Questions and Answers Submit text questions using the



Questions and Answers • Submit text questions using the “Ask a Question” button

What We Will Cover • Last time Known issues • Review Oct. releases – 10+1 New security bulletins (1 Out-of-band) – 2 High-priority non-security updates – 1 re-release on Sep. 25 (Out-of-band) • Other security resources – Windows Malicious Software Removal Tool • Resources • Questions and answers
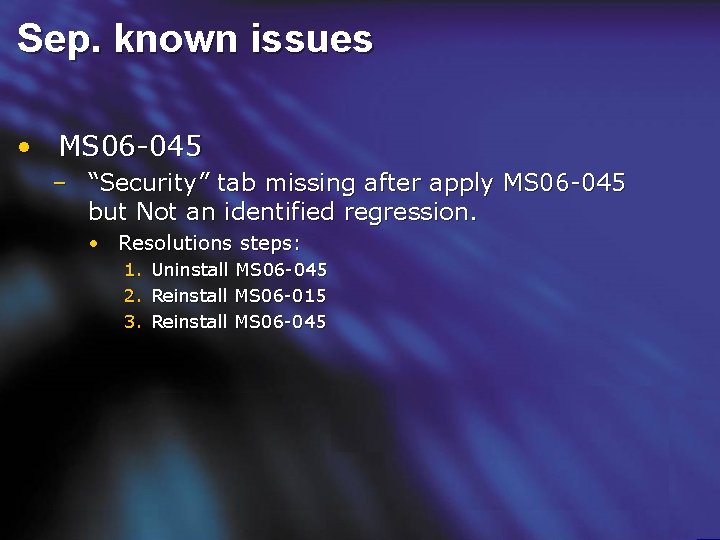
Sep. known issues • MS 06 -045 – “Security” tab missing after apply MS 06 -045 but Not an identified regression. • Resolutions steps: 1. 2. 3. Uninstall MS 06 -045 Reinstall MS 06 -015 Reinstall MS 06 -045
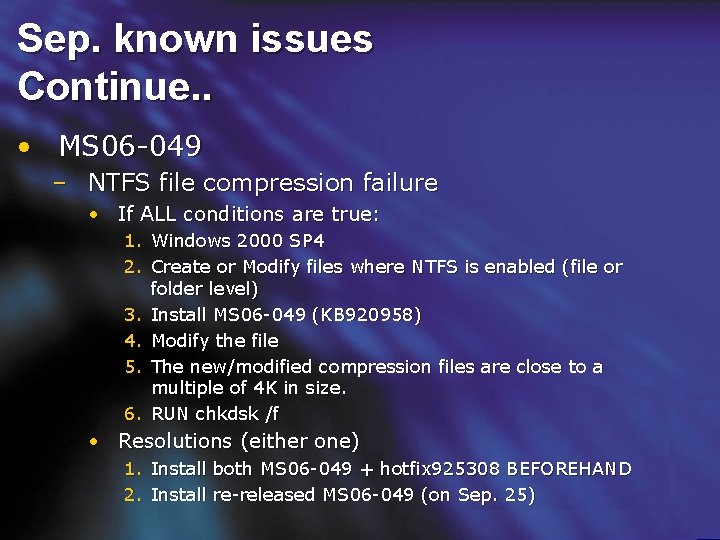
Sep. known issues Continue. . • MS 06 -049 – NTFS file compression failure • If ALL conditions are true: 1. Windows 2000 SP 4 2. Create or Modify files where NTFS is enabled (file or folder level) 3. Install MS 06 -049 (KB 920958) 4. Modify the file 5. The new/modified compression files are close to a multiple of 4 K in size. 6. RUN chkdsk /f • Resolutions (either one) 1. Install both MS 06 -049 + hotfix 925308 BEFOREHAND 2. Install re-released MS 06 -049 (on Sep. 25)

