RAC Recovery Audit Contractor Connolly Healthcare Connolly is














































- Slides: 65

RAC • Recovery Audit Contractor – Connolly Healthcare Connolly is tasked with auditing Region C, which consists of the ARRA and HITECH: Two Years Later states of: AL, AR, CO, FL, GA, LA, MS, NC, NM, OK, SC, TN, TX, VA, WV and the territories of Puerto Rico. Group, and U. S. LLC Virgin Islands. Management Resource & Associates Lunch & Learn The RAC Program’s Mission: Biloxi, payments Mississippi "To reduce Medicare improper through efficient detection April the 14, identification 2011 and collection of overpayments, of underpayments, and the implementation of actions that will prevent future improper payments. ” Dinetia M. Newman, Esquire Balch & Bingham LLP 1

ARRA and HITECH: Two Years Later Today’s Agenda: – – – Background – – Operational and Compliance Challenges Rules for Business Associates Definition of “Breach” Breach Analysis Notification Requirements New Mississippi Law (H. B. 583) Penalty Structure Recent Enforcement Developments – Best Practices and Recommendations 2

Background 3 – HIPAA—August 1996 – Privacy Rule—April 2003 – Security Rule—April 2005 – Enforcement Rule—March 2006 – American Reinvestment and Recovery Act (“ARRA”) —February 17, 2009 – Health Information Technology for Economic and Clinical Health Act (“HITECH”)—ARRA Division A, Title XIII – Health Information Technology, § 13001 et seq

Background 4 – April 17, 2009—Security methodology for PHI – August 24, 2009 (effective September 23, 2009)—HITECH breach notification/ interim final rule (74 Fed. Reg. 42740) – October 30, 2009 (effective November 30, 2009)—HITECH enforcement/ interim final rule (74 Fed. Reg. 56123) – May 7, 2010 – Draft HIPAA Security Standards: Guidance on Risk Analysis – July 14, 2010 – Modifications to the HIPAA Privacy Security, and Enforcement Rules under HITECH Act: Proposed Rule (75 Fed. Reg. 40868) (“Proposed Rule”) (Proposed effective date 180 days following effective date of final rule’s issuance)

Rules for Business Associates 5

What is a “Business Associate”? – Defined at 45 C. F. R. § 160. 103 – Essentially, a person who performs or assists in performing, on behalf of a CE or OHCA (but not as part of the CE’s or OHCA’s workforce), a function or activity involving the use or disclosure of individually identifiable health information – Subcontractors as BAs? 6

Regulation of Business Associates Prior to HITECH – HIPAA Privacy (2002) and Security (2003) Rules applied indirectly to BAs through BA Agreements (BAAs) • With few exceptions, CEs required to have written BAA with BAs – If BA violated a term of the BAA, only CE faced penalties for violating HIPAA Privacy or Security only if complaint BAA was not in effect – CE could terminate the BAA and underlying contract or bring a contract action for damages but seldom did so. 7

Regulation of Business Associates After HITECH – Must comply with the Privacy Rule and the additional requirements of HITECH – “Minimum Necessary” disclosures – Disclosures to Health Plans – Marketing and Fundraising Limitations – Accounting of Disclosures – Access to PHI – Prohibition on Sale of PHI 8

Regulation of Business Associates After HITECH – Must comply with the administrative, physical and technical safeguards of the Security Rule – Must also comply with policies and procedures documentation requirements of Security Rule – Must comply with additional requirements of HITECH related to Security of e. PHI – Unsecured PHI breach reporting requirement 9

What is a “Business Associate” • Proposed Rule: – Includes specifically PSOs, HIEs, e-prescribing gateways, and PHR vendors – Broadens BA definition to include non-workforce subcontractors – Should BAAs be revised to update based on Privacy and Security Rule amendments in HITECH and clarifications and changes in Proposed Rule? 10

