Randomized PRF Tree Walking Algorithm for Secure RFID









- Slides: 20

Randomized PRF Tree Walking Algorithm for Secure RFID Leonid Bolotnyy and Gabriel Robins Department of Computer Science University of Virginia lb 9 xk@cs. virginia. edu, robins@cs. virginia. edu

Talk Outline • Identification Problem – Secure Binary-Tree Walking Algorithm • Reader-tag Authentication Problem • Multi-tag RFID Systems

Identification Problem Tags Local Server Reader Tag ID

Secure Identification Problem Tags Local Server Reader Tag ID

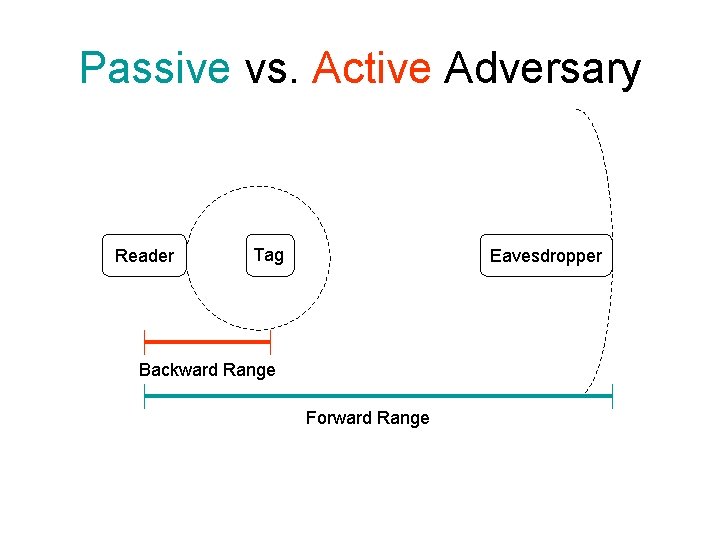
Passive vs. Active Adversary Reader Tag Eavesdropper Backward Range Forward Range

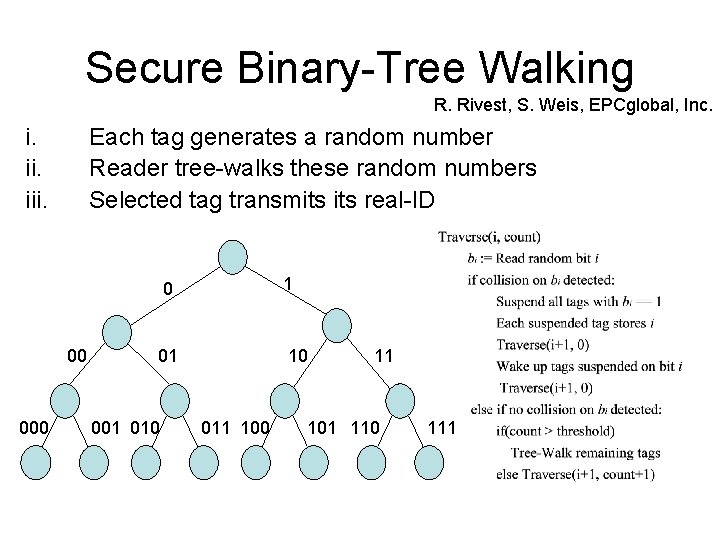
Secure Binary-Tree Walking R. Rivest, S. Weis, EPCglobal, Inc. i. iii. Each tag generates a random number Reader tree-walks these random numbers Selected tag transmits real-ID 00 0 1 01 10 001 010 011 100 11 101 110 111