Oct 2006 Security Bulletins Summary • On Sep. 25, 2 Out-Of-Band releases – MS 06 -055 (Critical) – MS 06 -049 re-release (Important) • On Oct. 11, 10 New Security Bulletins – 7 new Critical – 2 new Moderate – 2 new Important – 1 new Low
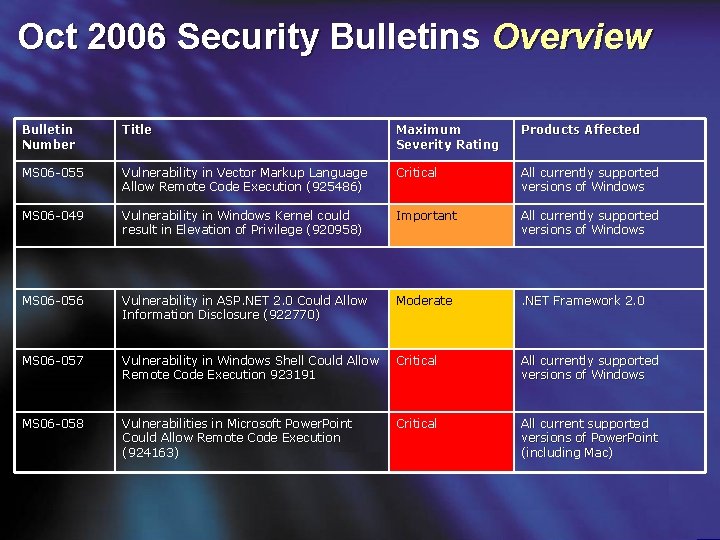
Oct 2006 Security Bulletins Overview Bulletin Number Title Maximum Severity Rating Products Affected MS 06 -055 Vulnerability in Vector Markup Language Allow Remote Code Execution (925486) Critical All currently supported versions of Windows MS 06 -049 Vulnerability in Windows Kernel could result in Elevation of Privilege (920958) Important All currently supported versions of Windows MS 06 -056 Vulnerability in ASP. NET 2. 0 Could Allow Information Disclosure (922770) Moderate . NET Framework 2. 0 MS 06 -057 Vulnerability in Windows Shell Could Allow Remote Code Execution 923191 Critical All currently supported versions of Windows MS 06 -058 Vulnerabilities in Microsoft Power. Point Could Allow Remote Code Execution (924163) Critical All current supported versions of Power. Point (including Mac)
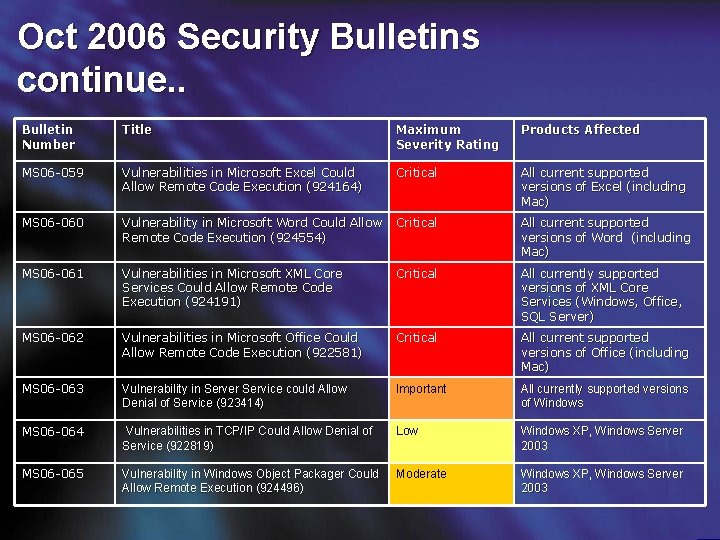
Oct 2006 Security Bulletins continue. . Bulletin Number Title Maximum Severity Rating Products Affected MS 06 -059 Vulnerabilities in Microsoft Excel Could Allow Remote Code Execution (924164) Critical All current supported versions of Excel (including Mac) MS 06 -060 Vulnerability in Microsoft Word Could Allow Remote Code Execution (924554) Critical All current supported versions of Word (including Mac) MS 06 -061 Vulnerabilities in Microsoft XML Core Services Could Allow Remote Code Execution (924191) Critical All currently supported versions of XML Core Services (Windows, Office, SQL Server) MS 06 -062 Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (922581) Critical All current supported versions of Office (including Mac) MS 06 -063 Vulnerability in Server Service could Allow Denial of Service (923414) Important All currently supported versions of Windows MS 06 -064 Vulnerabilities in TCP/IP Could Allow Denial of Service (922819) Low Windows XP, Windows Server 2003 MS 06 -065 Vulnerability in Windows Object Packager Could Allow Remote Execution (924496) Moderate Windows XP, Windows Server 2003
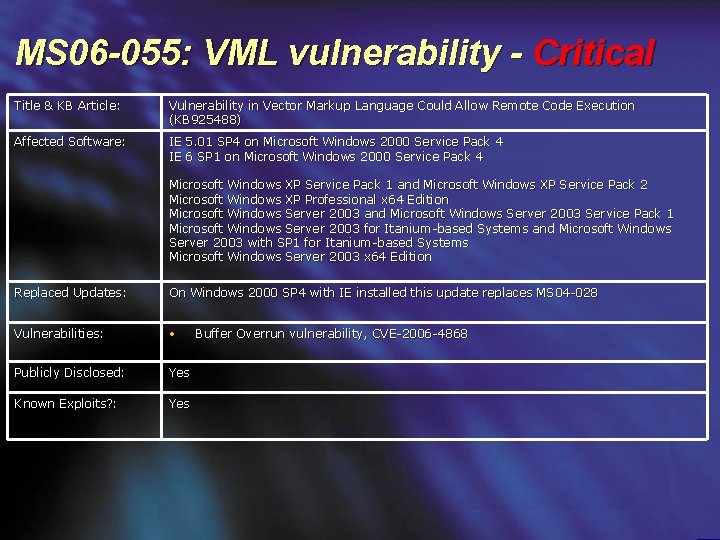
MS 06 -055: VML vulnerability - Critical Title & KB Article: Vulnerability in Vector Markup Language Could Allow Remote Code Execution (KB 925488) Affected Software: IE 5. 01 SP 4 on Microsoft Windows 2000 Service Pack 4 IE 6 SP 1 on Microsoft Windows 2000 Service Pack 4 Microsoft Windows XP Service Pack 1 and Microsoft Windows XP Service Pack 2 Microsoft Windows XP Professional x 64 Edition Microsoft Windows Server 2003 and Microsoft Windows Server 2003 Service Pack 1 Microsoft Windows Server 2003 for Itanium-based Systems and Microsoft Windows Server 2003 with SP 1 for Itanium-based Systems Microsoft Windows Server 2003 x 64 Edition Replaced Updates: On Windows 2000 SP 4 with IE installed this update replaces MS 04 -028 Vulnerabilities: • Publicly Disclosed: Yes Known Exploits? : Yes Buffer Overrun vulnerability, CVE-2006 -4868
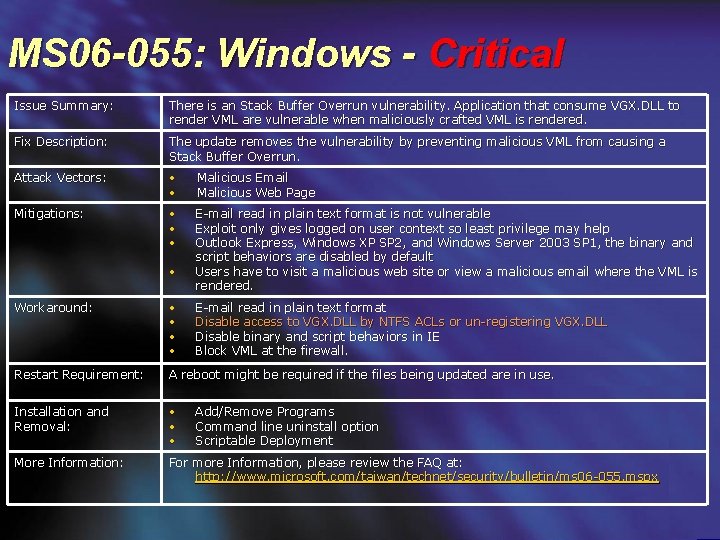
MS 06 -055: Windows - Critical Issue Summary: There is an Stack Buffer Overrun vulnerability. Application that consume VGX. DLL to render VML are vulnerable when maliciously crafted VML is rendered. Fix Description: The update removes the vulnerability by preventing malicious VML from causing a Stack Buffer Overrun. Attack Vectors: • • Malicious Email Malicious Web Page Mitigations: • • • E-mail read in plain text format is not vulnerable Exploit only gives logged on user context so least privilege may help Outlook Express, Windows XP SP 2, and Windows Server 2003 SP 1, the binary and script behaviors are disabled by default Users have to visit a malicious web site or view a malicious email where the VML is rendered. • Workaround: • • Restart Requirement: A reboot might be required if the files being updated are in use. Installation and Removal: • • • More Information: For more Information, please review the FAQ at: http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -055. mspx E-mail read in plain text format Disable access to VGX. DLL by NTFS ACLs or un-registering VGX. DLL Disable binary and script behaviors in IE Block VML at the firewall. Add/Remove Programs Command line uninstall option Scriptable Deployment

Questions about MS 06 -055?
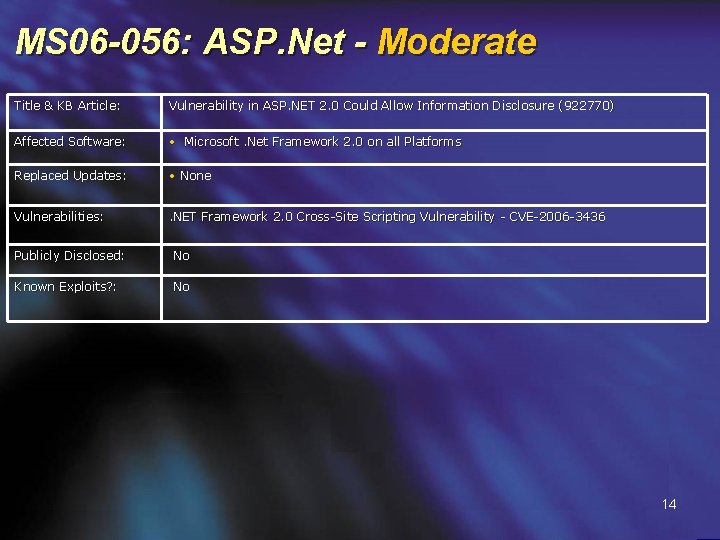
MS 06 -056: ASP. Net - Moderate Title & KB Article: Vulnerability in ASP. NET 2. 0 Could Allow Information Disclosure (922770) Affected Software: • Microsoft. Net Framework 2. 0 on all Platforms Replaced Updates: • None Vulnerabilities: . NET Framework 2. 0 Cross-Site Scripting Vulnerability - CVE-2006 -3436 Publicly Disclosed: No Known Exploits? : No 14
MS 06 -056: ASP. Net - Moderate Issue Summary: A cross-site scripting vulnerability exists in ASP. NET that could allow an attacker to run client-side script on behalf of a user. Fix Description: The update removes the vulnerability by modifying the way that. ASP. NET validates the value on a HTTP request. Attack Vectors: • • Malicious Web Page Malicious Email containing URL to malicious web site Mitigations: • • A user would have to be persuaded to visit a malicious Web site By default ASP. NET 2. 0 controls do not set the Auto. Post. Back property to “true”. Workaround: • Disable Auto. Post. Back controls on web page Restart Requirement: No Installation and Removal: • More Information: For more Information, please review the FAQ at: http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -056. mspx Add/Remove Programs 15