HIPAA “Breach and Breach Analysis” 11

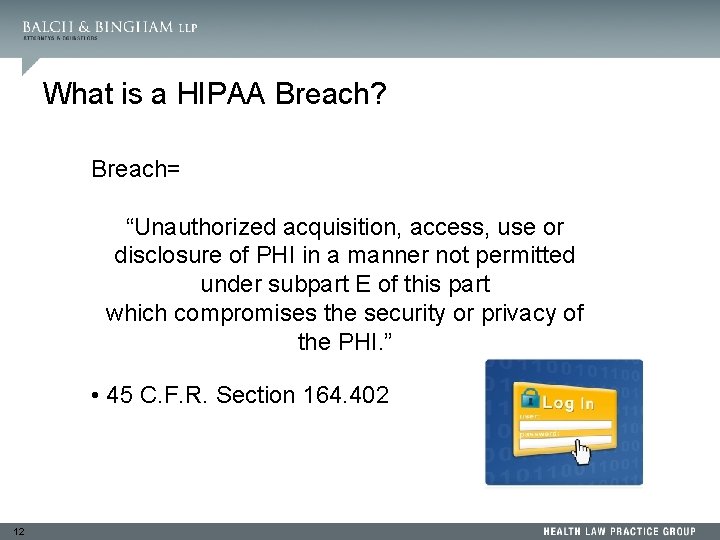
What is a HIPAA Breach? Breach= “Unauthorized acquisition, access, use or disclosure of PHI in a manner not permitted under subpart E of this part which compromises the security or privacy of the PHI. ” • 45 C. F. R. Section 164. 402 12

New Definition of “Breach” – 45 C. F. R. § 164. 402(1) – Paragraph (1) clarifies when security or privacy is considered to be compromised: (i) When the disclosure of PHI “poses a significant risk of financial, reputational, or other harm to the individual” – BUT note that (ii) A use or disclosure of PHI that doesn’t include the identifiers in § 164. 514(e)(2), date of birth, and zip code doesn’t compromise the security or privacy of the information. 13

New Definition of “Breach” – Breach Exceptions – 45 C. F. R. § 164. 402(2) – Paragraph (2) includes the statutory exceptions to a breach. 14 – (i): any unintentional acquisition, access or use of PHI by a workforce member or person acting under the authority of a CE or BA, if done in good faith and within the scope of authority and doesn’t result in further use or disclosure – Example: A workforce member, in the course of her duties, accidentally types in the wrong encounter number, i. e. , 01234 instead of 01243. When Jane Doe’s account instead of John Smith’s account is retrieved, she immediately recognizes her mistake and exits the chart

New Definition of “Breach” – Breach Exceptions, cont. 15 – (ii): any inadvertent disclosure by a person authorized to access PHI to another person authorized to access PHI at the same CE or BA or OHCA and the information received is not further used or disclosed – Example: Genie sending Julie Jones (instead of Joan Johnson) an email containing PHI, where: – Genie, Julie and Joan are part of the same workforce – Genie, Julie and Joan are authorized to access PHI – Julie recognizes the mistake and deletes the email

New Definition of “Breach” – Breach Exceptions, cont. 16 – (iii): a disclosure of PHI where a CE or BA has a good faith belief that the unauthorized person to whom the disclosure was made would not reasonably be able to retain such information – Example: The medical records copy clerk accidently drops an entire stack of copied medical records on the floor and a visitor to the hospital, seeing the mess, stops and helps her pick them up.

New Definition of “Breach” – Other Points – Most of the PHI we will encounter will be deemed “unsecured PHI”. – Neither password protection nor firewalls make PHI “secured PHI”. – The breach notification rules apply only to breaches of unsecured PHI. 17

Securing PHI: Encrypt or Destroy Encryption – Data at rest (NIST Special Publication 800 -111, Guide to Storage Encryption Technologies for End User Devices) – Data in transit (Federal Information Processing Standards 1402) Destruction – Non-electronic media: shredded or destroyed such that the PHI cannot be read or otherwise reconstructed – Electronic media: cleared, purged or destroyed consistent with NIST Special Publication 800 -88, Guidelines for Media Sanitization, so that PHI cannot be retrieved 18

