Quantum Polling Joan Vaccaro Joe Spring Anthony Chefles
![Introduction Secure Survey Secure Voting Summary Quantum Fingerprinting [Buhrman…PRL 87, 167902 (2003)] Introduction fingerprint: Introduction Secure Survey Secure Voting Summary Quantum Fingerprinting [Buhrman…PRL 87, 167902 (2003)] Introduction fingerprint:](https://slidetodoc.com/presentation_image/2cbaf5a23fd0554744f2016e79420a4b/image-3.jpg)
- Slides: 16

Quantum Polling Joan Vaccaro Joe Spring Anthony Chefles Griffith University PRA 75, 012333 (2007), quant-ph/0504161 ~ Hillery et al. PLA 349 75 (2006), quant-ph/0505041 Uni of Hertfordshire HP Labs, Bristol QUantum PRoperties Of DIstributed Systems CQCT Feb 07 Griffith University 1

Introduction Secure Survey Secure Voting Summary Introduction ~ small scale quantum processing quantum data security QKD – commercial… other (incl. multiparty) protocols Quantum Fingerprinting Quantum Seals Authentication of Quantum Messages Quantum Broadcast Communication Quantum Anonymous Transmissions Quantum Exam Secret Sharing CQCT Feb 07 Griffith University 2
![Introduction Secure Survey Secure Voting Summary Quantum Fingerprinting BuhrmanPRL 87 167902 2003 Introduction fingerprint Introduction Secure Survey Secure Voting Summary Quantum Fingerprinting [Buhrman…PRL 87, 167902 (2003)] Introduction fingerprint:](https://slidetodoc.com/presentation_image/2cbaf5a23fd0554744f2016e79420a4b/image-3.jpg)
Introduction Secure Survey Secure Voting Summary Quantum Fingerprinting [Buhrman…PRL 87, 167902 (2003)] Introduction fingerprint: smaller string ~ uniquely identifies message. ~ Small scale quantum processing quantum fingerprints of classical messages are exp. smaller Quantum Seals [Bechmann-Pasquinucci quant-ph/0303173] encode classical message in quantum state Quantum data security (0 |0>|0>|f>, 1 |1>|1>|f>, order of bits is random, |f>=|0>+ei |1>) easily read vote)protocols – can detect if message has been read QKD – (majority 2 party – commercial… Authentication of Quantum Messages [Barnum… quant-ph/0205128] Other (incl. multiparty) protocols allows Bob to check that message has not been altered e. g. distribute EPR pairs, use purity. Communication checking, teleport, … Quantum Broadcast Quantum Anonymous Transmissions Fingerprinting [Christandl… quant-ph/0409201] Quantum Seals. Hadamard, measure – announce, share GHZ state, pi phase, Quantum Messages answer Authentication is mod 2. Can also of share entanglement with “anon Bob” Quantum Exam Anonymous Transmissions [Nguyen PLA 350, 174 (2006)] share GHZ states – local meas. gives shared random class. key Quantum Exam – use key to send common exam text and the individual answers. Secret [Hillery…, Sharing. PRA 59 1829 ; Cleve…PRL 83 648 (1999)] Secret Sharing CQCT Feb 07 Griffith University 3

