RECONFIGURABLE SECURITY SUPPORT FOR EMBEDDED SYSTEMS AKSHATA VARDHARAJ

RECONFIGURABLE SECURITY SUPPORT FOR EMBEDDED SYSTEMS AKSHATA VARDHARAJ 1

INTRODUCTION Security challenges - Limited resources - Power constraints. SANES (Security Architecture for Embedded Systems ) - Reconfigurable hardware - Efficient, flexible - Supports security standards , range of attacks. The SANES architecture is based on - Reconfigurable security primitives - Reconfigurable hardware monitors - A hierarchy of security controllers 2

MAIN ISSUES TO BE CONSIDERED WHEN DESIGNING THE ARCHITECTURE Security primitives and protocols Attacks CURRENT SOLUTIONS TO ADDRESS BOTH FACE SEVERAL GAPS SUCH AS Processing gap Battery gap Flexibility gap Tamper resistance gaps Assurance gaps SOLUTIONS Reconfigurable computing : high performance and flexibility Intrusion detection system : detect abnormal behavior 3

PURPOSE Prevention, detection , remediation of attacks Dynamically adapt security protections to deal with dynamic constraints Reconfigurable hardware , A continuous monitoring system Performance and energy issues are taken care by reconfigurable security primitives Reliability is managed by use of different implementations Hierarchy of hardware monitors - Provides different levels of flexibility - Enables compromise between accuracy and simplicity 4
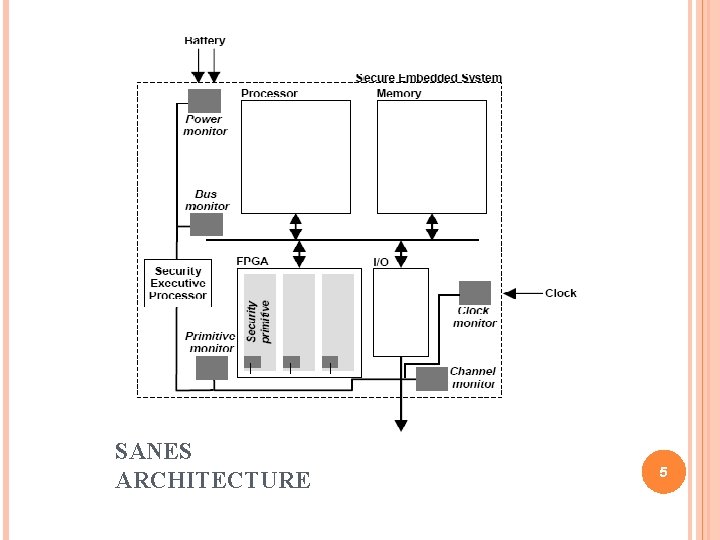
SANES ARCHITECTURE 5

MONITORS Track specific data of system Number and complexity - Overhead cost of security architecture Role - Detect attacks against system Autonomy and adaptability Distributed : analyze different parts - Battery - Buses - Security primitives - Communication channel Reflex reaction Global reaction 6

SEP: SECURITY EXECUTIVE PROCESSOR Links monitors by on-chip intelligence Controls the network Acts as gateway to outside world. Provides software to map new monitoring and verification algorithms to monitors. Issues commands to control operation 7

RECONFIGURABLE ARCHITECTURE Implements security primitives Security primitives work independently Speedup computation of security algorithm Flexibility - Update primitives - Switch from one primitive to another Tradeoffs: throughput, area, latency, reliability, power , energy to meet real time constraints 8
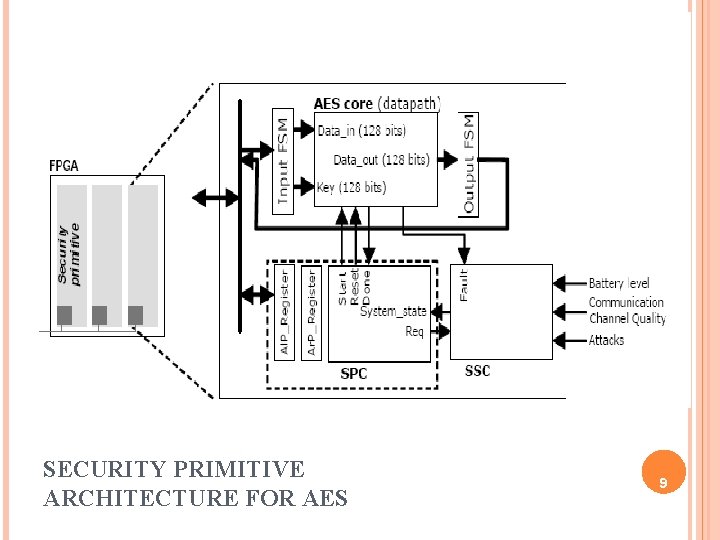
SECURITY PRIMITIVE ARCHITECTURE FOR AES 9