Questions about MS 06 -056?
MS 06 -057: Windows - Critical Title & KB Article: Vulnerability in Windows Shell Could Allow Remote Code Execution (KB 923191) Affected Software: Microsoft Windows 2000 Service Pack 4 Microsoft Windows XP Service Pack 1 and Microsoft Windows XP Service Pack 2 Microsoft Windows XP Professional x 64 Edition Microsoft Windows Server 2003 and Microsoft Windows Server 2003 Service Pack 1 Microsoft Windows Server 2003 for Itanium-based Systems and Microsoft Windows Server 2003 with SP 1 for Itanium-based Systems Microsoft Windows Server 2003 x 64 Edition Replaced Updates: None Vulnerabilities: • Publicly Disclosed: Yes Known Exploits? : Yes CVE-2006 -4690 17
MS 06 -057: Windows - Critical Issue Summary: The Active. X control called out in the public reports and in the Proof of Concept code is the Microsoft Web. View. Folder. Icon Active. X control (Web View). The vulnerability exists in Windows Shell and is exposed by Web View. Fix Description: The update removes the vulnerability by resolving the code issue. Attack Vectors: • • Malicious Email Malicious Web Page Mitigations: • A user would have to be persuaded to visit a malicious Web site Workaround: • • • Set IE security to High for Internet and Intranet zones Read e-mail messages in plain text format Set killbit for Web. View. Folder. Icon Active. X control Configure IE to prompt before running Active. X controls Restrict browsing to trusted web sites Restart Requirement: Yes Installation and Removal: • • • More Information: For more Information, please review the FAQ at: http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -057. mspx Add/Remove Programs Command line uninstall option Scriptable Deployment 18

Questions about MS 06 -057? 19

MS 06 -058: Power. Point - Critical Title Vulnerabilities in Microsoft Power. Point Could Lead to Remote Code Execution (924163) The Problem This Power. Point update addresses four 'Remote Code Execution' Power. Point vulnerabilities. An attacker could exploit one of these vulnerabilities by constructing a specially crafted file that could potentially allow remote code execution if a user visited a web site or opened an affected email attachment. An attacker who successfully exploited this vulnerability could potentially take complete control of an affected system. Affected versions • • • Attack Vectors/Impact In a Web-based attack scenario, an attacker would have to host a Web site that contains a Power. Point file that is used to attempt to exploit this vulnerability. An attacker would have to persuade them to visit the Web site, typically by getting them to click a link that takes them to the attacker's site. The vulnerability cannot be exploited automatically through e-mail. For an attack to be successful a user must open an attachment that is sent in an e-mail message. Microsoft Microsoft Power. Point 2000 Service Pack 3 Power. Point 2002 Service Pack 3 Office Power. Point 2003 Service Pack 1 or Service Pack 2 Office 2004 for Macintosh Power. Point v. X for Macintosh • This Security Update replaces MS 06 -028. • CVE-2006 -4694 - Power. Point Malformed Record Vulnerability has been publicly disclosed. • When this security bulletin was released, Microsoft had received information that the CVE-2006 -4694 vulnerability was being exploited.

MS 06 -058: Power. Point - Critical Title Vulnerabilities in Microsoft Power. Point Could Lead to Remote Code Execution (924163) The Fix • Power. Point Malformed Object Pointer Vulnerability - CVE-2006 -3435 - Modifies the way that Power. Point parses the file and validates the object pointer before passing it to the allocated buffer. • Power. Point Malformed Data Record Vulnerability - CVE-2006 -3876, Power. Point Malformed Record Memory Corruption Vulnerability - CVE-2006 -3877, and Power. Point Malformed Record Vulnerability - CVE-2006 -4694 – Modifies the way that Power. Point parses the file and validates the record before passing it to the allocated buffer. Mitigations • In a Web-based attack scenario, an attacker would have to host a Web site that contains a Power. Point file that is used to attempt to exploit this vulnerability. An attacker would have to persuade them to visit the Web site, typically by getting them to click a link that takes them to the attacker's site. • The vulnerability cannot be exploited automatically through e-mail. For an attack to be successful a user must open an attachment that is sent in an e-mail message. • Users who have installed and are using the Office Document Open Confirmation Tool for Office 2000 will be prompted with Open, Save, or Cancel before opening a document. Workaround Do not open or save Power. Point files that you receive from un-trusted sources or that you received unexpectedly from trusted sources. This vulnerability could be exploited when a user opens a file.
MS 06 -058: Power. Point - Critical Title Vulnerabilities in Microsoft Power. Point Could Lead to Remote Code Execution (924163) Other information • To help reduce the chance that a restart will be required, exit Power. Point prior to installing the security update. For more information about the reasons why you may be prompted to restart, see Microsoft Knowledge Base Article 887012. • For Power. Point 2000 and Macintosh versions, this update cannot be uninstalled. • For Power. Point 2002 and 2003, typically there is an uninstall option, but see Microsoft Knowledge Base Article 903771 for typical Office uninstall issues. More Information • For more Information, please review the FAQ at: http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -058. mspx

