RedDragon Rising com RedDragon Rising com RedDragon Rising









- Slides: 15

Red-Dragon. Rising. com©

Red-Dragon. Rising. com©

Red-Dragon. Rising. com©

中 華 人 民 共 和 國 網 絡 代 碼 衝 突. . . 中国人民共和国 信息戰 What Country Poses The Most Existential Cyber Threat to the World? LTCOL (RET) William Hagestad II MSc Security Technologies MSc Management of Technology www. red-dragonrising. com hagestadwt@red-dragonrising. com Red-Dragon. Rising. com©

Red-Dragon. Rising. com©

“ 21 st Century Chinese Cyber Warfare” “二十一世紀中國網絡戰” 取締中華人民共和國 Red-Dragon. Rising. com© ISBN: 9781849283342

取締中華人民共和國 ISBN: 978 -1482577105 Red-Dragon. Rising. com©

取締中華人民共和國 Red-Dragon. Rising. com© ISBN: 978 -1493771974

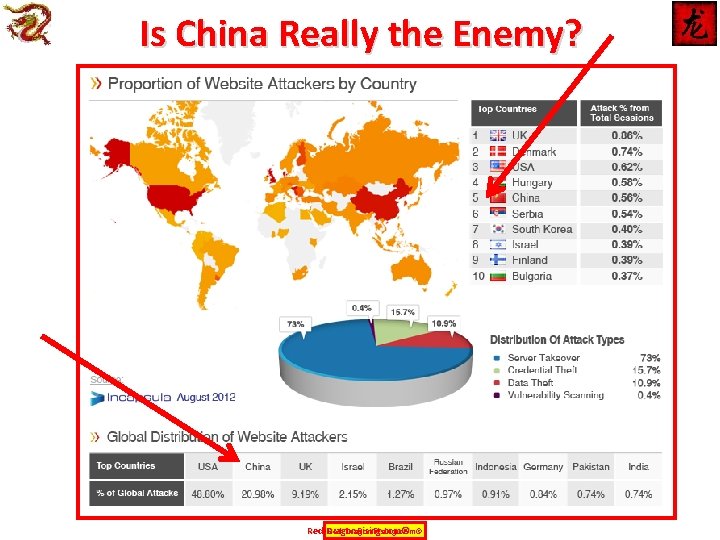
Is China Really the Enemy? Red-Dragon. Rising. com©

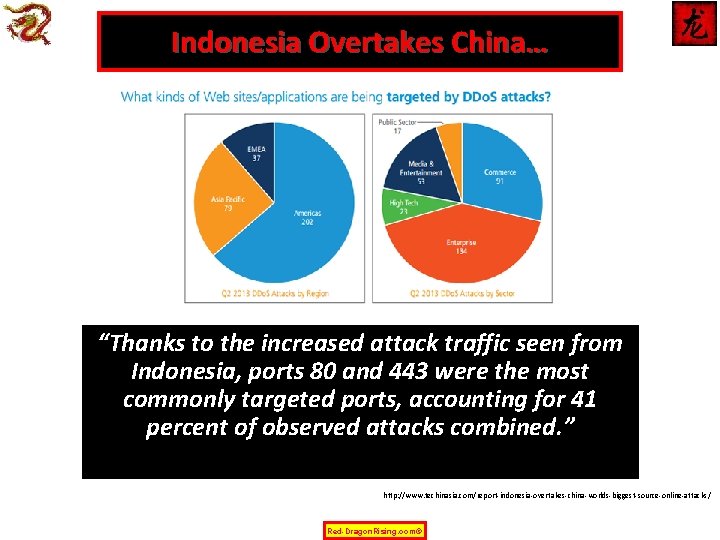
Indonesia Overtakes China… “Thanks to the increased attack traffic seen from Indonesia, ports 80 and 443 were the most commonly targeted ports, accounting for 41 percent of observed attacks combined. ” http: //www. techinasia. com/report-indonesia-overtakes-china-worlds-biggest-source-online-attacks/ Red-Dragon. Rising. com©