RECONFIGURABLE SECURITY PRIMITIVE Security primitive datapath Security Primitive Controller(SPC) - Flexibility - Memory mapped mechanism - Defines the configuration of primitive - Control tasks - Processor configures the SPC - Check what execution modes can be used System Security Controller(SSC) - Connected to security primitive - Monitor the primitive - Detects attacks against the primitive - Also connected to other monitors 10
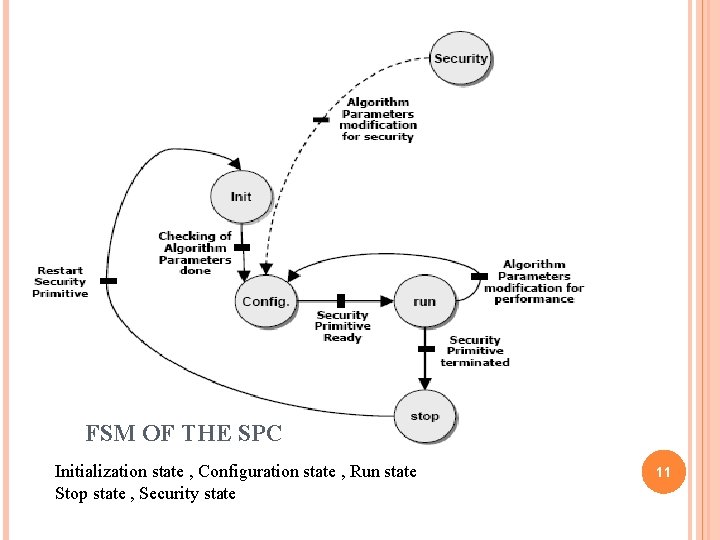
FSM OF THE SPC Initialization state , Configuration state , Run state Stop state , Security state 11

DYNAMIC SECURITY WITHIN THE SYSTEM: MONITORING Execution of the security primitives - Managed by SPC - Flexibility Protect system - Managed by SSC - Deals with attacks Examples of attacks - Hijacking - Denial of service - Extraction of secret information 12

HEURISTIC APPROACH Problem - The normal defined behavior can be over written This works for Embedded systems - Simplicity of work load - Repetitiveness of workload - Application profiling - Capture large fraction of application behavior - Power, clock, bus, security primitive , communication channel monitors 13

PERFORMANCE AND SECURITY POLICIES SPC: - New configuration , best performance tradeoff - It runs protected modes only when required - Continuously checks the state of the system - Best performance of the primitive SPC selects parameters - The power limitation - Evolving environment - Level of quality of the communication channels. 14