Questions about MS 06 -058?
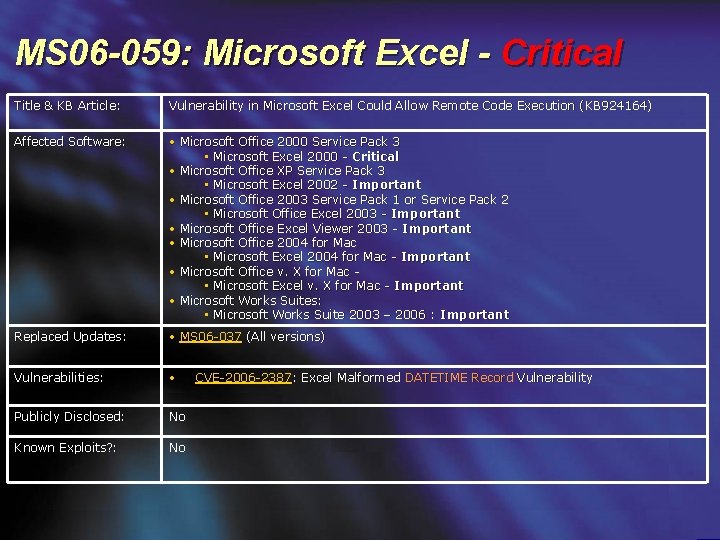
MS 06 -059: Microsoft Excel - Critical Title & KB Article: Vulnerability in Microsoft Excel Could Allow Remote Code Execution (KB 924164) Affected Software: • Microsoft Office 2000 Service Pack 3 • Microsoft Excel 2000 - Critical • Microsoft Office XP Service Pack 3 • Microsoft Excel 2002 - Important • Microsoft Office 2003 Service Pack 1 or Service Pack 2 • Microsoft Office Excel 2003 - Important • Microsoft Office Excel Viewer 2003 - Important • Microsoft Office 2004 for Mac • Microsoft Excel 2004 for Mac - Important • Microsoft Office v. X for Mac • Microsoft Excel v. X for Mac - Important • Microsoft Works Suites: • Microsoft Works Suite 2003 – 2006 : Important Replaced Updates: • MS 06 -037 (All versions) Vulnerabilities: • Publicly Disclosed: No Known Exploits? : No CVE-2006 -2387: Excel Malformed DATETIME Record Vulnerability
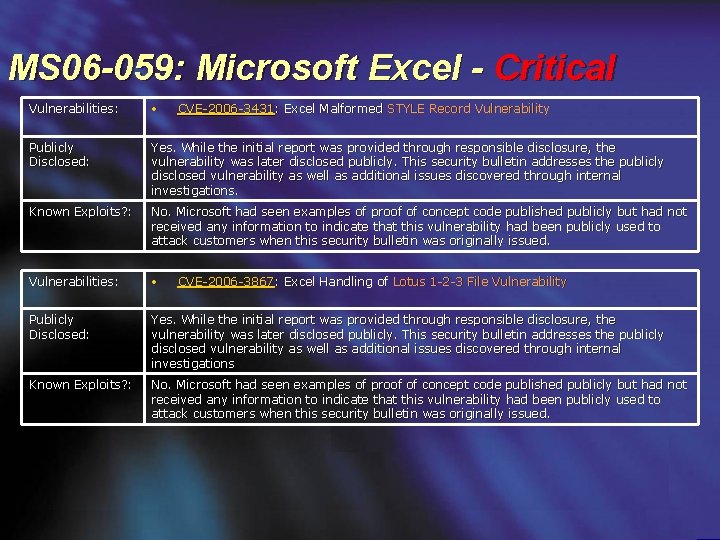
MS 06 -059: Microsoft Excel - Critical Vulnerabilities: • Publicly Disclosed: Yes. While the initial report was provided through responsible disclosure, the vulnerability was later disclosed publicly. This security bulletin addresses the publicly disclosed vulnerability as well as additional issues discovered through internal investigations. Known Exploits? : No. Microsoft had seen examples of proof of concept code published publicly but had not received any information to indicate that this vulnerability had been publicly used to attack customers when this security bulletin was originally issued. Vulnerabilities: • Publicly Disclosed: Yes. While the initial report was provided through responsible disclosure, the vulnerability was later disclosed publicly. This security bulletin addresses the publicly disclosed vulnerability as well as additional issues discovered through internal investigations Known Exploits? : No. Microsoft had seen examples of proof of concept code published publicly but had not received any information to indicate that this vulnerability had been publicly used to attack customers when this security bulletin was originally issued. CVE-2006 -3431: Excel Malformed STYLE Record Vulnerability CVE-2006 -3867: Excel Handling of Lotus 1 -2 -3 File Vulnerability
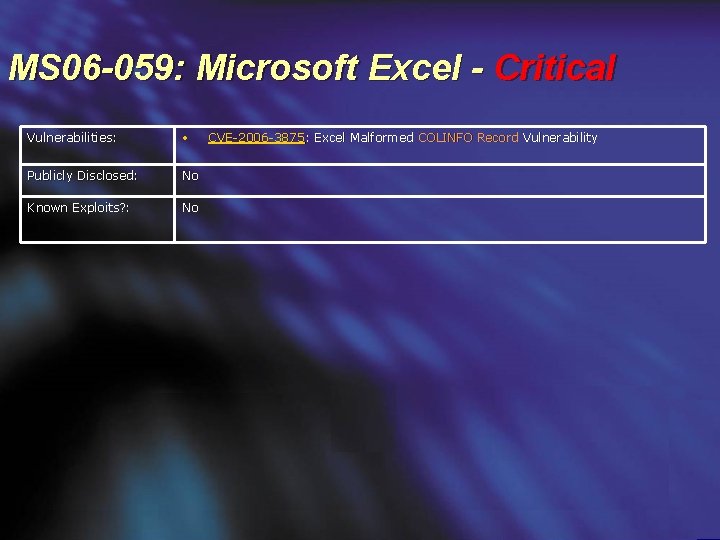
MS 06 -059: Microsoft Excel - Critical Vulnerabilities: • Publicly Disclosed: No Known Exploits? : No CVE-2006 -3875: Excel Malformed COLINFO Record Vulnerability
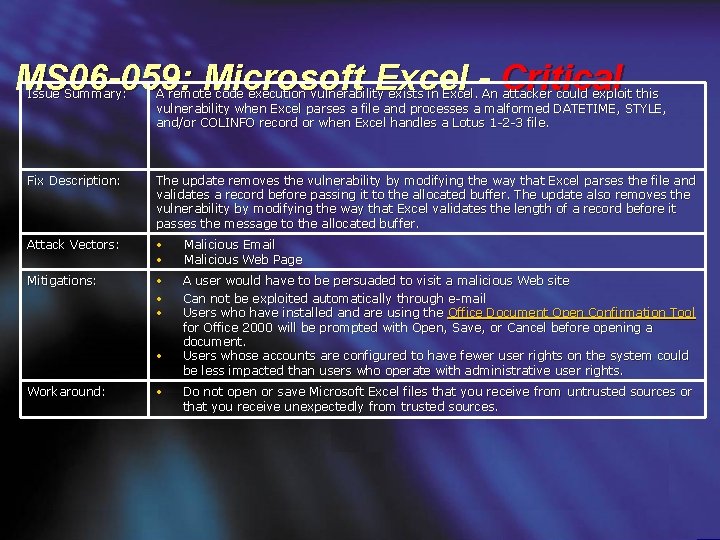
MS 06 -059: Microsoft Excel - Critical Issue Summary: A remote code execution vulnerability exists in Excel. An attacker could exploit this vulnerability when Excel parses a file and processes a malformed DATETIME, STYLE, and/or COLINFO record or when Excel handles a Lotus 1 -2 -3 file. Fix Description: The update removes the vulnerability by modifying the way that Excel parses the file and validates a record before passing it to the allocated buffer. The update also removes the vulnerability by modifying the way that Excel validates the length of a record before it passes the message to the allocated buffer. Attack Vectors: • • Malicious Email Malicious Web Page Mitigations: • • • A user would have to be persuaded to visit a malicious Web site Can not be exploited automatically through e-mail Users who have installed and are using the Office Document Open Confirmation Tool for Office 2000 will be prompted with Open, Save, or Cancel before opening a document. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. • Workaround: • Do not open or save Microsoft Excel files that you receive from untrusted sources or that you receive unexpectedly from trusted sources.
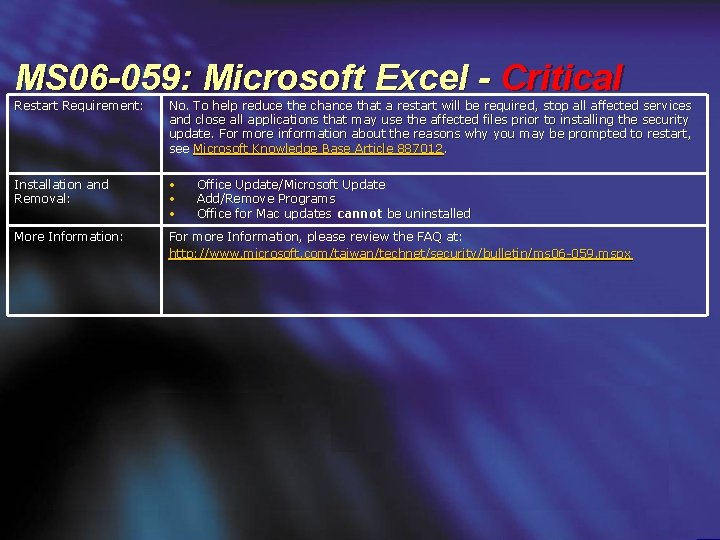
MS 06 -059: Microsoft Excel - Critical Restart Requirement: No. To help reduce the chance that a restart will be required, stop all affected services and close all applications that may use the affected files prior to installing the security update. For more information about the reasons why you may be prompted to restart, see Microsoft Knowledge Base Article 887012. Installation and Removal: • • • More Information: For more Information, please review the FAQ at: http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -059. mspx Office Update/Microsoft Update Add/Remove Programs Office for Mac updates cannot be uninstalled

