Recognizing Attacks 1 Recognition Stances Recognizing Attacks 2















- Slides: 24

Recognizing Attacks 1

Recognition Stances Recognizing Attacks 2

Leading Questions • • Is it a real break-in? Was any damage really done? Is protecting evidence important? Is restoring normal operation quickly important? • Willing to chance modification of files? • Is no publicity important? • Can it happen again? Recognizing Attacks 3

Document Actions • • Start notebook Collect printouts and backup media Use scripts Get legal assistance for evidencegathering • PLAN AHEAD Recognizing Attacks 4

Finding the Intruder • Finding changes • Receiving message from other system administrator / net defender • Strange activities • User reports Recognizing Attacks 5

Steps in Handling 1. Identify/understand the problem 2. Contain/stop the damage 3. Confirm diagnosis and determine damage 4. Restore system 5. Deal with the cause 6. Perform related recovery Recognizing Attacks 6

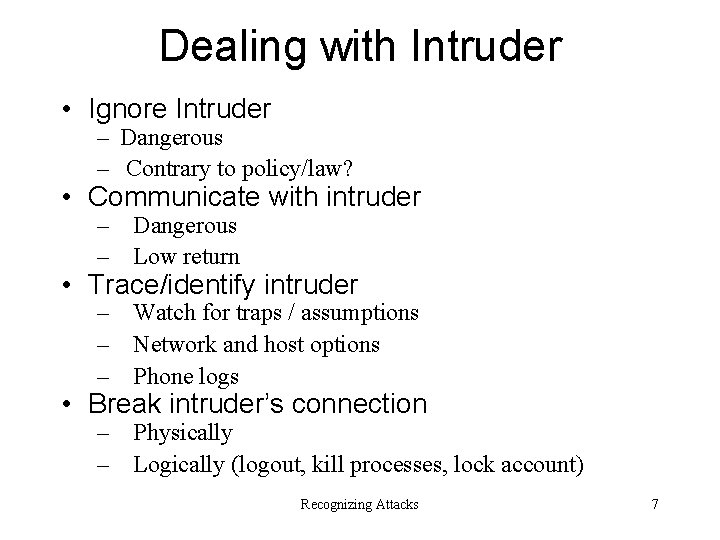
Dealing with Intruder • Ignore Intruder – Dangerous – Contrary to policy/law? • Communicate with intruder – Dangerous – Low return • Trace/identify intruder – Watch for traps / assumptions – Network and host options – Phone logs • Break intruder’s connection – Physically – Logically (logout, kill processes, lock account) Recognizing Attacks 7

Asking for Help • CERT, FIRST, Law enforcement, etc. • Don’t use infected system • Avoid using email from connected systems Recognizing Attacks 8

Finding Damage • What have affected accounts done lately? – – – Missing log files? What has root done? What reboots have occurred? Unexplained error messages? Connections from/to unfamiliar sites? New hidden directories? – – – Changed binaries? Changed configuration files? Changed library files? Changed boot files? Changed user files? • Integrity checkers Recognizing Attacks 9

Dealing with Damage • Delete unauthorized account(s) • Restore authorized access to affected account(s) • Restore file / device protections • Remove setuid/setgid programs • Remove unauthorized mail aliases • Remove added files / directories • Force new passwords Recognizing Attacks 10

Resume Service • Patch and repair damage, enable further monitoring, resume • Quick scan and cleanup, resume • Call in law enforcement -- delay resumption • Do nothing -- use corrupted system Recognizing Attacks 11

Dealing with Consequences • Was sensitive information disclosed? • Who do you need to notify formally? • Who do you need to notify informally? • What disciplinary action is needed? Recognizing Attacks 12

Moving Forward • What vendor contacts do we need to make? • What other system administrators should be notified? • What updated employee training is needed? Recognizing Attacks 13

Netwar • Individual: affect key decision-maker – Ems telegram – Gulf war marines • Corporate: affect environment of decision – Zapatista peso collapse – Vietnam protests – Intifada / Cyber-Intifada? • Strategic combination of all previous Recognizing Attacks 14

Example: Zapatista Cyberstrike • Mid-1990 s rebellion in Mexico • Military situation strongly favored Mexican Army • Agents of influence circulated rumors of Peso instability • Peso crash forced government to negotiating table Recognizing Attacks 15

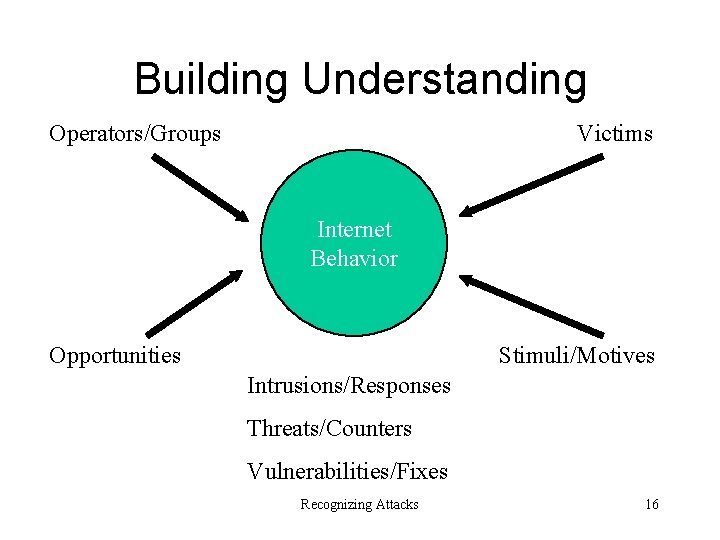
Building Understanding Operators/Groups Victims Internet Behavior Stimuli/Motives Opportunities Intrusions/Responses Threats/Counters Vulnerabilities/Fixes Recognizing Attacks 16