AES (ADVANCED ENCRYPTION STANDARD) CASE STUDY Memory - Bit streams (each bit stream corresponds to a configuration). registers - The algorithm AES - Execution mode (i. e. feedback, non-feedback) - The key and data sizes(i. e. 128 bits). Architecture parameters. - Reliability (i. e. no, fault detection, fault tolerance), - On the throughput, - The area (use rate of the device) - The energy consumption. 15
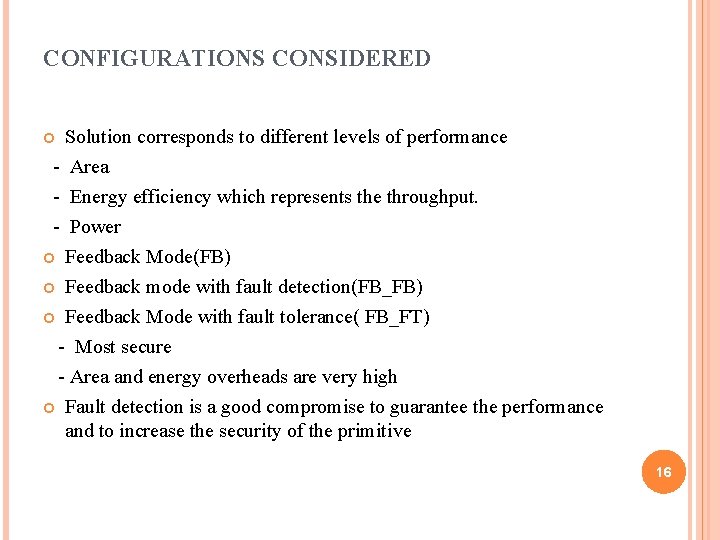
CONFIGURATIONS CONSIDERED Solution corresponds to different levels of performance - Area - Energy efficiency which represents the throughput. - Power Feedback Mode(FB) Feedback mode with fault detection(FB_FB) Feedback Mode with fault tolerance( FB_FT) - Most secure - Area and energy overheads are very high Fault detection is a good compromise to guarantee the performance and to increase the security of the primitive 16
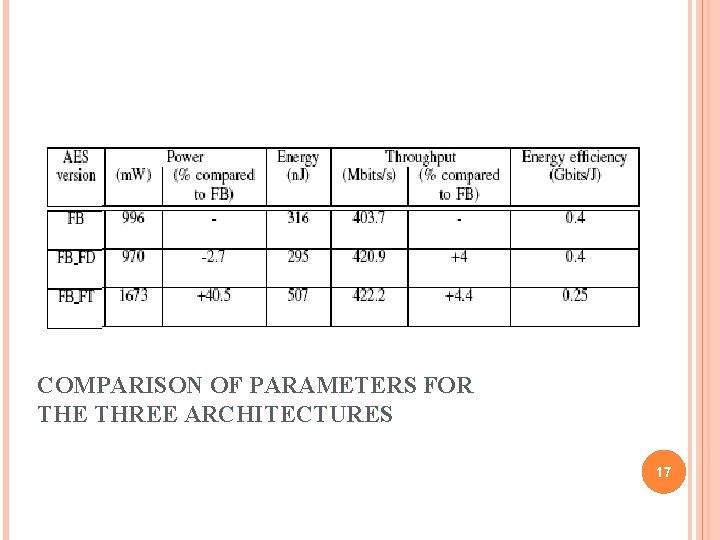
COMPARISON OF PARAMETERS FOR THE THREE ARCHITECTURES 17
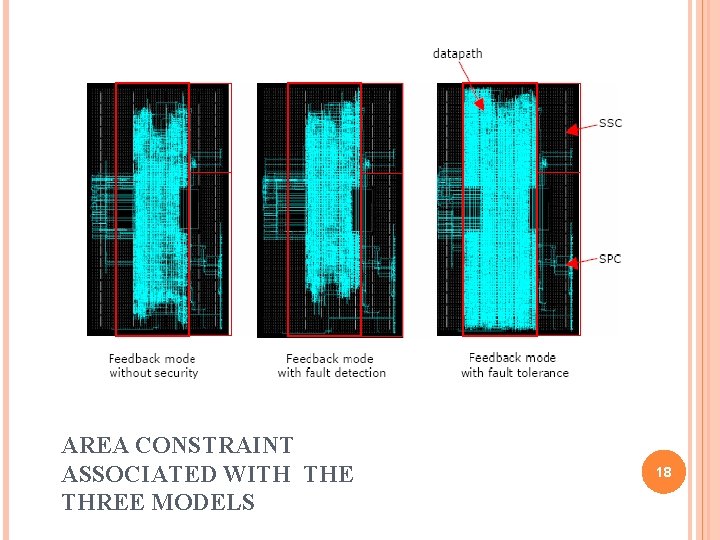
AREA CONSTRAINT ASSOCIATED WITH THE THREE MODELS 18

ADVANTAGES Application verification and protection is provided in dedicated hardware and not inside application Implies dynamically updated durability Flexibility and security Hierarchy of hardware monitors Meets embedded system constraints 19
- Slides: 19