Reading Log Files 1 Segment Format http www












- Slides: 29

Reading Log Files 1

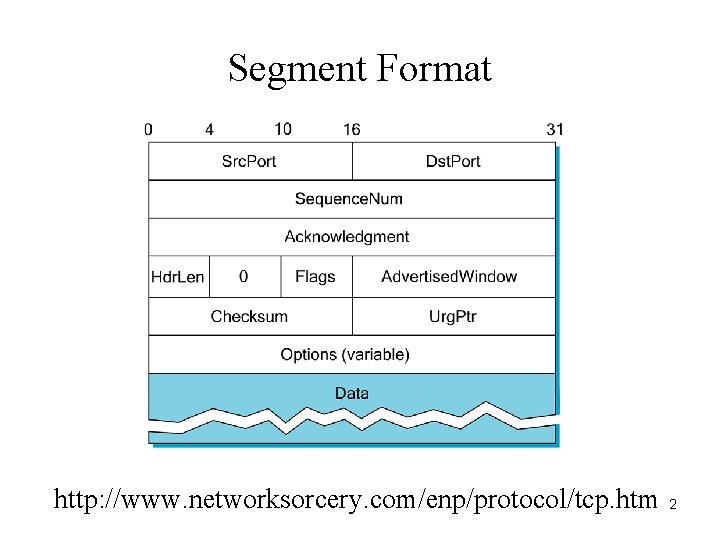
Segment Format http: //www. networksorcery. com/enp/protocol/tcp. htm 2

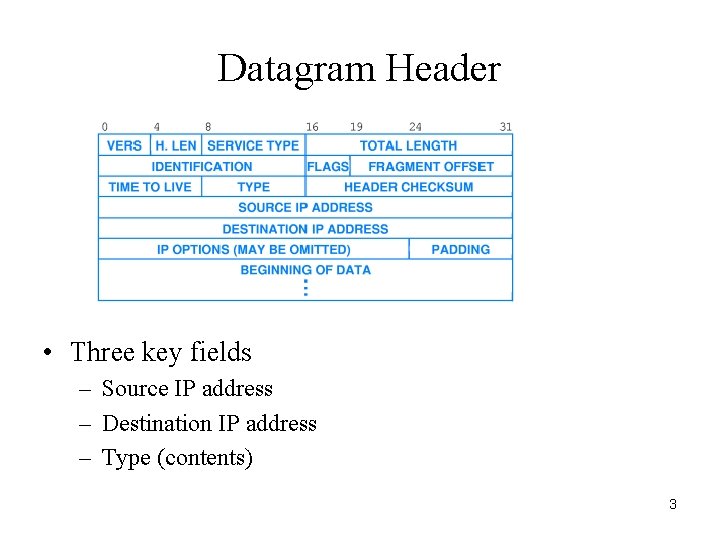
Datagram Header • Three key fields – Source IP address – Destination IP address – Type (contents) 3

TCP Flags • TCP packets have one-bit flags • Flags are used to specify the meaning of the packet. –SYN (Start of connection): S –ACK (Acknowledge): ack –FIN ("FINish" or French for “end”): F –RESET: R –PUSH: P –URGENT: urg

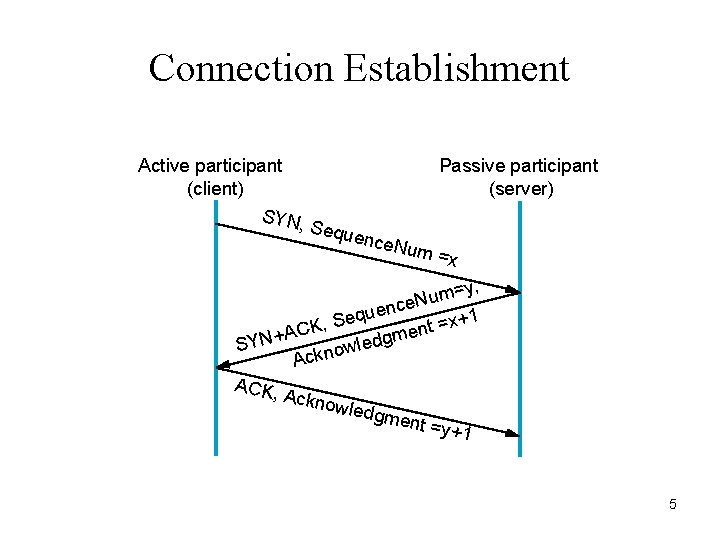
Connection Establishment Active participant (client) SYN, Passive participant (server) Sequ e nce. N um = x =y, m u N nce e u q e +1 S x , = t K AC men + g N d Y e l S ow Ackn ACK, Ackno wledg ment =y+1 5