Questions about MS 06 -059?
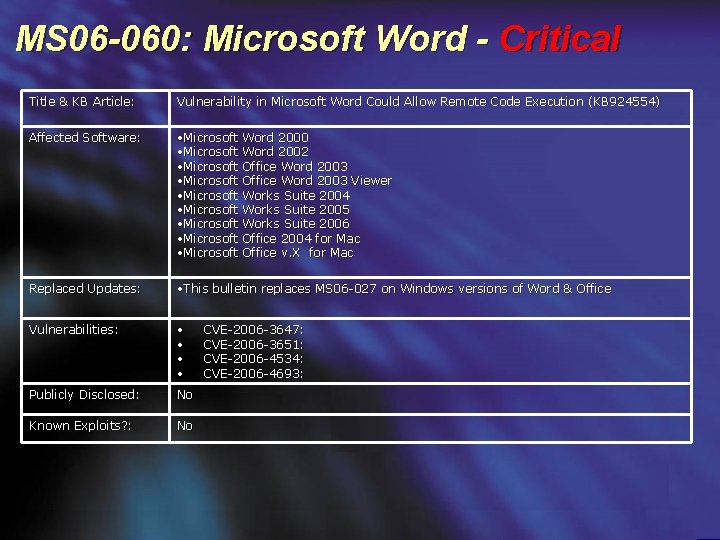
MS 06 -060: Microsoft Word - Critical Title & KB Article: Vulnerability in Microsoft Word Could Allow Remote Code Execution (KB 924554) Affected Software: • Microsoft Word 2000 • Microsoft Word 2002 • Microsoft Office Word 2003 Viewer • Microsoft Works Suite 2004 • Microsoft Works Suite 2005 • Microsoft Works Suite 2006 • Microsoft Office 2004 for Mac • Microsoft Office v. X for Mac Replaced Updates: • This bulletin replaces MS 06 -027 on Windows versions of Word & Office Vulnerabilities: • • Publicly Disclosed: No Known Exploits? : No CVE-2006 -3647: CVE-2006 -3651: CVE-2006 -4534: CVE-2006 -4693:
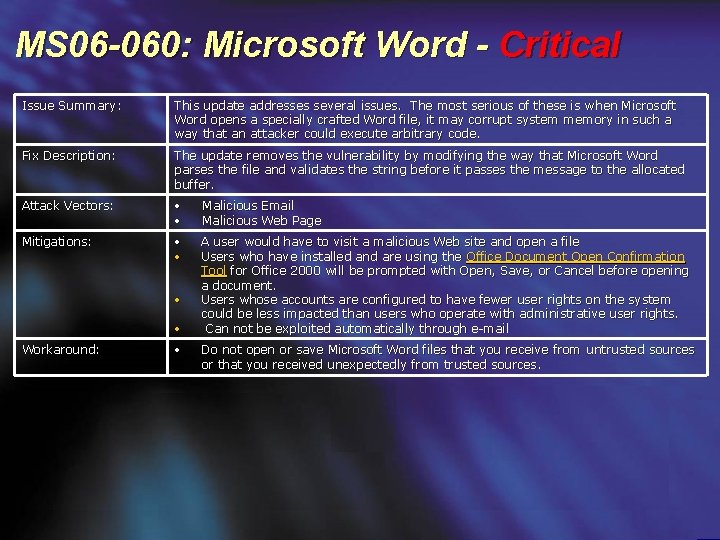
MS 06 -060: Microsoft Word - Critical Issue Summary: This update addresses several issues. The most serious of these is w hen Microsoft Word opens a specially crafted Word file, it may corrupt system memory in such a way that an attacker could execute arbitrary code. Fix Description: The update removes the vulnerability by modifying the way that Microsoft Word parses the file and validates the string before it passes the message to the allocated buffer. Attack Vectors: • • Malicious Email Malicious Web Page Mitigations: • • A user would have to visit a malicious Web site and open a file Users who have installed and are using the Office Document Open Confirmation Tool for Office 2000 will be prompted with Open, Save, or Cancel before opening a document. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. Can not be exploited automatically through e-mail • • Workaround: • Do not open or save Microsoft Word files that you receive from untrusted sources or that you received unexpectedly from trusted sources.
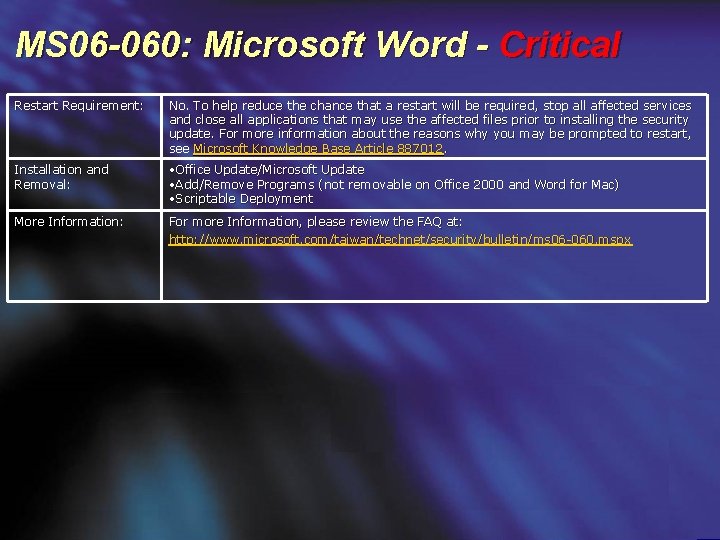
MS 06 -060: Microsoft Word - Critical Restart Requirement: No. To help reduce the chance that a restart will be required, stop all affected services and close all applications that may use the affected files prior to installing the security update. For more information about the reasons why you may be prompted to restart, see Microsoft Knowledge Base Article 887012. Installation and Removal: • Office Update/Microsoft Update • Add/Remove Programs (not removable on Office 2000 and Word for Mac) • Scriptable Deployment More Information: For more Information, please review the FAQ at: http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -060. mspx

