Radio Frequency Identification Systems New Ideas and Algorithms
- Slides: 1

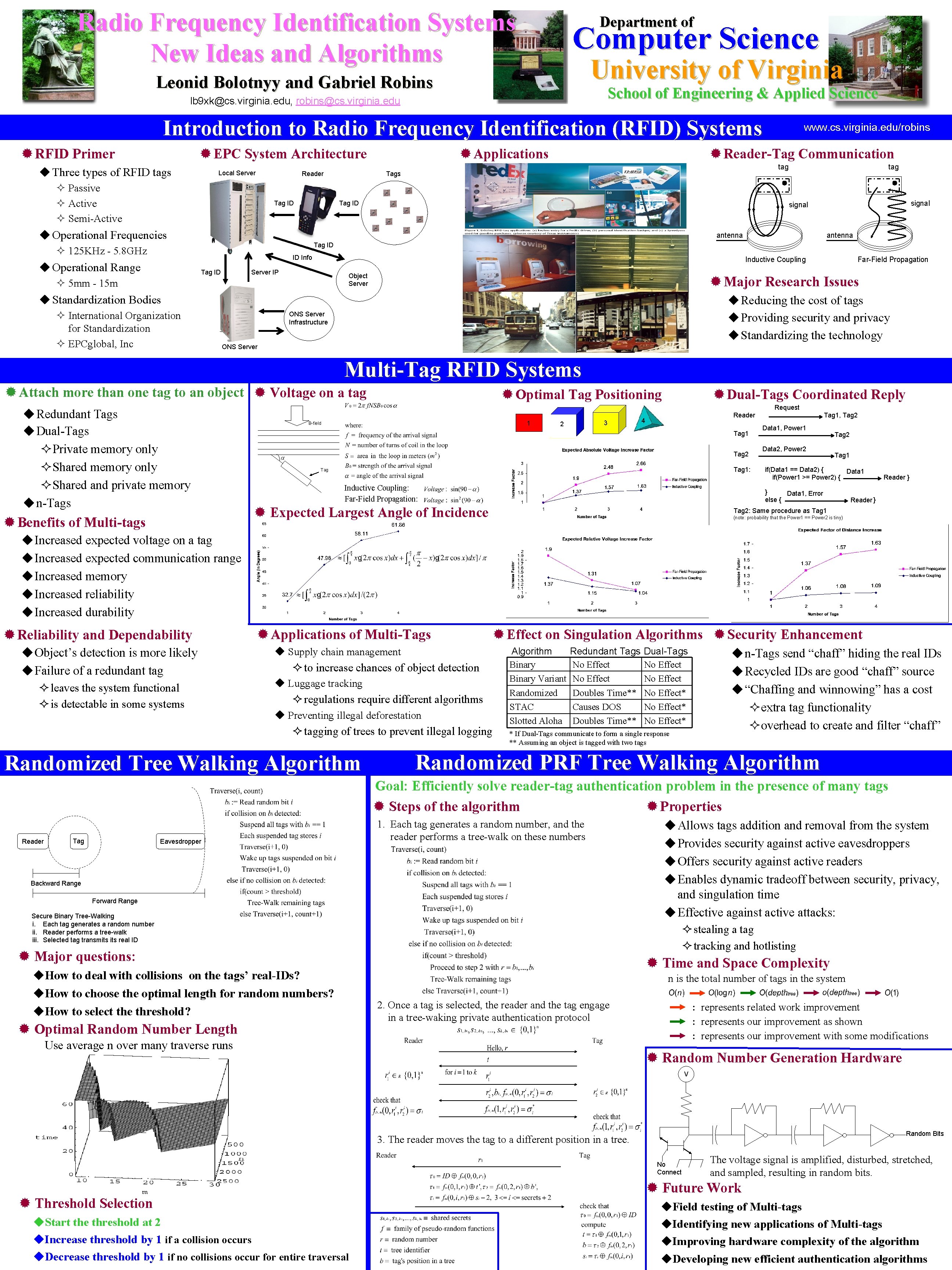
Radio Frequency Identification Systems New Ideas and Algorithms Department of Computer Science University of Virginia Leonid Bolotnyy and Gabriel Robins School of Engineering & Applied Science lb 9 xk@cs. virginia. edu, robins@cs. virginia. edu Introduction to Radio Frequency Identification (RFID) Systems ® RFID Primer ® EPC System Architecture u Three types of RFID tags Local Server Reader ² Passive ² Active ² Semi-Active Tag ID ® Applications www. cs. virginia. edu/robins ® Reader-Tag Communication tag Tags Tag ID tag signal u Operational Frequencies antenna Tag ID ² 125 KHz - 5. 8 GHz ID Info u Operational Range Tag ID Inductive Coupling Server IP Object Server ² 5 mm - 15 m ® Major Research Issues u Standardization Bodies ² International Organization for Standardization ² EPCglobal, Inc Far-Field Propagation u Reducing the cost of tags u Providing security and privacy u Standardizing the technology ONS Server Infrastructure ONS Server Multi-Tag RFID Systems ® Attach more than one tag to an object ® Voltage on a tag u Redundant Tags u Dual-Tags ² Private memory only ² Shared and private memory u n-Tags ® Benefits of Multi-tags ® Optimal Tag Positioning ® Dual-Tags Coordinated Reply Request 1 B-field 3 2 Reader 4 Tag 1 Tag 2 Tag 1: Tag Inductive Coupling: Far-Field Propagation: Tag 1, Tag 2 Data 1, Power 1 Data 2, Power 2 Tag 1 if(Data 1 == Data 2) { Data 1 if(Power 1 >= Power 2) { } Data 1, Error else { ® Expected Largest Angle of Incidence Reader } Tag 2: Same procedure as Tag 1 (note: probability that the Power 1 == Power 2 is tiny) u Increased expected voltage on a tag u Increased expected communication range u Increased memory u Increased reliability u Increased durability ® Reliability and Dependability u Object’s detection is more likely u Failure of a redundant tag ² leaves the system functional ² is detectable in some systems ® Applications of Multi-Tags ® Effect on Singulation Algorithms ® Security Enhancement u Supply chain management ² to increase chances of object detection u Luggage tracking ² regulations require different algorithms u Preventing illegal deforestation ² tagging of trees to prevent illegal logging Randomized Tree