Registry Services Security LDAPbased Attributes and Authentication Information

Registry Services Security LDAP-based Attributes and Authentication Information Technology

Presentation Goals • Describe – The Registry – Its use for authentication – Its use for attribute information – Security of Registry information 9/17/2020 Information Technology 2

The Registry • A database exposed through LDAP protocols • Populated from both authoritative and other sources • Failure-tolerant architecture • Looks like a directory with more data items • But it’s NOT the “white pages” 9/17/2020 Information Technology 3

What Data Items? • • Names, addresses, phone numbers Affiliations, positions, locations, groups E-mail routing Passwords and certificates Entitlements Optional information Standards-based items 9/17/2020 Information Technology 4
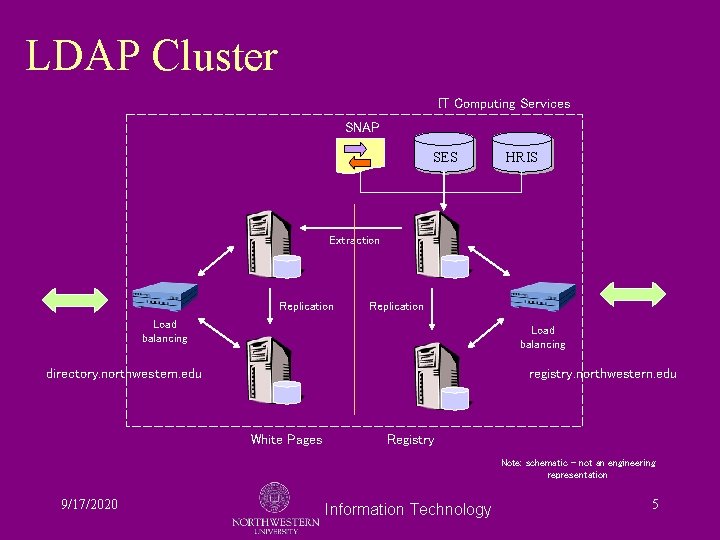
LDAP Cluster IT Computing Services SNAP SES HRIS Extraction Replication Load balancing directory. northwestern. edu registry. northwestern. edu White Pages Registry Note: schematic – not an engineering representation 9/17/2020 Information Technology 5