Questions about MS 06 -060?
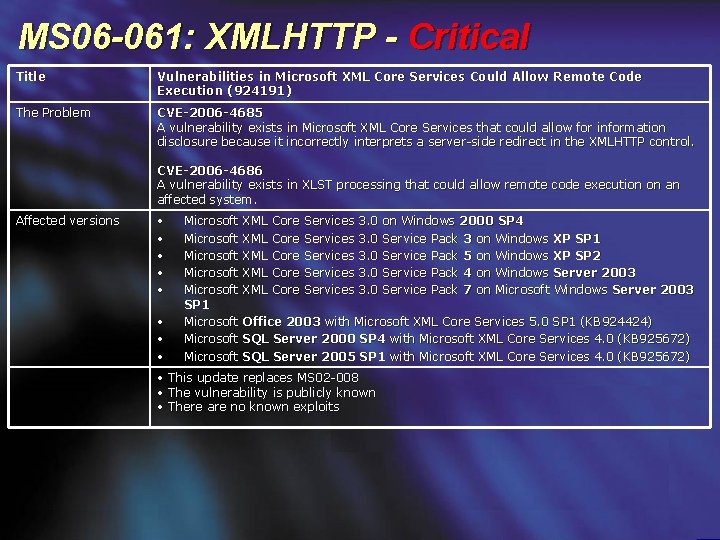
MS 06 -061: XMLHTTP - Critical Title Vulnerabilities in Microsoft XML Core Services Could Allow Remote Code Execution (924191) The Problem CVE-2006 -4685 A vulnerability exists in Microsoft XML Core Services that could allow for information disclosure because it incorrectly interprets a server-side redirect in the XMLHTTP control. CVE-2006 -4686 A vulnerability exists in XLST processing that could allow remote code execution on an affected system. Affected versions • • Microsoft Microsoft SP 1 Microsoft XML XML XML Core Core Services Services 3. 0 3. 0 on Windows 2000 SP 4 Service Pack 3 on Windows XP SP 1 Service Pack 5 on Windows XP SP 2 Service Pack 4 on Windows Server 2003 Service Pack 7 on Microsoft Windows Server 2003 Office 2003 with Microsoft XML Core Services 5. 0 SP 1 (KB 924424) SQL Server 2000 SP 4 with Microsoft XML Core Services 4. 0 (KB 925672) SQL Server 2005 SP 1 with Microsoft XML Core Services 4. 0 (KB 925672) • This update replaces MS 02 -008 • The vulnerability is publicly known • There are no known exploits
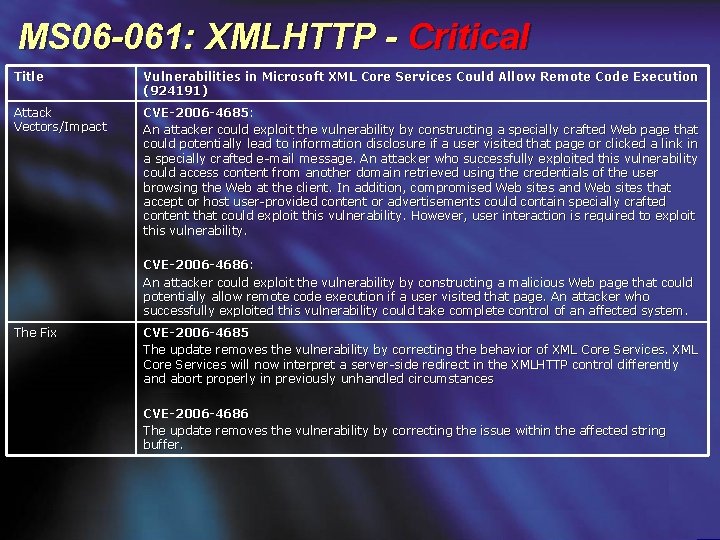
MS 06 -061: XMLHTTP - Critical Title Vulnerabilities in Microsoft XML Core Services Could Allow Remote Code Execution (924191) Attack Vectors/Impact CVE-2006 -4685: An attacker could exploit the vulnerability by constructing a specially crafted Web page that could potentially lead to information disclosure if a user visited that page or clicked a link in a specially crafted e-mail message. An attacker who successfully exploited this vulnerability could access content from another domain retrieved using the credentials of the user browsing the Web at the client. In addition, compromised Web sites and Web sites that accept or host user-provided content or advertisements could contain specially crafted content that could exploit this vulnerability. However, user interaction is required to exploit this vulnerability. CVE-2006 -4686: An attacker could exploit the vulnerability by constructing a malicious Web page that could potentially allow remote code execution if a user visited that page. An attacker who successfully exploited this vulnerability could take complete control of an affected system. The Fix CVE-2006 -4685 The update removes the vulnerability by correcting the behavior of XML Core Services will now interpret a server-side redirect in the XMLHTTP control differently and abort properly in previously unhandled circumstances CVE-2006 -4686 The update removes the vulnerability by correcting the issue within the affected string buffer.
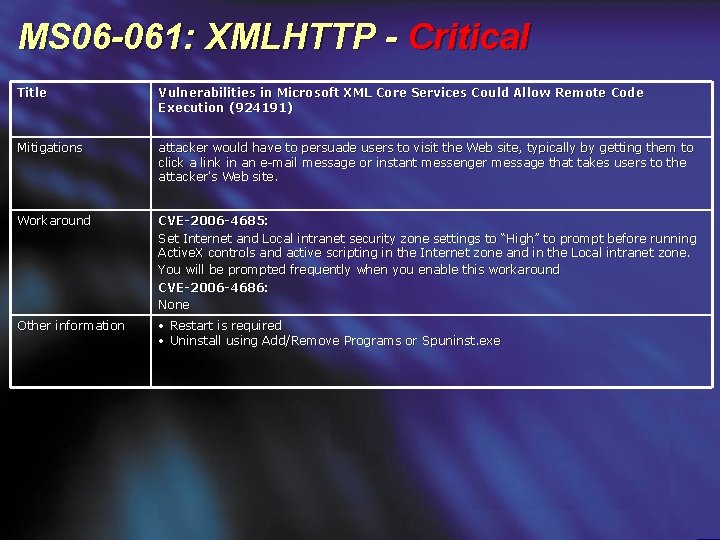
MS 06 -061: XMLHTTP - Critical Title Vulnerabilities in Microsoft XML Core Services Could Allow Remote Code Execution (924191) Mitigations attacker would have to persuade users to visit the Web site, typically by getting them to click a link in an e-mail message or instant messenger message that takes users to the attacker's Web site. Workaround CVE-2006 -4685: Set Internet and Local intranet security zone settings to “High” to prompt before running Active. X controls and active scripting in the Internet zone and in the Local intranet zone. You will be prompted frequently when you enable this workaround CVE-2006 -4686: None Other information • Restart is required • Uninstall using Add/Remove Programs or Spuninst. exe
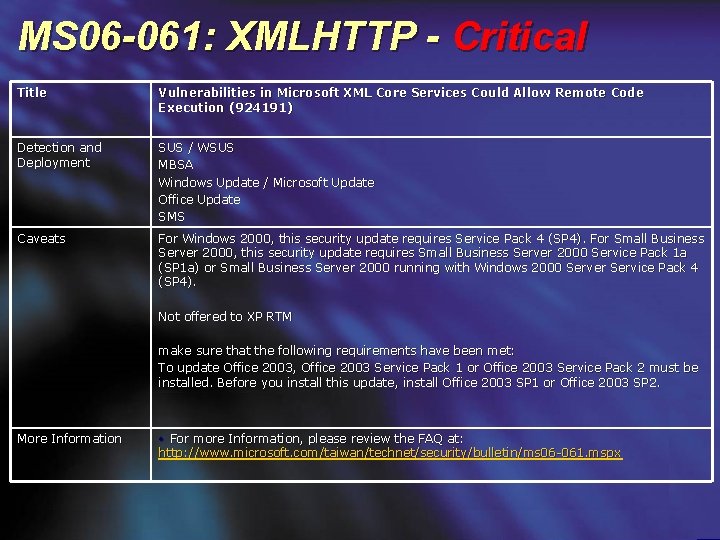
MS 06 -061: XMLHTTP - Critical Title Vulnerabilities in Microsoft XML Core Services Could Allow Remote Code Execution (924191) Detection and Deployment SUS / WSUS MBSA Windows Update / Microsoft Update Office Update SMS Caveats For Windows 2000, this security update requires Service Pack 4 (SP 4). For Small Business Server 2000, this security update requires Small Business Server 2000 Service Pack 1 a (SP 1 a) or Small Business Server 2000 running with Windows 2000 Server Service Pack 4 (SP 4). Not offered to XP RTM make sure that the following requirements have been met: To update Office 2003, Office 2003 Service Pack 1 or Office 2003 Service Pack 2 must be installed. Before you install this update, install Office 2003 SP 1 or Office 2003 SP 2. More Information • For more Information, please review the FAQ at: http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -061. mspx
MS 06 -061: XMLHTTP - Critical • Installation fail issue – Try install MSI 3. 1 v 2 then reinstall the patch http: //support. microsoft. com/? kbid=893803 – If still fail to install, contact Microsoft CSS support. http: //support. microsoft. com/contactus/? ws=support

Questions about MS 06 -061?

MS 06 -062: Office - Critical Title Vulnerabilities in Microsoft Office Could Lead to Remote Code Execution (922581) The Problem This Office update addresses three 'Remote Code Execution' Office vulnerabilities. An attacker could exploit one of these vulnerabilities by constructing a specially crafted file that could potentially allow remote code execution if a user visited a web site or opened an affected email attachment. An attacker who successfully exploited this vulnerability could potentially take complete control of an affected system. Affected versions • • • Attack Vectors/Impact In a Web-based attack scenario, an attacker would have to host a Web site that contains an Office file that is used to attempt to exploit this vulnerability. An attacker would have to persuade them to visit the Web site, typically by getting them to click a link that takes them to the attacker's site. The vulnerability cannot be exploited automatically through e-mail. For an attack to be successful a user must open an attachment that is sent in an e-mail message. Microsoft Microsoft Microsoft Office 2000 Service Pack 3 Office XP Service Pack 3 Office 2003 Service Pack 1 and Service Pack 2 Excel 2003 Viewer Word 2003 Viewer Office 2004 for Macintosh Office v. X for Macintosh Visio 2002 and Microsoft Visio 2003 Project 2000, Microsoft Project 2002, and Microsoft Project 2003 • This Security Update replaces MS 06 -038 • These vulnerabilities have not been reported to Microsoft as publicly disclosed. • There have been no reported exploits.
MS 06 -062: Office - Critical Title Vulnerabilities in Microsoft Office Could Lead to Remote Code Execution (922581) The Fix • Office Improper Memory Access Vulnerability - CVE-2006 -3434 – Modifies the way that Office parses the file and validates the length of a string before passing it to the allocated buffer. • Office Malformed Chart Record Vulnerability - CVE-2006 -3650 – Modifies the way that Office parses the length of a record before it passes the message to the allocated buffer. • Office Malformed Record Memory Corruption Vulnerability - CVE-2006 -3864 - Modifies the way that Office parses the file and validates the length of a string before passing it to the allocated buffer. Mitigations In a Web-based attack scenario, an attacker would have to host a Web site that contains an Office file that is used to attempt to exploit this vulnerability. An attacker would have to persuade them to visit the Web site, typically by getting them to click a link that takes them to the attacker's site. The vulnerability cannot be exploited automatically through e-mail. For an attack to be successful a user must open an attachment that is sent in an e-mail message. Users who have installed and are using the Office Document Open Confirmation Tool for Office 2000 will be prompted with Open, Save, or Cancel before opening a document. Workaround • Do not open or save Office files that you receive from un-trusted sources or that you received unexpectedly from trusted sources. • This vulnerability could be exploited when a user opens a file.
MS 06 -062: Office - Critical Title Vulnerabilities in Microsoft Office Could Lead to Remote Code Execution (922581) Other information • Is a Restart required? If Office is not running, no restart should be required. see Microsoft Knowledge Base Article 887012 for known reasons why you may be prompted to restart. • Is there an uninstall option? This Security Update cannot be uninstalled from Office 2000 or from Macintosh versions of Office. More Information • For more Information, please review the FAQ at: http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -062. mspx

Questions about MS 06 -062?