Breach Analysis 19

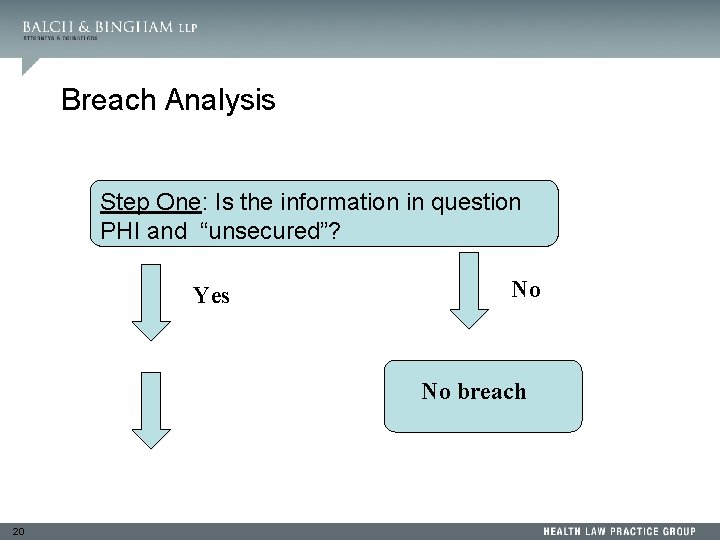
Breach Analysis Step One: Is the information in question PHI and “unsecured”? Yes No No breach 20

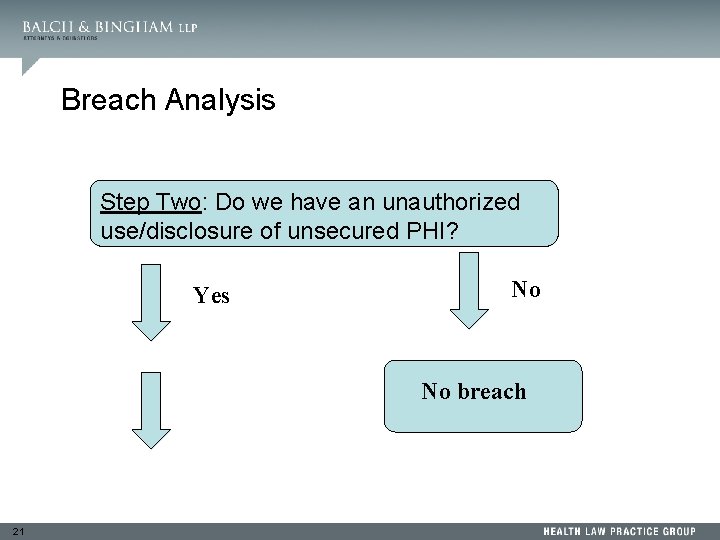
Breach Analysis Step Two: Do we have an unauthorized use/disclosure of unsecured PHI? Yes No No breach 21

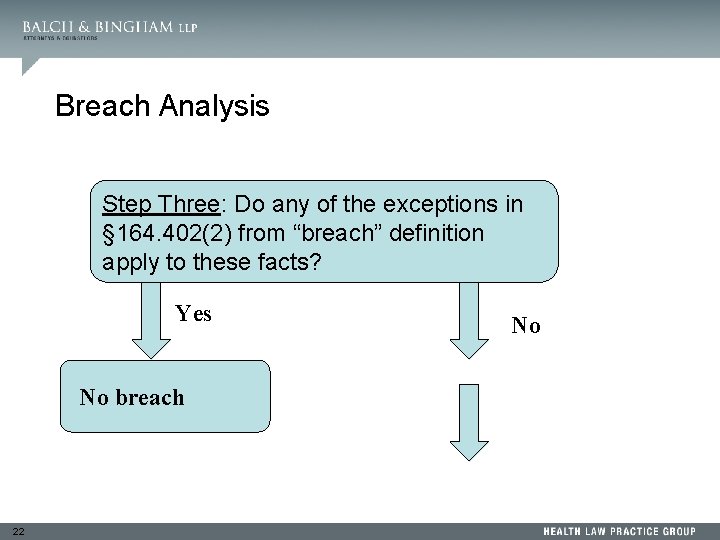
Breach Analysis Step Three: Do any of the exceptions in § 164. 402(2) from “breach” definition apply to these facts? Yes No breach 22 No