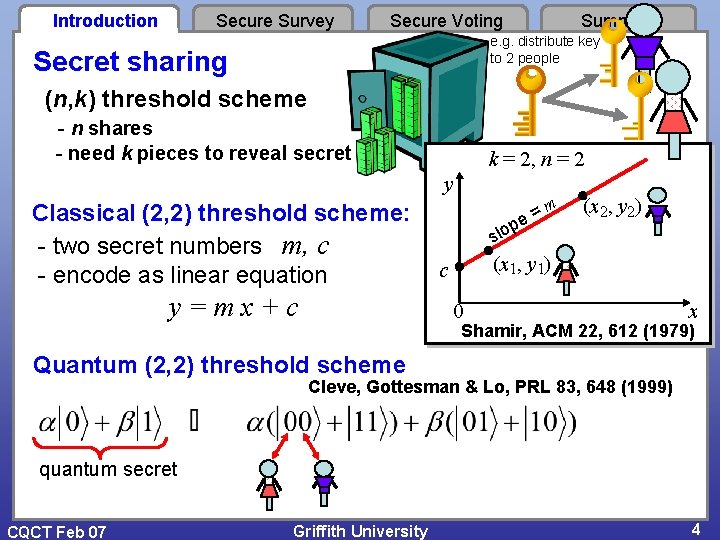
Introduction Secure Survey Secure Voting Summary e. g. distribute key to 2 people Secret sharing (n, k) threshold scheme - n shares - need k pieces to reveal secret k = 2, n = 2 y Classical (2, 2) threshold scheme: - two secret numbers m, c - encode as linear equation y=mx+c = e p m (x 2, y 2) slo (x 1, y 1) c 0 x Shamir, ACM 22, 612 (1979) Quantum (2, 2) threshold scheme Cleve, Gottesman & Lo, PRL 83, 648 (1999) quantum secret CQCT Feb 07 Griffith University 4

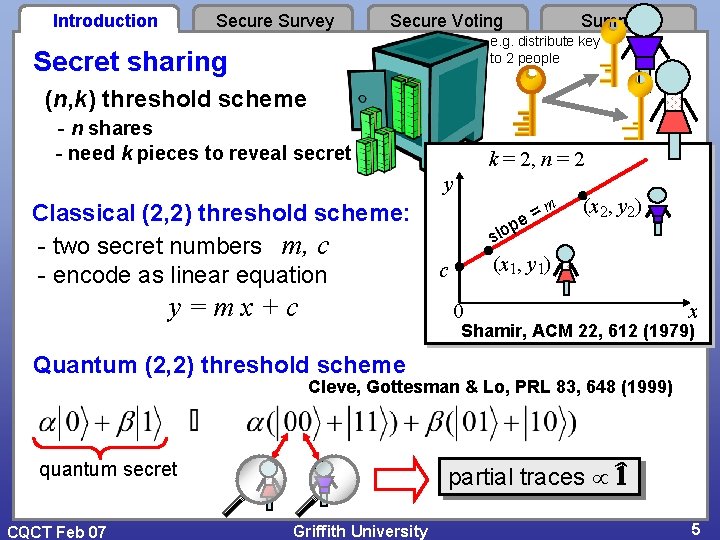
Introduction Secure Survey Secure Voting Summary e. g. distribute key to 2 people Secret sharing (n, k) threshold scheme - n shares - need k pieces to reveal secret k = 2, n = 2 y Classical (2, 2) threshold scheme: - two secret numbers m, c - encode as linear equation y=mx+c = e p m (x 2, y 2) slo (x 1, y 1) c 0 x Shamir, ACM 22, 612 (1979) Quantum (2, 2) threshold scheme Cleve, Gottesman & Lo, PRL 83, 648 (1999) quantum secret CQCT Feb 07 partial traces Griffith University 5

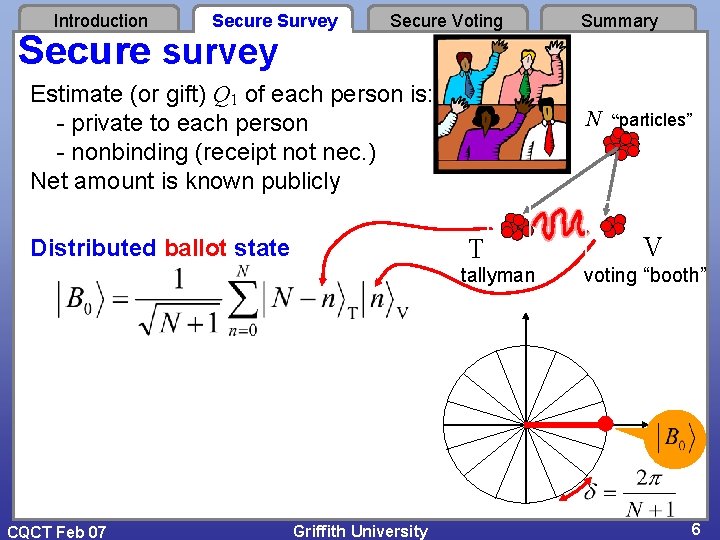
Introduction Secure Survey Secure survey Secure Voting Estimate (or gift) Q 1 of each person is: - private to each person - nonbinding (receipt not nec. ) Net amount is known publicly N “particles” T Distributed ballot state tallyman CQCT Feb 07 Griffith University Summary V voting “booth” 6

