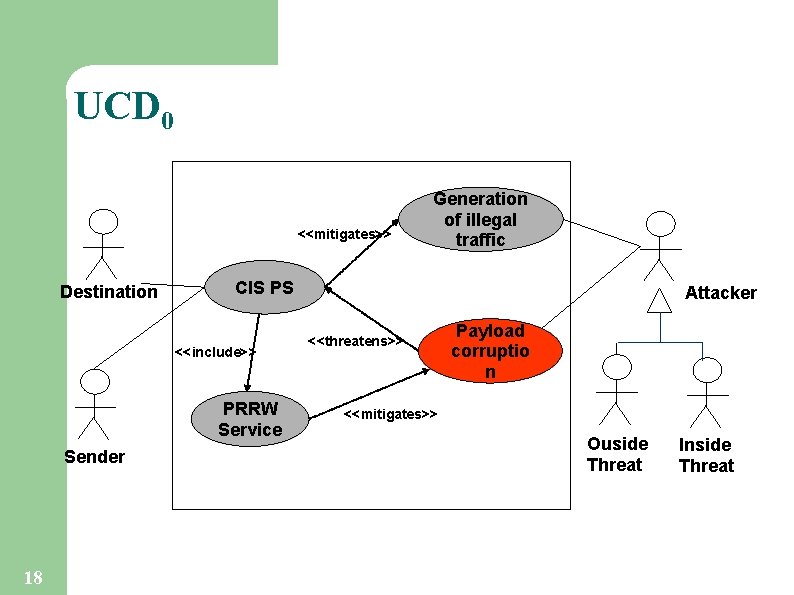
UCD 0 <<mitigates>> Destination CIS PS <<include>> PRRW Service Sender 18 Generation of illegal traffic Attacker <<threatens>> Payload corruptio n <<mitigates>> Ouside Threat Inside Threat
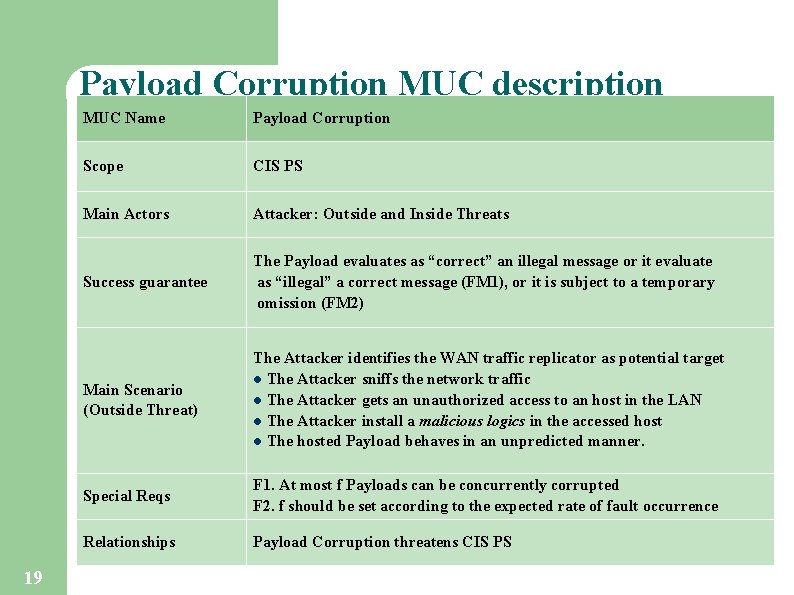
Payload Corruption MUC description 19 MUC Name Payload Corruption Scope CIS PS Main Actors Attacker: Outside and Inside Threats Success guarantee The Payload evaluates as “correct” an illegal message or it evaluate as “illegal” a correct message (FM 1), or it is subject to a temporary omission (FM 2) Main Scenario (Outside Threat) The Attacker identifies the WAN traffic replicator as potential target l The Attacker sniffs the network traffic l The Attacker gets an unauthorized access to an host in the LAN l The Attacker install a malicious logics in the accessed host l The hosted Payload behaves in an unpredicted manner. Special Reqs F 1. At most f Payloads can be concurrently corrupted F 2. f should be set according to the expected rate of fault occurrence Relationships Payload Corruption threatens CIS PS