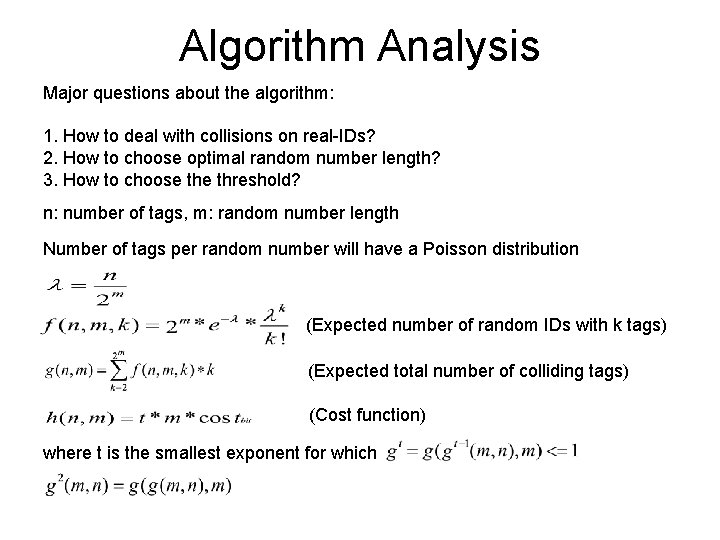
Algorithm Analysis Major questions about the algorithm: 1. How to deal with collisions on real-IDs? 2. How to choose optimal random number length? 3. How to choose threshold? n: number of tags, m: random number length Number of tags per random number will have a Poisson distribution (Expected number of random IDs with k tags) (Expected total number of colliding tags) (Cost function) where t is the smallest exponent for which

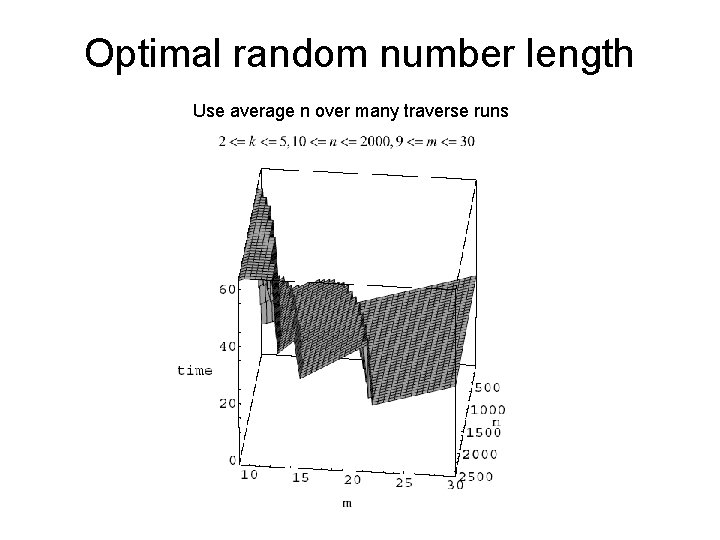
Optimal random number length Use average n over many traverse runs

Determining threshold (Expected number of tags on a branch after Pr[ bits) tags match in threshold number of bits] = For n = 2000, after about 11 bits, we expect zero, one, or two bits per branch Still have a “long” way to finish traversing the tree Costly over all branches if we traverse every branch to the end Start the threshold at 2 Increase threshold by 1 if collision occurs Decrease threshold by 1 if over the entire traverse no collisions occurred

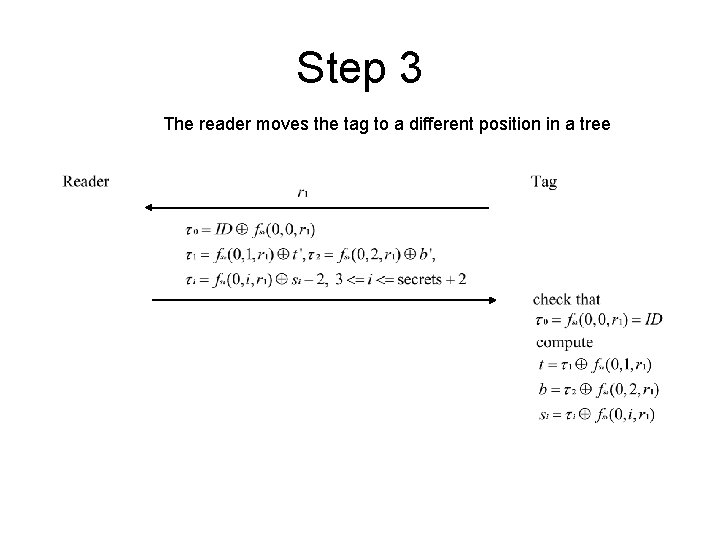
Randomized PRF Tree Walking Algorithm Goal: Efficiently solve reader-tag authentication problem in the presence of many tags Steps of the algorithm: 1. Each tag generates a random number, and the reader performs a tree-walk on these numbers 2. Once a tag is selected, the reader and the tag engage in a tree-waking private authentication protocol 3. The reader moves the tag to a different position in a tree.