Walking Algorithm Binary Variant Randomized STAC Slotted Aloha Redundant Tags No Effect Doubles Time** Causes DOS Doubles Time** Dual-Tags No Effect* No Effect* * If Dual-Tags communicate to form a single response ** Assuming an object is tagged with two tags u n-Tags send “chaff” hiding the real IDs u Recycled IDs are good “chaff” source u “Chaffing and winnowing” has a cost ² extra tag functionality ² overhead to create and filter “chaff” Randomized PRF Tree Walking Algorithm Goal: Efficiently solve reader-tag authentication problem in the presence of many tags ® Steps of the algorithm ® Properties Reader Tag Eavesdropper 1. Each tag generates a random number, and the reader performs a tree-walk on these numbers Backward Range Forward Range Secure Binary Tree-Walking i. Each tag generates a random number ii. Reader performs a tree-walk iii. Selected tag transmits real ID ² stealing a tag ² tracking and hotlisting ® Major questions: u. How to deal with collisions on the tags’ real-IDs? u. How to choose the optimal length for random numbers? u. How to select the threshold? ® Optimal Random Number Length u Allows tags addition and removal from the system u Provides security against active eavesdroppers u Offers security against active readers u Enables dynamic tradeoff between security, privacy, and singulation time u Effective against active attacks: ® Time and Space Complexity n is the total number of tags in the system 2. Once a tag is selected, the reader and the tag engage in a tree-waking private authentication protocol Use average n over many traverse runs : represents related work improvement : represents our improvement as shown : represents our improvement with some modifications ® Random Number Generation Hardware V Random Bits 3. The reader moves the tag to a different position in a tree. No Connect ® Threshold Selection u. Start the threshold at 2 u. Increase threshold by 1 if a collision occurs u. Decrease threshold by 1 if no collisions occur for entire traversal The voltage signal is amplified, disturbed, stretched, and sampled, resulting in random bits. ® Future Work u. Field testing of Multi-tags u. Identifying new applications of Multi-tags u. Improving hardware complexity of the algorithm u. Developing new efficient authentication algorithms