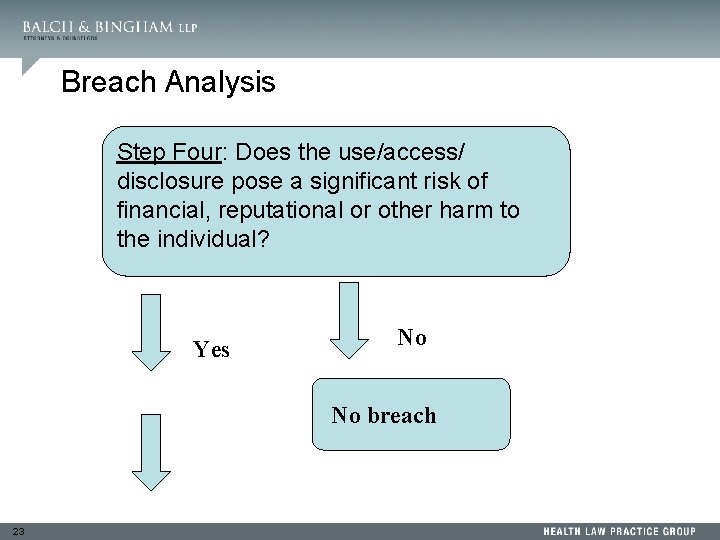
Breach Analysis Step Four: Does the use/access/ disclosure pose a significant risk of financial, reputational or other harm to the individual? Yes No No breach 23

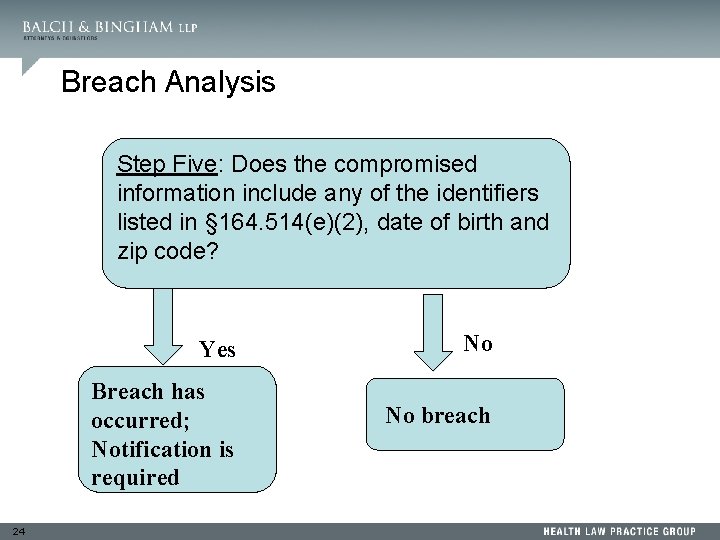
Breach Analysis Step Five: Does the compromised information include any of the identifiers listed in § 164. 514(e)(2), date of birth and zip code? Yes Breach has occurred; Notification is required 24 No No breach

• Query whether Breach analysis will be included in revised Final Rule 25

Breach Notification Requirements 26

Breach Notification Requirements 27 – The number of people affected by the breach is critical to assess because it determines how notice of the breach is given, to whom, and when. – The statute does allow for delays in notification because of law enforcement involvement under certain circumstances, but documentation requirements apply. See § 164. 412 for requirements and definition of law enforcement official in § 164. 103.

Breach Notification Requirements – Individuals – Notification to each affected individual is required “without unreasonable delay” and not later than 60 calendar days after discovery. – Notices to individuals are required to contain specific information about the breach in understandable language. See § 164. 404(c). – Notices are to be provided by mail or if agreed upon earlier, by email. See § 164. 404(d)(1). 28

Breach Notification Requirements Substitute Notice: § 164. 404(d)(2) – 29 If you have insufficient or out of date contact information for fewer than 10 individuals, substitute notice can be provided by an alternative form of written notice, telephone or other means.

Breach Notification Requirements – If you have insufficient or out of date contact information for more than 10 individuals, substitute notice must be: – in the form of a conspicuous posting on the home page of the website of the CE or – a “conspicuous notice in major print or broadcast media in geographic areas where the individuals affected by the breach likely reside” and – include a toll-free phone number active for at least 90 days where an individual can learn if his/her PHI was included in the breach. 30

Breach Notification Requirements – Media – If you have a breach involving more than 500 residents of a state, the CE must “notify prominent media outlets serving the state or jurisdiction”. – 31 Timing is the same as for individual notice— without unreasonable delay NTE 60 days

Breach Notification Requirements – Secretary of HHS – If you have a breach involving more than 500 individuals, the CE must notify the Secretary of HHS contemporaneously with the notification to individuals – 32 For breaches of fewer than 500 individuals, a CE must maintain a log or other documentation of breaches and, not later than 60 days after the end of each calendar year, provide notice to the Secretary of breaches occurring during the preceding calendar year.