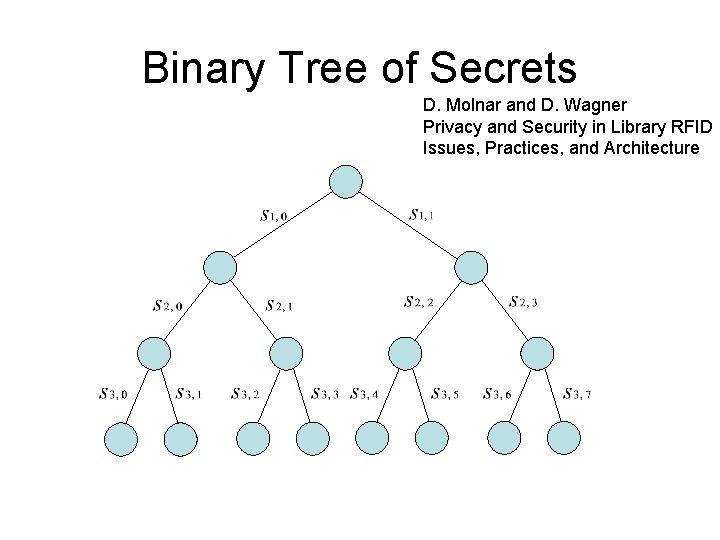
Binary Tree of Secrets D. Molnar and D. Wagner Privacy and Security in Library RFID Issues, Practices, and Architecture

Step 1 Each tag generates a random number, and the reader performs a tree-walk on these numbers

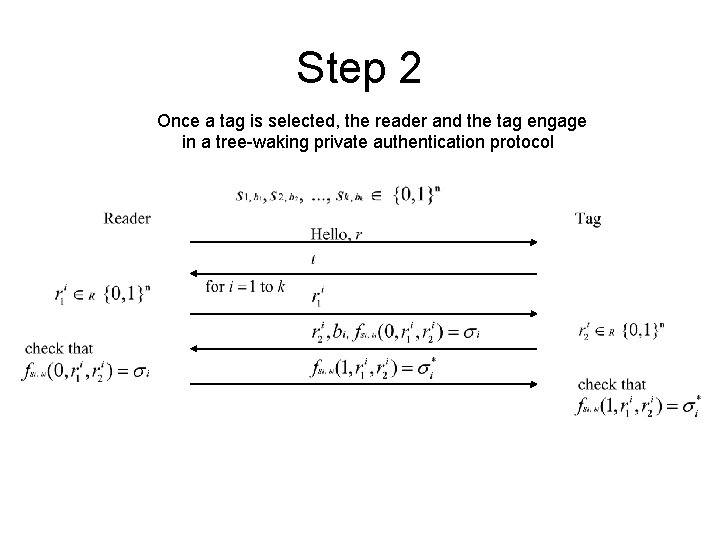
Step 2 Once a tag is selected, the reader and the tag engage in a tree-waking private authentication protocol