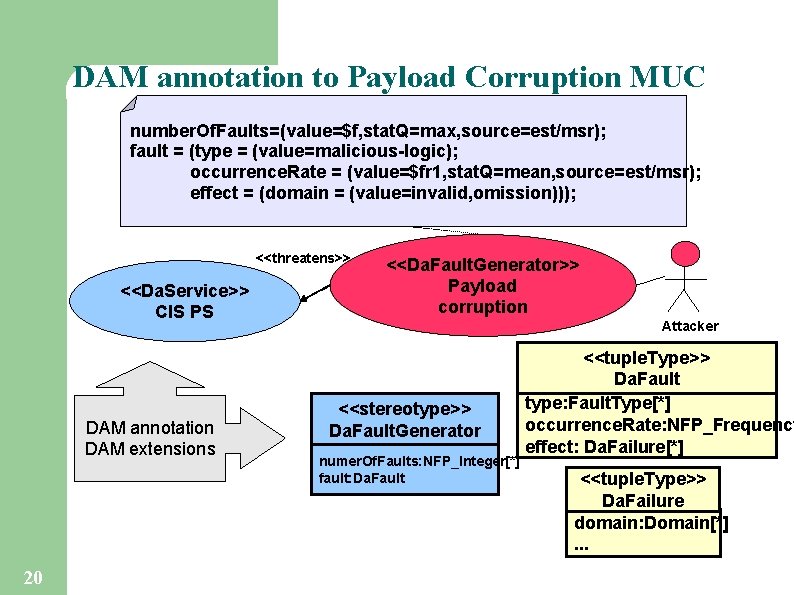
DAM annotation to Payload Corruption MUC number. Of. Faults=(value=$f, stat. Q=max, source=est/msr); fault = (type = (value=malicious-logic); occurrence. Rate = (value=$fr 1, stat. Q=mean, source=est/msr); effect = (domain = (value=invalid, omission))); <<threatens>> <<Da. Service>> CIS PS DAM annotation DAM extensions 20 <<Da. Fault. Generator>> Payload corruption Attacker <<stereotype>> Da. Fault. Generator numer. Of. Faults: NFP_Integer[*] fault: Da. Fault <<tuple. Type>> Da. Fault type: Fault. Type[*] occurrence. Rate: NFP_Frequency effect: Da. Failure[*] <<tuple. Type>> Da. Failure domain: Domain[*]. . .
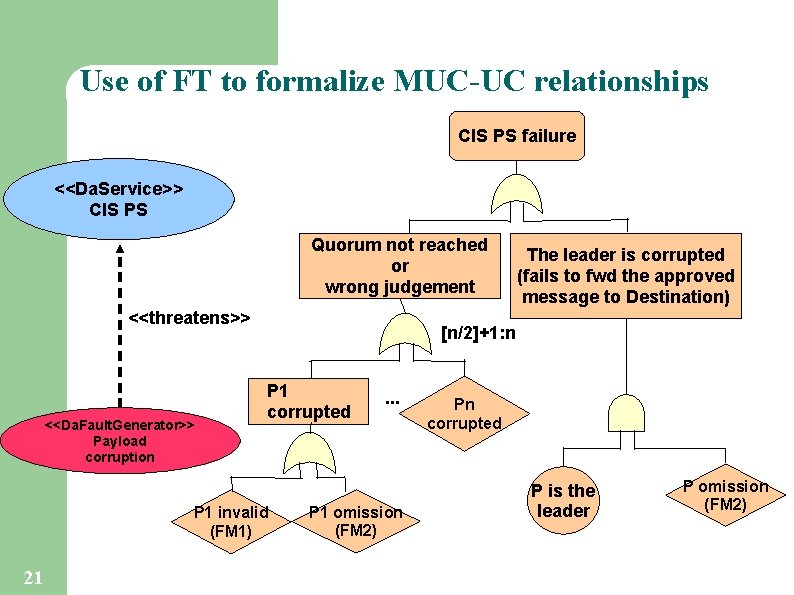
Use of FT to formalize MUC-UC relationships CIS PS failure <<Da. Service>> CIS PS Quorum not reached or wrong judgement <<threatens>> <<Da. Fault. Generator>> Payload corruption [n/2]+1: n P 1 corrupted P 1 invalid (FM 1) 21 The leader is corrupted (fails to fwd the approved message to Destination) . . . P 1 omission (FM 2) Pn corrupted P is the leader P omission (FM 2)