Operational and Compliance Challenges 33

Operational and Compliance Challenges: Business Associate Agreements – HITECH • Business Associates are required to notify the CE following discovery of a breach “without unreasonable delay” NTE 60 days after discovery. • Business Associate Agreements may shorten this time frame, particularly if BA is an “agent” of the CE. • Business Associates are required to provide the CE with information for the notice. – 34 Debate over amending Business Associate Agreements continues.

Operational and Compliance Challenges: New Rules for Accounting Disclosures and TPO 35 – PRE-HITECH: CEs were required to provide an accounting of non-routine disclosures occurring during the prior 6 years; disclosures for TPO weren’t included. – HITECH: Accounting obligation will apply to TPO disclosures made through an EHR during the prior 3 years

Operational and Compliance Challenges: Rights of Individual to Access PHI – Pre-HITECH: Individuals have right to review and obtain copies of their PHI contained in a CE’s designated record set (within 30 days or, if off site, 60 days) with possible 30 day extension. – HITECH: Access rights expanded • Individual may direct a CE with an EHR to send a copy directly to a designee, but request must be clear, conspicuous and specific. • CE’s fee to provide electronic copy cannot exceed CEs labor costs involved. – Proposed Rule: If CE maintains PHI electronically and individual requests PHI in electronic form, CE must so provide it if readily producible and, if not, in a mutually agreeable electronic form and format. 36

Operational and Compliance Challenges: Notice of Privacy Practices – Pre-HITECH: NPPs must state that uses and disclosures in addition to permitted disclosures require individual’s written authorization and provide ability to opt out. – Proposed Rule: • NPP must state individual may opt out of various CE communications: those about treatment alternatives and other health related products and fund-raising communications. • NPP must state that individual may ask CE to restrict PHI disclosures regarding treatment for which individual (rather than health plan) has paid in full. 37

Operational and Compliance Challenges: Rules for PHI Restrictions 38 – Pre-HITECH: CEs were not required to agree to restrictions on disclosures that they were otherwise able to make for TPO purposes – HITECH: Patient’s request must be honored by CE if the disclosure is to a health plan for purposes of carrying out payment or health care operations (not treatment) AND the PHI pertains solely to a health care item or service for which the provider has been paid out of pocket in full.

Operational and Compliance Challenges: Restrictions on Sale of PHI – HITECH: Prohibition on sale of PHI except in certain limited circumstances • Statutory exemptions – public health activities, research, treatment, sale/merger/consolidation of CE, BA services, providing PHI to individual. • CE may receive financial remuneration for written treatment communications without authorization. • CE may not receive financial remuneration for HCO communications without authorization. 39

Operational and Compliance Challenges: Restrictions on Marketing and Fundraising – Right to opt-out of receiving fundraising communications – Proposed Rule: • Opt-out method must not cause individual undue burden • CE cannot condition treatment or payment on whether individual ops out • CE must assure opting out individual does not receive fund-raising communication (vs. just make “reasonable efforts”). – Changes in definition of marketing – HITECH: HCO disclosures for which CE receives direct or indirect payment require marketing authorization – Proposed Rule: Changes “direct or indirect payment” to “financial remuneration”. “Financial remuneration” includes cash and cash equivalents but does not include in-kind remuneration or payment for treatment by health plan or other responsible party. CE may receive remuneration for refill reminders if the payments is reasonably related to the CE’s cost to make the communication. – For most non-treatment related purposes, disclosures must be limited to “minimum necessary” 40