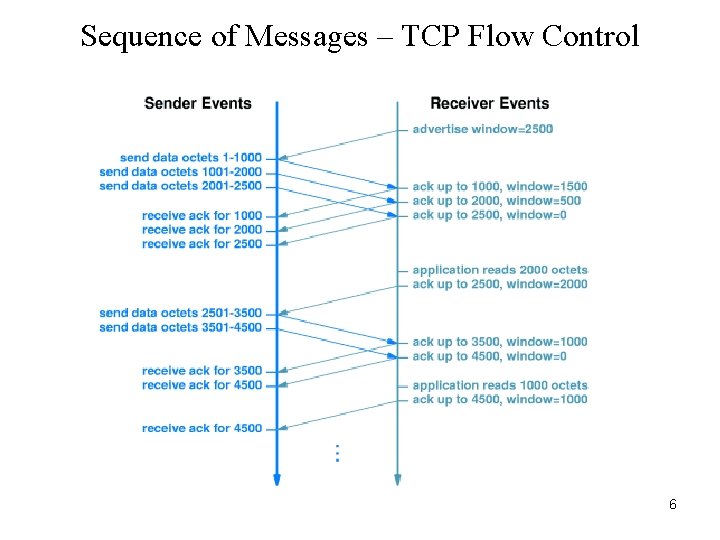
Sequence of Messages – TCP Flow Control 6

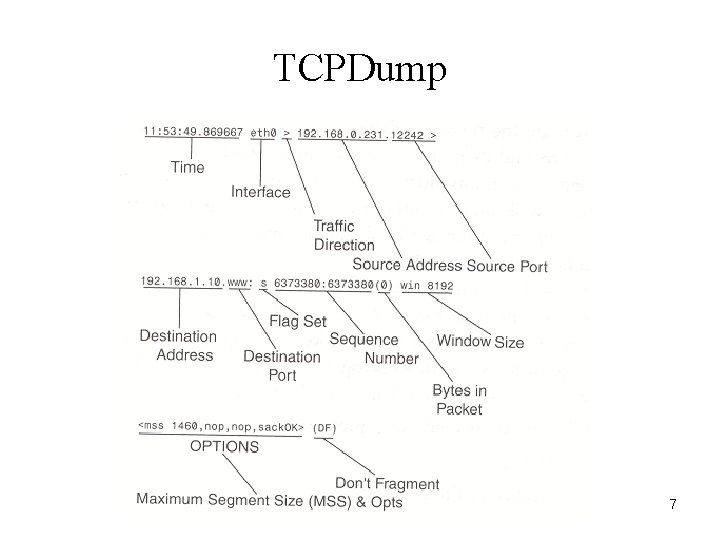
TCPDump 7

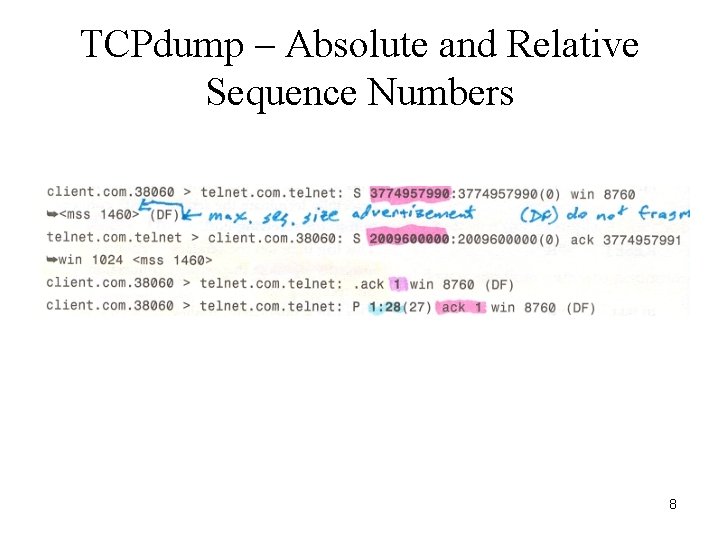
TCPdump – Absolute and Relative Sequence Numbers 8