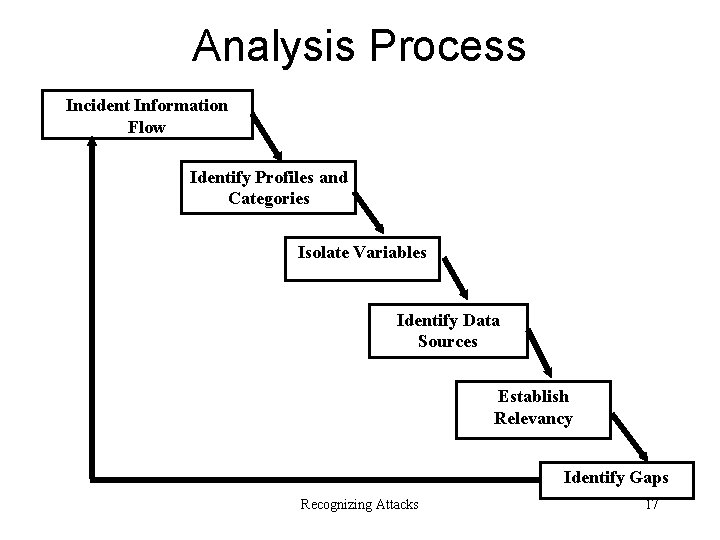
Analysis Process Incident Information Flow Identify Profiles and Categories Isolate Variables Identify Data Sources Establish Relevancy Identify Gaps Recognizing Attacks 17

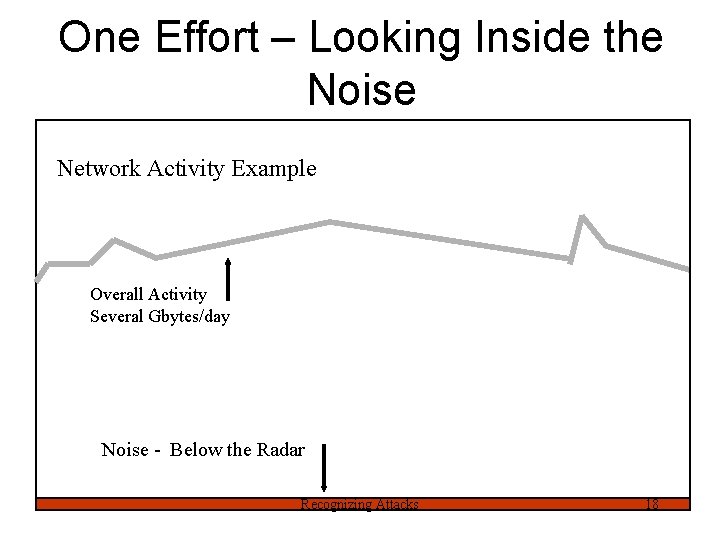
One Effort – Looking Inside the Noise Network Activity Example Overall Activity Several Gbytes/day Noise - Below the Radar Recognizing Attacks 18

Low-Packet Filtering It’s hard to use TCP without generating a lot of packets – Negotiation, transmission, configuration, error checking Few legitimate low-packet sessions possible – Mostly web access Recognizing Attacks 19

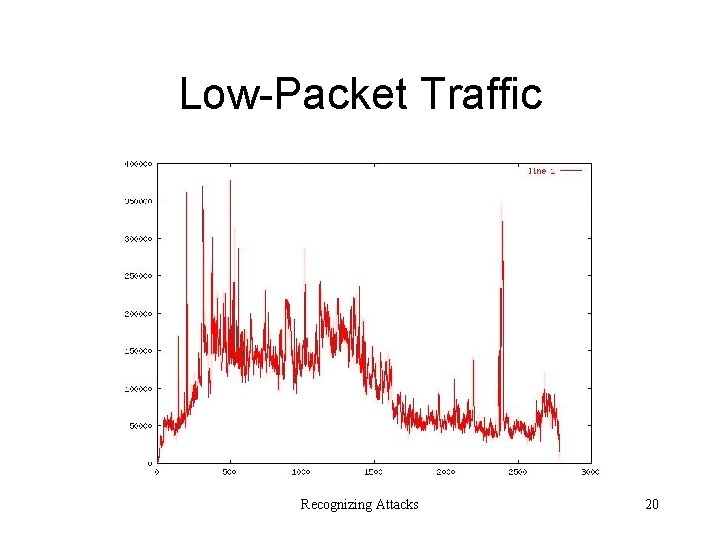
Low-Packet Traffic Recognizing Attacks 20

Flow Based Detection • • Scans and Probes Distributed Tools Worm/Virus Propagation ? ? ? Recognizing Attacks 21

Challenges to Analysis • Gathering sufficient datasets to make statistically valid judgments • Developing automated technical analysis tools • Developing a reliable methodology for cyber-analysis • Overcoming organizational bias against sharing information

Limits of Analysis • Inherently partial data • Baseline in dynamic environment • Correlation vs. Causation • Implications – Need to be cautious in kinds of conclusions – Consider strategies for dealing with trends gone wrong Recognizing Attacks 23

Summary • Incidents are not proof of bad administration • Lots of effort involved in handling Incidents • Need proactive, strategic planning to reduce costs, improve handling Recognizing Attacks 24