Step 3 The reader moves the tag to a different position in a tree

Properties of the Algorithm • • Allows on-line addition and removal of tags Provides security against active eavesdroppers Offers security against foreign readers Enables dynamic tradeoff between security, privacy and singulation time • Effective against active attacks – stealing a tag – tracking and hotlisting • Requires a tag to be equipped with – pseudo-random function, XOR unit – random number generator – writable memory

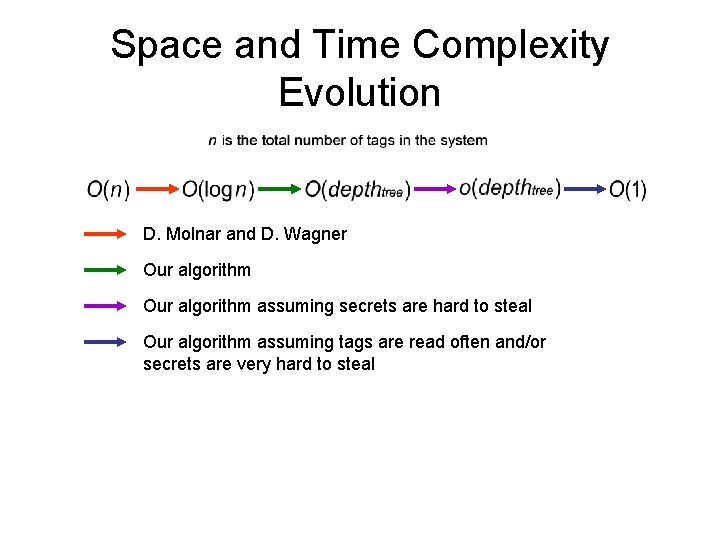
Space and Time Complexity Evolution D. Molnar and D. Wagner Our algorithm assuming secrets are hard to steal Our algorithm assuming tags are read often and/or secrets are very hard to steal

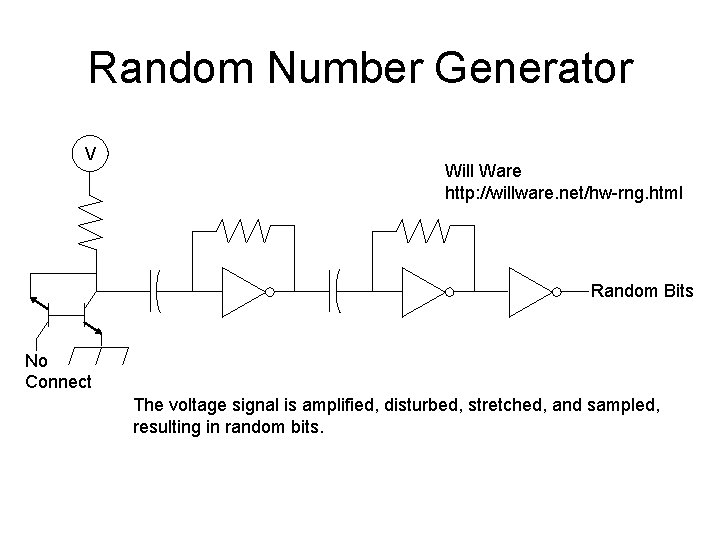
Random Number Generator V Will Ware http: //willware. net/hw-rng. html Random Bits No Connect The voltage signal is amplified, disturbed, stretched, and sampled, resulting in random bits.

New Idea: Multi-Tags Attach more than one tag to an object • Redundant Tags • Dual-Tags – Own Memory Only – Shared Memory Only – Own and Shared Memory • Triple-Tags • n-Tags 1 2 3 4

Benefits of Multi-Tag Systems New applications • Increased expected voltage on a tag • Increased expected communication range – Increased availability • • Increased memory Increased reliability Increased durability Enhanced security

Our Current and Future Work Find New and Improve Existing Algorithms A. Juels, S. Weis Authentication algorithms with human protocols D. Molnar, D. Wagner Tag identification with delegation, ownership transfer A. Juels Efficient cloning-resistant identification algorithms New and emerging problems Let’s Collaborate!