MS 06 -063: Windows - Important Title Vulnerability in Server Service Could Allow Denial of Service or Remote Code Execution (KB 923414) The Problem A Do. S vulnerability (CVE-2006 -3942) exists in the Server service because of the way it handles certain network messages. An attacker could exploit the vulnerability by sending a specially crafted network message to a computer running the Server service, causing the computer to stop responding. A RCE vulnerability (CVE-2006 -4696) exists in the Server service because of the way it handles certain network messages. An attacker could exploit the vulnerability by sending a specially crafted network message to a computer running the Server service as an authenticated user, taking complete control of the affected system. Affected versions Both vulnerabilities affect all currently supported versions of Windows: Win 2000 SP 4 Win XP SP 1, XP SP 2, XP x 64 Win 2003, 2003 SP 1, 2003 Itanium SP 1, 2003 x 64 Attack Vectors/Impact Any anonymous attacker could exploit the Denial of Service vulnerability (CVE-2006 -3942) by creating a specially crafted message and sending the message to an affected system. Any authenticated attacker could exploit the Remote Code Execution vulnerability (CVE-20064696) by creating a specially crafted message and sending the message to an affected system. • This update supersedes MS 06 -035 on all supported platforms. • Do. S vulnerability (CVE-2006 -3942): This vulnerability had been publicly disclosed when this bulletin was originally issued. Proof of Concept code had been published publicly, but Microsoft had not received reports of attacks exploiting this vulnerability when this bulletin was originally issued. • RCE vulnerability (CVE-2006 -4696): This vulnerability had not been publicly disclosed when this bulletin was originally issued. Po. C code had not been published publicly, and MS had not received reports of attacks exploiting this vulnerability when this bulletin was originally issued.

MS 06 -063: Windows - Important Title Vulnerability in Server Service Could Allow Denial of Service or Remote Code Execution (KB 923414) The Fix • The update removes the Do. S vulnerability (CVE-2006 -3942) by initializing a buffer before it is used. The update removes the RCE vulnerability (CVE-2006 -4696) by removing the faulty code. Mitigations • Firewall best practices and standard default firewall configurations can help protect networks from attacks that originate outside the enterprise perimeter. Best practices recommend that systems that are connected to the Internet have a minimal number of ports exposed. Workaround • Block UDP ports 135, 137, 138, and 445, and TCP ports 135, 139, 445, and 593 • These ports can be blocked at dedicated border firewalls, or individual machines can be protected with the Internet Connection Firewall / Windows Firewall in Windows XP and Windows 2003 • As an alternative, IPSEC can be used to filter TCP and UDP ports per KB 313190 & KB 813878 Other information • A restart is required. • The update can be uninstalled. More Information • For more Information, please review the FAQ at: http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -063. mspx

Questions about MS 06 -063?

MS 06 -064: TCP/IP - Low Title & KB Article: Vulnerabilities in TCP/IP Could Allow Denial of Service (KB 922819) Affected Software: • Microsoft Windows XP SP 1 and SP 2, x 64 Edition • Microsoft Windows Server 2003 RTM & SP 1, x 64 Edition • Microsoft Windows Server 2003 for RTM & SP 1 for Itanium-based Systems Replaced Updates: • None Vulnerabilities: • • • Publicly Disclosed: Yes Known Exploits? : No CAN-2004 -0790: ICMP Connection Reset Vulnerability CAN-2004 -0230: TCP Connection Reset Vulnerability CAN-2005 -0688 Spoofed Connection Request Vulnerability

MS 06 -064: TCP/IP - Low Issue Summary: This update addresses several issues. • Two denial of service vulnerabilities exists that could allow an attacker to send a specially crafted ICMP or TCP message to an affected system. An attacker who successfully exploited this vulnerability could cause the affected system to reset existing TCP connections • A denial of service vulnerability exists that could allow an attacker to send a specially crafted TCP/IP message to an affected system. An attacker who successfully exploited this vulnerability could cause the affected system to stop responding. Fix Description: • The update removes the vulnerability by modifying the way that the affected operating systems validate ICMP and TCP packets. Attack Vectors: • Affected versions of systems using IPv 6 on networks which are not protected by a firewall Mitigations: • Workaround: • • • A user would have to be on a network that did not block unsolicited external ICMP/TCP traffic IPv 6 is not installed by default on any version of Windows Attacker would have to be on the same IPv 6 network Block IPv 6 ICMP and TCP ports at the firewall ICMP Reset vuln. would require attacker to predict/learn connection information Spoofed Connection vuln. would require router to forward malformed packets • • Block IPv 6 at firewall Block ICMP using IPSec Use Syn. Attack. Protect registry value on Windows Server 2003 Remove IPv 6 if not needed

MS 06 -064: TCP/IP - Low Restart Requirement: Yes Installation and Removal: • • • More Information: For more Information, please review the FAQ at: http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -064. mspx Add/Remove Programs Command line uninstall option Scriptable Deployment

Questions about MS 06 -064?
MS 06 -065: Windows Object Packager Moderate Title & KB Article: Vulnerability in Windows Object Packager Could Allow Remote Execution (KB 924496) Affected Software: • Windows XP SP 1, SP 2 and x 64 Edition • Windows Server 2003 RTM, SP 1, Itanium and x 64 Edition Replaced Updates: • None Vulnerabilities: • Publicly Disclosed: No Known Exploits? : No CVE-2006 -4692: Object Packager Dialogue Spoofing Vulnerability
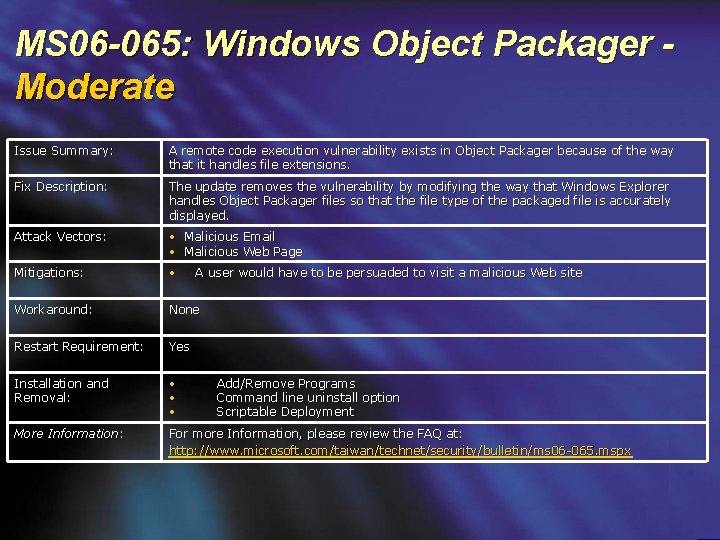
MS 06 -065: Windows Object Packager Moderate Issue Summary: A remote code execution vulnerability exists in Object Packager because of the way that it handles file extensions. Fix Description: The update removes the vulnerability by modifying the way that Windows Explorer handles Object Packager files so that the file type of the packaged file is accurately displayed. Attack Vectors: • Malicious Email • Malicious Web Page Mitigations: • Workaround: None Restart Requirement: Yes Installation and Removal: • • • More Information: For more Information, please review the FAQ at: http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -065. mspx A user would have to be persuaded to visit a malicious Web site Add/Remove Programs Command line uninstall option Scriptable Deployment