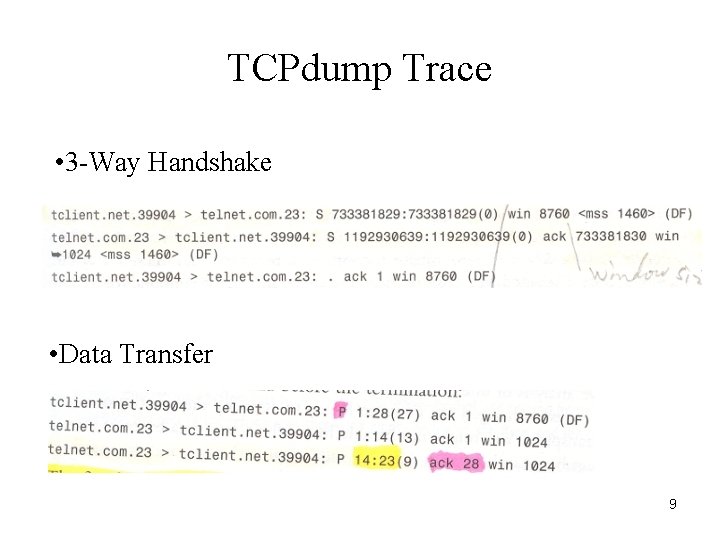
TCPdump Trace • 3 -Way Handshake • Data Transfer 9

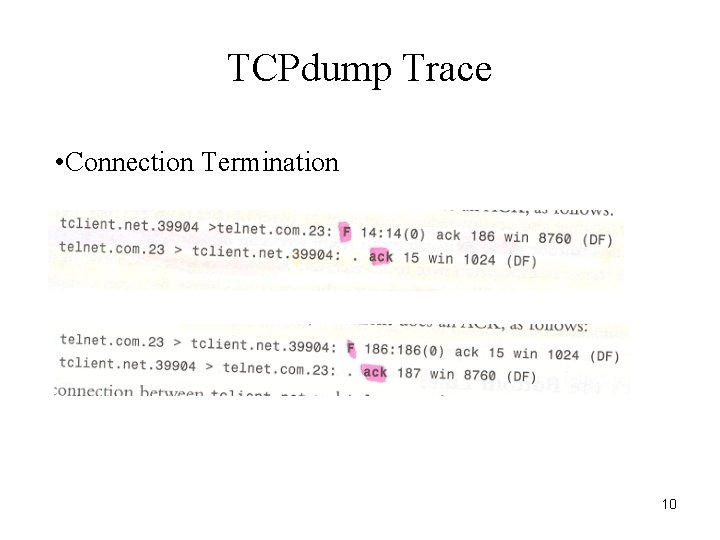
TCPdump Trace • Connection Termination 10