Access to Data Items • Access is controlled in four ways: – Anonymous bind to registry is reserved to known e-mail hosts – User binding restricted by IP address – Attribute retrieval protected by application credentialing and Access Control Lists – White pages is an extract of registry data 9/17/2020 Information Technology 6
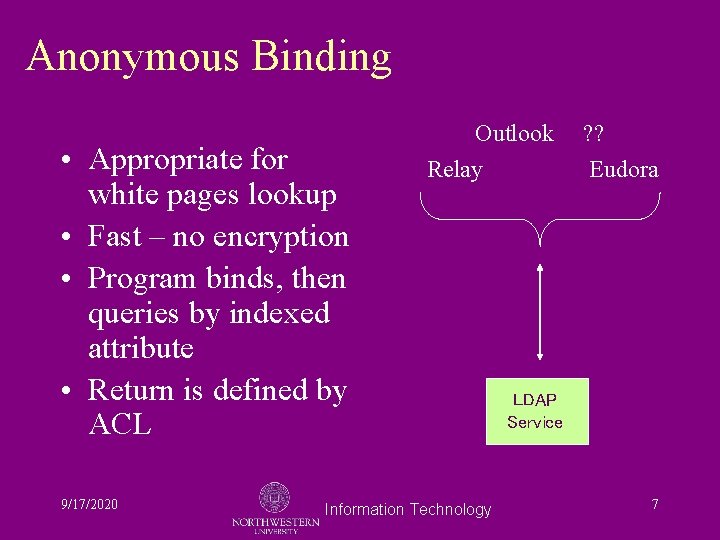
Anonymous Binding • Appropriate for white pages lookup • Fast – no encryption • Program binds, then queries by indexed attribute • Return is defined by ACL 9/17/2020 Outlook Relay Information Technology ? ? Eudora LDAP Service 7
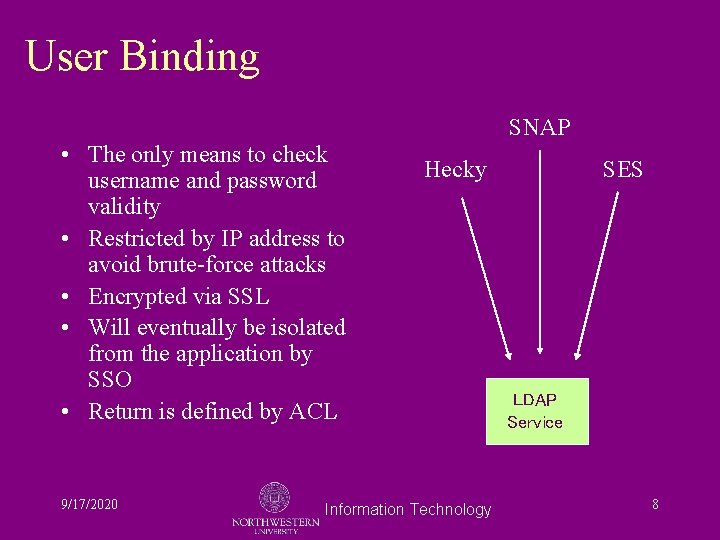
User Binding SNAP • The only means to check username and password validity • Restricted by IP address to avoid brute-force attacks • Encrypted via SSL • Will eventually be isolated from the application by SSO • Return is defined by ACL 9/17/2020 Hecky Information Technology SES LDAP Service 8
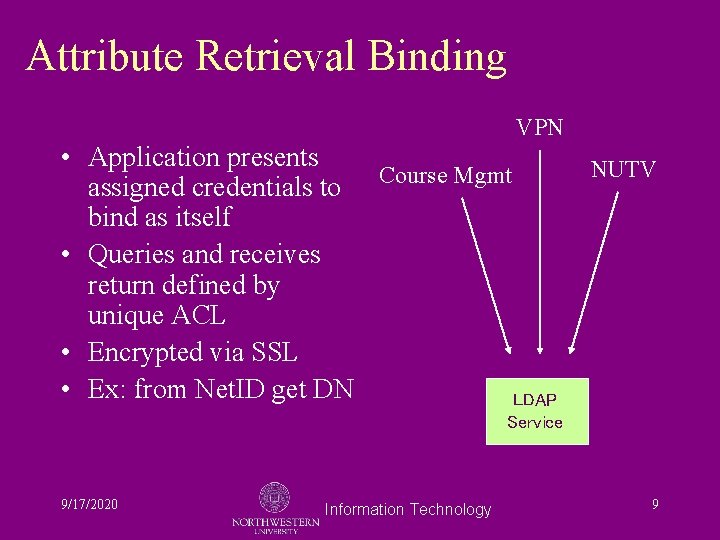
Attribute Retrieval Binding VPN • Application presents Course Mgmt assigned credentials to bind as itself • Queries and receives return defined by unique ACL • Encrypted via SSL • Ex: from Net. ID get DN LDAP NUTV Service 9/17/2020 Information Technology 9
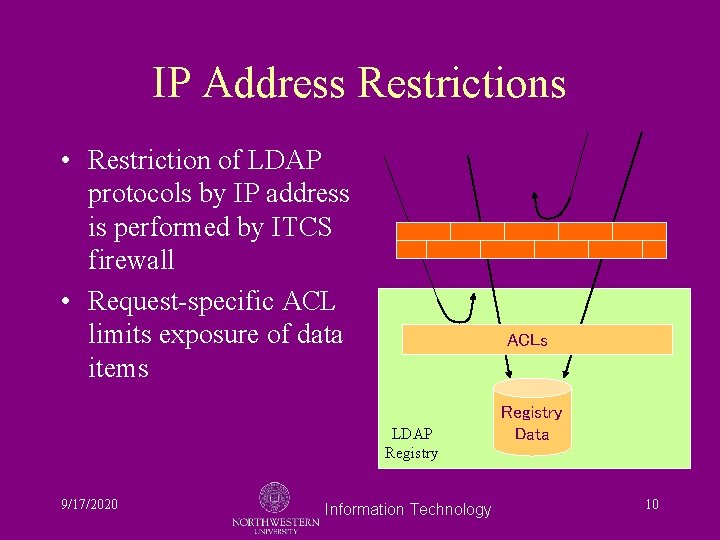
IP Address Restrictions • Restriction of LDAP protocols by IP address is performed by ITCS firewall • Request-specific ACL limits exposure of data items ACLs LDAP Registry 9/17/2020 Information Technology Registry Data 10
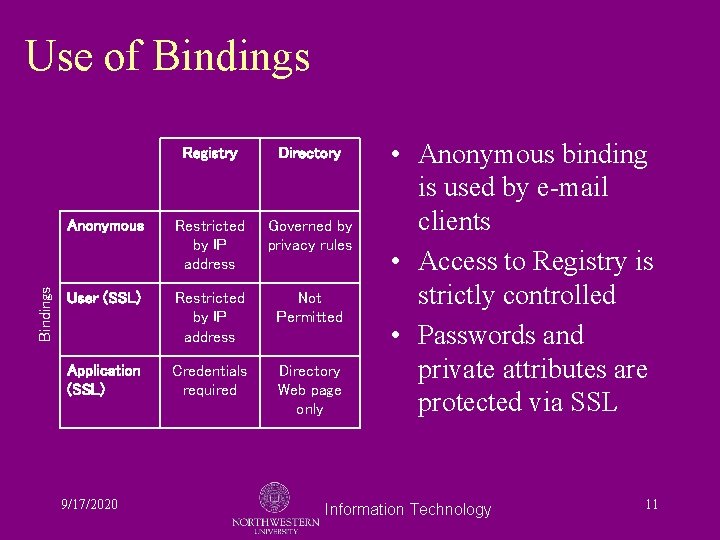
Bindings Use of Bindings Registry Directory Anonymous Restricted by IP address Governed by privacy rules User (SSL) Restricted by IP address Not Permitted Application (SSL) Credentials required Directory Web page only 9/17/2020 • Anonymous binding is used by e-mail clients • Access to Registry is strictly controlled • Passwords and private attributes are protected via SSL Information Technology 11