Questions about MS 06 -065?
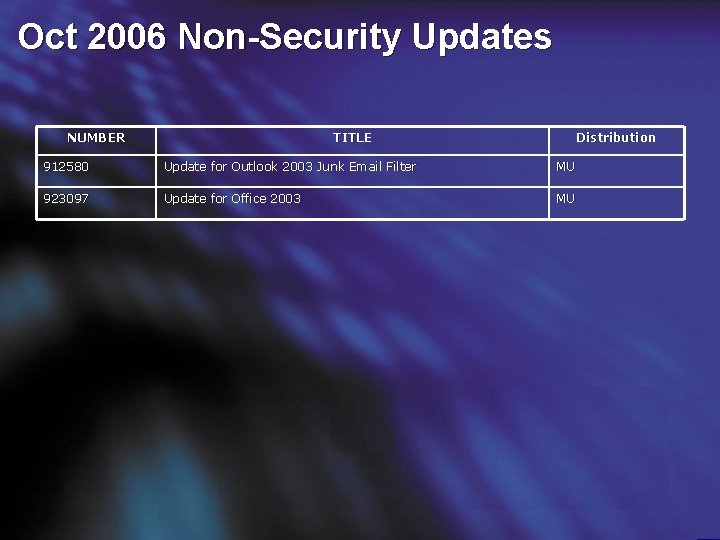
Oct 2006 Non-Security Updates NUMBER TITLE Distribution 912580 Update for Outlook 2003 Junk Email Filter MU 923097 Update for Office 2003 MU
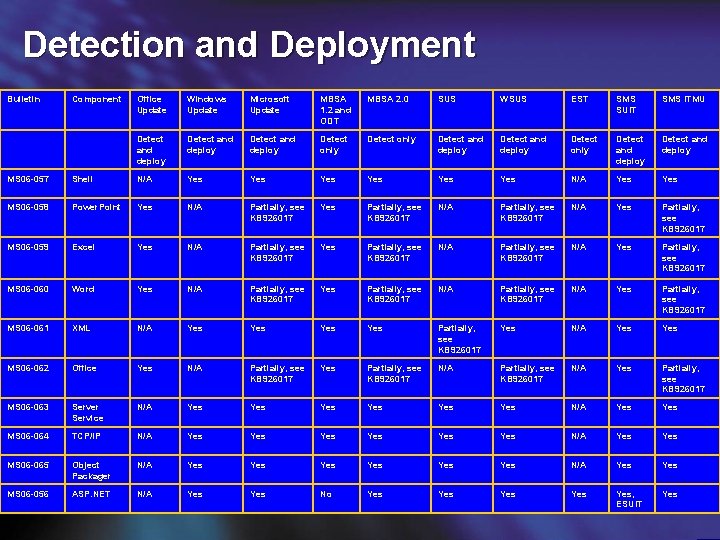
Detection and Deployment Bulletin Component Office Update Windows Update Microsoft Update MBSA 1. 2 and ODT MBSA 2. 0 SUS WSUS EST SMS SUIT SMS ITMU Detect and deploy Detect only Detect and deploy MS 06 -057 Shell N/A Yes Yes Yes N/A Yes MS 06 -058 Power. Point Yes N/A Partially, see KB 926017 Yes Partially, see KB 926017 N/A Yes Partially, see KB 926017 MS 06 -059 Excel Yes N/A Partially, see KB 926017 Yes Partially, see KB 926017 N/A Yes Partially, see KB 926017 MS 06 -060 Word Yes N/A Partially, see KB 926017 Yes Partially, see KB 926017 N/A Yes Partially, see KB 926017 MS 06 -061 XML N/A Yes Yes Partially, see KB 926017 Yes N/A Yes MS 06 -062 Office Yes N/A Partially, see KB 926017 Yes Partially, see KB 926017 N/A Yes Partially, see KB 926017 MS 06 -063 Server Service N/A Yes Yes Yes N/A Yes MS 06 -064 TCP/IP N/A Yes Yes Yes N/A Yes MS 06 -065 Object Packager N/A Yes Yes Yes N/A Yes MS 06 -056 ASP. NET N/A Yes No Yes Yes Yes, ESUIT Yes
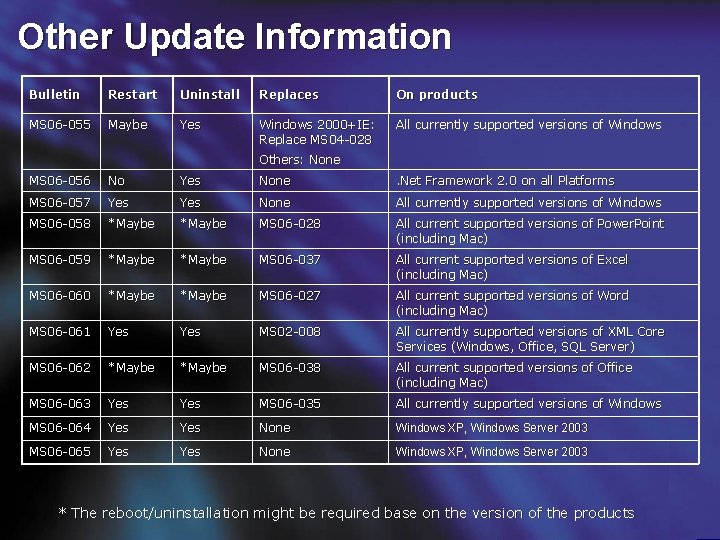
Other Update Information Bulletin Restart Uninstall Replaces On products MS 06 -055 Maybe Yes Windows 2000+IE: Replace MS 04 -028 All currently supported versions of Windows Others: None MS 06 -056 No Yes None . Net Framework 2. 0 on all Platforms MS 06 -057 Yes None All currently supported versions of Windows MS 06 -058 *Maybe MS 06 -028 All current supported versions of Power. Point (including Mac) MS 06 -059 *Maybe MS 06 -037 All current supported versions of Excel (including Mac) MS 06 -060 *Maybe MS 06 -027 All current supported versions of Word (including Mac) MS 06 -061 Yes MS 02 -008 All currently supported versions of XML Core Services (Windows, Office, SQL Server) MS 06 -062 *Maybe MS 06 -038 All current supported versions of Office (including Mac) MS 06 -063 Yes MS 06 -035 All currently supported versions of Windows MS 06 -064 Yes None Windows XP, Windows Server 2003 MS 06 -065 Yes None Windows XP, Windows Server 2003 * The reboot/uninstallation might be required base on the version of the products
Windows Malicious Software Removal Tool • Twenty-second monthly incremental update. • The Oct update adds the ability to remove: – Win 32/Tibs – Win 32/Harnig – Win 32/Passalert • Available as priority update through Windows Update or Microsoft Update for Windows XP users – Offered through WSUS; not offered through SUS 1. 0 • Also as an Active. X control or download at www. microsoft. com/malwareremove
Lifecycle Support Information • ENDED of public security support for Windows XP SP 1 – 10 October 2006 • Support EOL for Software Update Services (SUS) 1. 0 – 6 December 2006 • www. microsoft. com/windowsserversystem/updates ervices/evaluation/previous/default. mspx • See www. microsoft. com/lifecycle for more information

Prepare for IE 7 over AU • Prepare for AU distribution of Internet Explorer 7 by 1 November 2006 • Internet Explorer 7 Blocker Toolkit available for enterprise customers – Blocks automatic delivery of Internet Explorer 7 • For additional information see: http: //www. microsoft. com/technet/updatemanagement/wi ndowsupdate/ie 7 announcement. mspx
Resources • • • September Security Bulletin Webcast (US) http: //msevents. microsoft. com/CUI/Event. Detail. aspx? Event. ID=1032305653&Culture= en-US Security Bulletins Summary http: //www. microsoft. com/taiwan/technet/security/bulletin/ms 06 -aug. mspx Security Bulletins Search www. microsoft. com/technet/security/current. aspx Security Advisories www. microsoft. com/taiwan/technet/security/advisory/ MSRC Blog http: //blogs. technet. com/msrc Notifications www. microsoft. com/technet/security/bulletin/notify. mspx Tech. Net Radio www. microsoft. com/tnradio Search. Security Column http: //searchsecurity. techtarget. com/news/0, 289141, sid 14, 00. html IT Pro Security Newsletter www. microsoft. com/technet/security/secnews/ Tech. Net Security Center www. microsoft. com/taiwan/technet/security
Questions and Answers • Submit text questions using the “Ask a Question” button • Don’t forget to fill out the survey • For upcoming and previously recorded webcasts: http: //www. microsoft. com/taiwan/technet/webcast/default. aspx • Webcast content suggestions: twwebst@microsoft. com

- Slides: 62