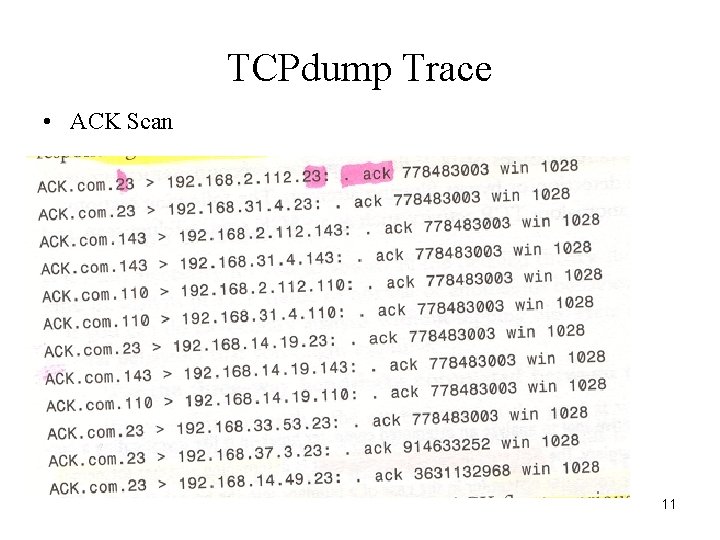
TCPdump Trace • ACK Scan 11

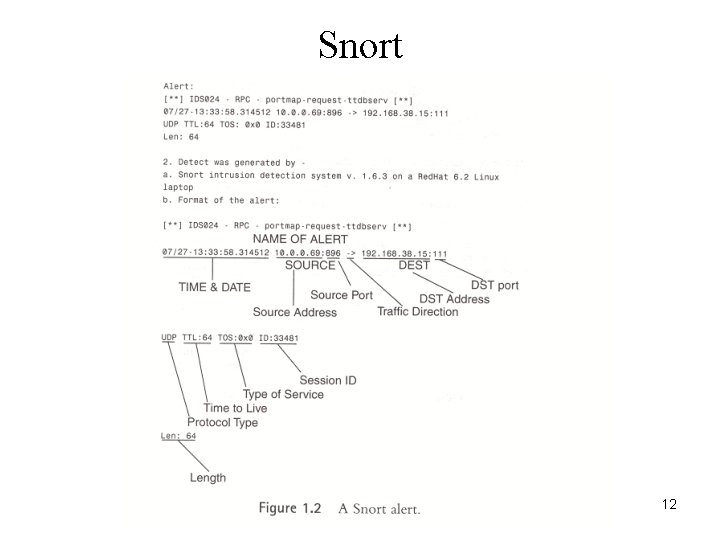
Snort 12

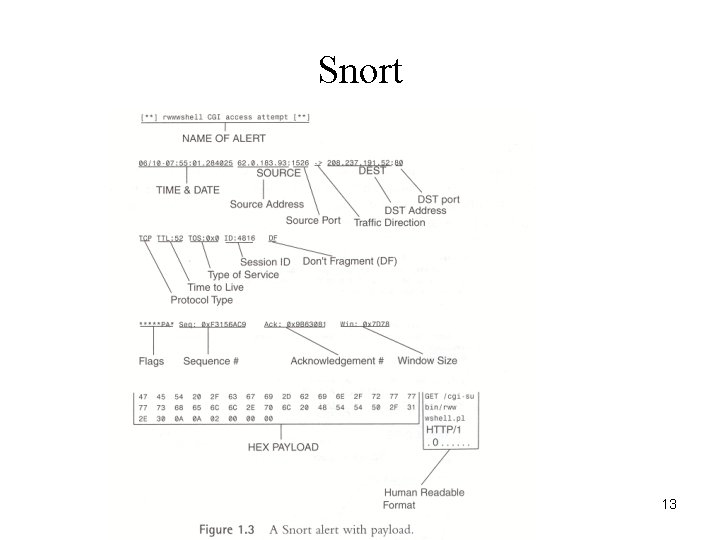
Snort 13

Introduction to Practicals 14

Introduction to Practicals • Network or system log trace of an event of interest on which the practical is based • Source of the detect – e. g. , snort • • Probability that the source address was spoofed Description of the attack Attack mechanism Correlations Evidence of active targeting Severity Defensive recommendation Multiple-choice question 15

Introduction to Practicals • The traffic was logged because it violated the security policy • The network or system trace – False positives – False negatives – False interpretations 16

One Trace Example P. 21 of the textbook 17

Probability the source address was spoofed • Probably spoofed – Do. S attacks: Smurf, ICMP broadcast, etc. • Probably not spoofed – TCP packets are not spoofed if the three-way handshake is completed • Combination of both aspects • Despoof: checking TTL to determine whether a received packet is spoofed or not – http: //packetstormsecurity. org/advisories/bindview/ 18

