Redesigning Edo Castle A Sociotechnical Systems Approach to





























- Slides: 47

Redesigning Edo Castle A Sociotechnical Systems Approach to Security Threats For MNEs in an Age of Asymmetric Threats IFSAM 2014 Allen D. Engle Norman Spain Peter Dowling

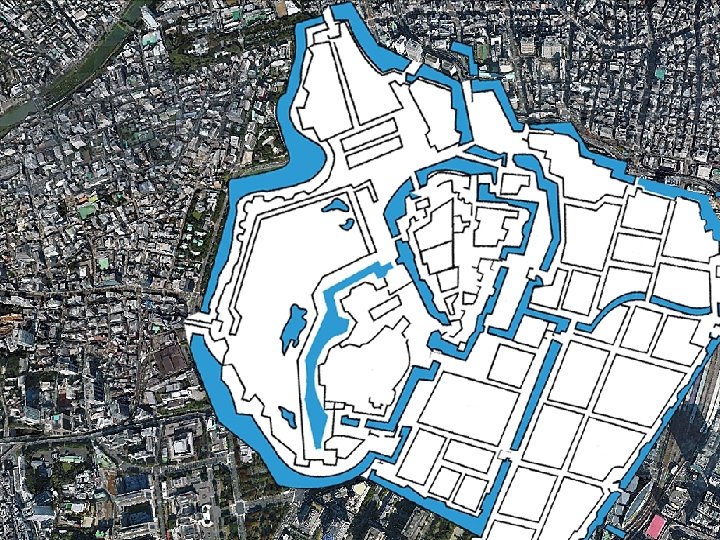
1 CONTEXT • • INTRODUCTORY CASTLE SEQUENCE Multinational Enterprises (MNEs) as. HERE Systems • Sophisticated Global Value Chains • Dispersed, Yet Leveraged and Integrated • Responsive and Flexible • Complex and Tightly Coupled Systems (Charles Perrow’s Normal Accidents (1984) • Rogue or Disaffected Employees

1 CONTEXT • INTRODUCTORY CASTLE SEQUENCE HERE

1 Asymmetric threats are … • • INTRODUCTORY CASTLE SEQUENCE HERE Unusual in our eyes. • Irregular in that they are posed by instruments unrecognized by the long-standing laws of war. • Unmatched in our arsenal of capabilities and plans. • Leveraged against our particular assets. Designed not only to secure leverage against our assets, but also intended to work around, offset, and negate what in other contexts are our strengths. -Gray, 2002

1 Environmental Realities • • INTRODUCTORY Political Acts – CASTLE SEQUENCE HERE state/terrorist • Highly Unusual Natural Disasters – tsunami, floods, droughts, ice caps, Götterdämmerung • Criminal Acts – kidnapping, piracy • Pandemics – Ebola, SARS • Industry and State Espionage















1 A Social-technical Systems Approach • • INTRODUCTORY CASTLE SEQUENCEHR HERE Beyond the Borders of Traditional • All-encompassing Asian “General Affairs” approach to IHRM • Sociotechnical Systems Theory People and Technology -Emery & Trist, 1978

1 Reaction: Risk Management • AINTRODUCTORY CASTLE SEQUENCE HERE Four Stage Model 1. Identify Risk 2. Assess Risk 3. Manage Risk 4. Evaluate Key Management Activities Relevant to Risk Management -Gillingham & Suder, 2007