Step-by-step process: ith iteration in the requirement workflow (III) 6. 7. 8. 9. 22 Discover new NFRs: SSi ← SSi-1 U NFRnew Select a subset of requirements: sel. NFRi SSi Forall nfr sel. NFRi do 1. Elaborate(nfr) Restructure UCDi and DMi if necessary

NFR elaboration activity l Rewriting of further NFR from the SS, related to dependability/fault-tolerance with the DAM profile – 23 Annotation in the Domain Model/Use Case Diagrams
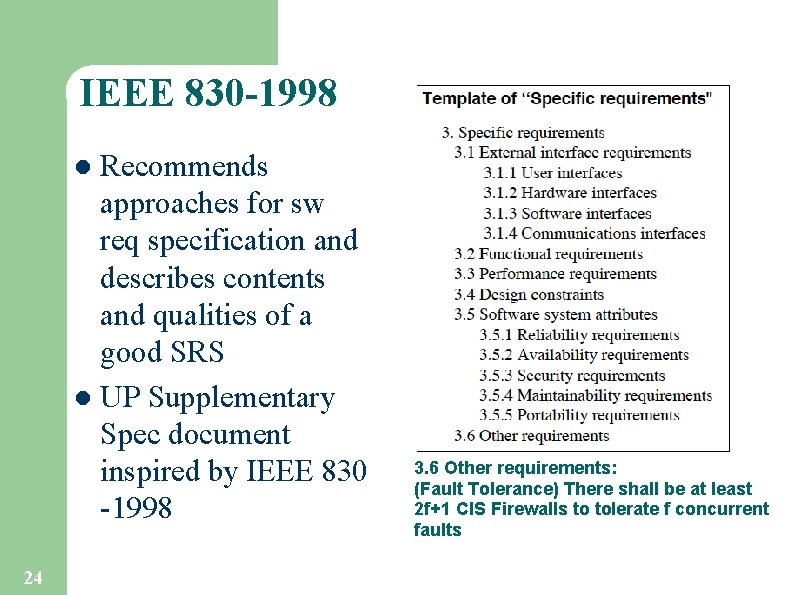
IEEE 830 -1998 Recommends approaches for sw req specification and describes contents and qualities of a good SRS l UP Supplementary Spec document inspired by IEEE 830 -1998 l 24 3. 6 Other requirements: (Fault Tolerance) There shall be at least 2 f+1 CIS Firewalls to tolerate f concurrent faults
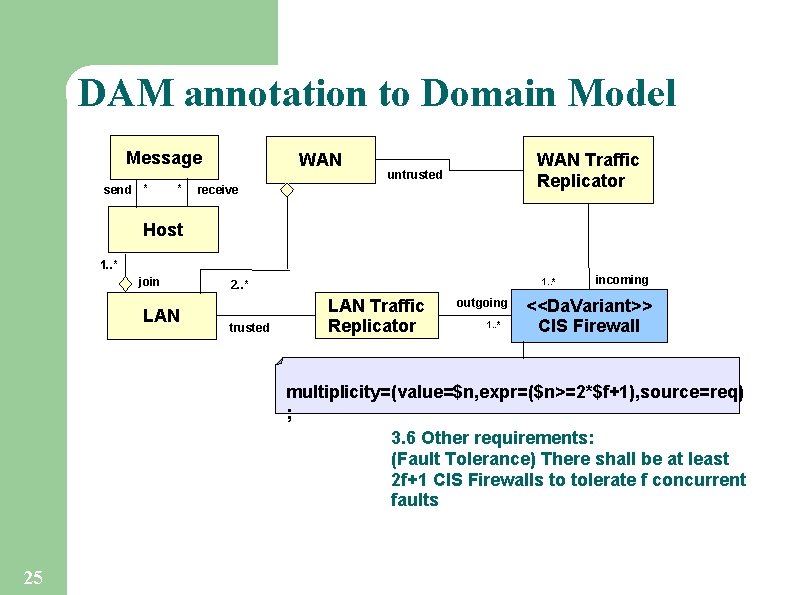
DAM annotation to Domain Model Message send * * WAN Traffic Replicator untrusted receive Host 1. . * join LAN 1. . * 2. . * trusted LAN Traffic Replicator outgoing 1. . * incoming <<Da. Variant>> CIS Firewall multiplicity=(value=$n, expr=($n>=2*$f+1), source=req) ; 3. 