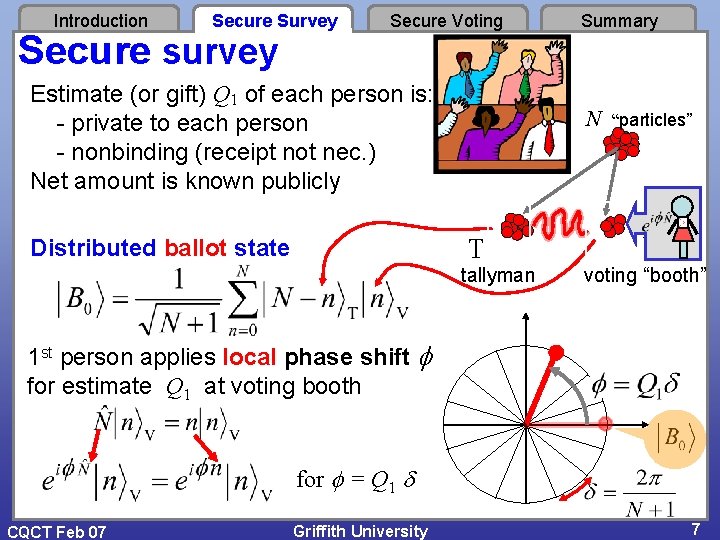
Introduction Secure Survey Secure survey Secure Voting Estimate (or gift) Q 1 of each person is: - private to each person - nonbinding (receipt not nec. ) Net amount is known publicly N “particles” T Distributed ballot state Summary tallyman V voting “booth” 1 st person applies local phase shift for estimate Q 1 at voting booth for = Q 1 CQCT Feb 07 Griffith University 7

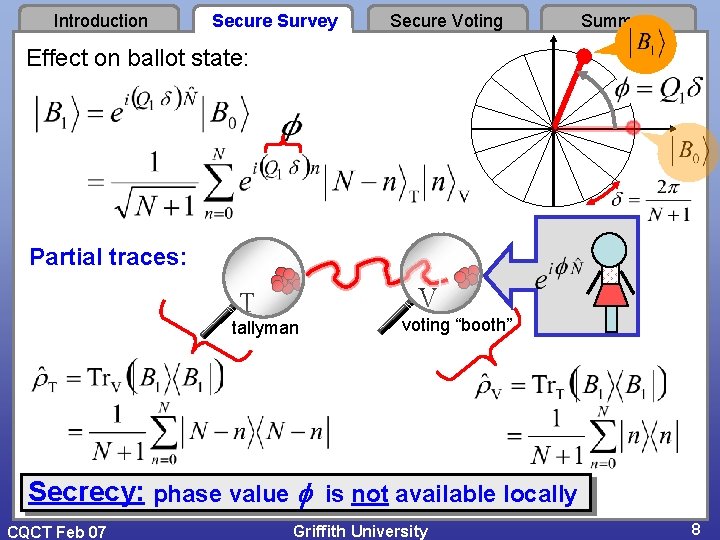
Introduction Secure Survey Secure Voting Summary Effect on ballot state: Partial traces: V T tallyman voting “booth” Secrecy: phase value is not available locally CQCT Feb 07 Griffith University 8