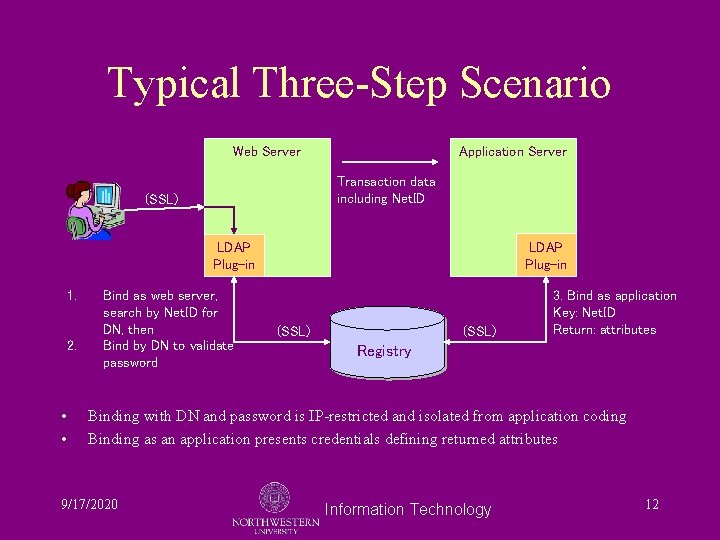
Typical Three-Step Scenario Web Server Application Server Transaction data including Net. ID (SSL) LDAP Plug-in 1. 2. • • Bind as web server, search by Net. ID for DN, then Bind by DN to validate password LDAP Plug-in (SSL) 3. Bind as application Key: Net. ID Return: attributes Registry Binding with DN and password is IP-restricted and isolated from application coding Binding as an application presents credentials defining returned attributes 9/17/2020 Information Technology 12

White Pages is a Separate Service • White pages (directory. northwestern. edu) is a separate service on separate hardware: – To increase performance – To separate the Registry for better security – To expose only the relevant data items to potential compromise 9/17/2020 Information Technology 13

How is Registry Access Governed? • Due to the protections in place, access must be requested through NUIT. • Requests must be approved by the custodian(s) of the data. • NUIT then assigns the appropriate ACL to restrict access to only the approved data items. 9/17/2020 Information Technology 14

How are Data Items Selected? • Registry data items fall into categories: – Those entrusted by SES and HRIS – Those necessary for e-mail routing and selective access to network services as defined by NUIT – Those historically available in the white pages 9/17/2020 Information Technology 15

New Data Items • Requests to include new items must be reviewed by NUIT and the source • Additional reviews by administrative offices may be required • New data items are not automatically exposed to existing ACLs 9/17/2020 Information Technology 16
- Slides: 16