Operational and Compliance Challenges: • Pre-HITECH: • • • CE may condition receipt of research-related treatment on subject’s agreement to execute disclosure authorization Compound authorization allowed, e. g. , including subject’s consent to participate in research trial with authorization to disclose subject’s PHI Proposed Rule: • Would eliminate requirement for separate documents if certain conditions met – Must be clear differentiation between the two authorizations – Must allow for subject to approve or decline authorization for corollary activity • Issue: When research trial includes research-related treatment and corollary activity, e. g. , banking of tissue (and associated PHI), CE must obtain separate authorization – HHS requests comments regarding differentiating authorizations for treatment-related research and those for corollary activities NOTE: Issue involves research entities’ need to use PHI in databases for future research • • 41 Disclosure authorizations must be study specific Future research would require recontacting individual to sign additional authorization forms HHS solicits comments on the proposed options to better understand impact on conduct of research and patient understanding of authorization. Patient must still be able to revoke authorization for future research at any time

HIPAA Penalty Structure 42

HIPAA Penalty Structure – Pre-HITECH: $100/ violation, NTE $25, 000/yr for all violations of an identical requirement. – BUT there were limitations on the imposition of these penalties – HITECH and Enforcement Rule: • Tiered penalty structure tied to increasing levels of culpability • Penalties are based on the nature and extent of the violation, the nature and extent of the harm caused by the violation, and other factors in Section 160. 408 (history of compliance, etc. ) 43

HITECH Penalty Structure – Tier 1: “Did not know and would not have known through reasonable diligence”= $100 -$50, 000 each violation, NTE $1, 500, 000/ calendar year for identical violations – Tier 2: “Reasonable cause”= $1, 000 - $50, 000 each violation, NTE $1, 500, 000/ calendar year for identical violations 44

HITECH Penalty Structure 45 – Tier 3: “Willful Neglect—corrected”= $10, 000$50, 000 each violation, NTE $1, 500, 000/ calendar year for identical violations – Tier 4: “Willful Neglect—uncorrected”= minimum $50, 000 penalty each violation, NTE $1, 500, 000/ calendar year for identical violations

HITECH Penalty Structure 46 – 30 day cure period unchanged – Cure period begins on date of knowledge of the occurrence of a violation, not just the underlying facts – Consider: When did you have actual or constructive knowledge of the violation? – Agency implications – Business Associate implications

HITECH Penalty Structure 47 – Pre-HITECH: 3 affirmative defenses – HITECH: Timely correction is required for “did not know” and “reasonable cause” violations to establish an affirmative defense and avoid penalties. – Note: no affirmative defense is available for violations due to willful neglect, but their timely correction will result in the application of a lesser tier of penalties.

Proposed Rule Changes in Penalty Structure and OCR Enforcement – Significant changes to compliance provisions, investigations and civil monetary penalty (CMP) imposition – Mandatory Investigations vs. Informal Means – 2009 Enforcement Rule: permits, but does not require OCR to investigate HIPAA complaints – Proposed Rule: requires OCR investigation if preliminary review indicates willful neglect – 2009 Enforcement Rule: requires OCR to resolve noncompliance through “informal means” – Proposed Rule: permits, but does not require OCR to use “informal means” 48

Proposed Rule Changes in Penalty Structure and OCR Enforcement – Tiered Penalty Structure – Amends definition of “reasonable cause” – Explains how OCR will determine “reasonable cause”, “reasonable diligence”, “willful neglect” Example: Failure to develop compliant HIPAA policies and procedures demonstrates either “conscious intent or reckless disregard” and may be basis for violation due to “willful neglect” 49

Proposed Rule Changes in Penalty Structure and OCR Enforcement – Penalty Amounts – HITECH: penalty amounts based on factors – nature and extent of violation and harm – Proposed Rule: Permits OCR to consider number of individuals affected; time period affected; physical, financial or reputational harm; whether violation hindered an individual from obtaining healthcare 50

Proposed Rule Changes in Penalty Structure and OCR Enforcement – Affirmative Defenses – HITECH and Proposed Rule Criminal Penalty: • For violations occurring between February 18, 2009 and before February 18, 2011 – OCR may not impose CMP if offense is punishable under HIPAA criminal penalty provisions • For violations on or after February 18, 2011 – OCR may not impose CMP if criminal penalty has been imposed under HIPAA criminal penalty provisions 51