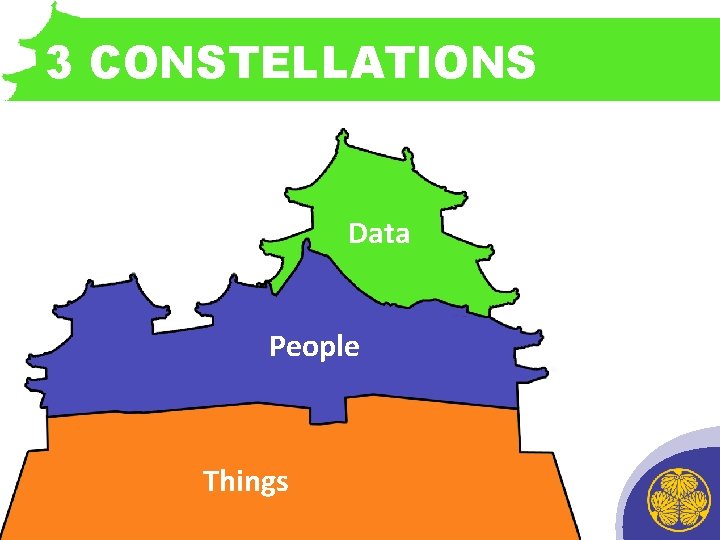
1 Three Starting Points and Traditions Data Information Technology; Passwords, Firewalls and beyond People Human Resources; Risk management; Security; Background Checking; Recruitment and Selection; Training in safety Policies; Payment to reinforce safe behaviors Things Loss Prevention and Safety; Plant Security, Law Enforcement and Military Culture -Data, People, Things. Fine & Wiley, 1971

1 Three Points Growing Together? Data People Things

2 COMPONENTS

2 Components: Immediate Goal An encompassing model that delineates the components (issues, qualities, characteristics) of building a defensive system (castle imagery) for MNEs that is capable of resisting or mitigating these new and unpredictable threats.

2 Components: Long Term Goal To create a template, vocabulary and attendant questionnaire instrument capable of capturing key decisions, elements and relationships of a robust MNE security system – a security portfolio.

2 Components: General Approaches Concentrated vs. Dispersed Assets Reinforced vs. Redundant Assets Extensive vs. Minimal Security Zones

2 Components: Perimeter • • Long Wall Fortlets – Outposts Convoys Other

2 Components: Interface • Bimodal “Green Zones” or “Red Zones” • Gradation and Levels • Roman Camp – Temporary, but high quality and safe with a significant reduction in risk • Other

2 Components: Suppliers / Contractors • Embedded in MNE • Isomorphism – Persuaded to adopt security practices • Stand Alone – Certified? ISO/IEC 27001 -2013 • Other

2 Other components?

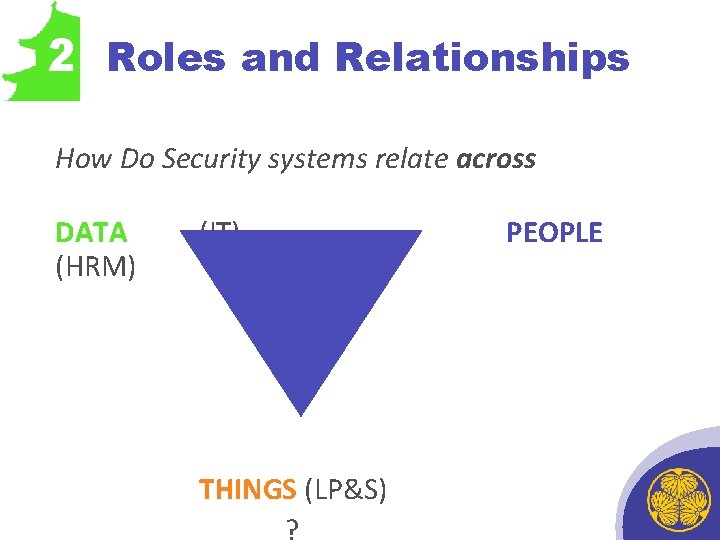
2 Roles and Relationships How Do Security systems relate across DATA (HRM) (IT) THINGS (LP&S) ? PEOPLE