Description of Attack • Common Vulnerabilities and Exposures (CVE) – http: //cve. mitre. org – One of the most important standards efforts for intrusion detection and information security in general – For example: TCP SYN flood, ADM buffer overflow against DNS, etc. 19

SYN Flood • Denial of service when an attacker sends many SYN packets to create multiple connections without ever sending an ACK to complete the connection, aka SYN flood. –CVE-1999 -0116 –Keeping track of each half-open connection takes up resources

Attack Mechanism • Is this a stimulus or response? – RFCs are the standards documents – Unfortunately, different implementations of TCP/IP react differently to deliberate violations of RFC standards • What service is being targeted? • Does the service have known vulnerabilities or exposures? • Is this benign, an exploit, Do. S, or reconnaissance? 21

Expected Stimulus-Response • Destination Host Listens on Requested Port – Stimulus – Response 22

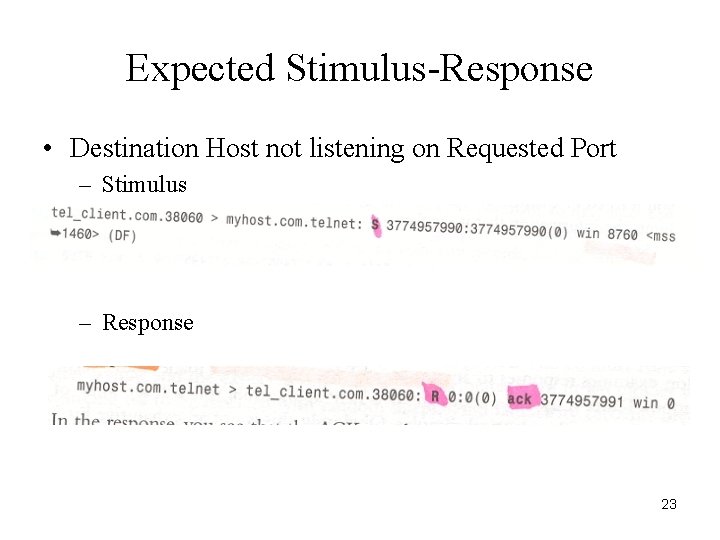
Expected Stimulus-Response • Destination Host not listening on Requested Port – Stimulus – Response 23

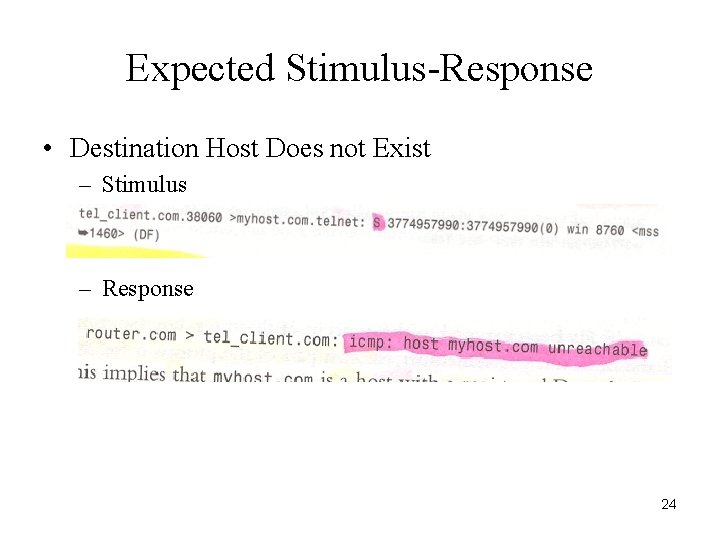
Expected Stimulus-Response • Destination Host Does not Exist – Stimulus – Response 24

Expected Stimulus-Response • Destination Port Blocked – Stimulus – Response 25

Expected Stimulus-Response • Destination Port Blocked, Router Does not Respond – Stimulus – Response 26

