RADIUS Georgy Melamed Eran Stiller RADIUS In This

















- Slides: 27

RADIUS Georgy Melamed Eran Stiller RADIUS

In This Presentation… Why Do We Need It? What is RADIUS? RADIUS Operation RADIUS Packets Operation Examples Attacks on RADIUS’ EAP Support RADIUS 2

Why Do We Need It? Embedded Network Devices Multiple Users & Workstations Simple Network Access Servers (NAS) l Central User Administration l User Roaming l Protection Against Sniffing / Active Attacker RADIUS 3

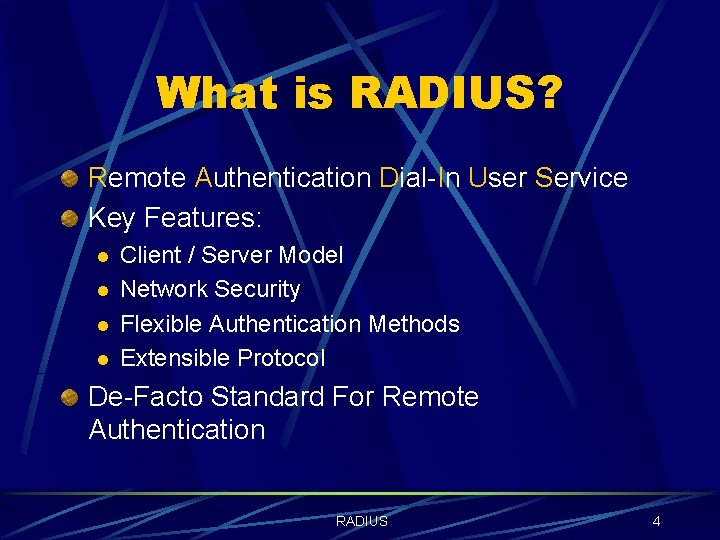
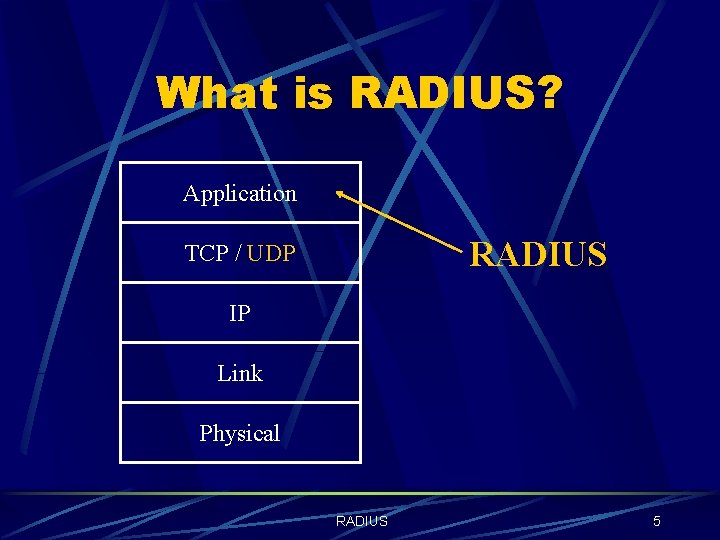
What is RADIUS? Remote Authentication Dial-In User Service Key Features: l l Client / Server Model Network Security Flexible Authentication Methods Extensible Protocol De-Facto Standard For Remote Authentication RADIUS 4

What is RADIUS? Application RADIUS TCP / UDP IP Link Physical RADIUS 5

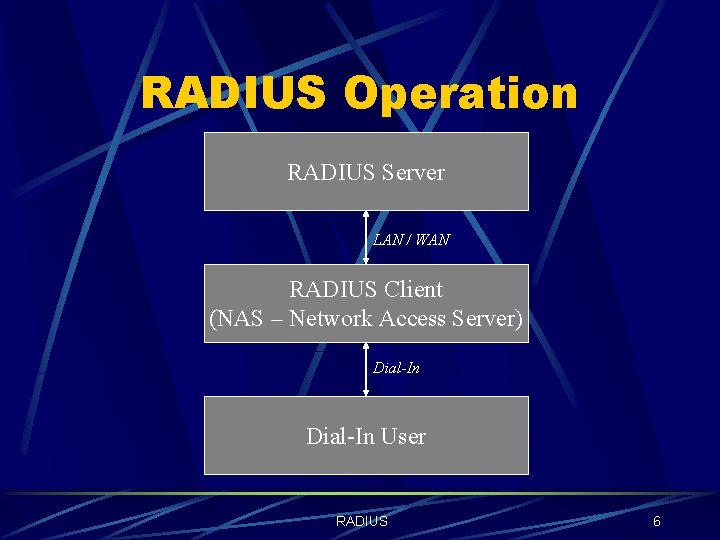
RADIUS Operation RADIUS Server LAN / WAN RADIUS Client (NAS – Network Access Server) Dial-In User RADIUS 6