Proposed Rule Changes in Penalty Structure and OCR Enforcement – HIPAA Compliance Reviews – HITECH/Enforcement Rule: Authorizes OCR to conduct discretionary compliance reviews of CEs and BAs outside of complaint process – Proposed Rule: Requires OCR to conduct compliance review if preliminary review indicates violation due to willful neglect 52

Proposed Rule Changes in Penalty Structure and OCR Enforcement – Vicarious Liability for Violations by Agent’s Workforce – HITECH/Enforcement Rule: CE not liable if agent is BA, BAA requirements met, CE did not know of pattern/practice in violation of BAA, CE acted in accord with Privacy and Security Rules regarding violation – Proposed Rule: • CE is liable for BA agents’ actions even if compliant BAA in place • CMP liability of BAs for their actions of workforce and downstream BA agents 53

Recent OCR Enforcement and Settlement Actions Cignet Health of Prince George’s County, Maryland • Operator of family physician practice group with four Maryland locations and of health insurance plan • Nature of breach – Failure to provide 41 individuals timely access to medical record copies – Failure to cooperate with HHS in OCR’s investigation of patient complaints – Failure to correct violations within 30 days of when Cignet knew or with exercise of reasonable diligence would have know of violations • Penalties Imposed – $100 per day (13, 516 days) for failure to provide medical records to patients (total $1. 3 million) – $50, 000 per day (7, 478 days) for failure to cooperate with HHS/OCR (total $3 million) 54

Recent OCR Enforcement and Settlement Actions – General Hospital Corporation & Massachusetts General Physicians Organization, Inc. (Mass General) • Nature of Breach – Patients’ charts removed from Mass General’s Infectious Disease Associates outpatient practice and inadvertently left on subway train – Documents included billing and encounter forms with name, date of birth, medical record number, health insurer and policy number, diagnosis and name of provider – Also included daily office schedules with names and medical record numbers of 192 patients (including patients with HIV/Aids) • Settlement Terms – Immediate payment of $1 million dollars – 3 year Corrective Action Plan requiring policy and procedure development regarding physical removal and transportation of documents containing PHI, encryption of laptops and USB drives, processes to distribute and update policies and procedures, workforce training, designation of monitor for assembling annual report to HHS 55

Recent OCR Enforcement and Settlement Actions – Implications for Covered Entities • Lack of final regulation lulled many CEs and BAs along with workforces into complacence and non-compliance • Reminder that HHS has six (6) years to impose CMPs • Although final HITECH regulations for most statutory enactments have not been published, the breach notification interim final rule is enforceable and includes increased penalties • Cignet’s multiple failures and inactions constituted “willful neglect” significantly increasing penalty amounts • HHS’s Corrective Action Plan offers road map to prevent workforce incident resulting in HIPAA violation • Encryption or other security measures offer opportunity to significantly improve required compliance 56

New Mississippi Law 57

Mississippi Law – H. B. 583 (April 7, 2010, eff. 7/1/2011): Requires all businesses who own, license or maintain personal information of any resident of MS to notify those individuals in event of a breach – However, also includes a harm standard: notification isn’t required if, after an appropriate investigation, the person reasonably determines that the breach will not likely result in harm to the affected individuals. 58

Mississippi Law Applies only to electronic breaches of “personal information” – 59 “Personal information” includes first name or initial plus last name, plus any one of the following: – Social security number – Driver’s license number or state ID – Account/ credit/ debit card number along with required codes/ passwords necessary for access

Mississippi Law – Notice Requirements – May be written, by telephone, or electronic (under some circumstances) – Substitute notice is allowed in some cases but involves media notification and website posting 60

Recommendations and Best Practices 61

Recommendations and Best Practices – – – – 62 Comprehensive HIPAA Compliance Review Update Policies and Procedures BAA Review – Understand Obligations BA and subcontractor due diligence Education and Workforce Training Prepare for Contingencies Expect more changes to the rules

Resources/Additional Information – HIPAA Privacy Resources www. hhs. gov/ocr/privacy/hipaa/understanding/coveredentities/index. html – HIPAA Security Resources, Guidance and NIST publications: www. hhs. gov/ocr/privacy/hipaa/administrative/securityrulegui dance. html 63