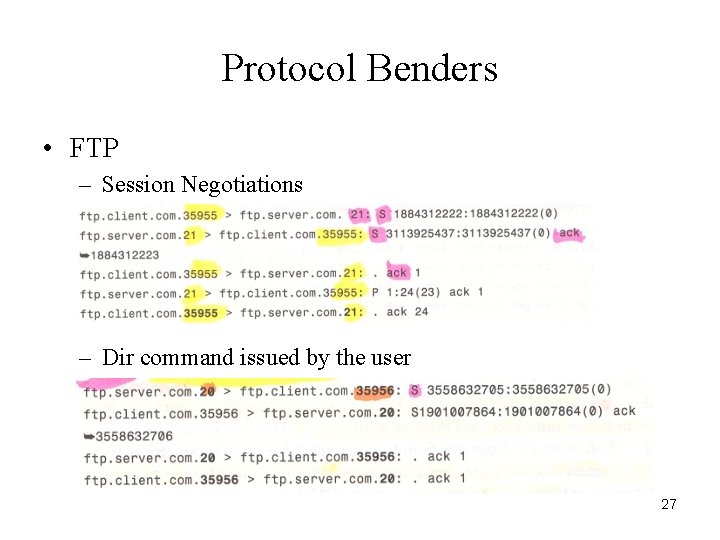
Protocol Benders • FTP – Session Negotiations – Dir command issued by the user 27

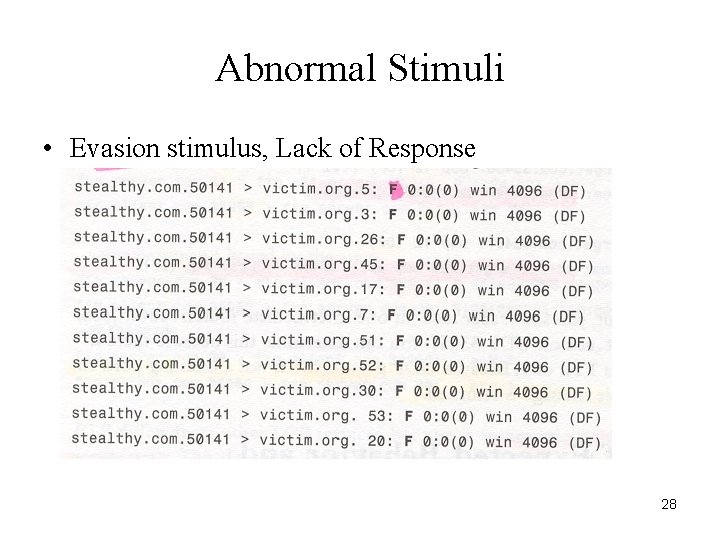
Abnormal Stimuli • Evasion stimulus, Lack of Response 28

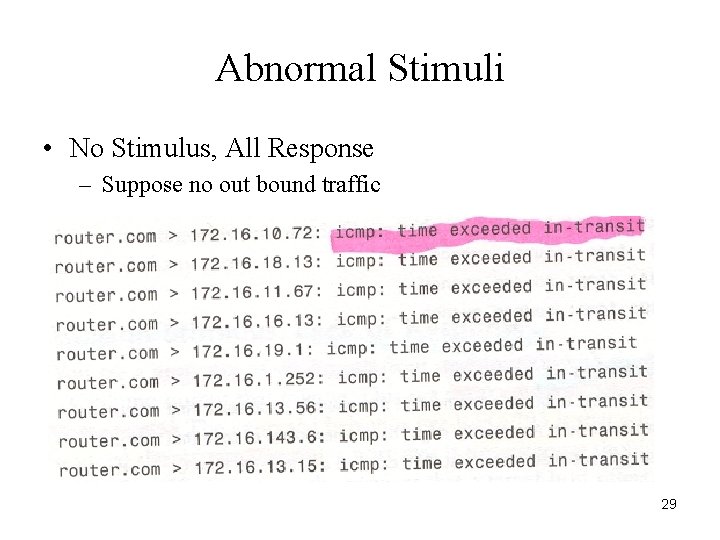
Abnormal Stimuli • No Stimulus, All Response – Suppose no out bound traffic 29