RADIUS Operation RADIUS Uses UDP. Why? l Significantly Different Timing Requirements l l Stateless Protocol l l However, retransmission capabilities are still needed Clients and servers come and go Simplifies Server Implementation Keep-Alives Considered Harmful RADIUS 7

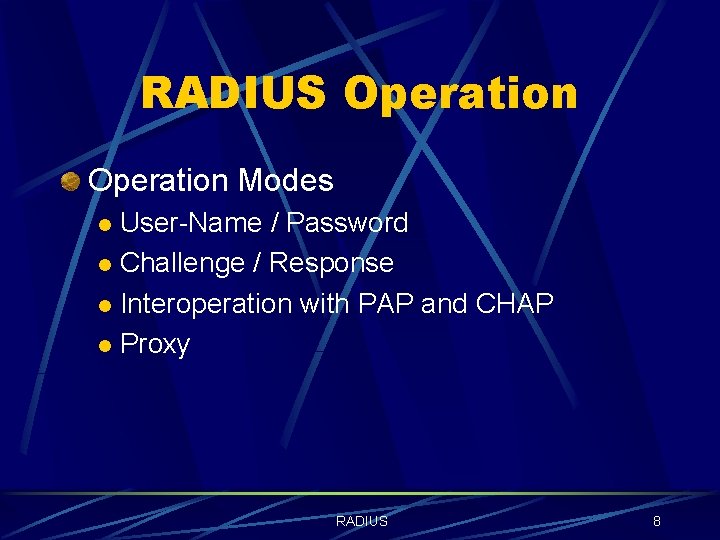
RADIUS Operation Modes User-Name / Password l Challenge / Response l Interoperation with PAP and CHAP l Proxy l RADIUS 8

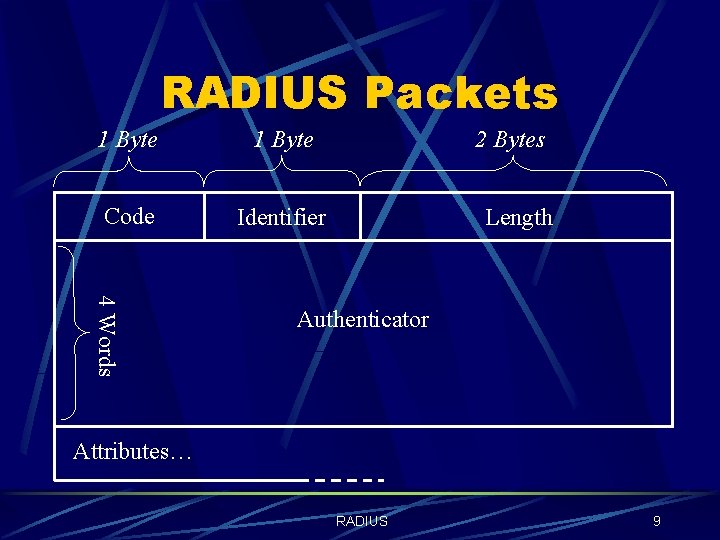
RADIUS Packets 1 Byte Code Identifier 2 Bytes Length 4 Words Authenticator Attributes… RADIUS 9

RADIUS Packets Packet Types Access-Request l Access-Accept l Access-Reject l Access-Challenge l RADIUS 10

RADIUS Packets The Authenticator l Request Authenticator Unpredictable and unique over the lifetime of a secret l Used for user-password hiding l l Response Authenticator l Calculated by an MD-5 hash: MD 5(Code + ID + Length + Request. Auth + Attributes + Secret) RADIUS 11

Examples User Telnet To Specified Host User Authenticating With CHAP User With Challenge-Response Card RADIUS 12

Attacks On RADIUS Weaknesses Of The Protocol Operation Modes User Name / Password Mode l Challenge / Response Mode l RADIUS 13

Attacks On RADIUS Response Authenticator Based Shared Secret Attack l l Attacker listens to requests and server responses, and pre-compute MD 5 state, which is the prefix of the response authenticator: MD 5(Code+ID+Length+Req. Auth+Attrib) Perform an exhaustive search on shared secret, adding it to the above MD 5 state each time. l Many implementations receive shared secret as an ASCII string from keyboard, and limit size to 16 bytes. RADIUS 14

Attacks On RADIUS User-Password Attribute Based Shared Secret Attack l l l The attacker attempts a connection to the NAS, and intercepts the access-request. XORs the user password attribute with the password he used to obtain: MD 5(Secret+Req. Auth) Perform an exhaustive search on shared secret. l l Cannot pre-compute MD 5 state. Finding the MD 5 value, is useful for other attacks. RADIUS 15