QUESTIONS? 64

RAC • Recovery Audit Contractor – Connolly Healthcare Connolly is tasked with auditing Region C, which consists of the states of: AL, AR, CO, FL, GA, LA, MS, NC, NM, OK, SC, TN, TX, VA, WV and the territories of Puerto Rico and U. S. Virgin Islands. Thank You! Dinetia M. Newman Balch & Bingham LLP The RAC Program’s Mission: 401 East Capitol Street, through Suite 200 "To reduce Medicare improper payments efficient detection and collection of overpayments, of underpayments, Jackson, the MSidentification 39201 and the implementation of 601 -965 -8169 actions that will prevent future improper payments. ” dnewman@balch. com 128001 65
 Connolly recovery audit
Connolly recovery audit Healthcare and the healthcare team chapter 2
Healthcare and the healthcare team chapter 2 Healthcare and the healthcare team chapter 2
Healthcare and the healthcare team chapter 2 Prashan patel grant thornton
Prashan patel grant thornton Connolly & hickey historical architects
Connolly & hickey historical architects Fundamentals of web development randy connolly ppt
Fundamentals of web development randy connolly ppt Ocd and school refusal
Ocd and school refusal Andrew connolly exeter
Andrew connolly exeter Southleeasd
Southleeasd Connolly lodge buckingham street
Connolly lodge buckingham street Disaster recovery audit program isaca
Disaster recovery audit program isaca The term audit is originated from a latin word
The term audit is originated from a latin word Perbedaan audit konvensional dengan audit berbasis risiko
Perbedaan audit konvensional dengan audit berbasis risiko Prosedur audit bottom-up dan audit top-down!
Prosedur audit bottom-up dan audit top-down! Audit universe vs audit plan
Audit universe vs audit plan Audit informasi klinis
Audit informasi klinis What is vouching
What is vouching Overall audit plan
Overall audit plan Beda audit medis dan audit klinis
Beda audit medis dan audit klinis Perbedaan audit konvensional dengan audit berbasis risiko
Perbedaan audit konvensional dengan audit berbasis risiko Hubungan ekonomisasi efisiensi dan efektivitas
Hubungan ekonomisasi efisiensi dan efektivitas Penyelesaian audit dan tanggung jawab pasca audit
Penyelesaian audit dan tanggung jawab pasca audit Sharding oracle
Sharding oracle Rac timeline
Rac timeline The sacred rac meaning
The sacred rac meaning Ash report for rac
Ash report for rac Rac electric highway charging station
Rac electric highway charging station Oracle rac
Oracle rac Mc rac
Mc rac Reflectory definition
Reflectory definition Codul rac
Codul rac Rac servicing
Rac servicing Rac 101
Rac 101 Bảng chân trị logic
Bảng chân trị logic Raco fib upc edu
Raco fib upc edu Bridge rac
Bridge rac Rac assessment
Rac assessment Oracle oci icons
Oracle oci icons Rac periodic maintenance inspection
Rac periodic maintenance inspection Thung rac
Thung rac Quan hệ thứ tự toàn phần
Quan hệ thứ tự toàn phần Rac prototype
Rac prototype Rac certification sample questions
Rac certification sample questions Contractor management program
Contractor management program Efs contractor portal
Efs contractor portal Hard barrication for excavation
Hard barrication for excavation Todd shields contractor
Todd shields contractor Small dynamic business search from the ccr home page
Small dynamic business search from the ccr home page Chevron 10 tenets of operation
Chevron 10 tenets of operation Agricultural contractor job tracker
Agricultural contractor job tracker Connex ngs
Connex ngs Subrecipient vs contractor
Subrecipient vs contractor Tyne and wear crushing contractor
Tyne and wear crushing contractor Subrecipient vs contractor
Subrecipient vs contractor Contractor sourcing application
Contractor sourcing application Contractor onboarding
Contractor onboarding Cpars overview
Cpars overview Company profile contractor
Company profile contractor Contractor past performance examples
Contractor past performance examples Abci contractor
Abci contractor Volusia county code enforcement
Volusia county code enforcement Orhp contractor portal
Orhp contractor portal Ramm contractor
Ramm contractor Independent contractor computer jobs
Independent contractor computer jobs Sspc qp 1 contractor list
Sspc qp 1 contractor list Pt georg fischer trading indonesia
Pt georg fischer trading indonesia