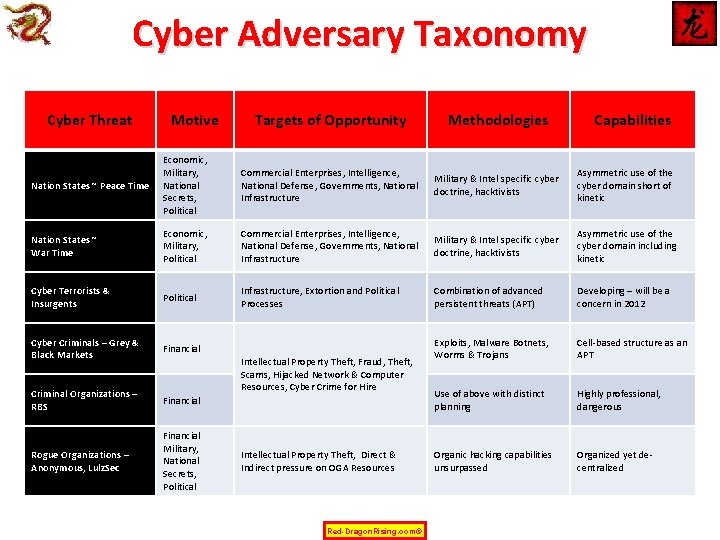
Cyber Adversary Taxonomy Cyber Threat Motive Targets of Opportunity Methodologies Nation States ~ Peace Time Economic, Military, National Secrets, Political Commercial Enterprises, Intelligence, National Defense, Governments, National Infrastructure Military & Intel specific cyber doctrine, hacktivists Asymmetric use of the cyber domain short of kinetic Nation States ~ War Time Economic, Military, Political Commercial Enterprises, Intelligence, National Defense, Governments, National Infrastructure Military & Intel specific cyber doctrine, hacktivists Asymmetric use of the cyber domain including kinetic Cyber Terrorists & Insurgents Political Infrastructure, Extortion and Political Processes Combination of advanced persistent threats (APT) Developing – will be a concern in 2012 Cyber Criminals – Grey & Black Markets Financial Exploits, Malware Botnets, Worms & Trojans Cell-based structure as an APT Criminal Organizations – RBS Financial Use of above with distinct planning Highly professional, dangerous Rogue Organizations – Anonymous, Lulz. Sec Financial Military, National Secrets, Political Organic hacking capabilities unsurpassed Organized yet decentralized Intellectual Property Theft, Fraud, Theft, Scams, Hijacked Network & Computer Resources, Cyber Crime for Hire Intellectual Property Theft, Direct & Indirect pressure on OGA Resources Red-Dragon. Rising. com© Capabilities

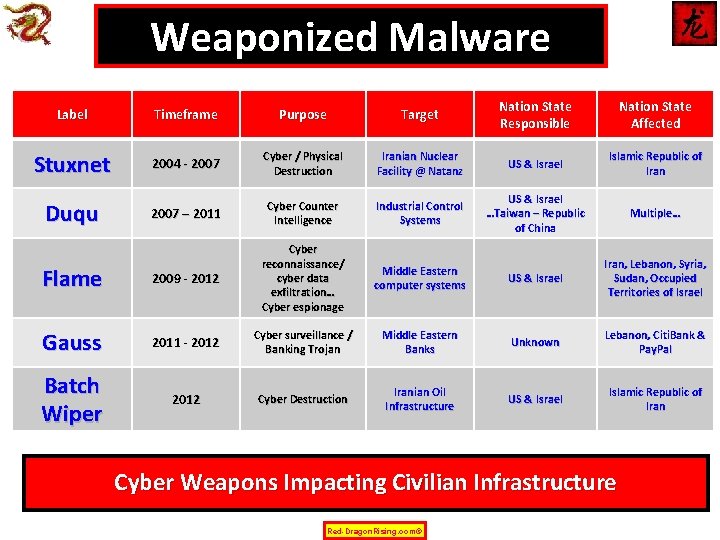
Weaponized Malware Label Timeframe Purpose Target Nation State Responsible Nation State Affected Stuxnet 2004 - 2007 Cyber / Physical Destruction Iranian Nuclear Facility @ Natanz US & Israel Islamic Republic of Iran 2007 – 2011 Cyber Counter Intelligence Industrial Control Systems US & Israel …Taiwan – Republic of China Multiple… Flame 2009 - 2012 Cyber reconnaissance/ cyber data exfiltration… Cyber espionage Middle Eastern computer systems US & Israel Iran, Lebanon, Syria, Sudan, Occupied Territories of Israel Gauss 2011 - 2012 Cyber surveillance / Banking Trojan Middle Eastern Banks Unknown Lebanon, Citi. Bank & Pay. Pal Batch Wiper 2012 Cyber Destruction Iranian Oil Infrastructure US & Israel Islamic Republic of Iran Duqu Cyber Weapons Impacting Civilian Infrastructure Red-Dragon. Rising. com©

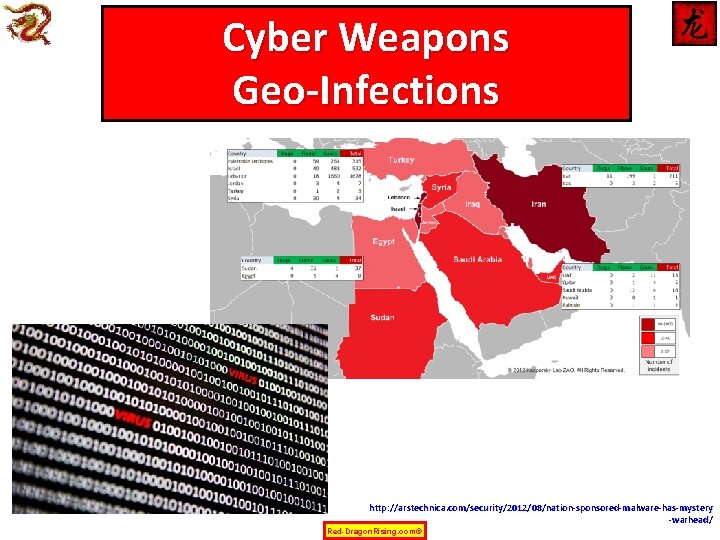
Cyber Weapons Geo-Infections http: //arstechnica. com/security/2012/08/nation-sponsored-malware-has-mystery -warhead/ Red-Dragon. Rising. com©


跟隨紅龍 Red-Dragon. Rising #Red. Dragon 1949 http: //www. linkedin. com/in/billhagestad Red-dragonrising. com Red-Dragon. Rising. com©