6 Other requirements: (Fault Tolerance) There shall be at least 2 f+1 CIS Firewalls to tolerate f concurrent faults 25
Conclusions l l 26 The DAM annotated UML artifacts (UCD, DM) provide input for the other UP workflows (design, test, . . ) as well as for V&V activities Next steps: l Study of the DAM applicability in the other UP workflows l V&V activities driven by DAM annotated M(UC)s

Thank you! 27
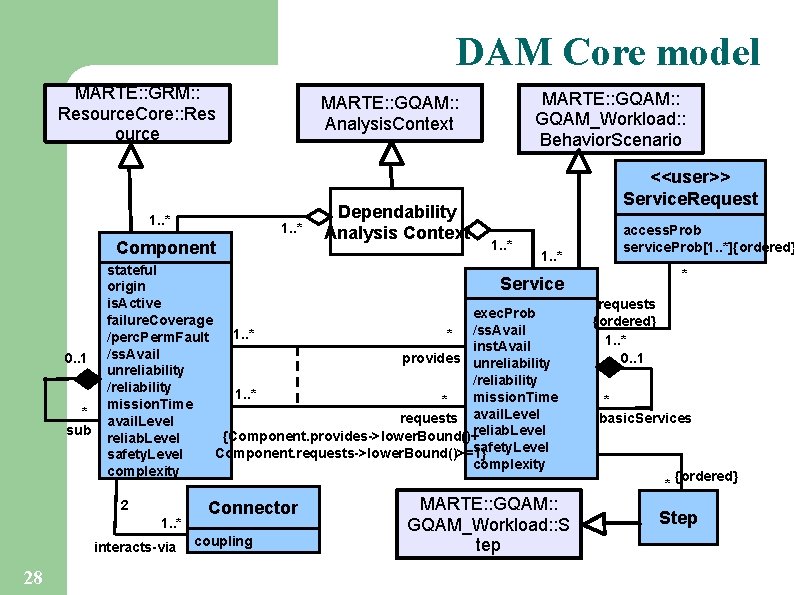
DAM Core model MARTE: : GRM: : Resource. Core: : Res ource 1. . * Component 0. . 1 * sub Dependability Analysis Context <<user>> Service. Request 1. . * stateful Service origin is. Active exec. Prob failure. Coverage 1. . * * /ss. Avail /perc. Perm. Fault inst. Avail /ss. Avail provides unreliability /reliability 1. . * mission. Time requests avail. Level {Component. provides->lower. Bound()+reliab. Level safety. Level Component. requests->lower. Bound()>=1} safety. Level complexity 2 1. . * interacts-via 28 MARTE: : GQAM_Workload: : Behavior. Scenario