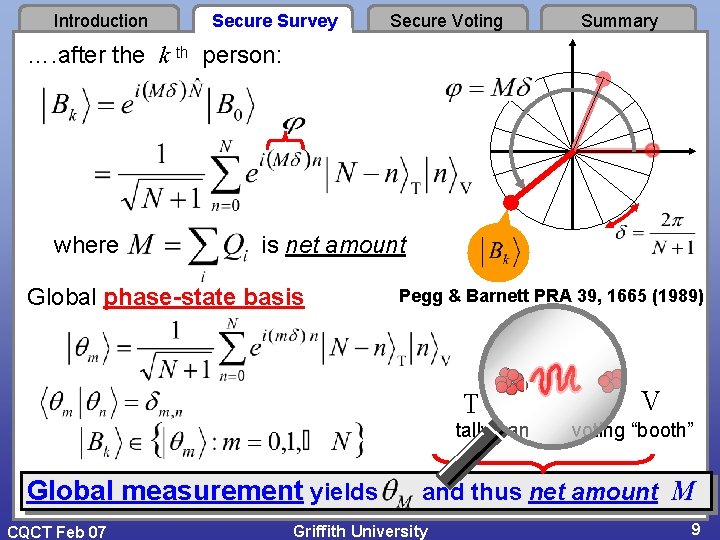
Introduction Secure Survey Secure Voting Summary …. after the k th person: where is net amount Global phase-state basis Pegg & Barnett PRA 39, 1665 (1989) T tallyman Global measurement yields CQCT Feb 07 V voting “booth” and thus net amount M Griffith University 9

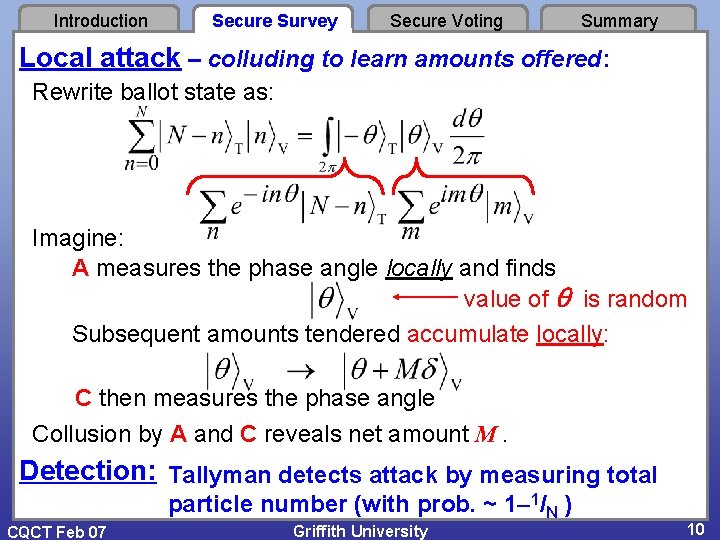
Introduction Secure Survey Secure Voting Summary Local attack – colluding to learn amounts offered: Rewrite ballot state as: Imagine: A measures the phase angle locally and finds value of is random Subsequent amounts tendered accumulate locally: C then measures the phase angle Collusion by A and C reveals net amount M. Detection: Tallyman detects attack by measuring total particle number (with prob. ~ 1 1/N ) CQCT Feb 07 Griffith University 10