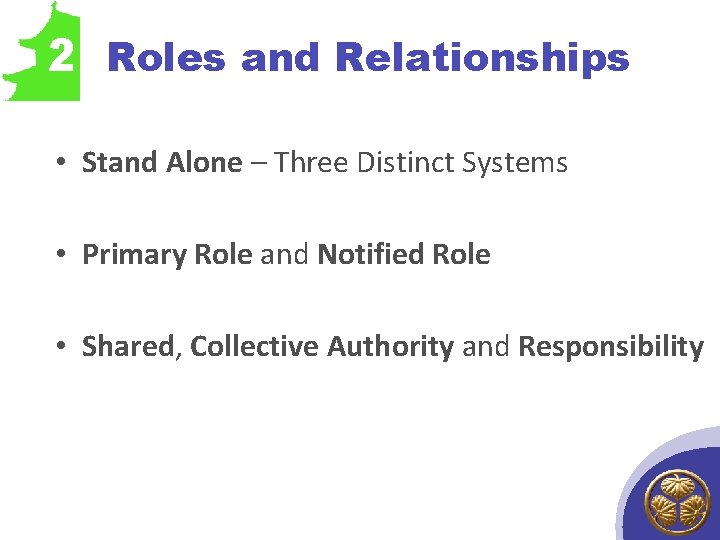
2 Roles and Relationships • Stand Alone – Three Distinct Systems • Primary Role and Notified Role • Shared, Collective Authority and Responsibility

2 Strategic Locii (Centralized / Decentralized) • Corporate • SBU • Regional / Product Division • Local - Facility

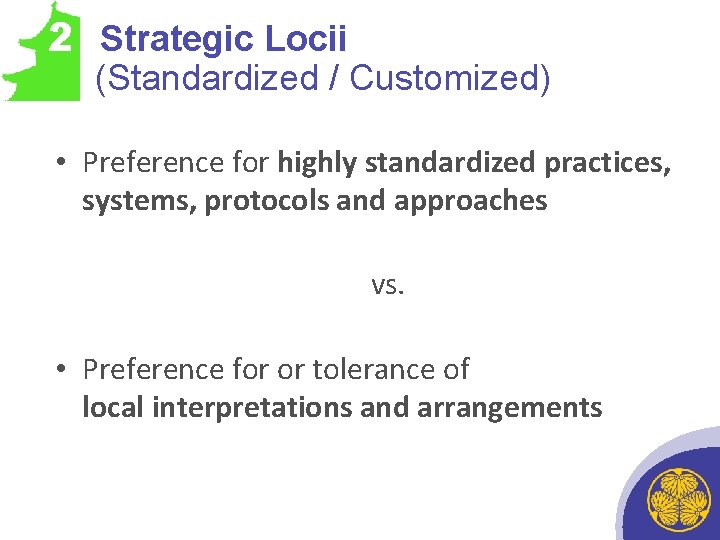
2 Strategic Locii (Standardized / Customized) • Preference for highly standardized practices, systems, protocols and approaches vs. • Preference for or tolerance of local interpretations and arrangements

2 Risk Management Cycles for MNEs Proactive Triggers • Constant • Weekly • Monthly • Quarterly • Annually • Other Reactive Triggers • Critical Incident – MNE Specific • Critical Incident – Industry • Critical Incident – General • Random

2 Risk Analysis • Risk Analysis Processes – Actors, Protocols and Schemas • Risk Analysis Results and Dissemination Processes – Need to Know – Timing – Form – Attention Getting

3 CONSTELLATIONS • INTRODUCTORY CASTLE SEQUENCE HERE

3 CONSTELLATIONS • INTRODUCTORY CASTLE SEQUENCE HERE Data

3 CONSTELLATIONS • INTRODUCTORY CASTLE SEQUENCE HERE Data People

3 CONSTELLATIONS • INTRODUCTORY CASTLE SEQUENCE HERE Data People Things

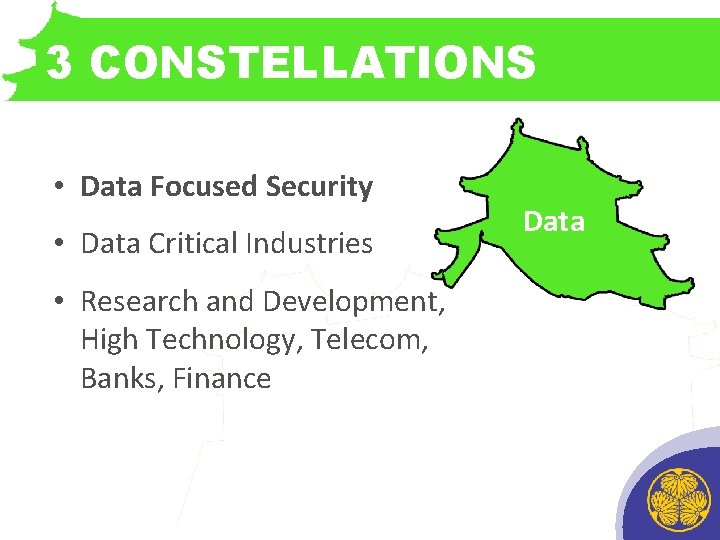
3 CONSTELLATIONS • Data Focused Security • Data Critical Industries • Research and Development, High Technology, Telecom, Banks, Finance Data