MARTE: : GQAM: : Analysis. Context Connector coupling MARTE: : GQAM_Workload: : S tep access. Prob service. Prob[1. . *]{ordered} * requests {ordered} 1. . * 0. . 1 * basic. Services * {ordered} Step
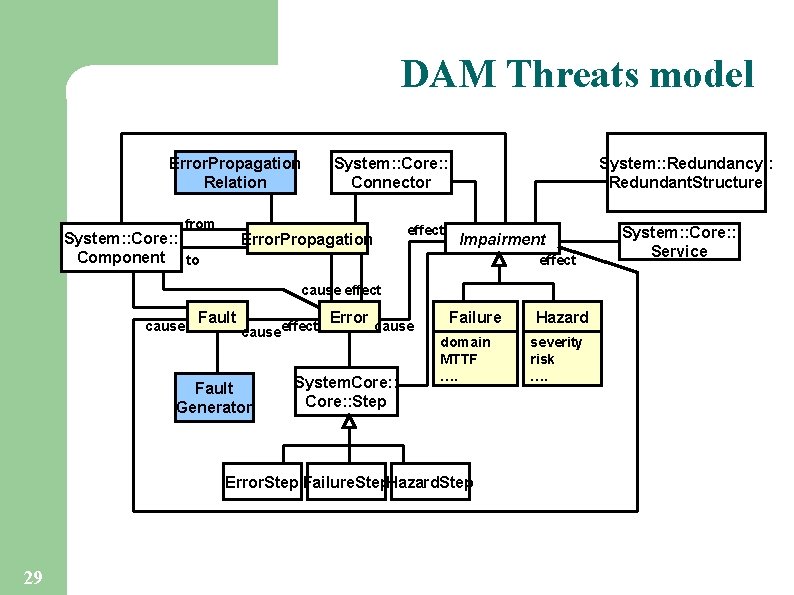
DAM Threats model Error. Propagation Relation from System: : Core: : Component to System: : Redundancy: : Redundant. Structure System: : Core: : Connector effect Error. Propagation Impairment effect cause Fault causeeffect Fault Generator Error cause System. Core: : Step Failure domain MTTF …. Error. Step Failure. Step. Hazard. Step 29 Hazard severity risk …. System: : Core: : Service
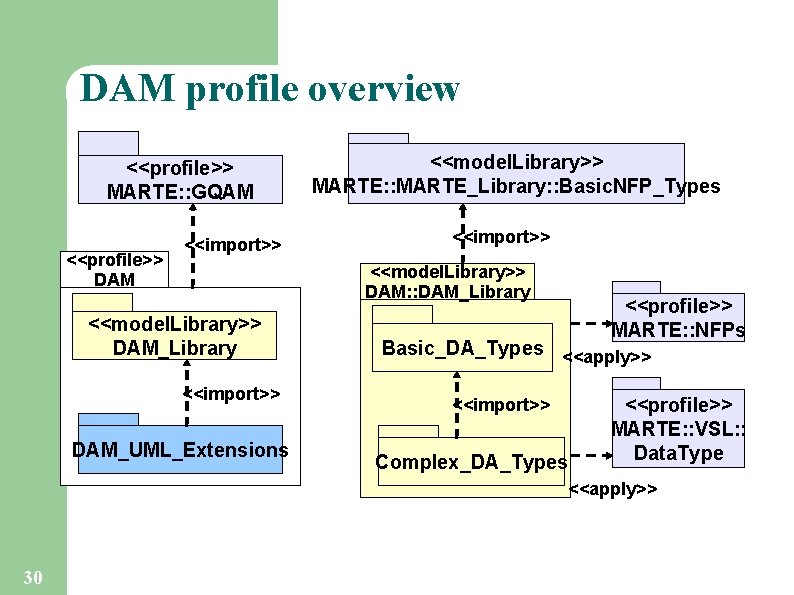
DAM profile overview <<profile>> MARTE: : GQAM <<profile>> DAM <<import>> <<model. Library>> MARTE: : MARTE_Library: : Basic. NFP_Types <<import>> <<model. Library>> DAM: : DAM_Library <<model. Library>> DAM_Library <<import>> DAM_UML_Extensions <<profile>> MARTE: : NFPs Basic_DA_Types <<apply>> <<import>> Complex_DA_Types <<profile>> MARTE: : VSL: : Data. Type <<apply>> 30
- Slides: 30