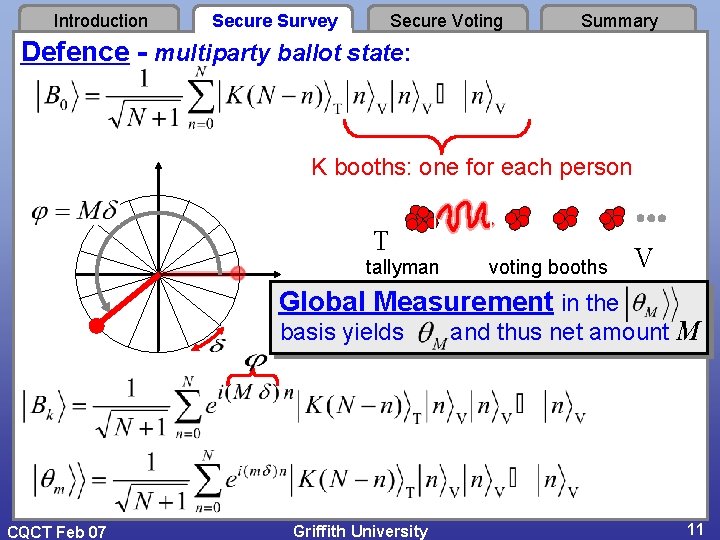
Introduction Secure Survey Secure Voting Summary Defence - multiparty ballot state: K booths: one for each person T tallyman voting booths V Global Measurement in the basis yields CQCT Feb 07 Griffith University and thus net amount M 11

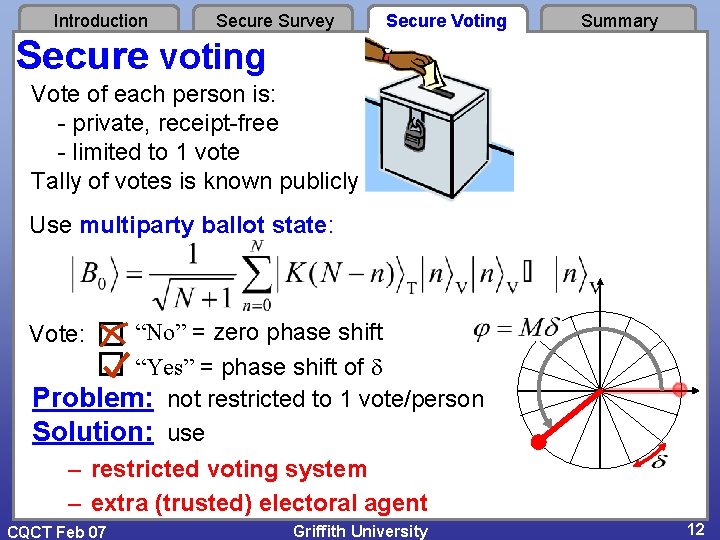
Introduction Secure Survey Secure Voting Summary Secure voting Vote of each person is: - private, receipt-free - limited to 1 vote Tally of votes is known publicly Use multiparty ballot state: “No” = zero phase shift “Yes” = phase shift of Problem: not restricted to 1 vote/person Solution: use – restricted voting system – extra (trusted) electoral agent Vote: CQCT Feb 07 Griffith University 12

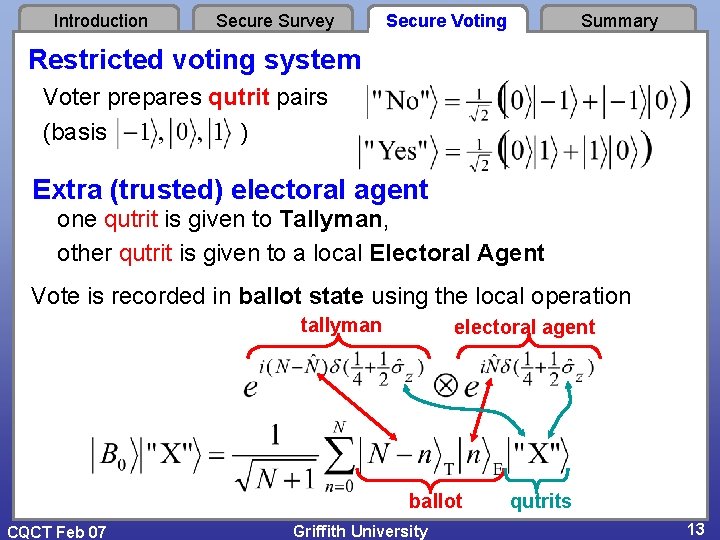
Introduction Secure Survey Secure Voting Summary Restricted voting system Voter prepares qutrit pairs (basis ) Extra (trusted) electoral agent one qutrit is given to Tallyman, other qutrit is given to a local Electoral Agent Vote is recorded in ballot state using the local operation tallyman electoral agent ballot CQCT Feb 07 Griffith University qutrits 13