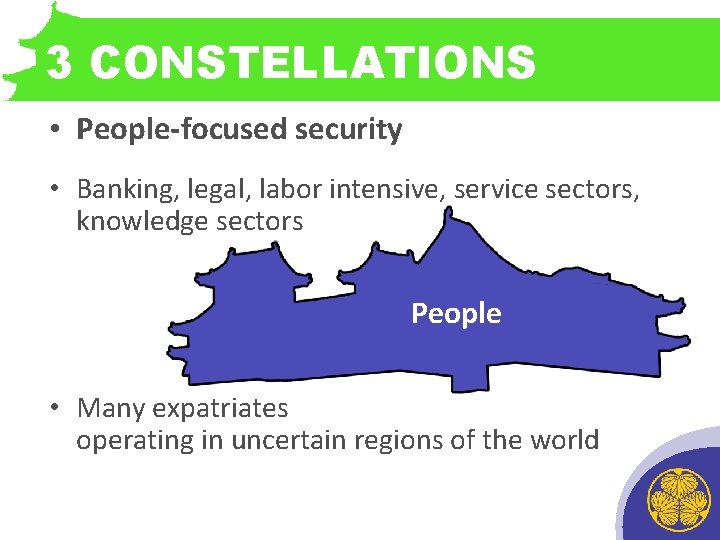
3 CONSTELLATIONS • People-focused security • Banking, legal, labor intensive, service sectors, knowledge sectors People • Many expatriates operating in uncertain regions of the world

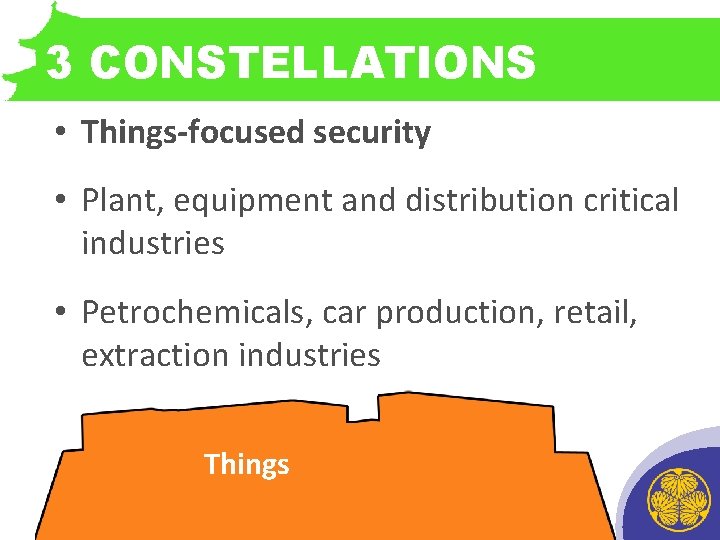
3 CONSTELLATIONS • Things-focused security • Plant, equipment and distribution critical industries • Petrochemicals, car production, retail, extraction industries Things

4 CONCLUSIONS • • INTRODUCTORY CASTLEand SEQUENCE Much more readings analyses. HERE across the three starting points of security (IT, HR and LP&S) • More assessment on components, roles and constellations • Review of the more complete model by security practitioners and specialist academics

4 CONCLUSIONS • • INTRODUCTORY CASTLE SEQUENCE HERE Conversion of model into a research instrument • Validation studies

IFSAM 2014 THANK YOU FOR YOUR ATTENTION DŌMO ARIGATŌGOZAIMASHITA どうもありがとうございました