Attacks On RADIUS User-Password Based Password Attack l l The attacker attempts a connection to the NAS, intercepts the access-request and computes MD 5(Secret+Req. Auth). Performs an exhaustive / dictionary attack on password, XORing it with above MD 5 and sending it each time in appropriate attribute. l l Bypasses any login restriction imposed by NAS. Possible due to no authentication on request packet. RADIUS 16

Attacks On RADIUS Request Authenticator Based Attacks l Possible due to bad implementations: Poor Pseudo Random Number Generator l Predictable Request ID l RADIUS 17

Attacks On RADIUS Request Authenticator Based Attacks l Passive User-Password Compromise through Repeated Request Authenticators l l l Attacker builds a dictionary of Req. Auth and userpassword attribute sent by NAS. When a Req. Auth repeats itself, attacker can XOR userpassword attributes and obtain: password 1 XOR password 2 Perform a dictionary attack, combined with the fact that the longer password is padded with 0’s, causing the other password’s characters XORed with it to remain unchanged. RADIUS 18

Attacks On RADIUS Request Authenticator Based Attacks l Active User-Password Compromise through Repeated Request Authenticators Attacker builds a dictionary as before. l When he predicts he can cause NAS to use a certain Req. Auth, he tries to connect it and intercepts access-request. l Calculates “password 1 XOR password 2”, but this time password 2 is known, thus user password is compromised. l RADIUS 19

Attacks On RADIUS Request Authenticator Based Attacks l Replay of Server Responses through Repeated Request Authenticators l l l The attacker builds a dictionary with Req. Auth, ID and entire server response. Most server responses will be access-accept. The attacker will attempt a connection to NAS, predicting the Req. Auth and ID, intercept the access-request, and inject the NAS with the packet from the dictionary which is an access-accept, and has same Req. Auth and ID. RADIUS 20

Attacks On RADIUS Request Authenticator Based Attacks l Do. S Arising from the Prediction of the Request Authenticator Much like previous attack. l This time, attacker connects to NAS many times, and building same dictionary as before, only this time with access-rejects. l When user tries to connect, and NAS uses repeated Req. Auth, the attacker injects his access-reject, causing a denial of service. l RADIUS 21

Attacks On RADIUS Summary User-Password Protection Technique l The Response-Authenticator l Access-Request Packets l Random Number Generators l Shared Secrets l RADIUS 22

RADIUS’ EAP Support RADIUS-Encapsulated EAP Packets Proprietary Protocol Between RADIUS Server and Backend Security Server Proxied RADIUS requests Retransmission and Fragmentation Issues RADIUS 23

RADIUS’ EAP Support Security Considerations Separation of EAP Server and PPP Authenticator l Connection Hijacking l Man-in-the-Middle Attack l Multiple Databases l Negotiation Attacks l RADIUS 24

Conclusion RADIUS is a remote authentication protocol. RADIUS is a de-facto standard for remote authentication. RADIUS has several weaknesses. RADIUS is an extensible protocol, and can support many authentication methods (e. g. EAP). RADIUS 25

What Next? Diameter l "Diameter clients, such as Network Access Servers (NASes) and Foreign Agents MUST support IP Security, and MAY support TLS. Diameter servers MUST support TLS, but the administrator MAY opt to configure IPSec instead of using TLS. Operating the Diameter protocol without any security mechanism is not recommended. " RADIUS 26

Questions ? RADIUS 27
 Georgy zhukov
Georgy zhukov (fueron/eran) las doce.
(fueron/eran) las doce. Periodic table of elements atomic radius
Periodic table of elements atomic radius Virtudes del apostol pedro
Virtudes del apostol pedro Eran nuestras dolencias las que llevaba
Eran nuestras dolencias las que llevaba Vaisías
Vaisías Versiculos de primera comunion
Versiculos de primera comunion Eran tromer
Eran tromer Hombres cobardes en la biblia
Hombres cobardes en la biblia Poemas de juglares
Poemas de juglares Eran fields
Eran fields Cómo eran las uvas que había en la parra silvestre
Cómo eran las uvas que había en la parra silvestre Que eran las guerras floridas
Que eran las guerras floridas Quiénes eran los francos
Quiénes eran los francos Los delfines eran terrestres
Los delfines eran terrestres Los huilliches eran nómadas o sedentarios
Los huilliches eran nómadas o sedentarios Que era la polis en grecia
Que era la polis en grecia Valivan el fariseo y el publicano
Valivan el fariseo y el publicano Eran segal
Eran segal Dr eran (ronald) lev
Dr eran (ronald) lev Colosenses 2 12-14 explicacion
Colosenses 2 12-14 explicacion Eran segal
Eran segal Que eran los polis
Que eran los polis Cultura greco
Cultura greco Intentalo fueron/eran las doce
Intentalo fueron/eran las doce Yaniv segal
Yaniv segal Malquesis
Malquesis Cuales eran los colores de la túnica de josé
Cuales eran los colores de la túnica de josé