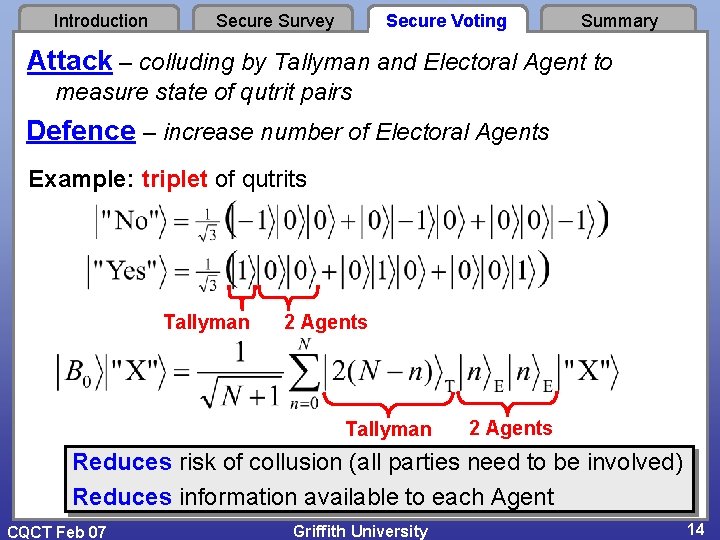
Introduction Secure Survey Secure Voting Summary Attack – colluding by Tallyman and Electoral Agent to measure state of qutrit pairs Defence – increase number of Electoral Agents Example: triplet of qutrits Tallyman 2 Agents Reduces risk of collusion (all parties need to be involved) Reduces information available to each Agent CQCT Feb 07 Griffith University 14

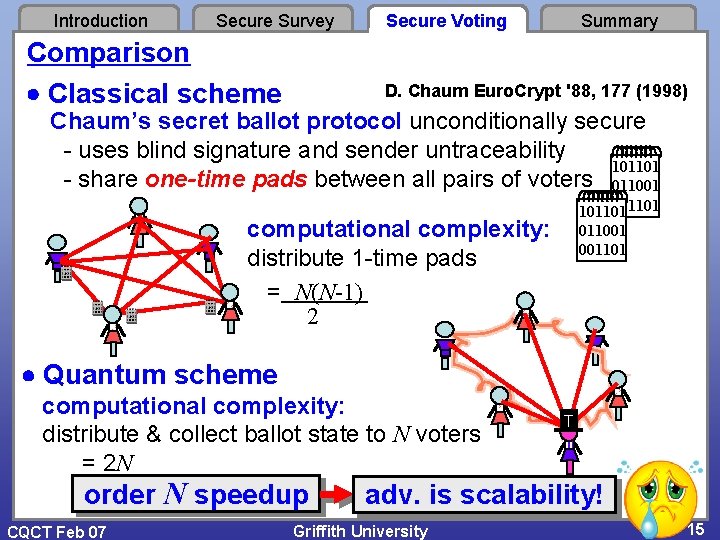
Introduction Secure Survey Comparison Classical scheme Secure Voting Summary D. Chaum Euro. Crypt '88, 177 (1998) Chaum’s secret ballot protocol unconditionally secure - uses blind signature and sender untraceability 101101 - share one-time pads between all pairs of voters 011001 001101 101101 011001 001101 computational complexity: distribute 1 -time pads = N(N-1) 2 Quantum scheme computational complexity: distribute & collect ballot state to N voters = 2 N order N speedup CQCT Feb 07 T adv. is scalability! Griffith University 15

Introduction Secure Survey Secure Voting Summary advocate small scale processing secure survey • multiparty ballot state • each offer is anonymous secure voting • 1 vote per voter • extra Electoral Agents • receipt-free CQCT Feb 07 Griffith University 16